Data Processing Addendum
Last Review Date: October 21, 2024
This Data Processing Addendum (“DPA”) is entered into by and between you and the entity you represent (“Customer”) and Specter Ops, Inc. (“SpecterOps“). This DPA is incorporated into and supplemental to the Master Service Agreement entered into between the parties which governs the provision of the SpecterOps Services by SpecterOps to Customer (“Agreement“). Except as modified below, the terms of the Agreement shall remain in full force and effect.
1. Definitions
1.1. Definitions: Capitalized terms not defined herein shall have the meaning given in the Agreement. In this DPA, the following terms (and derivations of such terms) shall have the following meanings:
- (a) “Applicable Data Protection Law” means all international, federal, national and state privacy and data protection laws that apply to the processing of Personal Data that is the subject matter of the Agreement (including, where applicable, California Consumer Privacy Act of 2018 or EU Data Protection Law).
- (b) “California Consumer Privacy Act of 2018” or “CCPA” means Cal. Civil Code Section 1798.100 et seq. and related regulations, as amended from time to time.
- (c) “Controller” means Customer or the entity that determines the purposes and means of the processing of Personal Data;
- (d) “Data Subject” means (i) a natural person whose Personal Data are processed in the context of this DPA and whose rights are protected by Applicable Data Protection Law; or (ii) a “Consumer” as that term is defined in the CCPA.
- (e) “Data Subject Rights” means those rights identified in the GDPR and the CCPA granted to Data Subjects.
- (f) “EU Data Protection Law” means: the EU General Data Protection Regulation 2016/679 (“GDPR”) and the laws implementing the GDPR, as amended from time to time.
- (g) “Personal Data” means any information which is provided by Customer (directly or indirectly) to Vendor and Processed by Vendor as part of its provision of Services to Customer and which either (i) is subject to EU Data Protection Law and defined as “personal data” under EU Data Protection Law; (ii) is subject to the CCPA and defined as “personal information” under the CCPA; or (iii) relates to an identified or identifiable natural person; an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person.
- (h) “Personal Data Breach” means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, Personal Data transmitted, stored or otherwise processed.
- (i) “Processing” shall have the meaning given in the GDPR.
- (j) “Processor“ means an entity that processes Personal Data on behalf of the Controller.
- (k) “Sub-Processor” means an entity engaged by the Processor or any further sub-contractor to process Personal Data on behalf of and under the instructions of the Controller.
2. Data Protection
2.1. Relationship of the parties: As between the parties and for the purposes of this DPA, Customer is the Controller of the Personal Data that is the subject of the Agreement (the “Data“) and appoints Vendor as a Processor to process the Data on behalf of Customer. Vendor is a “service provider” as defined in CCPA Section 1798.140(v). Customer shall comply with Applicable Data Protection Law, including but not limited to providing notice to Data Subjects and obtaining Data Subjects’ consent, where required. Vendor shall comply with Applicable Data Protection Law and understands the prohibitions on service providers set forth in CCPA Section 1798.140(t)(2)(C)(ii).
2.2. Purpose and Processing limitation: Vendor shall process the Data as a Processor only as necessary to perform the Services for Customer under the Agreement, and strictly in accordance with the documented instructions of Customer (including those in this DPA and the Agreement); and Customer shall only give lawful instructions to Vendor that comply with Applicable Data Protection Law. In no event shall Vendor process the Data for its own purposes or those of any third party. Customer discloses Personal Data subject to the CCPA to Vendor solely for a valid business purpose and for Vendor to perform the Services. Pursuant to the CCPA, Vendor is prohibited from: (i) selling the Personal Data; (ii) retaining, using, or disclosing the Personal Data for a commercial purpose other than providing the Services or as permitted by the CCPA; and (iii) retaining, using, or disclosing the Personal Data outside of the Agreement with Customer.
