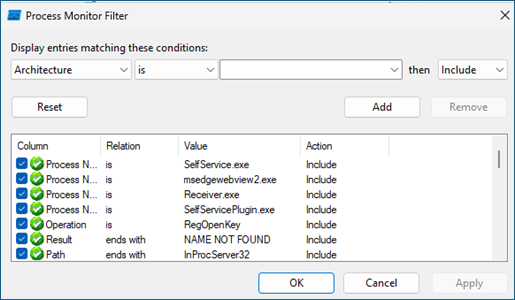
TL;DR: This post shows how COM hijacking can serve as a reliable persistence method while also enabling execution within commonly used applications across an environment. Overview Persistence is one of the most important steps in any red team engagement. Without persistence, all it takes is a reboot, a user logout, or some unexpected disruption, and […]
Understanding & Mitigating BadSuccessor
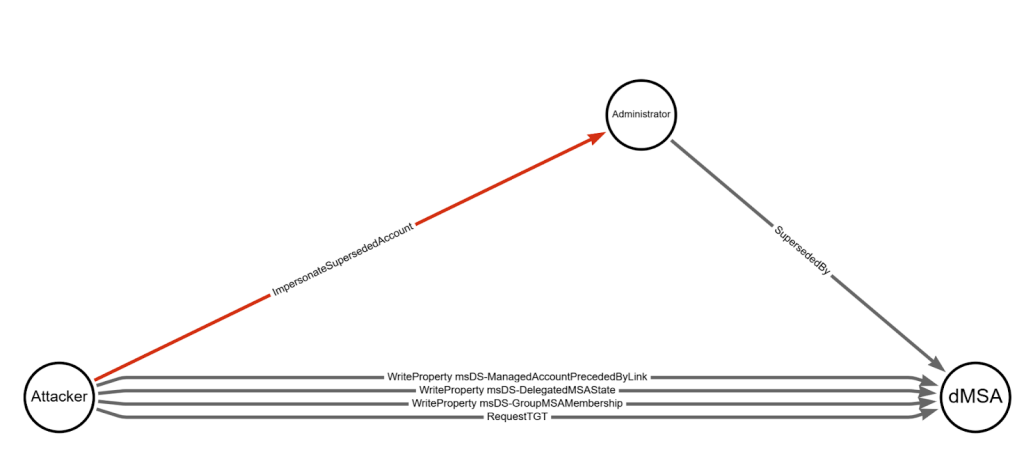
TL;DR: BadSuccessor is a new AD attack primitive that abuses dMSAs, allowing an attacker who can modify or create a dMSA to escalate privileges and take over the forest. The DACL-based parts of the attack have relatively straightforward mitigations. Recently Yuval Gordon at Akamai released the blog post BadSuccessor: Abusing dMSA to Escalate Privileges in […]
(Why) IAM demands an #AttackGraph First Approach
TL;DR: Don’t start with access lists—start with attacker movement. Your new baseline: “Be the best at predicting how an attacker would reach identities that control critical assets.”. Lead with an Attack Graph First approach. Add context and clear narrative to attack paths. Expose real risk and prioritize the most impactful fixes. Quick What Is; An […]
Running From Complacency: Getting Off Your InfoSec Hamster Wheels
TL;DR Breaking free from InfoSec complacency: We discuss how security leaders can align their security strategy with business goals, evaluate metrics critically, and collaborate with peers instead of running aimlessly on their information security hamster wheels. The past months have been your typical Information Security chaos with a bit of extra political flair. A rapidly […]
Getting the Most Value Out of the OSCP: The Exam
A practical guide to maximizing the short- and long-term benefits of your upcoming OSCP exam attempt(s). Disclaimer: All opinions expressed in this article are solely my own. I have reviewed the content to ensure compliance with OffSec’s copyright policies and agreements. I have not been sponsored or incentivized in any way to recommend or oppose […]
