Manage Identity Risk
Measure and improve your identity security risk posture
Uncover all Identity Attack Paths and track your identity security risk posture in real-time. Prioritize your resources effectively and understand the impact of your remediation efforts as you remove Attack Paths.
Why Managing Identity Risk is Important
The complex relationships of users, systems, and privileges within Active Directory (AD) and Entra ID create an Identity Attack Path Risk that is invisible to built-in tooling. Without visibility over your Identity Risk, hundreds of thousands of Attack Paths will remain unseen, unmanaged, and will continue to grow.
-

Adversary’s Top Technique
Abusing identity privileges is the adversary’s favorite weapon. Reasonably skilled adversaries can use Identity Attack Paths to take over your enterprise within hours.
-
Making Blind Changes Is Dangerous
Small changes in Active Directory and Entra ID can massively increase the identity risk to your environment. You need visibility across the exposure of every change.
-
Attack Paths Keep Increasing
As business demands require changes to your Active Directory and Entra ID configurations, more and more hidden Attack Paths get inadvertently created.
Take back control with BloodHound Enterprise
BloodHound Enterprise provides real-time knowledge of your identity risk as your environment changes by performing continuous and comprehensive measurements of AD and Azure AD environments. With identity risk management, you can observe positive and negative trends in your identity security posture and empirically know the positive impact of removing Attack Paths.
Risk Baseline and Continuous Security Assessment
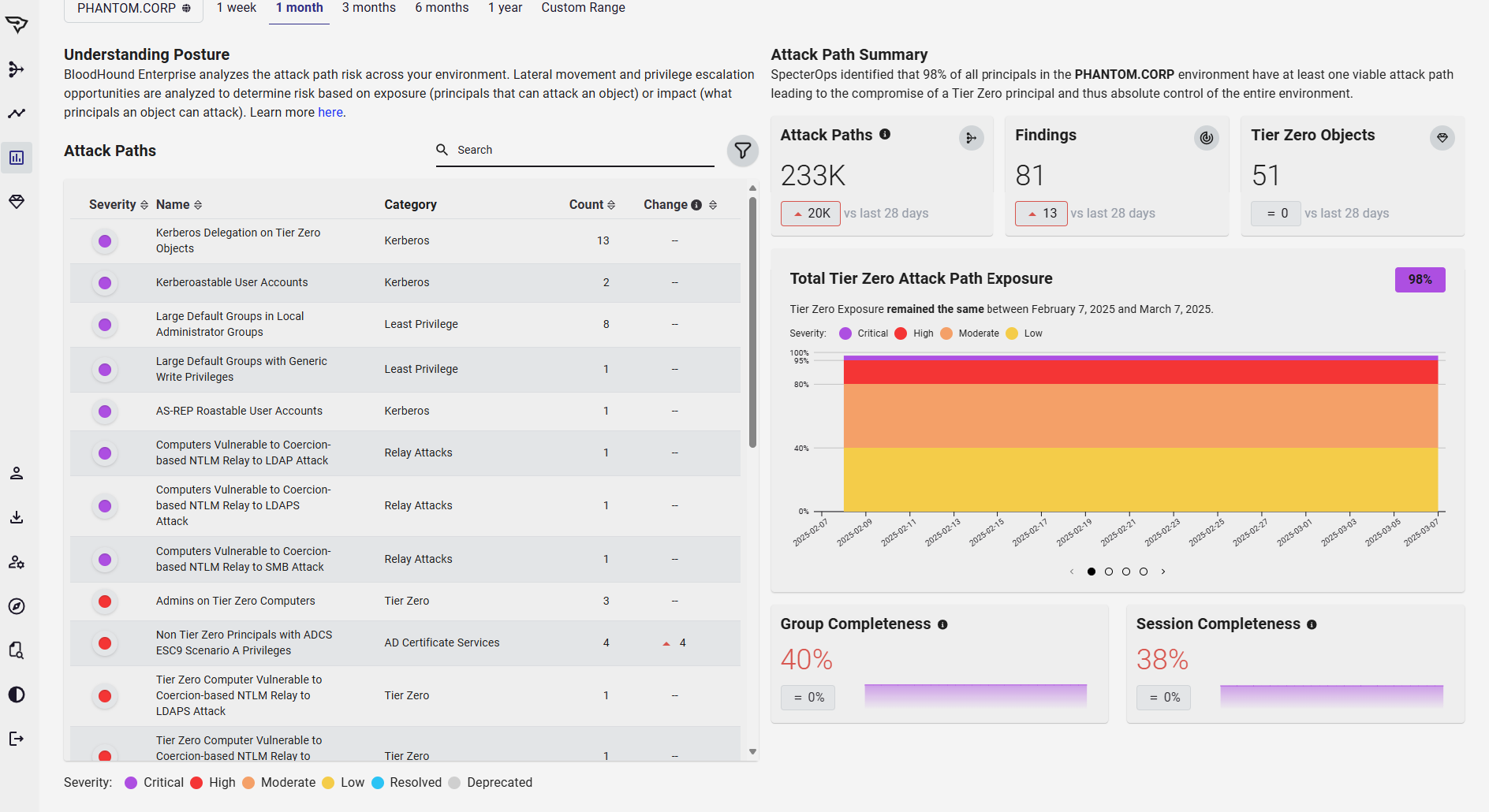
Identify Attack Path Risk
BloodHound Enterprise enumerates all Attack Paths within Active Directory and Entra ID to establish your Identity Risk Baseline.
