See identity risk the way adversaries do
You’ve deployed identity tools. You’ve adopted least privilege. You’ve patched, segmented, and monitored. But attackers are still getting in — and even worse, they’re moving through. Why? Attackers don’t go through your tools. They go around them.
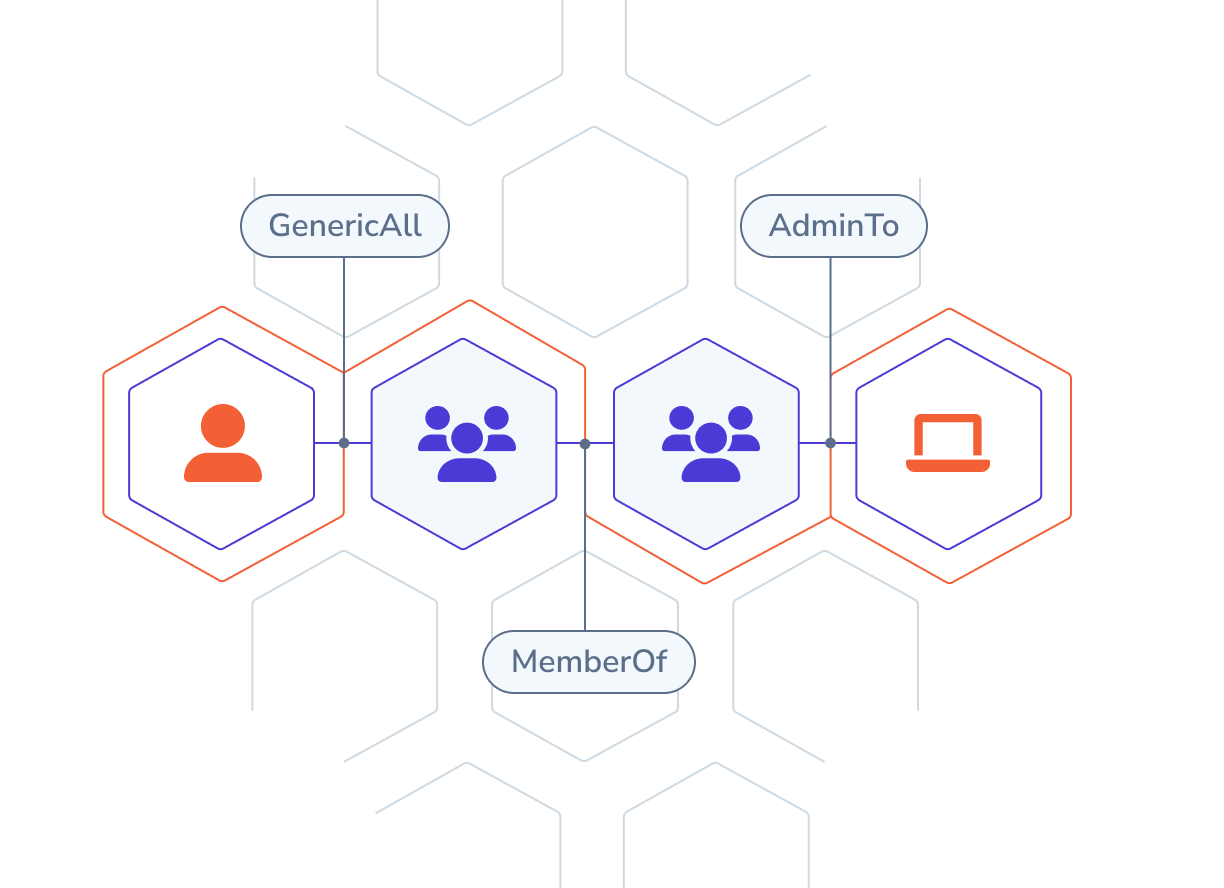
Why Identity Attack Path Management
Identity risk manifests as attack paths
Adversaries rely on relationships between identities, systems, and permissions. They chain together misconfigurations, overlooked privileges, and system relationships to get in.
Identity Attack Path Management helps you see these chains like attackers do, so you can:
Discover how attackers exploit identity relationships to access your crown jewels.
Visualize and prioritize risk based on attacker movement, not static policy.
Align Security, Identity, and IT around shared visibility and accountability.
Focus remediation efforts on the identity paths that pose the greatest business risk.