2.3. International transfers of Data: Vendor is located in the United States and Processes the Data in the United States and, except as otherwise agreed upon by the parties, Processes the Data in the United States. Vendor will at all times provide an adequate level of protection for the Data, in accordance with the requirements of Applicable Data Protection Law. To perform the Services for Customer under the Agreement, Customer transfers (directly or indirectly) Personal Data to Vendor in the United States, which may be a country other than the country in which the Data were originally collected. Customer authorizes such cross-border Personal Data transfers and confirms and warrants that it will comply with any requirements under EU Data Protection Law with regard to such Personal Data transfers. For such cross-border Personal Data transfers, Vendor and Customer agree to be bound by the Standard Contractual Clauses for the transfer of Personal Data to third countries pursuant to Regulation (EU) 2016/679 of the European Parliament and the Council approved by European Commission Implementing Decision (EU) 2021/914 of 4 June 2021, as currently set out at https://eur-lex.europa.eu/eli/dec_impl/2021/914/oj (the “Standard Contractual Clauses”). Clause 5(h) of the Standard Contractual Clauses is satisfied by compliance with Section 2.6 below; and Vendor may remove all commercial information or terms unrelated to the standard contractual clauses from agreements it provides upon Customer’s request pursuant to Clause 5(j) of the Standard Contractual Clauses.
2.4. Confidentiality of processing: Vendor shall ensure that any person that it authorises to process the Data (including Vendor’s staff, agents and subcontractors) shall be subject to a duty of confidentiality (whether a contractual duty or a statutory duty), and shall not permit any person to process the Data who is not under such a duty of confidentiality.
2.5. Security: Vendor shall implement appropriate technical and organisational measures intended to protect the Data from (i) accidental or unlawful destruction, and (ii) loss, alteration, unauthorised disclosure of, or access to the Data. At a minimum, such measures shall include the security measures identified in Annex B.
2.6. Subcontracting: Subject to the conditions set forth in this DPA, Customer authorizes Vendor to continue to use and disclose Data to Sub-Processors currently engaged by Vendor in the context of providing Vendor Services as laid out in Annex C. Vendor shall not subcontract any processing of the Data to a third party Sub-Processor unless: (i) such Sub-Processor is subject to an agreement with Vendor which contains the same data protection terms as those provided for by this DPA; and (ii) Vendor provides at least thirty [30] days’ prior notice of the addition or replacement of such Sub-Processor (including the details of the processing it performs or will perform, and the location of such processing). Customer shall notify Vendor within ten [10] business days after receipt of Vendor’s notice, if it objects to the addition or replacement of a sub-Processor. Customer’s objection should be sent to support@specterops.io and explain the reasonable grounds for the objection. If Customer objects to Vendor’s appointment of a third party sub-Processor on reasonable grounds relating to the protection of the Data, and Vendor is unable to adequately address the reasonable grounds, then Vendor will either not appoint the Sub-Processor, or Customer may elect to suspend or terminate the Agreement without penalty. Vendor shall remain fully liable for any breach of this DPA that is caused by an act, error or omission of its Sub-Processor.
2.7. Cooperation and Data Subject Rights: Customer is responsible for responding to Data Subject requests using Customer’s own access to the relevant Personal Data. Taking into account the nature of the processing and the information available, upon Customer’s request, Vendor shall provide all reasonable and timely assistance to enable Customer to respond to: (i) any request from an individual to exercise any Data Subject Rights under Applicable Data Protection Law; and (ii) any other correspondence received from a regulator or public authority in connection with the processing of the Data. In the event that any such communication is made directly to Vendor, Vendor shall promptly and without undue delay (and in any event, no later than within forty-eight (48) hours of receiving such communication) provide Customer full details of the same and shall not respond to the communication unless specifically required by law or authorized by Customer.
2.8. Data Protection Impact Assessment: Taking into account the nature of the processing and the information available to the Vendor, upon Customer’s request, Vendor shall provide Customer with reasonable and timely assistance as required by GDPR Article 35 or 36 with any data protection impact assessments and, where necessary, consultations with data protection authorities.
