LudusHound: Raising BloodHound Attack Paths to Life
TL;DR LudusHound is a tool for red and blue teams that transforms BloodHound data into a fully functional, Active Directory replica environment via the Ludus framework for controlled testing. This tool can be used to replicate most AD objects and permissions or can be used to replicate a specific Attack Path. Full credit to this […]
Privilege Zones: BloodHound Enterprise spreading like a computer virus (of security)
TL;DR The BloodHound Enterprise team recently pushed out Privilege Zones, one of the most requested features from our clients. Here’s a brief overview of how it expands (literally) the capabilities of BloodHound Enterprise. A couple of years ago, I wrote a blog post explaining the basic functionality of BloodHound Enterprise: what it does, how it […]
Machine Learning Series Chapter 1
MICROGRAD FOR MORTALS TL;DR Let’s use Micrograd to explain core ML concepts like supervised learning, regression, classification, loss functions, and gradient descent. We’ll break down how models adjust weights and biases during training using backpropagation. Through simple code examples, it visualizing how gradients flow through a minimalistic neural network. Intro This article deviates from the […]
Requesting Entra ID Tokens with Entra ID SSO Cookies
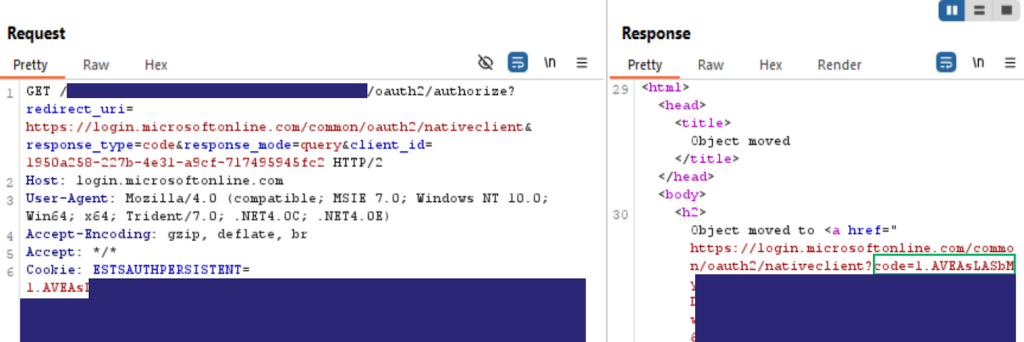
TL;DR This post explains how to request OAuth tokens and enumerate an Entra ID tenant by using an SSO cookie from a non cloud-joined device. Introduction In this post, I’m going to cover a method for requesting Entra ID access tokens using a browser Single Sign-On (SSO) cookie. This is especially useful in scenarios where […]
Misconfiguration Manager: Still Overlooked, Still Overprivileged
TL;DR It has been one year since Misconfiguration Manager’s release and the security community has been hard at work researching new tradecraft and identifying new attack paths. Here we summarize everything that we (the community) have done over the past year and the impact it’s making on the state of SCCM security. Introduction In 2024, […]
Good Fences Make Good Neighbors: New AD Trusts Attack Paths in BloodHound
TL;DR The ability of an attacker controlling one domain to compromise another through an Active Directory (AD) trust depends on the trust type and configuration. To better map these relationships and make it easier to identify cross-domain attack paths, we are replacing the TrustedBy edge in BloodHound with new trust edges. We are also improving […]
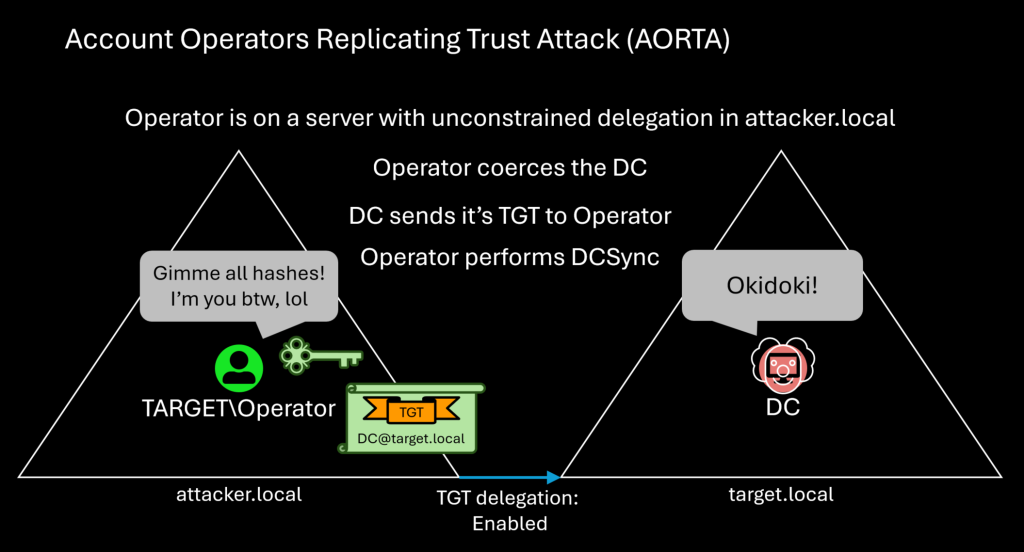
Untrustworthy Trust Builders: Account Operators Replicating Trust Attack (AORTA)
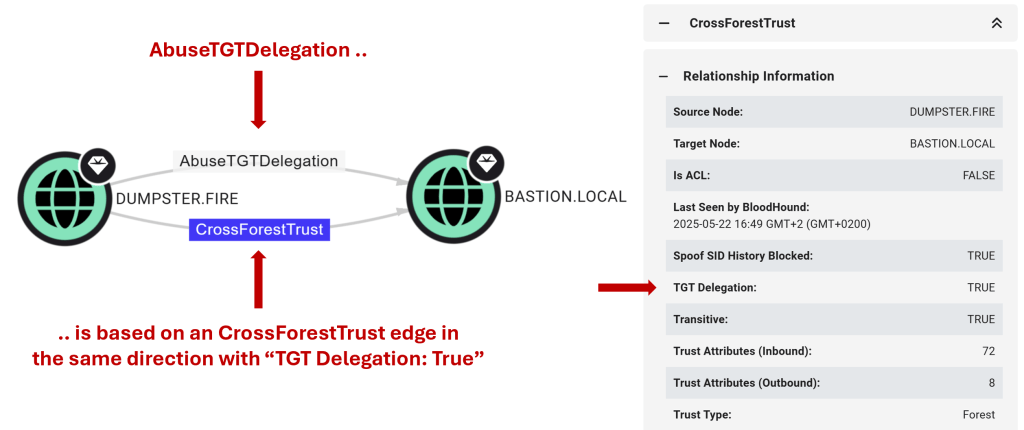
TL;DR The Incoming Forest Trust Builders group (not AdminSDHolder protected) can create inbound forest trusts with ticket-granting ticket (TGT) delegation enabled. This configuration causes servers to send their TGT across the trust when coerced to authenticate to a computer with unconstrained delegation. An attacker can abuse this by creating a trust to a fake domain, […]
Lost in Translation: How L33tspeak Might Throw Sentiment Analysis Models for a Loop
TL;DR Sentiment analysis models are used to assess conventional use of language, but what happens when you engage with them using l33tspeak? If you’ve been in the security space for some time, you may be familiar with l33tspeak, or 1337, where you replace letters with visually similar words or symbols that resemble the original letters. […]
LLMentary, My Dear Claude: Prompt Engineering an LLM to Perform Word-to-Markdown Conversion for Templated Content
While LLMs can expedite parts of the technical writing/editing process, these tools still require human oversight and guidance to provide an accurate and helpful response.
Ghostwriter v6: Introducing Collaborative Editing
TL;DR: Ghostwriter now supports real-time collaborative editing for observations, findings, and report fields using the YJS framework, Tiptap editor, and Hocuspocus server, enabling multiple users to edit simultaneously without overwriting each other. This feature integrates seamlessly with Ghostwriter’s existing GraphQL API and infrastructure while introducing modern frontend tooling, React-based components, and upgrades to Django, PostgreSQL, […]