Unwrapping BloodHound v6.3 with Impact Analysis
Dec 12 2024
By: Justin Kohler • 6 min read
Just in time for the holidays, sharper tools for faster defense
Today, the SpecterOps team rolled out a number of new features, product enhancements, and recommendations intended to help users of BloodHound Enterprise and BloodHound Community Edition more easily visualize attack paths and show improvements in identity risk reduction over time. Scroll down to learn more about v6.3.0 and related changes to BloodHound Enterprise and BloodHound Community Edition.
BloodHound Enterprise Updates
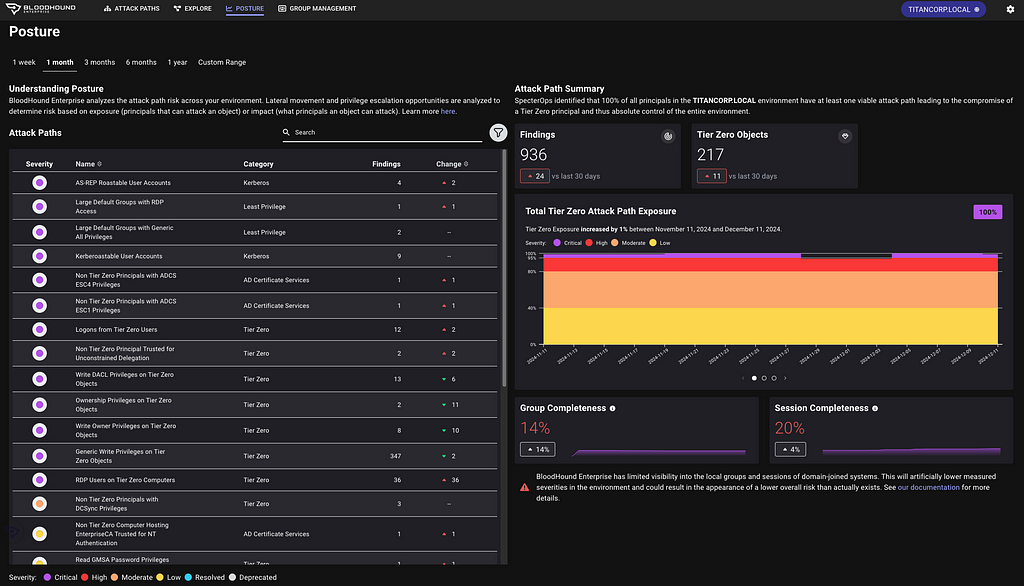
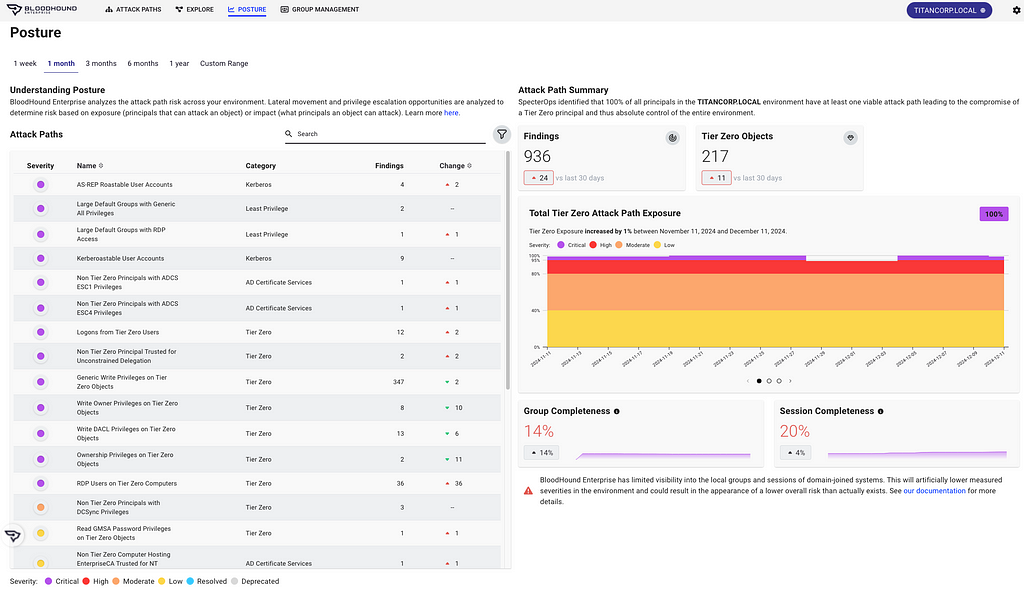
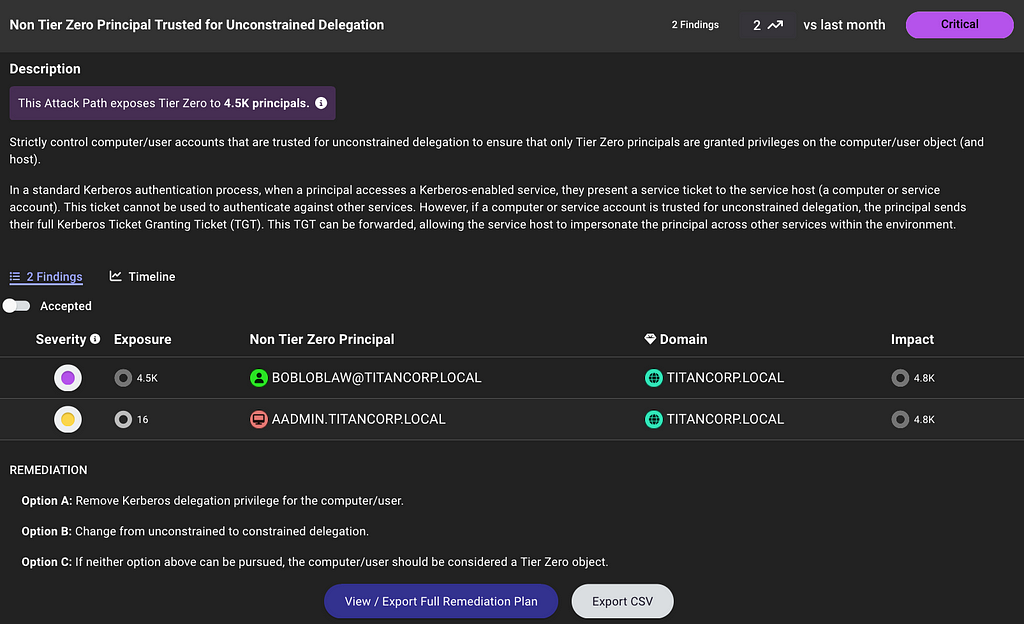
Report on attack path risk with Revamped Posture page
The BloodHound Enterprise team has completely redesigned the Posture page, delivering several significant enhancements:
- Enhanced visibility into resolved attack paths
