blog category
Research & Tradecraft
Research & Tradecraft
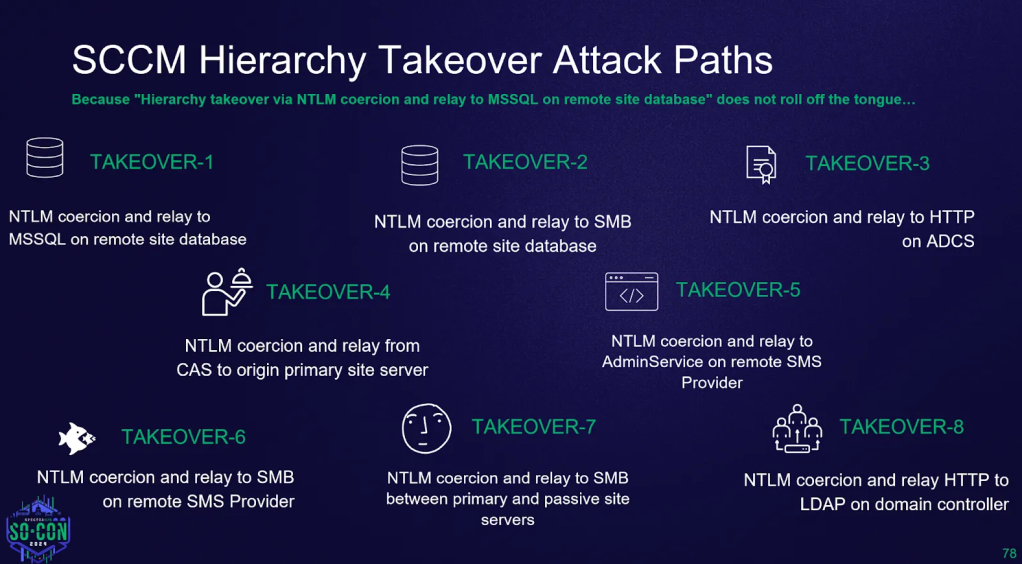
Rooting out Risky SCCM Configs with Misconfiguration Manager
tl;dr: I wrote a script to identify every TAKEOVER and ELEVATE attack in Misconfiguration Manager. Ever...
By: Chris Thompson
Apr 11, 2024 • 4 min read
Read Post
Research & Tradecraft
Ghostwriter v4.1: The Custom Fields Update
Let’s dive into what makes this so exciting! There’s so much to cover that we won’t...
By: Christopher Maddalena
Apr 5, 2024 • 7 min read
Read Post
Research & Tradecraft
Getting Intune with Bugs and Tokens: A Journey Through EPM
Written by Zach Stein & Duane Michael SpecterOps Hackathon Back in January, SpecterOps held our annual hackathon...
By: Zach Stein
Apr 2, 2024 • 19 min read
Read Post
Research & Tradecraft
Agent Customization in Mythic: Tailoring Tools for Red Team Needs
By: Cody Thomas
Mar 27, 2024 • 9 min read
Read Post
Research & Tradecraft
How MS Exchange on-premises compromises Active Directory and what organizations can do to prevent that. At SpecterOps,...
By: Jonas Bülow Knudsen
Mar 20, 2024 • 28 min read
Read Post
Research & Tradecraft
Summoning RAGnarok With Your Nemesis
I hope I’m Not Too Late With the explosion of large language model (LLM) use, everyone is...
By: Will Schroeder
Mar 13, 2024 • 16 min read
Read Post
Research & Tradecraft
Browserless Entra Device Code Flow
Zugspitze, Bavaria, Germany. Photo by Andrew Chiles Did you know that it is possible to perform every...
By: Andy Robbins
Mar 6, 2024 • 8 min read
Read Post
Research & Tradecraft
Misconfiguration Manager: Overlooked and Overprivileged
TL;DR: Misconfiguration Manager is a central knowledge base for all known Microsoft Configuration Manager tradecraft and...
By: Duane Michael
Mar 5, 2024 • 13 min read
Read Post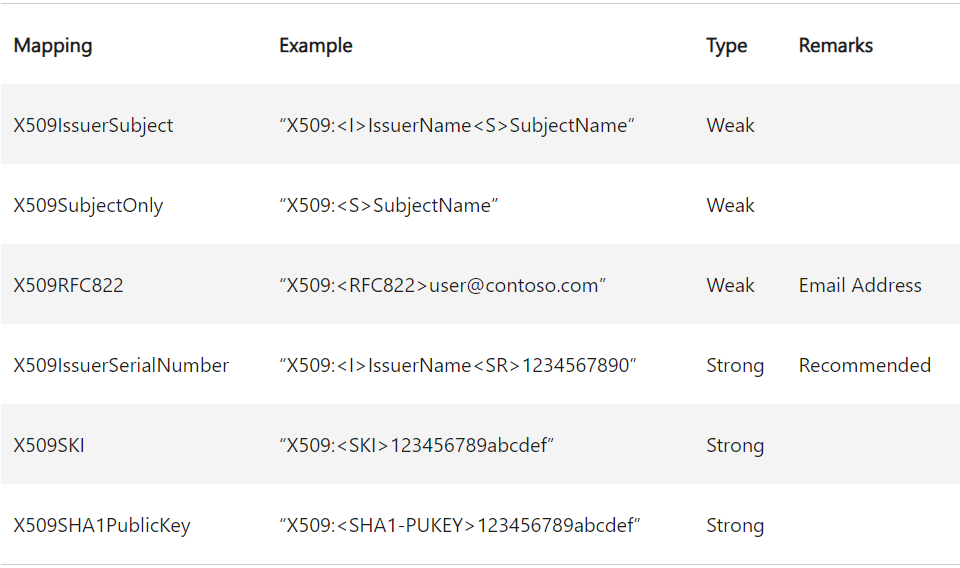
Research & Tradecraft
The altSecurityIdentities attribute of Active Directory (AD) computers and users allows you to specify explicit certificate...