BloodHound Enterprise
Eliminate Attack Paths
Manage Identity Attack Paths across your hybrid environment and remove the adversary’s paths to your critical assets.

See how BloodHound Enterprise uncovers and eliminates hidden threats to your vital systems
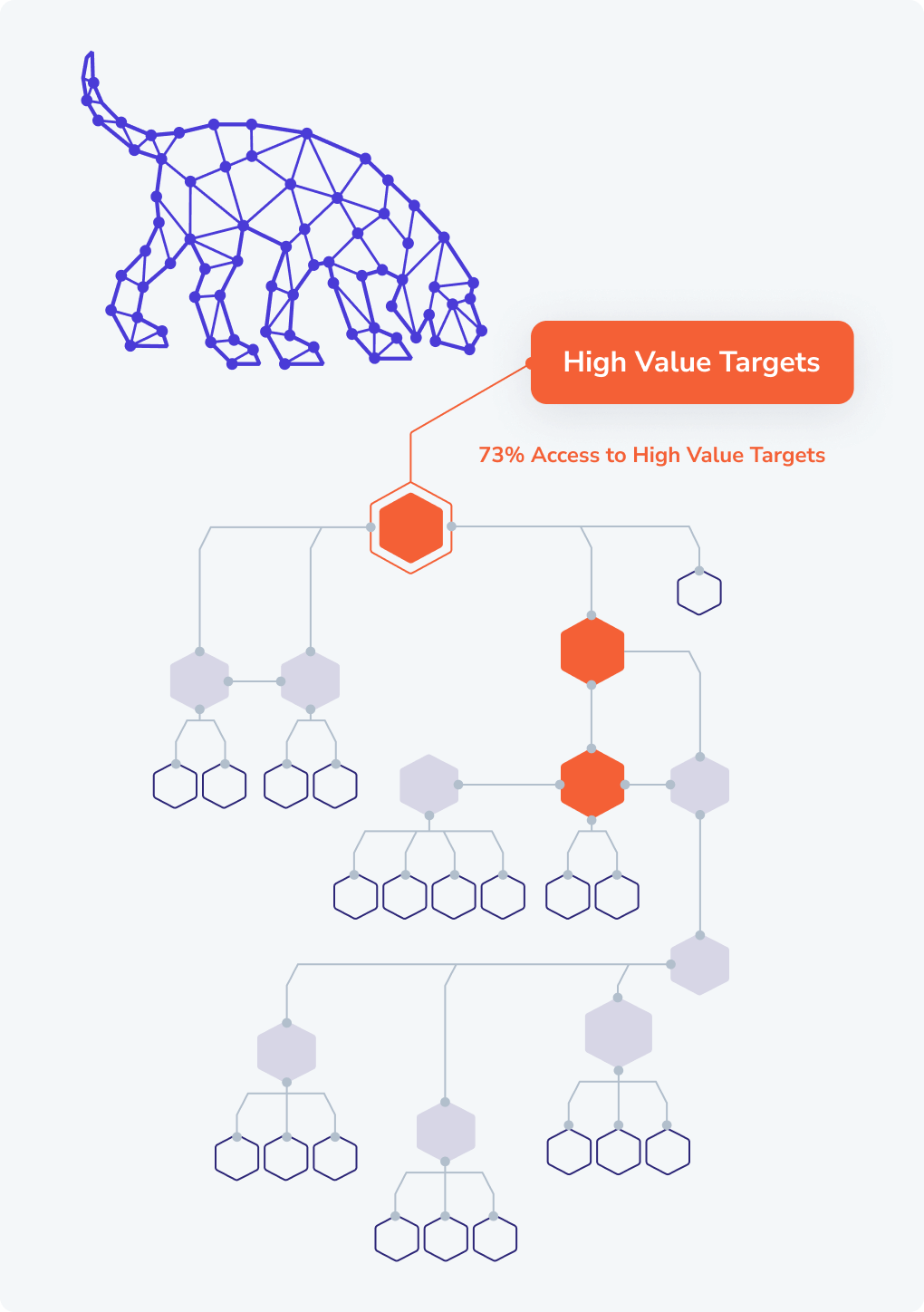
Discover Attack Paths
Advanced, accurate, and effective
Improve identity practices while protecting what matters most. Eliminate identity attack paths and the conditions that introduce them.