- New metrics to track remediation progress over time
- New filter and search capabilities to highlight specific improvements
- Consolidated view of relevant data into a single page, reducing unnecessary scrolling
Improved Analysis Algorithm
This is a massive upgrade to BloodHound Enterprise’s risk analysis capability with a new algorithm we call “Butterfly”:
- Enhanced risk scoring with “Impact” analysis
- Granular risk measurement per finding for better prioritization
- Support for hybrid attack path risk analysis
Let’s get more specific with the first two bullets; Enhanced risk scoring and better prioritization.
Enhanced risk scoring with “Impact” analysis
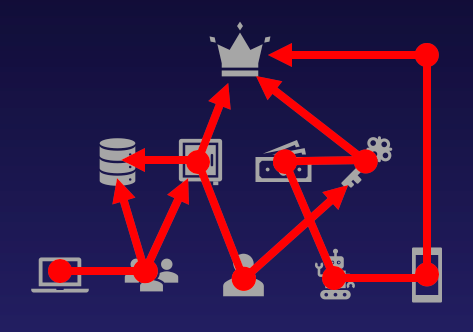
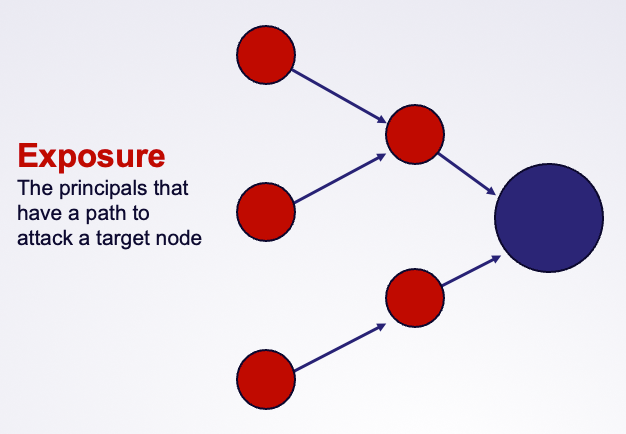
BloodHound Enterprise has historically assessed the risk of attack paths by modeling the principals that can target specific identities and resources:
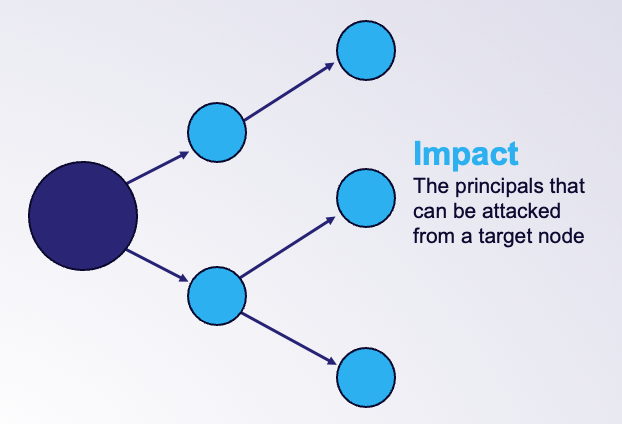