As configuration changes are made (both good and bad), BloodHound automatically reassesses identity risk.
- Attack path mapping and measuring every Attack Path across your AD and Entra ID footprint
- Informs you immediately of the impact of any configuration changes
- Continuously presents your overall security posture and identity risk
SO Con Register
Sign up for SO-CON updates for the latest information:

Work Smart
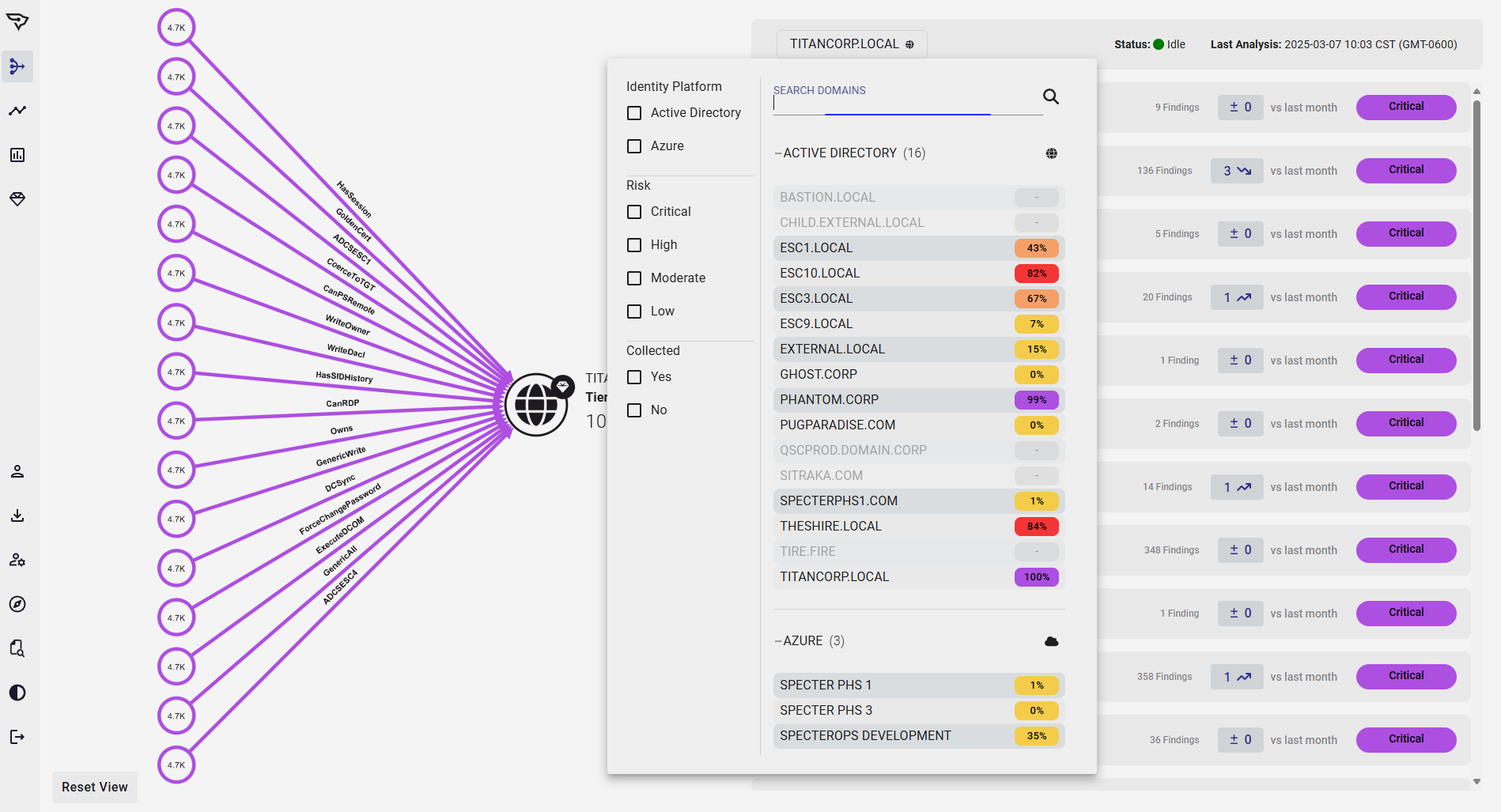
Deploy Security Choke Point Resources Confidently
Prioritized Attack Path Choke Points ensure your security team’s efforts will make the biggest impact.
- Immediately understand how changes made in one domain or tenant affect the enterprise
- Respond promptly to new high-risk Entra ID and Active Directory Attack Paths
- See your mitigation efforts pay off
SO Con Register
Sign up for SO-CON updates for the latest information:
Be Informed on Cybersecurity
Enterprise Identity Risk Reporting
Visualize and report on your identity risk across your entire enterprise (all domains & Azure tenants).
- Manage and report your Identity risk with confidence
- Monitor remediation for attack paths and track status over time
- Communicate the value of remediations and impact on security posture
Get a demo
SO Con Register
Sign up for SO-CON updates for the latest information: