Mergers and Acquisitions
Identify and mitigate risk before the merge
Assess the risks of an acquisition’s domain/tenant before establishing a trusted connection. Mitigate critical Identity Attack Paths to ensure new subsidiaries will not introduce risk to the organization.
The importance of knowing the risk of joining your acquisition to your domain or tenant
With every acquisition, security diligence is performed on endpoints, networks, and software before the acquired company is integrated. But traditional technologies don’t provide the ability to perform the most important assessment, understanding the Identity risk introduced by joining organizations.
-

Adversary’s Target Your Acquisitions
Adversaries target acquired organizations to compromise the new parent org, the risk to the child becomes risk to the parent.
-

Making Blind Changes Is Dangerous
Whether making a small configuration change or performing a large domain/forest trust change, you do so without understanding the exposure that you will create in your environment.
-

Stalled Mergers
Lack of visibility into the risk of the merger causes delays and harms the business objectives of the acquisition.
Take back control with BloodHound Enterprise
BloodHound Enterprise removes uncertainty and allows organizations to manage the risk of acquisitions for the first time.
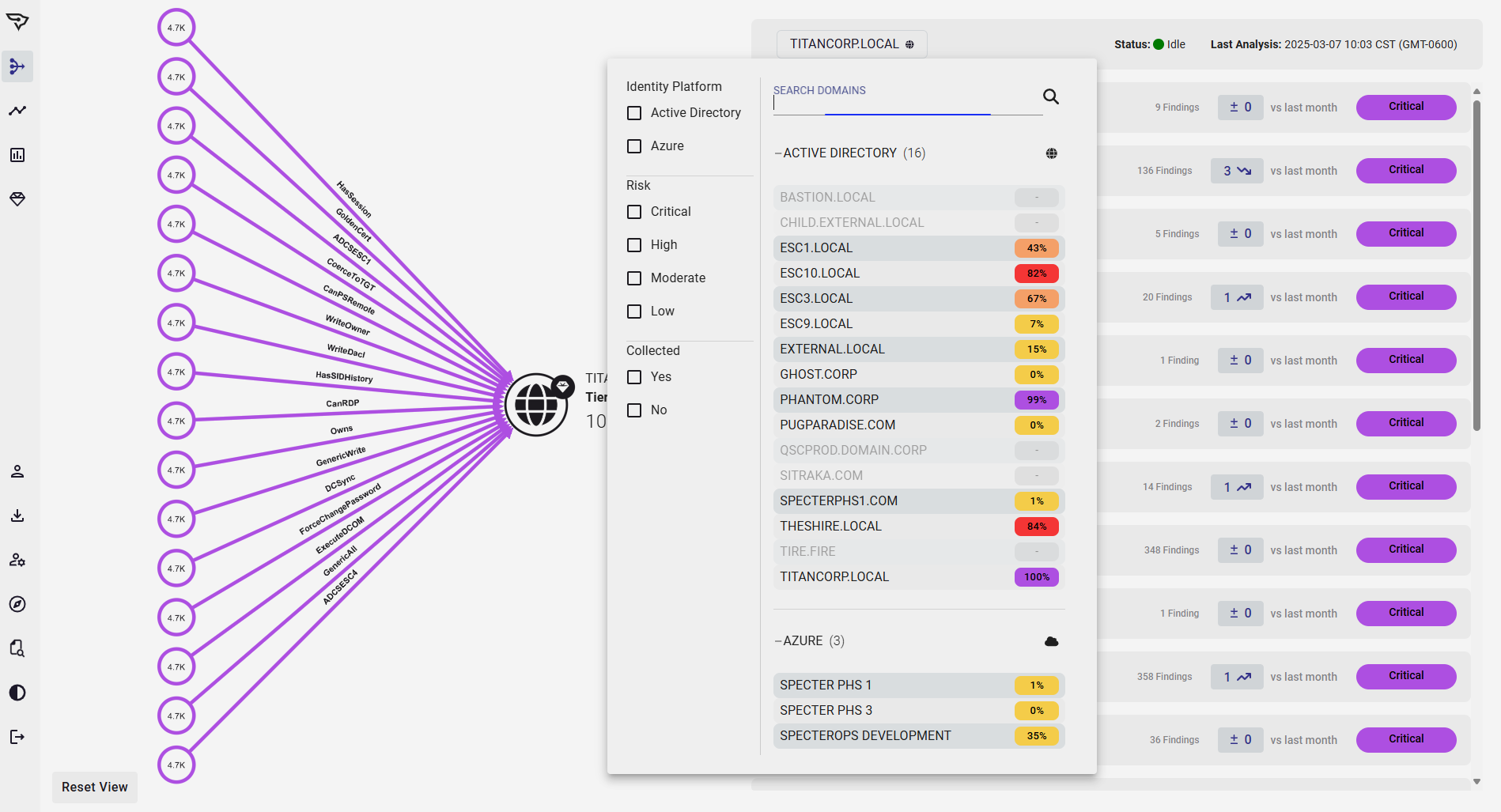
Assess Attack Path Risk
Quantify Acquisition Exposure
BloodHound Enterprise allows organizations to fully assess the identity security posture of the acquired company:
- Maps every relationship and connection into Attack Paths
- Measures the initial impact of each point of each Attack Path
- Presents a baseline of their overall Identity security risk
SO Con Register
Sign up for SO-CON updates for the latest information:
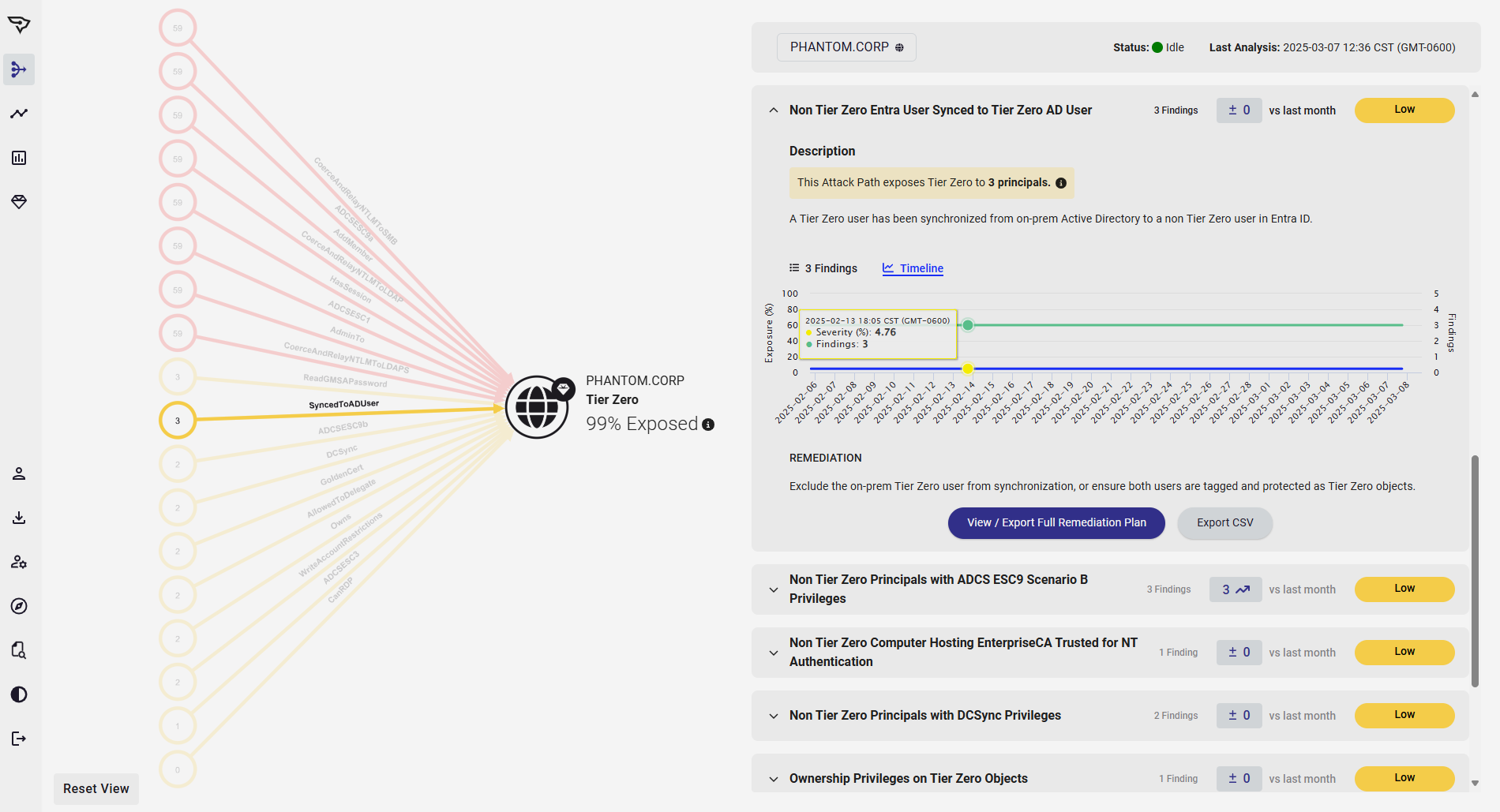
Mitigate & Manage Risk
Eliminate Critical Attack Paths
BloodHound Enterprise identifies the strategic Choke Points to eliminate high-risk Attack Paths and provides remediation guidance to help fast and safe mitigation efforts.