Starting with v6.3, BloodHound will also incorporate Impact analysis — the principals that can be attacked by a target node:
This new bi-directional risk analysis significantly improves BloodHound Enterprise capabilities in determining severity for attack paths:
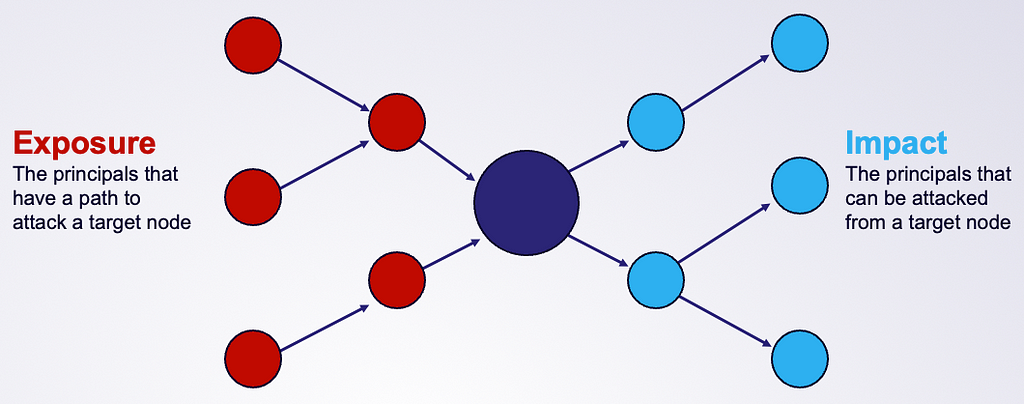
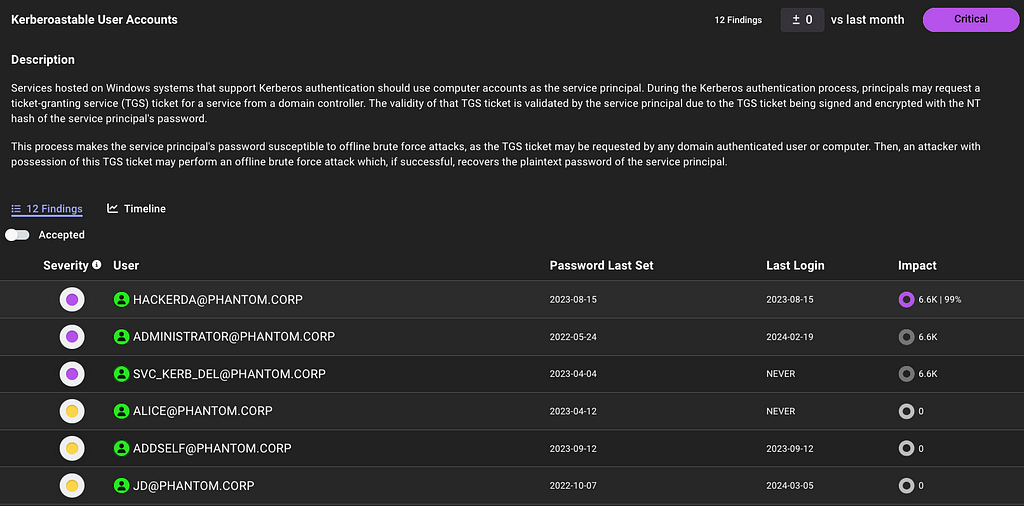
For example, here is the improved analysis in action with Kerberoastable Users:
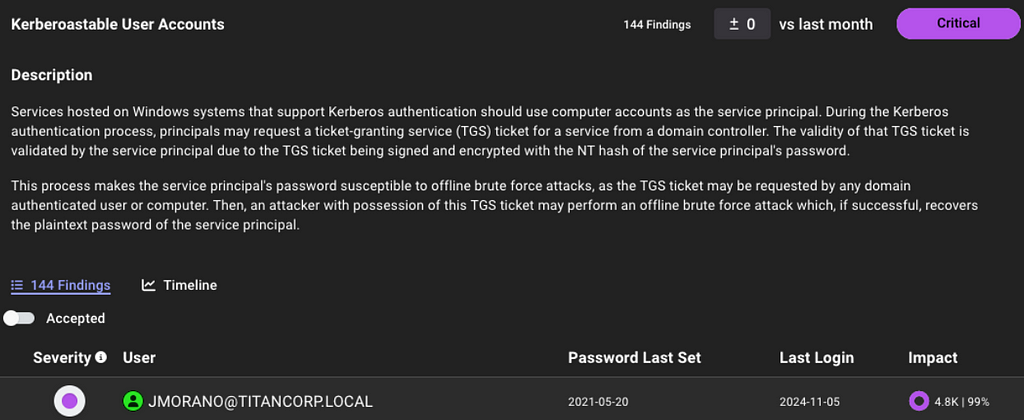
A quick refresher on Kerberoast attack: A Kerberoast attack exploits the Kerberos authentication protocol by targeting service account passwords in a Windows Active Directory environment. An attacker requests Kerberos service tickets for Service Principal Names (SPNs), extracts them, and performs offline password cracking since the tickets are encrypted with the service account’s NTLM hash. If successful, the attacker gains the plaintext service account credentials, which can be used for lateral movement or privilege escalation.