The most extensive and reliable attack graph technology available
Map, prioritize, and remediate millions of Identity Attack Paths
Surface decades of identity tech debt with guidance to programmatically eliminate it
Stay Ahead of the Adversary
Identity is the adversary’s favorite target
As identities evolve and environments expand, static defenses fall short.
BloodHound Enterprise helps you stay ahead by operationalizing Identity Attack Path Management.
Establish a continuous, measurable Identity Attack Path Management program
Strengthen your existing stack with BloodHound Enterprise’s integrated analysis and workflows
Eliminate the attack paths behind many of your alerts — and reduce detection noise at the source
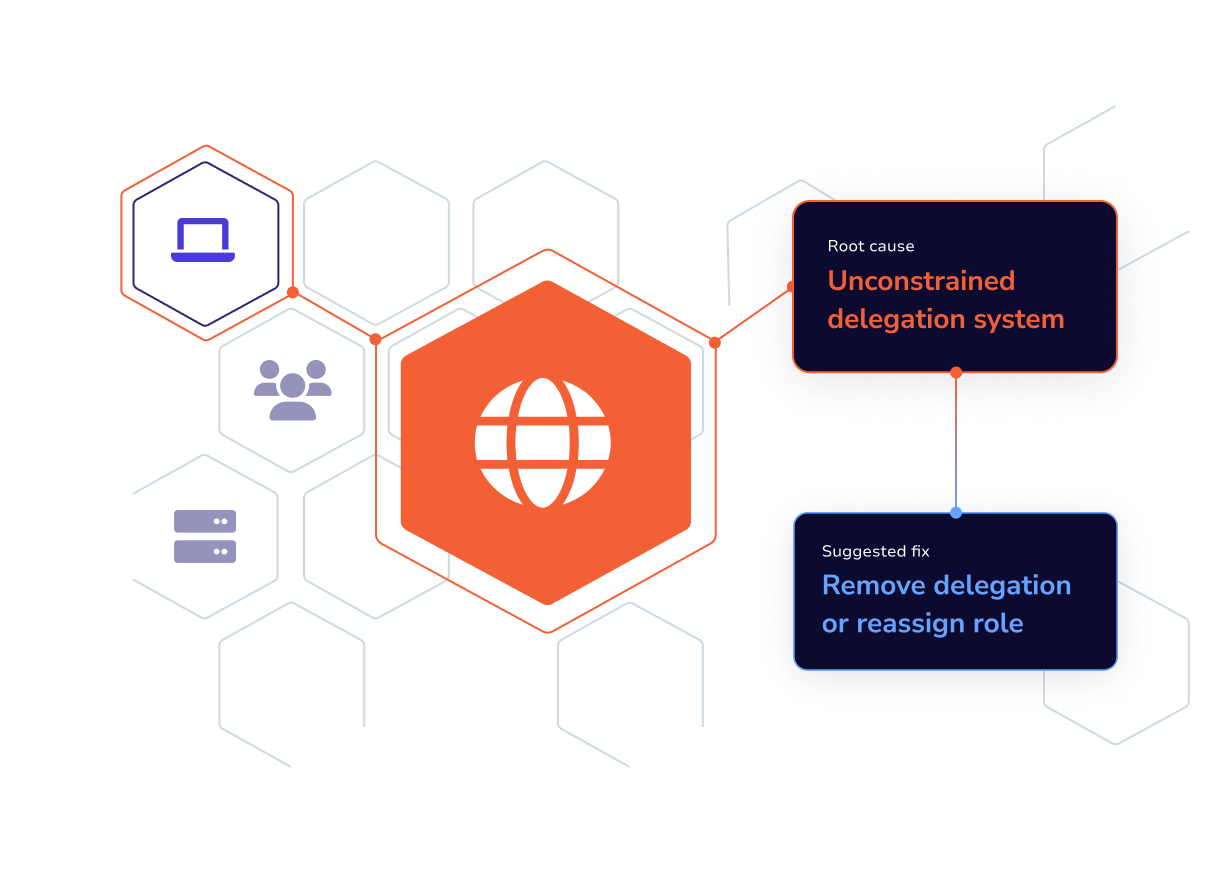
Remove Risk
Eliminate identity attack paths at scale
Bring Security and Identity teams together to tackle identity risk at scale — all in one platform.
