LLMentary, My Dear Claude: Prompt Engineering an LLM to Perform Word-to-Markdown Conversion for Templated Content
While LLMs can expedite parts of the technical writing/editing process, these tools still require human oversight and guidance to provide an accurate and helpful response.
Ghostwriter v6: Introducing Collaborative Editing
TL;DR: Ghostwriter now supports real-time collaborative editing for observations, findings, and report fields using the YJS framework, Tiptap editor, and Hocuspocus server, enabling multiple users to edit simultaneously without overwriting each other. This feature integrates seamlessly with Ghostwriter’s existing GraphQL API and infrastructure while introducing modern frontend tooling, React-based components, and upgrades to Django, PostgreSQL, […]
Administrator Protection Review
TL;DR Microsoft will be introducing Administrator Protection into Windows 11, so I wanted to have an understanding of how this technology works and how it interacts with existing offensive tooling. While this technology is just a thin wrapper around a separate account, there are a few nuances such as who is permitted to access these […]
Introducing the BloodHound Query Library
TL;DR The BloodHound Query Library is a community-driven collection of Cypher queries designed to help BloodHound Community Edition and BloodHound Enterprise users to unlock the full potential of the flexible BloodHound platform by creating an open query ecosystem. The library is a free tool for the community and you can start using it today at […]
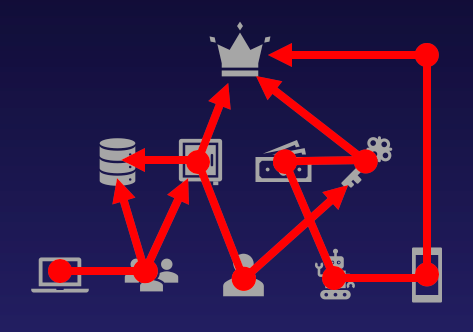
Making Least Privilege Real: Previewing Privilege Zones in BloodHound Enterprise
TL;DR Most organizations assume they’ve implemented least privilege, but assumptions don’t stop attackers. Privilege Zones in BloodHound Enterprise lets you define and analyze real-world security boundaries to stop lateral movement and eliminate attack paths across hybrid environments. Organizations assume they have clear privilege boundaries, but those assumptions rarely match reality. Attack paths exist precisely because […]
OneLogin, Many Issues: How I Pivoted from a Trial Tenant to Compromising Customer Signing Keys
TL;DR OneLogin was found to have security vulnerabilities in its AD Connector service that exposed authentication credentials and enabled account impersonation. This research showed that attackers could access credentials and signing keys to generate valid JWT tokens, allowing user impersonation. Leaked AWS credentials allowed SpecterOps to register an unclaimed S3 bucket referenced in the OneLogin […]
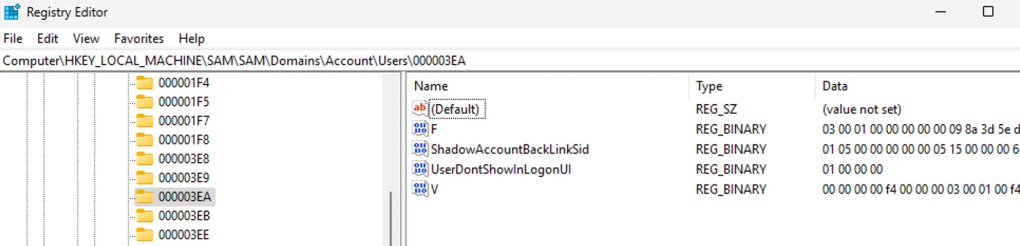
Update: Dumping Entra Connect Sync Credentials
TL;DR Microsoft has recently changed how Entra Connect Sync authenticates to Entra ID. This blog post will discuss what has been changed and how to adjust attacker tradecraft. Recently, Microsoft changed the way the Entra Connect Connect Sync agent authenticates to Entra ID. These changes affect attacker tradecraft, as we can no longer export the […]
Chatting with Your Attack Paths: An MCP for BloodHound
TL;DR In an effort to learn about Model Context Protocol servers, I created a MCP server that allows Claude Desktop to access and analyze data contained with a running instance of BloodHound Community Edition. This MCP is recommended to be used with Lab or Example data. Future releases will have Local LLM support. Introduction During […]
TL;DR Tokenization Confusion: We look at the new Prompt Guard 2 model from Meta, how “confusing” Unigram tokenization can lead to misclassification of malicious prompts, and why building up our ML knowledge will lead to better findings when assessing LLM API’s. Recently, upon getting ready to board a flight across the Atlantic, I was deciding […]
Getting the Most Value Out of the OSCP: After the Exam
TL;DR In the final post of this series, I’ll discuss what to do after your latest exam attempt to get the most value out of your OSCP journey. Introduction Throughout this series, I’ve shared practical advice for PEN-200: Penetration Testing with Kali Linux students seeking to maximize the professional, educational, and financial value of pursuing […]