Anyone can request the service ticket for a kerberoastable account which means the exposure is always 100%. The risk of this finding is what an attacker could do with access to that account with a successful crack. Therefore, the risk is determined by the impact; or what can be attacked once the attacker has control of the account.
Granular risk measurement per finding for better prioritization
BloodHound Enterprise delivers better prioritization by analyzing risk per finding with v6.3. Historically, risk was calculated per attack path type:
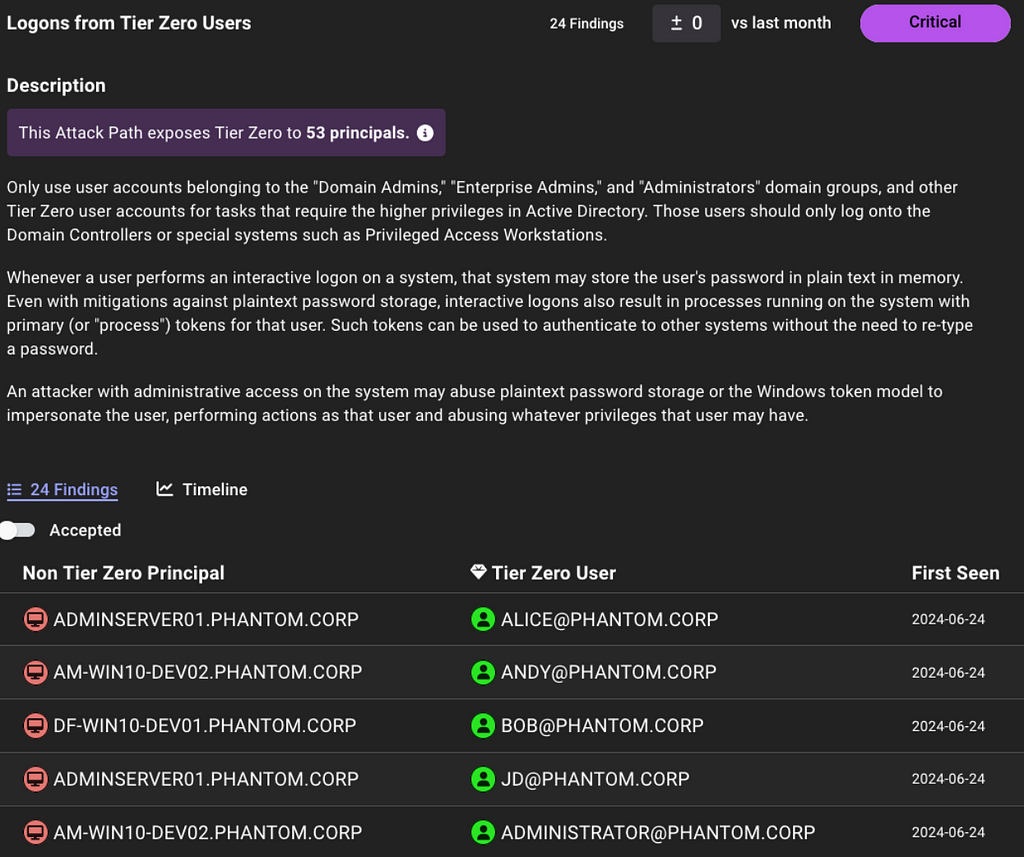
Now, BloodHound Enterprise will assess the risk of every finding, allowing you to pinpoint where to start first:
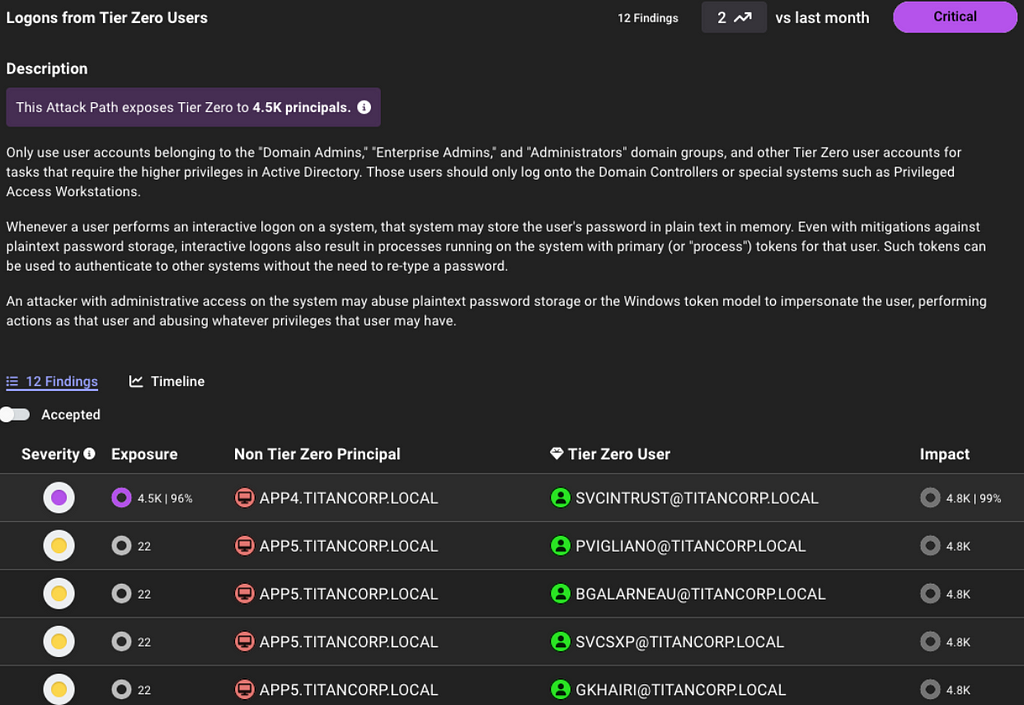
In the example above, one particular login is more risky than the others and should be prioritized. BloodHound Enterprise is simplifying the analysis for you to enable better prioritization. In this case, APP4.TITANCORP.LOCAL is prioritized above the rest as DOMAIN USERS has the ability to RDP into the host and capture the user session:
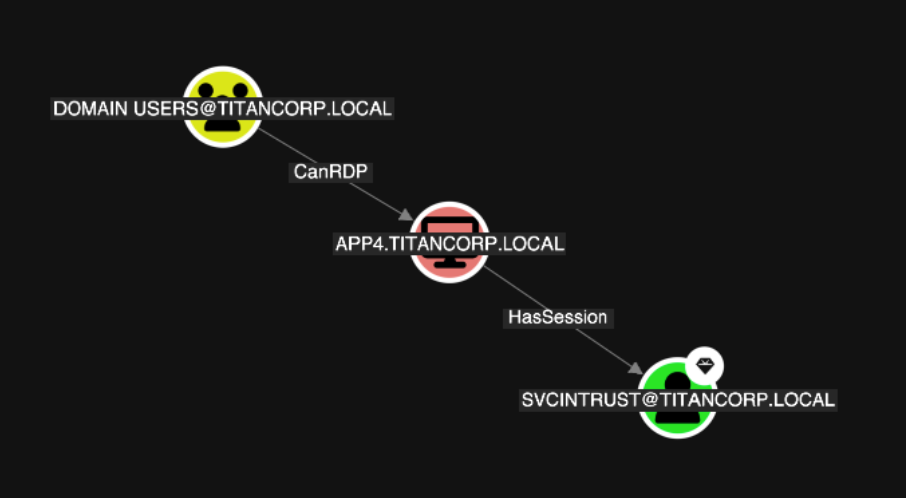
This granularity is on every finding. Let’s look again at a large list of Kerberoastable users. Thanks to this improvement, we now know where to prioritize our efforts:
BloodHound Common Updates
All enhancements listed below are available to both BloodHound Community and BloodHound Enterprise users.