The Renaissance of NTLM Relay Attacks: Everything You Need to Know
NTLM relay attacks have been around for a long time. While many security practitioners think NTLM relay is a solved problem, or at least a not-so-severe one, it is, in fact, alive and kicking and arguably worse than ever before. Relay attacks are the easiest way to compromise domain-joined hosts nowadays, paving a path for […]
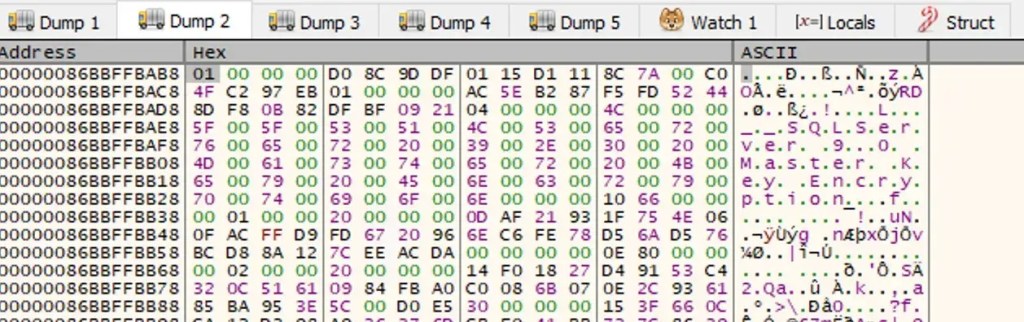
The SQL Server Crypto Detour
As part of my role as Service Architect here at SpecterOps, one of the things I’m tasked with is exploring all kinds of technologies to help those on assessments with advancing their engagement. Not long after starting this new role, I was approached with an interesting problem. A SQL Server database backup for a ManageEngine’s […]
An Operator’s Guide to Device-Joined Hosts and the PRT Cookie
About five years ago, Lee Chagolla-Christensen shared a blog detailing the research and development process behind his RequestAADRefreshToken proof-of-concept (POC).
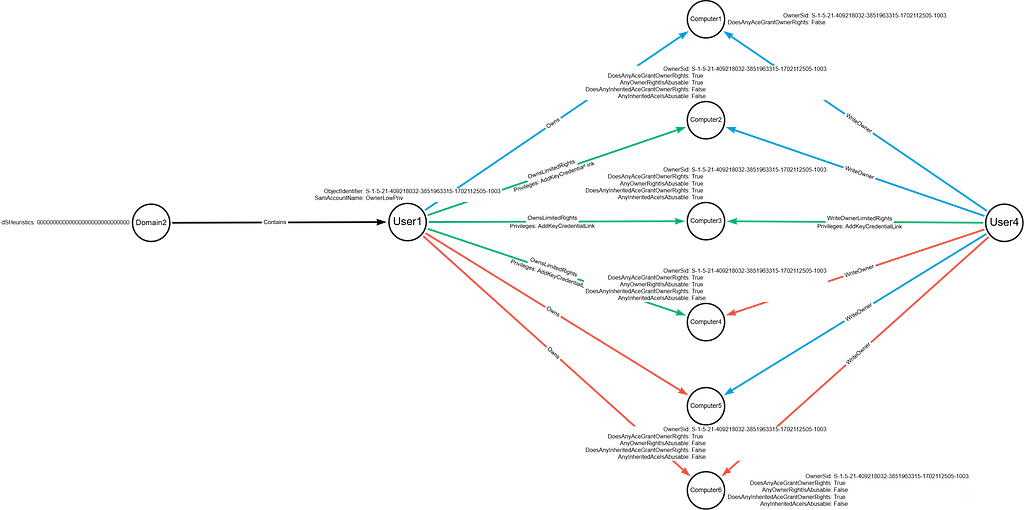
Do You Own Your Permissions, or Do Your Permissions Own You?
tl;dr: Less FPs for Owns/WriteOwner and new Owns/WriteOwnerLimitedRights edges Before we get started, if you’d prefer to listen to a 10-minute presentation instead of or to supplement reading this post, please check out the recording of our most recent BloodHound Release Recap webinar. You can also sign up for future webinars here. Back in August, a […]
Getting the Most Value Out of the OSCP: The PEN-200 Labs
How to leverage the PEN-200 simulated black-box penetration testing scenarios for maximal self-improvement and career success. Disclaimer: All opinions expressed in this article are solely my own. I have reviewed the content to ensure compliance with OffSec’s copyright policies and agreements. I have not been sponsored or incentivized in any way to recommend or oppose any […]