blog category
Research & Tradecraft
Research & Tradecraft
TL;DR: BOFHound can now parse Active Directory Certificate Services (AD CS) objects, manually queried from LDAP,...
By: Matt Creel
Oct 30, 2024 • 14 min read
Read Post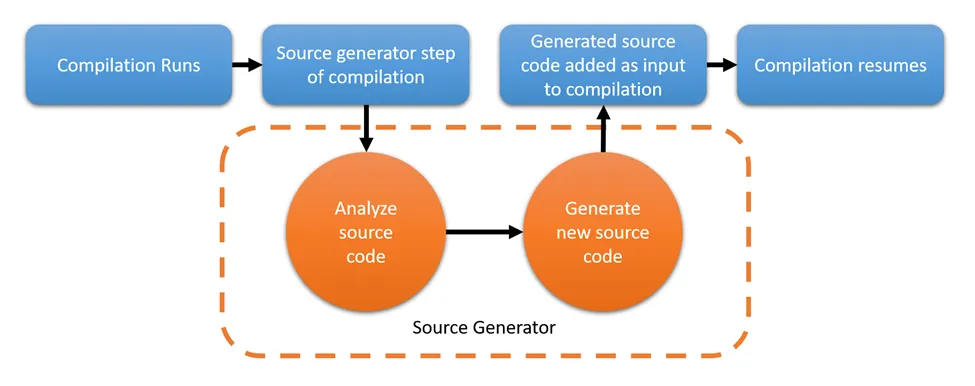
Research & Tradecraft
Dotnet Source Generators in 2024 Part 1: Getting Started
Introduction In this blog post, we will cover the basics of a source generator, the major...
By: Jonathan Owens
Oct 1, 2024 • 35 min read
Read Post
Research & Tradecraft
Ghostwriter v4.3: SSO, JSON Fields, and Reporting with BloodHound
Ghostwriter v4.3 is available now, and it enhances features introduced in previous versions of v4 in...
By: Christopher Maddalena
Sep 23, 2024 • 7 min read
Read Post
Research & Tradecraft
ADCS Attack Paths in BloodHound — Part 3
ADCS Attack Paths in BloodHound — Part 3 In Part 1 of this series, we explained how we incorporated...
By: Jonas Bülow Knudsen
Sep 11, 2024 • 22 min read
Read Post
Research & Tradecraft
Mythic 3.3 — Out of Beta Mythic 3.3 was released in a Beta six weeks ago, and since then...
By: Cody Thomas
Aug 28, 2024 • 10 min read
Read Post
Research & Tradecraft
Ghostwriter ❤ Tool Integration
Incorporating new components into existing systems is such a pain, this process has been labeled “Integration...
By: Alexander Sou
Aug 27, 2024 • 5 min read
Read Post
Research & Tradecraft
Navigating the Uncharted: A Framework for Attack Path Discovery
This is the second post in a series on Identity-Driven Offensive Tradecraft, which is also the...
By: Elad Shamir
Aug 20, 2024 • 8 min read
Read Post
Research & Tradecraft
Hiding C2 With Stealthy Callback Channels Write a custom command and control (C2) implant — Check...
By: Forrest Kasler
Aug 14, 2024 • 12 min read
Read Post
Research & Tradecraft
Relay Your Heart Away: An OPSEC-Conscious Approach to 445 Takeover
Even within organizations that have achieved a mature security posture, targeted NTLM relay attacks are still...