2.9. Personal Data Breach: Upon becoming aware of a Personal Data Breach affecting the Data, Vendor shall inform Customer without undue delay and shall provide sufficient available information and cooperation to enable Customer to fulfil its data breach reporting obligations under (and in accordance with the timescales required by) Applicable Data Protection Law. Vendor shall further take such measures and actions as are necessary to remedy and mitigate the effects of the Personal Data Breach and shall keep Customer informed of all material developments in connection with the Personal Data Breach. Vendor shall not notify any third parties of a Personal Data Breach affecting the Data unless and to the extent that: (a) Customer has agreed to such notification, and/or (b) notification is required to be made by Vendor under Applicable Data Protection Laws.
2.10. Deletion or return of Data: Upon termination or expiry of the Agreement, Vendor shall (at Customer’s election) delete or return all Data, including copies, in its possession or control. This requirement shall not apply to the extent that Vendor is required by Applicable Data Protection Laws to retain some or all of the Data, in which event Vendor shall isolate and protect the Data from any further processing except to the extent required by such law.
2.11. Audit: Vendor uses an external auditor to verify the adequacy of its security measures and controls for Services. The audit is conducted annually by an independent third-party in accordance with AICPA SOC2 standards and results in the generation of a SOC2 report (“Audit Report”) which is Vendor’s confidential information. Upon written request, Vendor shall provide Customer with a copy of the Audit Report subject to the confidentiality obligations of the Agreement or a non-disclosure agreement covering the Audit Report. If Vendor Processes Personal Data of Data Subjects located in the European Economic Area and the Audit Report and other information and documentation Vendor has otherwise provided to Customer does not meet the relevant requirements of GDPR, including Article 28(3)(h), then Vendor shall permit Customer (or its independent appointed representatives) to audit Vendor’s compliance with this DPA and shall make available all such information, systems and staff reasonably necessary to conduct such audit as required to meet the relevant requirements of GDPR. Customer shall not exercise its audit rights more than once per year except following a Personal Data Breach or following an instruction by a regulator or public authority. Customer shall give Vendor thirty (30) days prior written notice of its intention to audit, conduct its audit during normal business hours, and take all reasonable measures to prevent unnecessary disruption to Vendor’s operations. Customer and Vendor shall mutually agree in advance on the date, scope, duration, and security and confidentiality controls applicable to an audit. Customer shall reimburse Vendor for actual expenses and costs incurred to allow for and contribute to any audit.
3. MISCELLANEOUS
3.1 The obligations placed upon the Vendor under this DPA shall survive so long as Vendor and/or its Sub-Processors process Personal Data on behalf of Customer.
3.2 Except for the changes made by this DPA, the Agreement remains unchanged and in full force and effect. If there is any conflict between this DPA and the Agreement, this DPA shall prevail to the extent of that conflict.
3.3 If any provision of this DPA is deemed invalid or unenforceable, then the remainder of this DPA shall remain valid and in force. The invalid or unenforceable provision shall be either (i) amended to ensure its validity and enforceability while preserving the parties’ intentions as closely as possible; or (ii) if that is not possible, then construed in a manner as if the invalid or unenforceable part had never been included herein.
ANNEX A: DETAILS OF PROCESSING OF PERSONAL DATA
This Annex 1 includes certain details of the processing of Personal Data as required by Article 28(3) GDPR.
Subject matter and duration of the processing of Customer Data
The subject matter and duration of the processing of the Customer Data are set out in the Vendor SaaS Terms and Conditions and this Addendum.
The nature and purpose of the processing of Customer Data
The nature and purpose of the processing of Customer Data are set out in the Vendor SaaS Terms and Conditions and this Addendum.
The types of Customer Data to be processed
Customer may submit Personal Data, the extent of which is determined and controlled by Customer (including Customer’s Users and Customers) in its sole discretion, and which may include, but is not limited to, the following types of Personal Data:
- IT information (computer ID, user ID, domain name, Active Directory Structural data, user session data, local administrator and group data)
The categories of Data Subject to whom the Customer Data relates
Customer may submit Personal Data, the extent of which is determined and controlled by Customer in its sole discretion, and which may include, but is not limited to, Personal Data relating to the following categories of data subjects:
- Employees, agents, advisors, freelancers of Customer (who are natural persons); and
- Customer’s Users, Partners, Vendors, and Customers and the users and employees of those entities.
