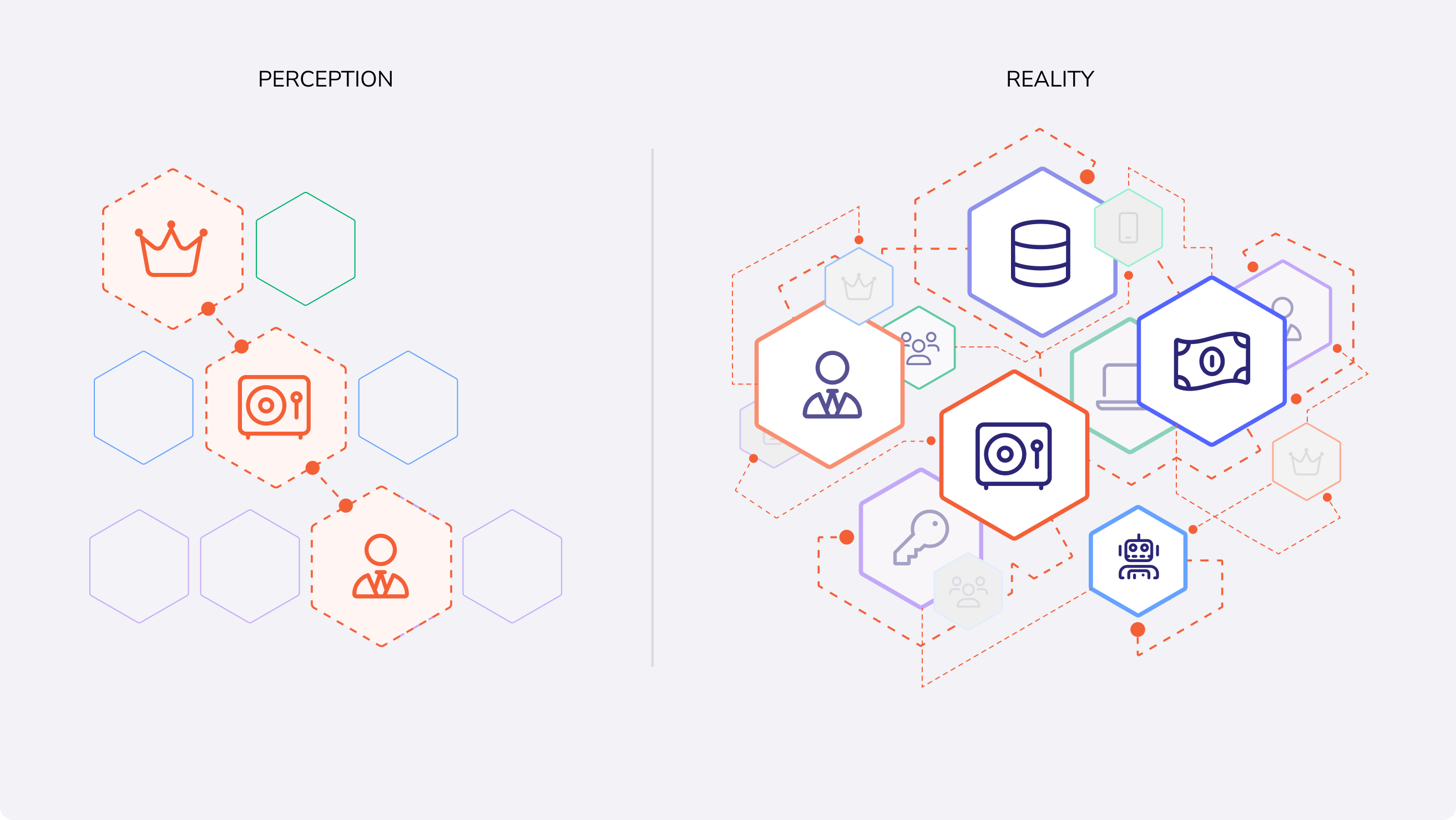
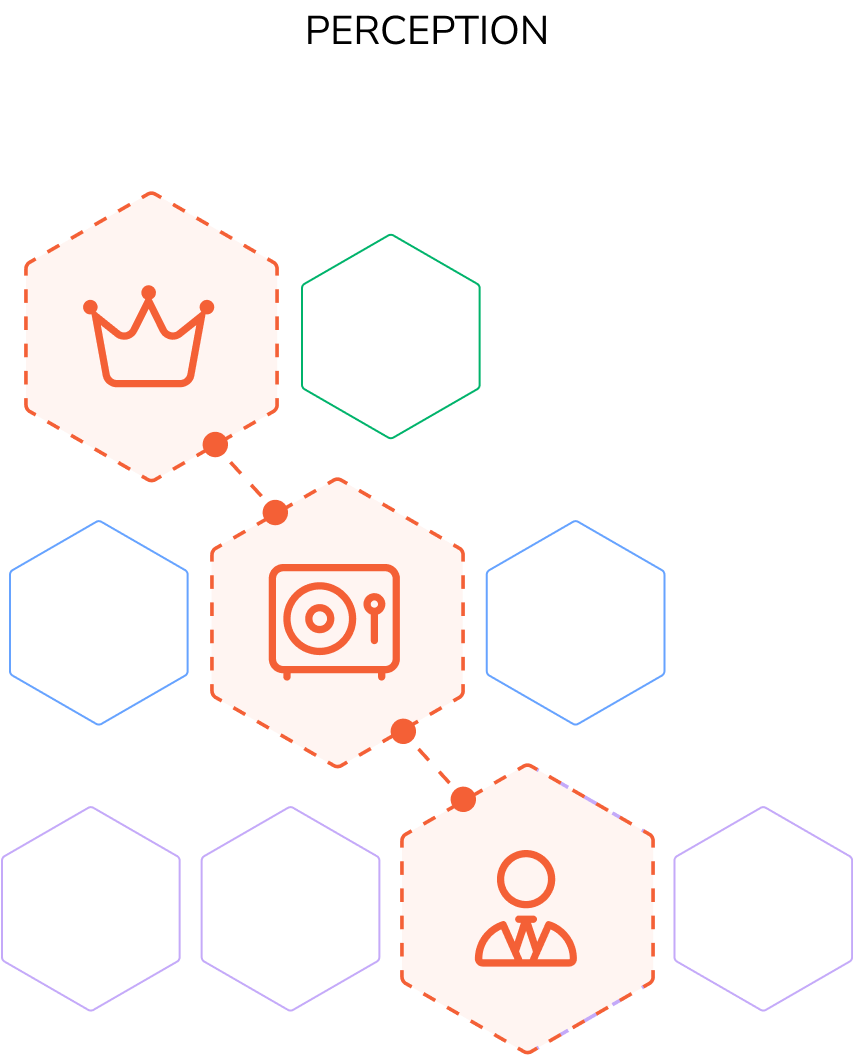
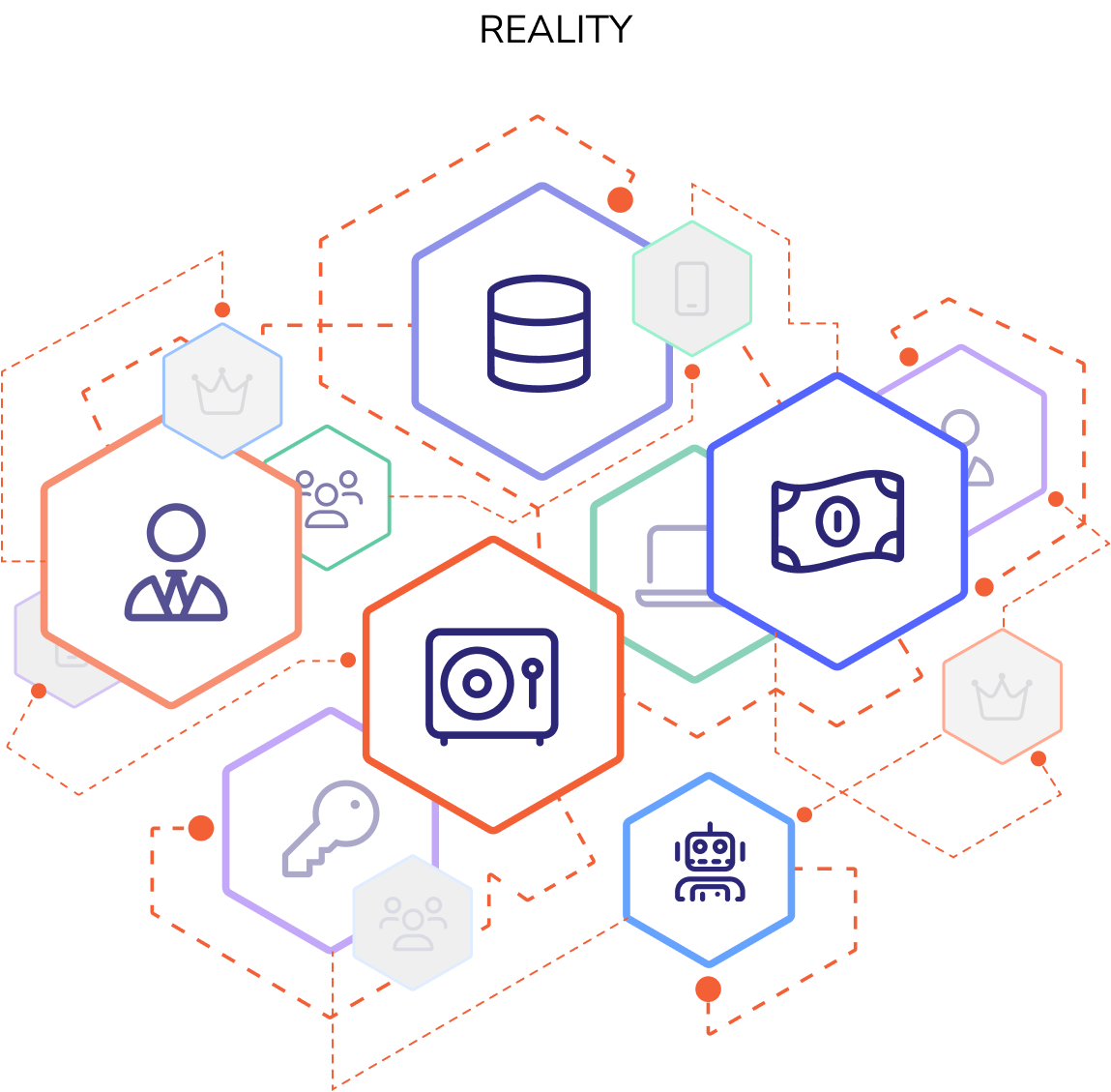
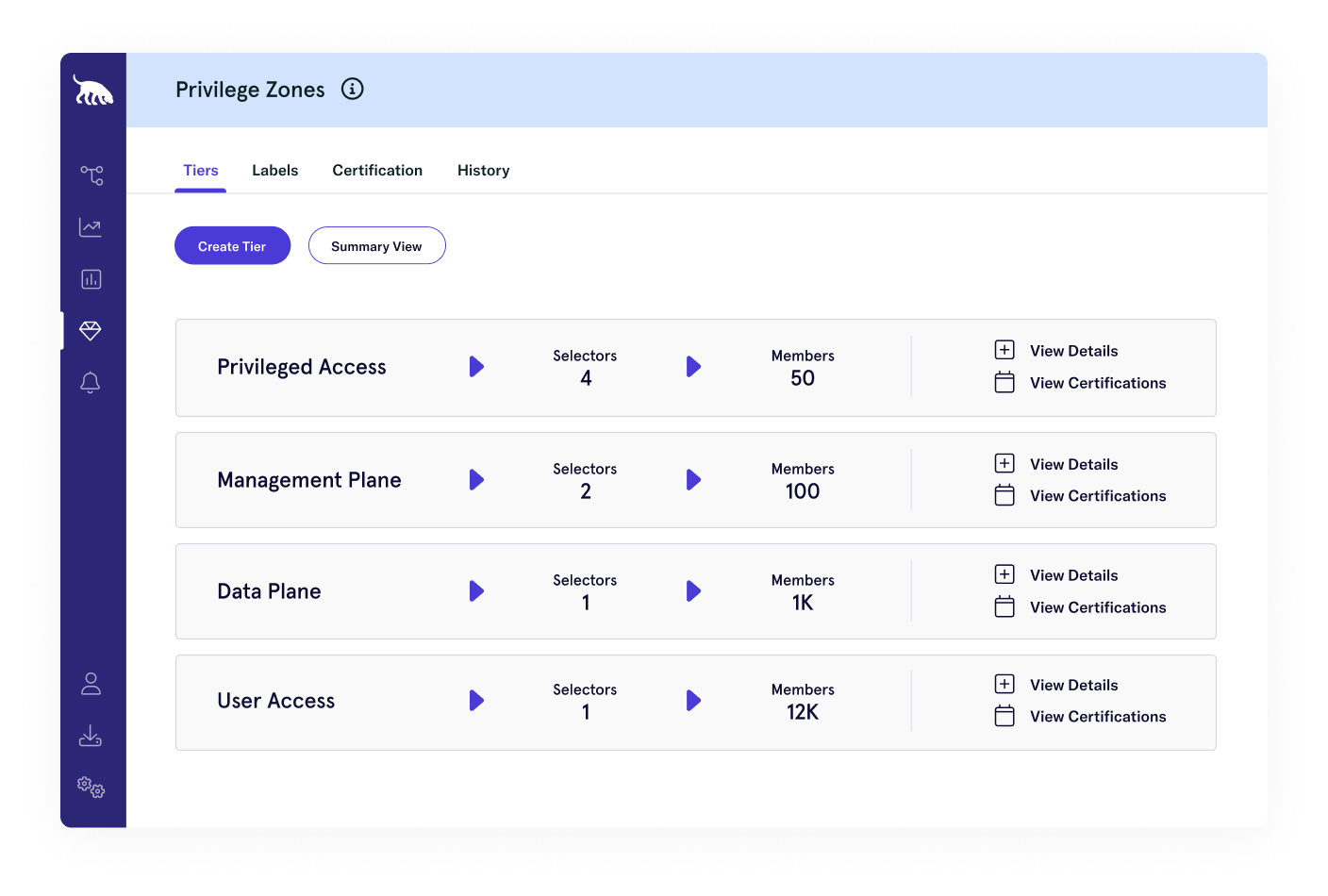
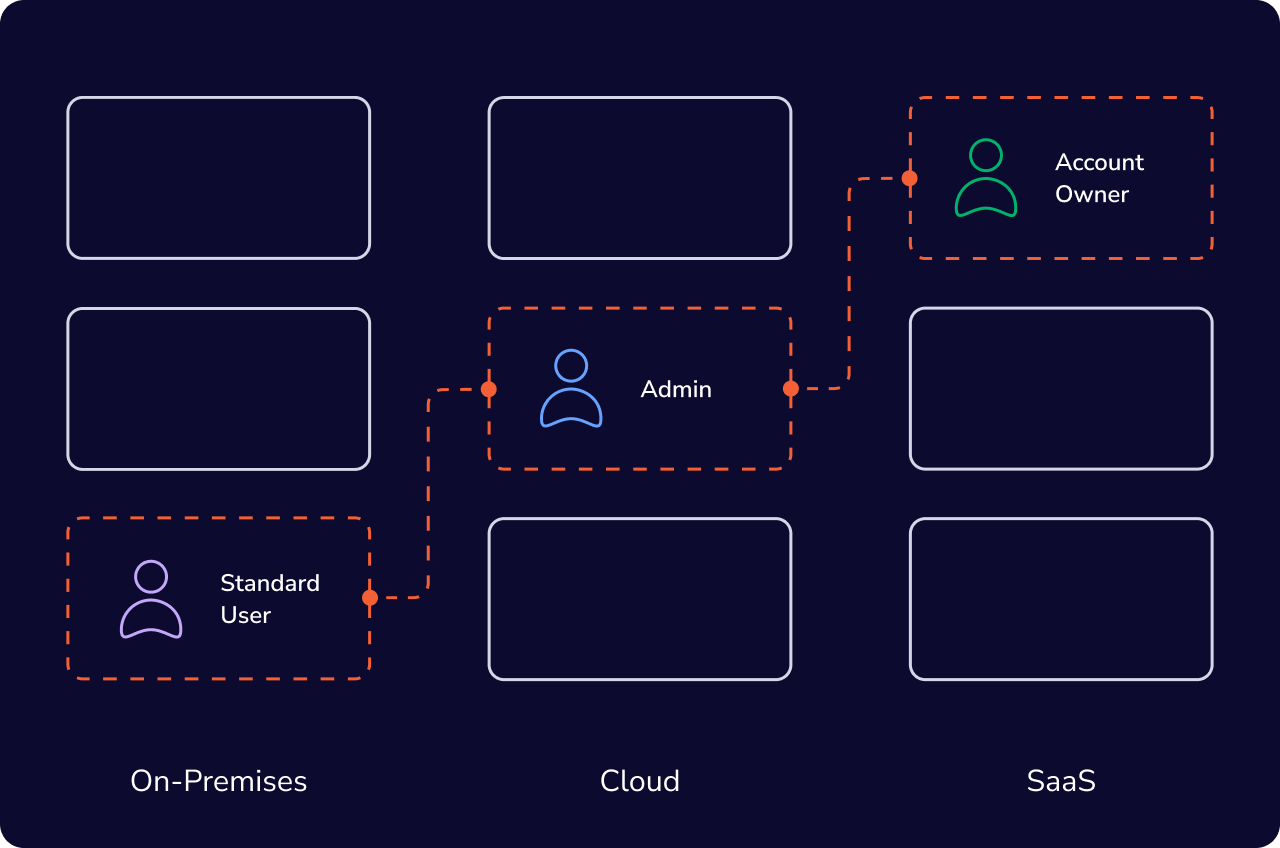
Visibility and enforcement lack connection
There has never been a technical control to enforce these boundaries. It’s all been best
practices, spreadsheets, and intent. So it’s no surprise that environments are full of:
- Hidden attack paths
- Over-permissioned accounts
- Privilege escalation opportunities waiting to be abused