- Pinpoint Choke Points to cut many Attack Paths at once
- Prioritize Choke Points by risk exposure to identify high impact, low effort wins
- Move fast with practical and precise remediation guidance
SO Con Register
Sign up for SO-CON updates for the latest information:
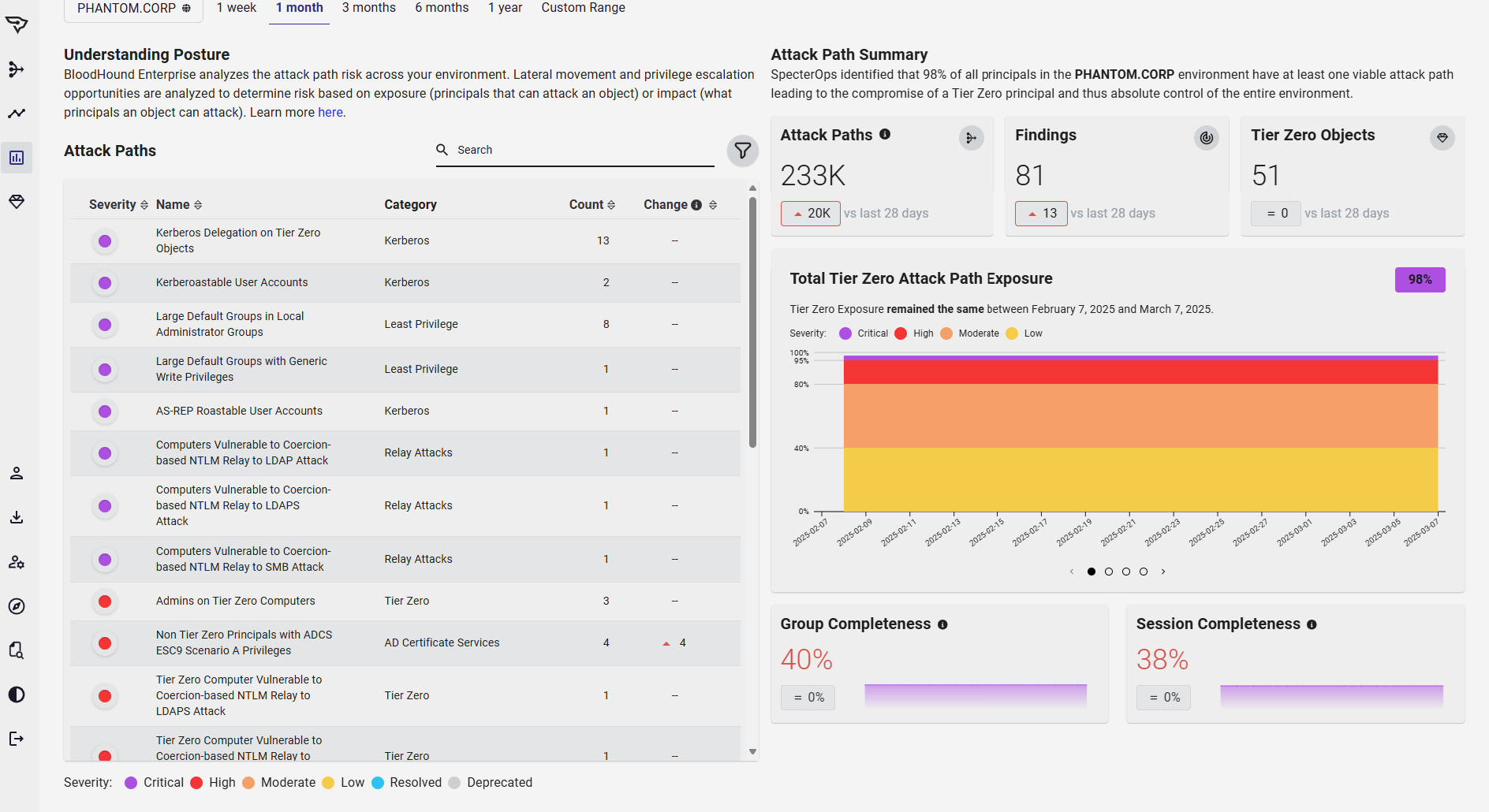
Forcing Function
Enterprise Class Reporting
BloodHound Enterprise can be used by the acquiring company as a forcing function for consistency and onboarding to ensure that the inevitable connection of domains is one of low risk.
- Understand risks before you establish trust with a new domain or tenant
- Enterprise-wide visibility in minutes
- Prioritized Attack Path Choke Points to mitigate the highest risk violations quickly.
Get a demo
SO Con Register
Sign up for SO-CON updates for the latest information: