Ghostwriter v4.3: SSO, JSON Fields, and Reporting with BloodHound


Ghostwriter v4.3 is available now, and it enhances features introduced in previous versions of v4 in some exciting ways! In particular, this article will dive into how you can integrate a tool like BloodHound Community Edition (BHCE) with Ghostwriter v4.3.
First, we would be remiss if we did not mention the refreshed single sign-on (SSO) feature.
Refreshed Single Sign-On
Ghostwriter has supported SSO for quite some time, but it’s a feature that always required extra effort that made implementation difficult. The steps to enable SSO were unique to each provider and required making changes to configurations you don’t normally touch, so we did not have much documentation. You may not have known it was an option!
That all changes with v4.3.0. The wiki has a new Access, Authentication, and Session Controls section that covers everything in this realm. It’s worth a review for new or current Ghostwriter administrators because we’ve added new documentation for SSO and expanded information around user session management features released earlier this year with v4.0.
Access, Authentication, & Session Controls | Ghostwriter
Once you have an SSO provider configured, you’ll see your provider(s) available on the login page.
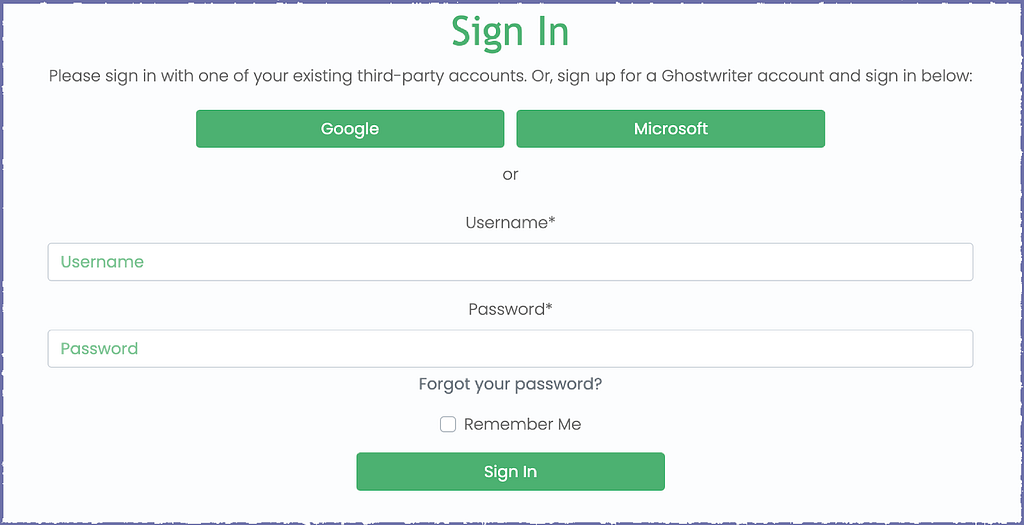
To support SSO, we added support for custom config files. Previously, to add an SSO configuration, you had to edit config files tracked in the Ghostwriter repository; this meant admins would have to stash and re-apply any customizations or changes before updating a Ghostwriter server. Ghostwriter v4.3 allows customization of your Ghostwriter server without worrying about a lost configuration. This support for custom configuration values mainly applies to SSO configuration, but you can use it for other configuration values — e.g., adding a Django application to your Ghostwriter installation or customizing an email backend configuration.
Introducing JSON to Custom Fields
Let’s dive into an even meatier topic with some extensive possibilities. Ghostwriter v4.1 introduced the capability of adding extra fields to most Ghostwriter objects (e.g., reports, projects, clients). That initial feature release supported strings, rich text fields, numbers, and boolean values. This release adds support for a JSON field type.
You can now add a field to hold a JSON blob. Whatever JSON you provide will be available to your reports. You can take JSON output from an assessment tool, provide it to Ghostwriter, and create a report with that data!
Various tools will output results as JSON or XML. If your tool can’t output JSON but does support XML, like nmap, you can easily convert the XML to JSON using a few lines of Python and xmltodict. One tool that works very well with this new feature is BHCE!
Here is an example of a custom SharpHound Data field added to a report with an example of BHCE data. You can view and explore the JSON in Ghostwriter with collapsible nodes.
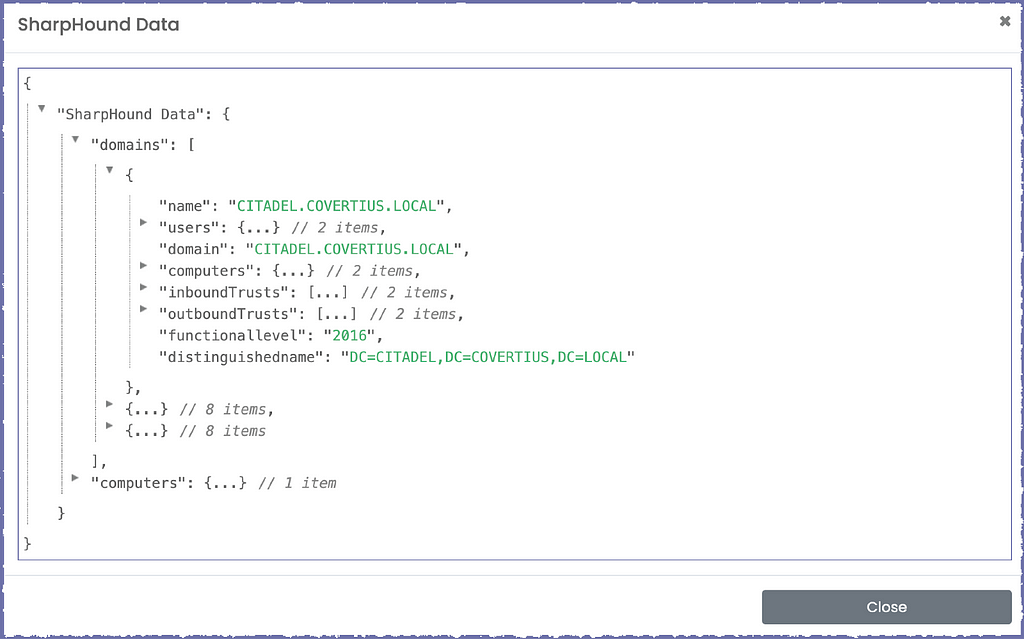
Case Study: Integrating BloodHound CE With Ghostwriter
BHCE’s data is already available as JSON, but the JSON files are typically large for most Active Directory (AD) environments outside of a lab environment. Also, the data’s full value comes from your analysis, so feeding the raw JSON to Ghostwriter isn’t the way to go. No one wants to copy and paste the contents of a dozen JSON files into fields anyway. We can leverage BHCE and Ghostwriter’s robust APIs to perform analysis and automatically pass the JSON to Ghostwriter.
For this case study, we’ll focus on extracting some AD domain data from the BHCE data loaded on our server and performing some fundamental analysis. We’ll also have a JSON field added to our Ghostwriter reports to hold the final output for reporting. If you want to follow along with this POC after updating your Ghostwriter server, you can find details in the GitHub repository linked below.
We can use some Python and BHCE’s API to get a list of all collected domains and extract some of their properties (e.g., name, functional level), information about trusts, and basic information about users and computers. All of this is available with BHCE’s built-in API endpoints, but the API also supports running custom Cypher queries.
We’ll perform some analysis by running queries to pull all the operating systems for computers in each domain and checking the pwdlastset property on all the users to count how many have passwords older than 90 days. Finally, we’ll count how many users have an old password and how many systems are running each unique operating system within each domain and globally for the collection.
When that analysis is complete, our script will assemble the data into a nicely formatted JSON blob and update our report field via Ghostwriter’s API.
The full proof-of-concept is available here:
The script performs the following actions:
- Authenticates to a BloodHound server
- Pulls all domains with the available-domains endpoint
- Collects properties for each domain from the domains/{DomainID} endpoint
- Gathers information about trusts from the domains/{DomainID}/inbound-trusts and outbound-trusts endpoints
- Executes the two Cypher queries shown below
- Constructs the final JSON structure
- Connects to a Ghostwriter server
- Updates a report with the BHCE JSON
# Return all computers for a given domain
MATCH (n:Computer) WHERE n.domain = "{domain}" RETURN n
# Return all users with a password last set date older than 90 days
MATCH (u:User) WHERE u.pwdlastset < (datetime().epochseconds - (90 * 86400)) and NOT u.pwdlastset IN [-1.0, 0.0] and u.domain = "{domain}" RETURN u
Now that we have our JSON structure and Ghostwriter has the data, we can build a report template that uses it. We can use the data in two ways.
We can leverage the support for Jinja2 templating inside rich text fields that we added in Ghostwriter v4.2. For this example, we will generate a list of our AD domains with some user statistics and then a table with the domains alongside information about their trusts, all of which will be inserted into our report later.
We can access the JSON data like the other objects in the report context you’re probably already familiar with. We build the list and table rows using some for loops. If you’re new to Jinja2, the syntax is akin to Python. The Ghostwriter Wiki has sections that introduce the basics.
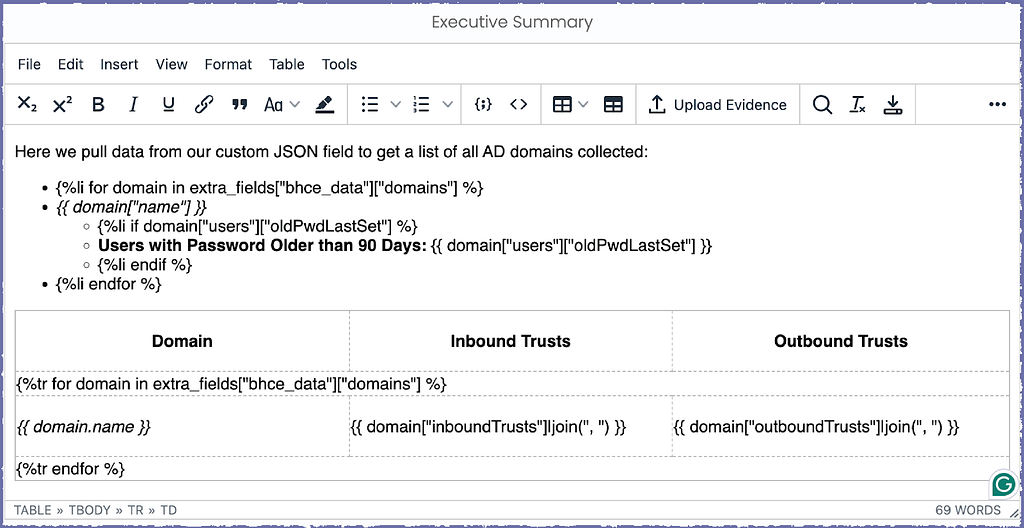
We can do this inside a report template, too. Here is what that looks like for a table of collected operating systems.
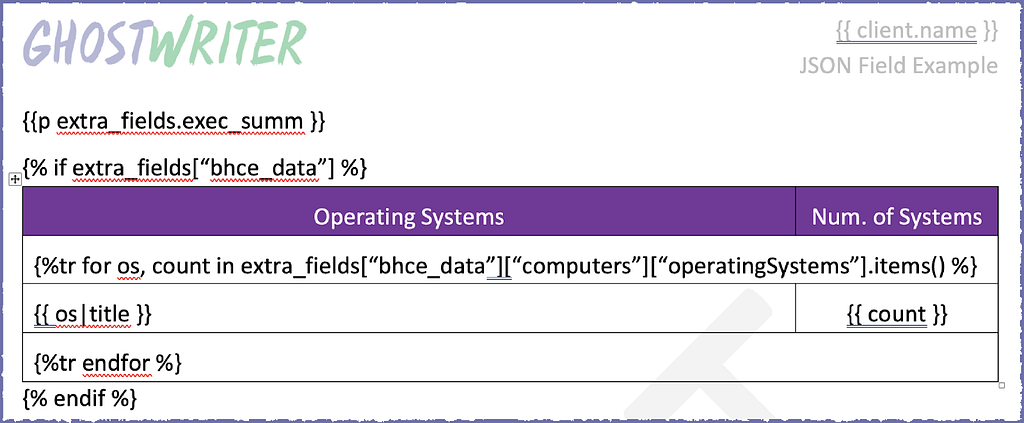
The first line pulls in the rich text field with our list and table of domain information. Then we build a table by looping over the operating system statistics in our JSON data.
With that done, we can upload our template and generate a report with it. The final output looks like this. You can find this report template in the GitHub repository if you’d like to experiment with it.
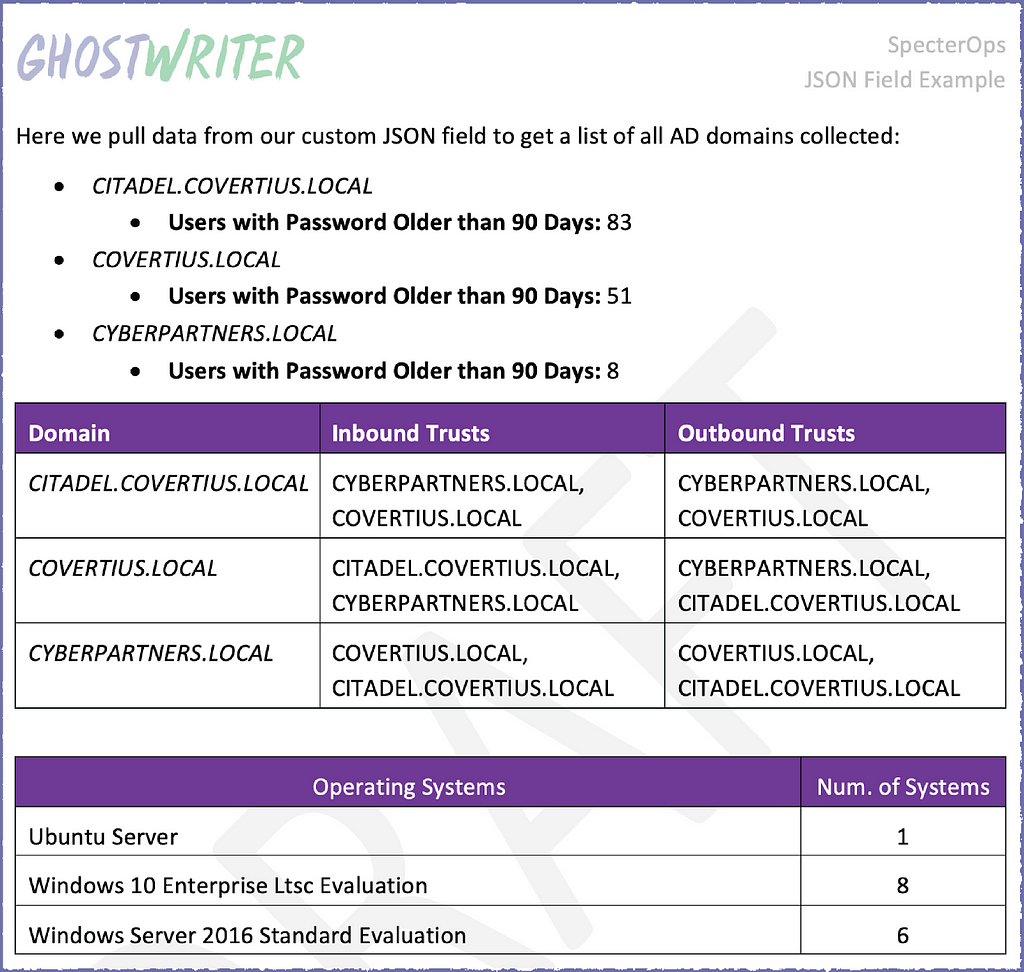
This example doesn’t necessarily include the sort of data you want to include in a report, but it should give you an idea of what is possible when you pull external data into Ghostwriter. We hope to see some creative uses of the JSON fields. If you haven’t experimented with the BloodHound API, this is a great way to start!
For more inspiration, check out the BloodHound password analysis case study we published in 2019. We did this work before the API existed, but the API would have been a fantastic aid. We also could have done all the reporting with Ghostwriter, as described here.
Case Study: Password Analysis with BloodHound
You can find the full Ghostwriter v4.3 CHANGELOG and release here:
Release Ghostwriter v4.3.0 · GhostManager/Ghostwriter
Ghostwriter v4.3: SSO, JSON Fields, and Reporting with BloodHound was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.