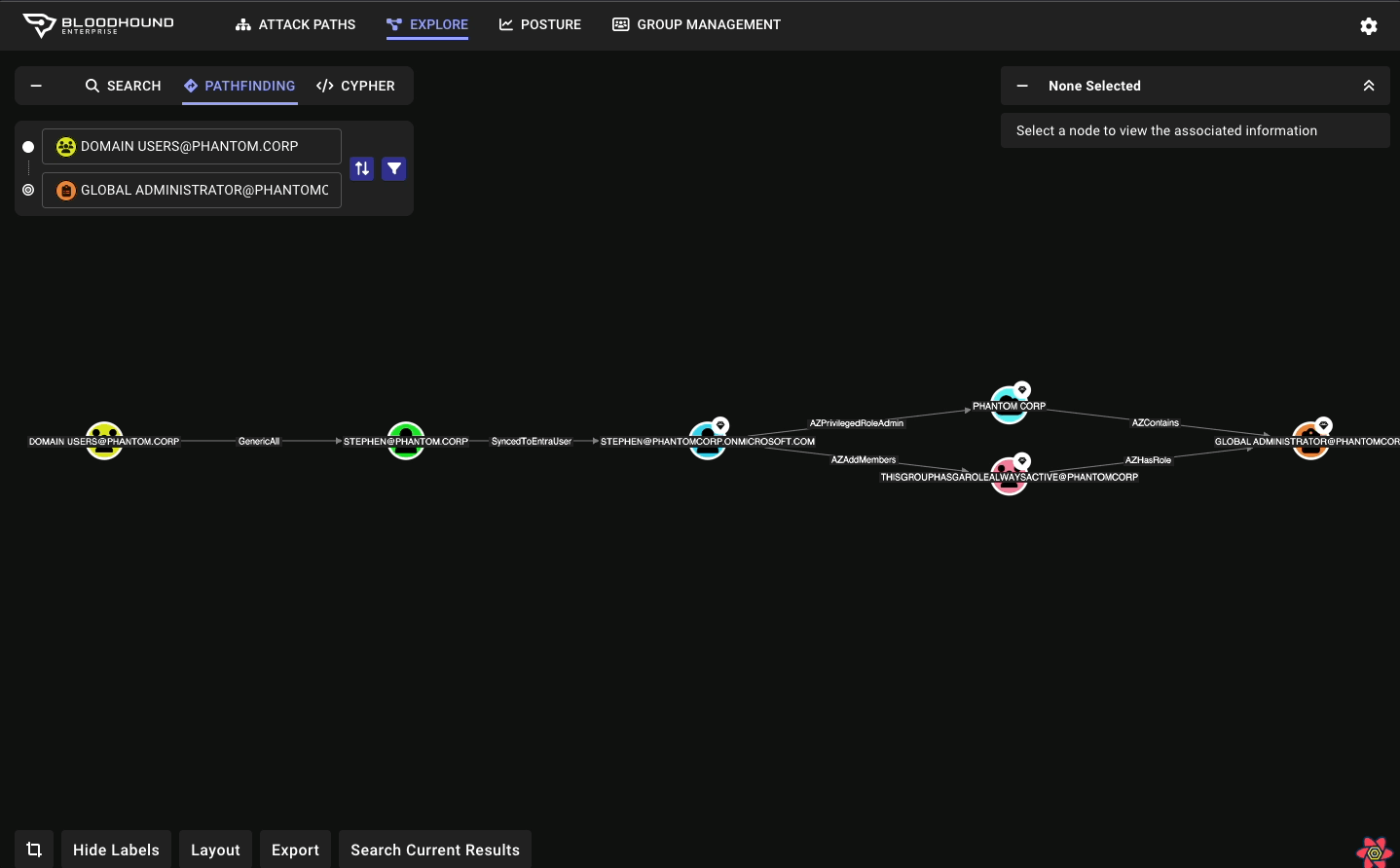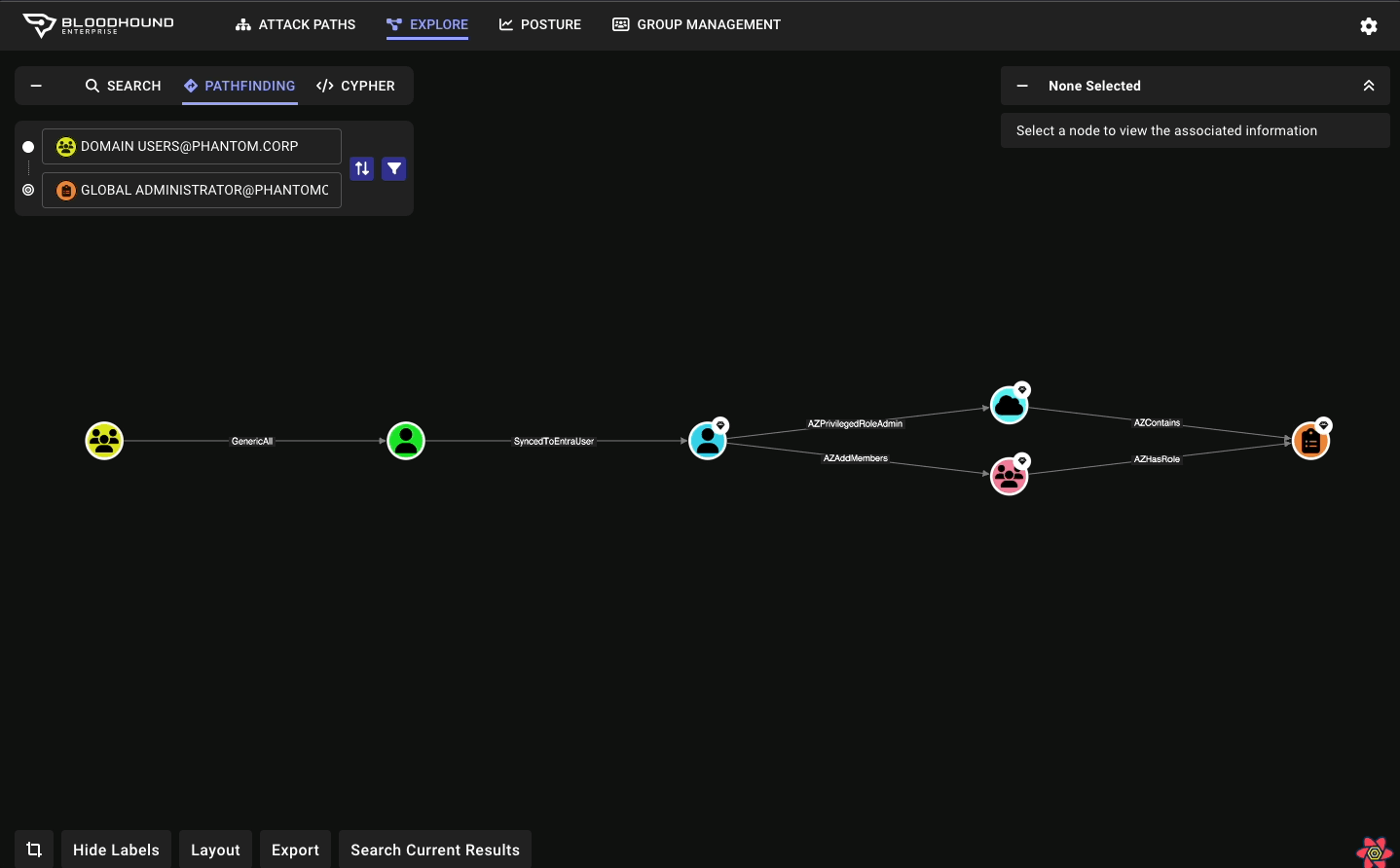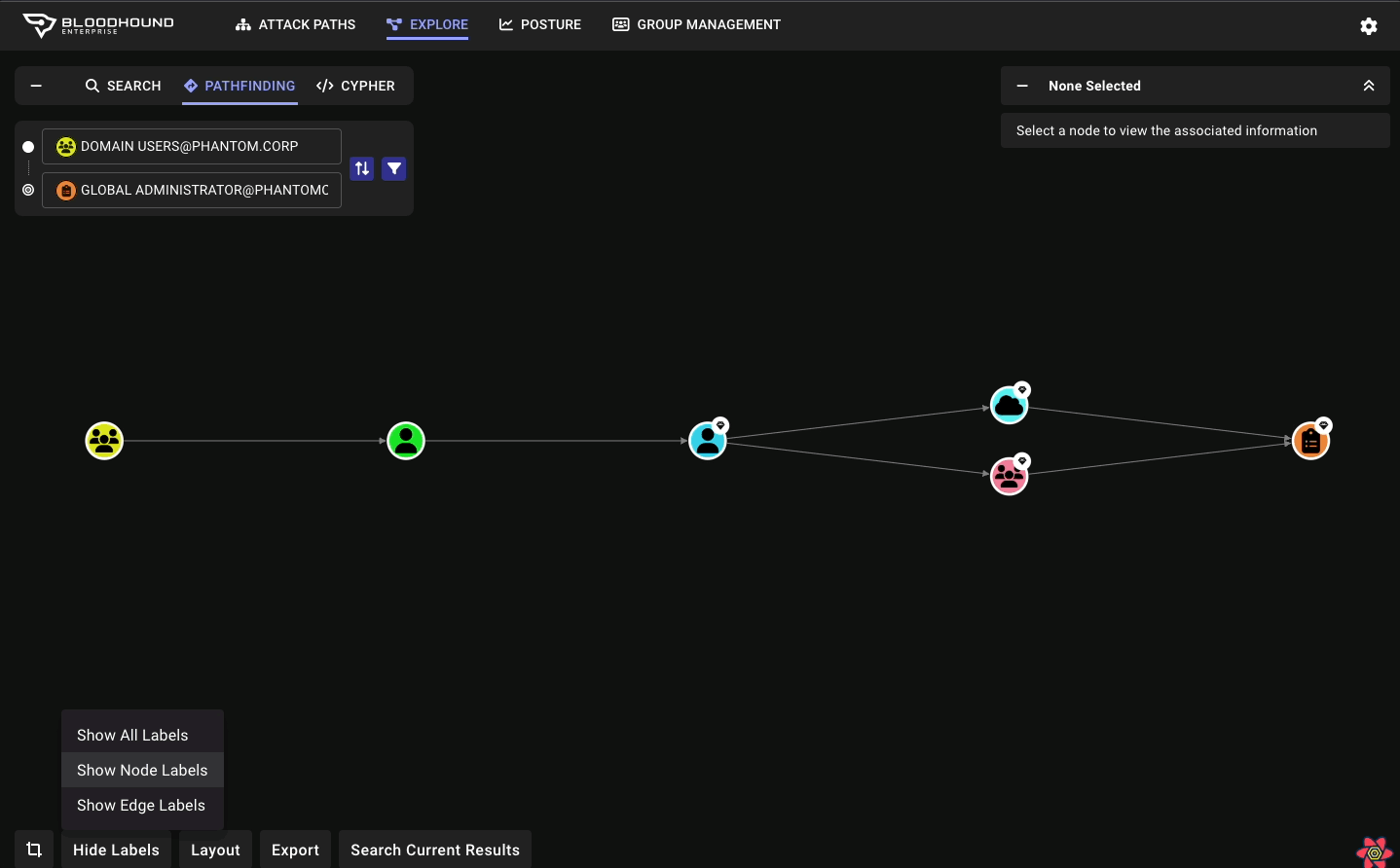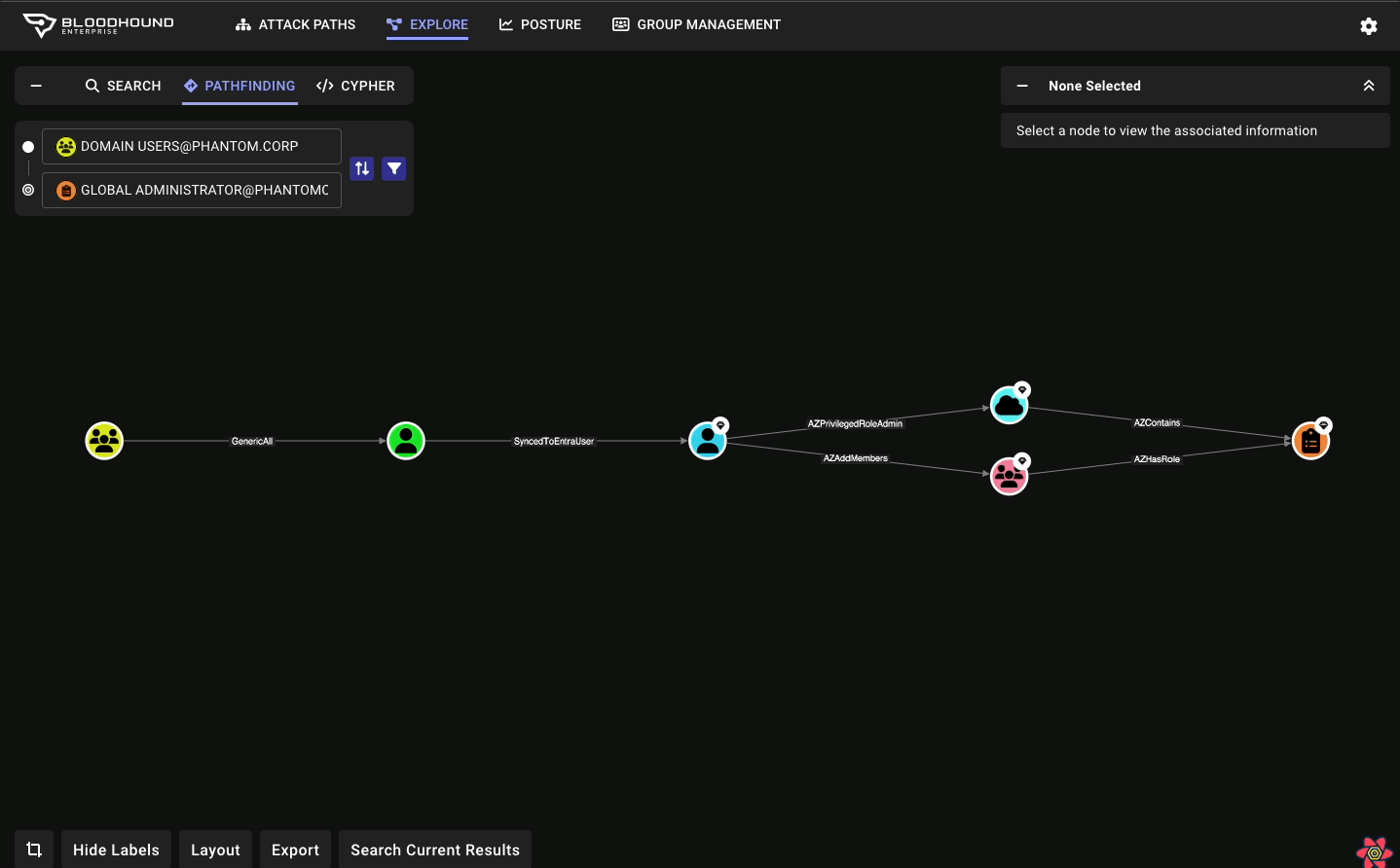
Node/Edge Label Toggle makes for more flexible public reporting
A long-requested feature has returned to BHCE and also available in BHE, allowing users to show or hide sensitive node and edge labels directly in the UI. This was contributed by the community member @palt — whom we give major kudos to!
New CoerceToTGT Edge Type
This new edge type provides more visibility into unconstrained delegation scenarios:
- Indicates principals configured for potential ticket-granting ticket (TGT) coercion
- For Enterprise users, this consolidates previous “Unconstrained Delegation” findings into a single, more informative attack path finding
Single Sign On (SSO) Improvements
- Added OpenID Connect (OIDC) support alongside existing SAMLv2 providers
- Automatic redirection for environments with a single SSO provider
Enterprise Domain Controllers Group Improvement
Improved consistency when creating an Enterprise Domain Controllers group to reduce confusion depending on how a collection was performed (note: requires a SharpHound upgrade).
Minor Improvements and Bug Fixes
The release also includes several quality-of-life improvements:
- Fixed scrolling issues in entity panels
- Resolved file upload hanging problems
- Corrected a pre-saved Cypher query for “Kerberoastable users with most privileges”
- Improved error handling in SharpHound data collection
Recommendations, Early Access and Further Information
Upgrade Recommendations:
- Upgrade to SharpHound v2.5.12 (Enterprise) or v2.5.9 (Community Edition)
- Upgrade to AzureHound to v2.2.1 for performance improvements
Early Access Features
- Administrators can enable the new analysis algorithm from the Administration -> Early Access configuration screen
To learn more about this release, sign up and join us for BloodHound Live: Monthly Release Recap on December 18 — and bring your questions! All BloodHound users can find expanded details on these updates today in our release notes or by contacting their Technical Account Manager.
Unwrapping BloodHound v6.3 with Impact Analysis was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.