The obligations and rights of Customer
The obligations and rights of Customer are set out in Vendor SaaS Terms and Conditions and this Addendum.
ANNEX B
SPECIFIC SECURITY MEASURES
1. Description of the technical and organizational security measures implemented by the Vendor:
Hosting and Physical Security
Vendor inherits the control environment which Amazon maintains and demonstrates via SSAE16 SOC 1, 2 and 3, ISO 27001 and FedRAMP/FISMA reports and certifications. Web servers and databases run on servers in secure datacenters. Physical access is restricted to authorized personnel. Premises are monitored and access is logged.
You can read further about AWS security and certifications here:
- aws.amazon.com/security/
In addition to the controls inherited through AWS, Vendor maintains ISO 27001 and ISO 27017 reports and certifications for the controls for the entire solution. Customers can request and Vendor will provide verification of these certifications at any time.
Isolation of Services
Vendor servers run in virtual machines which are isolated from one another and from the underlying hardware layer. All services associated with each account are logically separated. There is no multi-tenancy of customer data.
Network Security
Vendor services are accessible only over HTTPS. Traffic over HTTPS is encrypted and is protected from interception by unauthorized third parties. Vendor uses only strong encryption algorithms with a key length of at least 128 bits.
All network access, both within the datacenter and between the datacenter and outside services, is restricted by firewall and routing rules. Network access is logged and logs are retained for a minimum of 30 days.
Vendor servers are only accessible through HTTPS and deny access to other ports, except that SSH access (protected by TLS and private key authentication) is enabled for administration. Administrative access is granted only to select employees of Vendor, based on role and business need.
Access to databases used in the Vendor service is over an encrypted link (TLS).
Authentication
Clients login to Vendor using a password which is known only to them and done only over secure (HTTPS) connections. Clients are required to have reasonably strong passwords. Passwords are not stored unencrypted; instead, as is standard practice, only a secure hash of the password is stored in the database. Because the hash is relatively expensive to compute, and because a “salting” method is used, brute-force guessing attempts are relatively ineffective, and password reverse-engineering is difficult even if the hash value were to be obtained by a malicious party.
When clients enable end users to connect to Vendor using user-supplied credentials (Single Sign On), this is done using security tokens, OAuth, or SAML 2.0, and in those cases, no credentials need to be stored in the Vendor system.
Development Process
Vendor developers have been trained in secure coding practices. Vendor application architecture includes mitigation measures for common security flaws such as the OWASP Top 10. The Vendor application uses industry standard, high-strength algorithms including AES and bcrypt. Periodic security tests are conducted, including using scanning and fuzzing tools to check for vulnerabilities.
Employee Screening and Policies
As a condition of employment all Vendor employees undergo pre-employment background checks and agree to company policies including security and acceptable use policies.
Security Issues
At Vendor, we consider the security of our systems a top priority. We have implemented a responsible disclosure policy to ensure that problems are addressed quickly and safely.
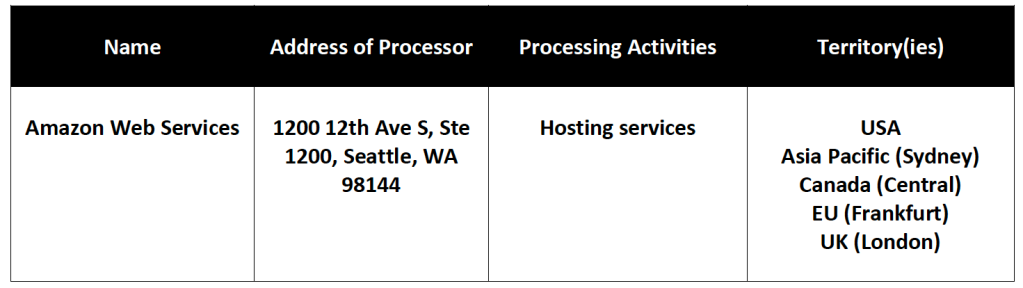
ANNEX C
LIST OF APPROVED SUBPROCESSORS