Tag
Attack paths

Attack paths
SCCM Hierarchy Takeover via Entra Integration…Because of the Implication
TL;DR SCCM sites (prior to KB35360093) integrated with Entra ID can be abused to compromise the...
Nov 19, 2025
Read Post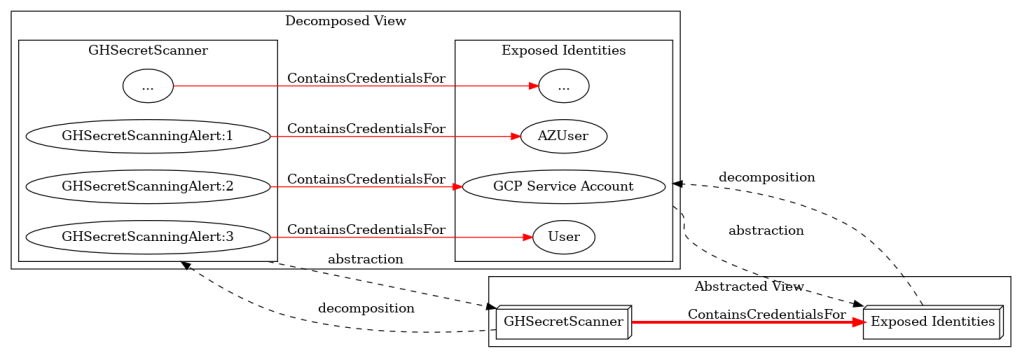
Attack paths
Taming the Attack Graph: A Many Subgraphs Approach to Attack Path Analysis
TL;DR This blog presents a framework using technology subgraphs, decomposition, and graph abstraction to model hybrid...
Nov 13, 2025
Read Post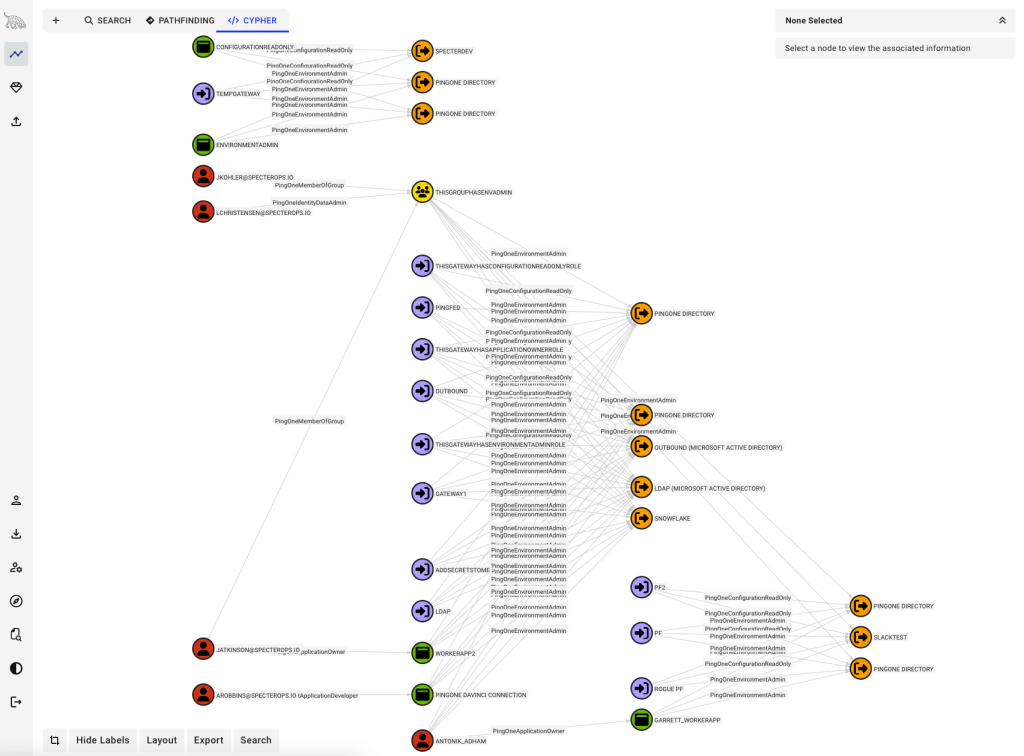
Attack paths
TL;DR: You can use PingOneHound in conjunction with BloodHound Community Edition to discover, analyze, execute, and...
Oct 20, 2025
Read Post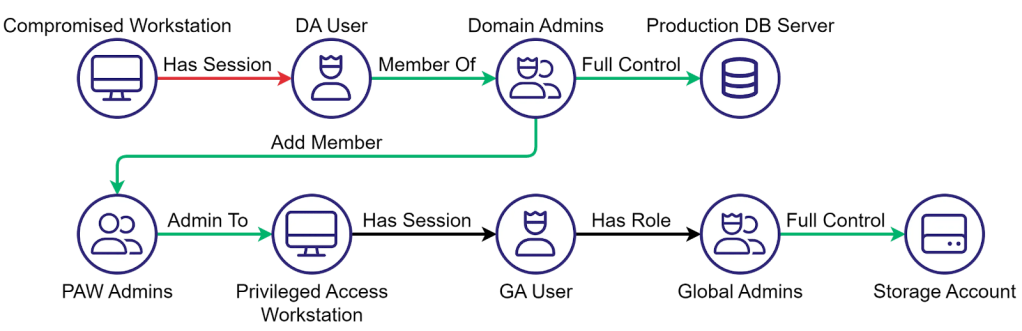
Attack paths
The Clean Source Principle and the Future of Identity Security
TL;DR Modern identity systems are deeply interconnected, and every weak dependency creates an attack path — no...
Oct 8, 2025
Read Post
Attack paths
WriteAccountRestrictions (WAR) – What is it good for?
TL;DR A lot of things. The User-Account-Restrictions property grants read/write permissions to the user-account-control LDAP attribute,...
Oct 1, 2025
Read Post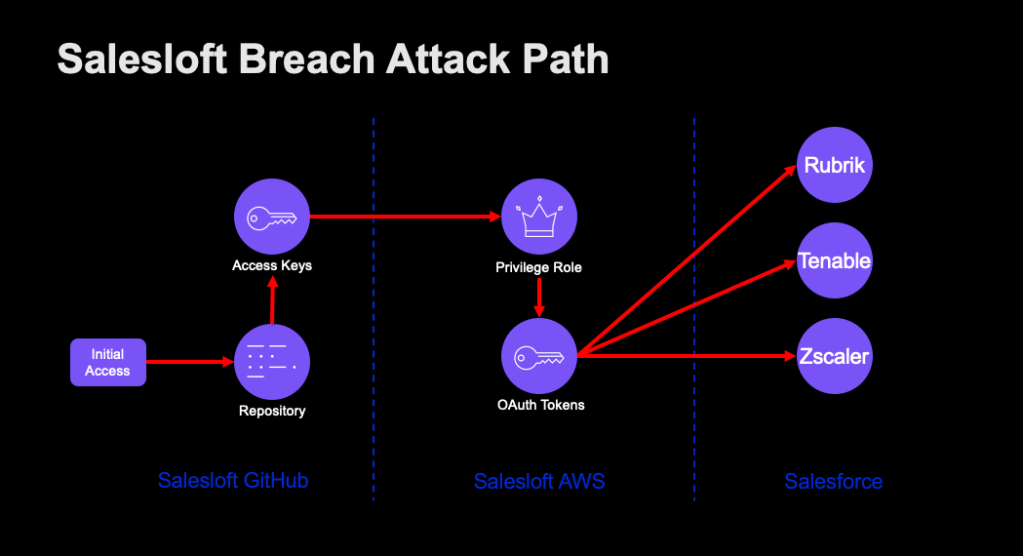
Attack paths
The Salesloft–Drift Breach: An Attack Path Case Study
TL;DR This post analyzes the Salesloft–Drift incident through an attack path lens, showing how violations of...
Sep 24, 2025
Read Post
Attack paths
HKLM\SYSTEM\Setup\sMarTdEpLoY – The (Static) Keys to Abusing PDQ SmartDeploy
TL;DR: Prior to version 3.0.2046, PDQ SmartDeploy used static, hardcoded, and universal encryption keys for secure...
Aug 12, 2025
Read Post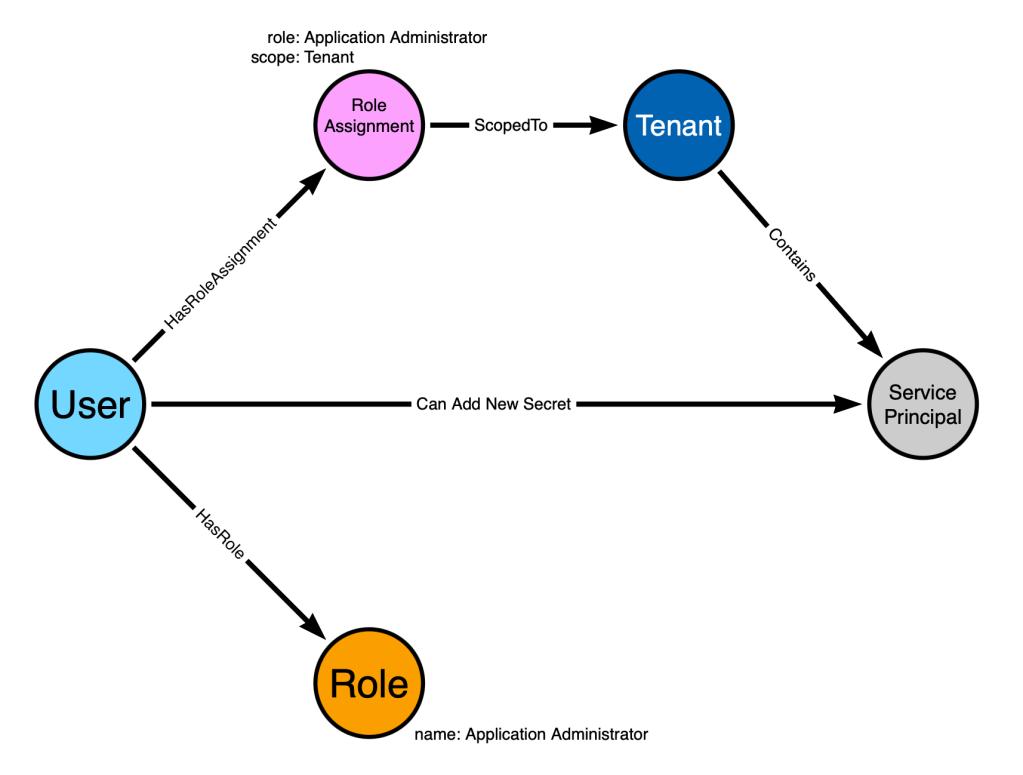
Attack paths
Attack Graph Model Design Requirements and Examples
TL;DR OpenGraph makes it easy to add new nodes and edges into BloodHound, but doesn’t design...
Aug 1, 2025
Read Post
Attack paths
Entra Connect Attacker Tradecraft: Part 3
TL;DR Attackers can exploit Entra Connect sync accounts to hijack device userCertificate properties, enabling device impersonation...