Continuously map and prioritize attack paths and choke points
Get clear, tested remediation guidance to reduce risk with minimal change
Monitor evolving threats and track progress over time
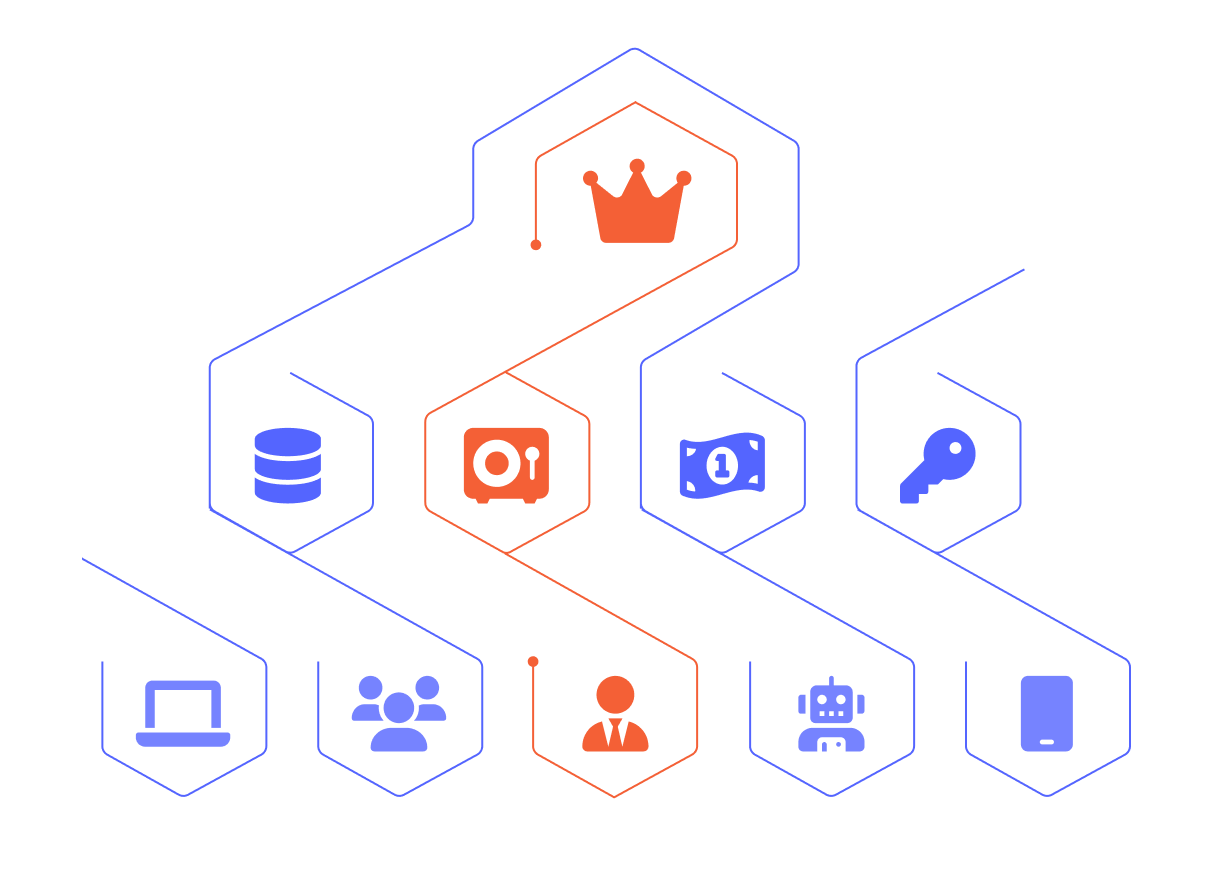
Protect high-impact assets with Privilege Zones
INTRODUCING PRIVILEGE ZONES
Enforce Least Privilege through Privilege Zones
BloodHound Enterprise Privilege Zones create secure and enforceable segregation of mission critical assets – enabling true least privilege enforcement
100
M+
Attack paths remediated
Hundreds of millions of attack paths remediated with BloodHound Enterprise.
35
%
Risk reduction
BloodHound Enterprise customers see an average 35% reduction of risk in the first 30 days.
17
K+
Paths cut per choke point
On average, cutting a single choke point severs access to more than 17,000 attack paths.
What Practitioners Are Saying
Validated by hands-on operators and strategic teams alike. These real-world testimonials show how organizations use BloodHound Enterprise to reduce identity risk at scale.
Learn More About
Attack Path Management
See how BloodHound Enterprise eliminates millions of attack paths while focusing your defenses on the routes attackers actually use to reach your critical assets.