KEY ELEMENTS OF AN APM PRACTICE
The identity attack path management practice: your strategic foundation
Making identity attack path management effective isn’t just about technology — it’s about establishing it as a practice within your cybersecurity program.
Operational blueprints
Best practices for implementing, maintaining, and scaling your Identity APM capability
Organizational alignment
A unified view that shows how identity relationships flow across your entire environment — from on-prem to cloud to SaaS applications.
Skills and mindset
Adversary-first thinking and the technical capabilities to operationalize it
Integration points
Integration guidance for integrating Identity APM within your existing security program and stack
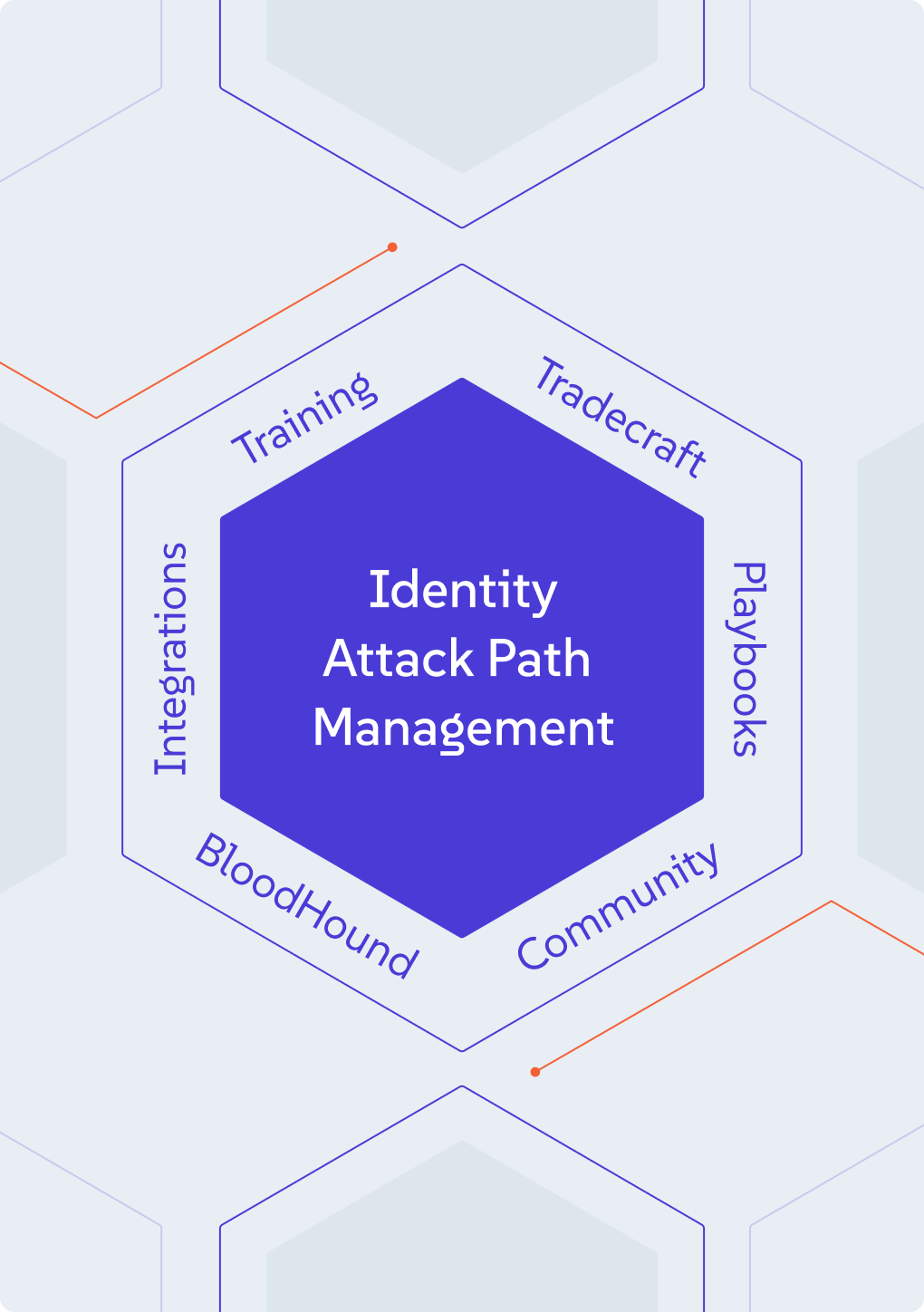
A Total Attack Path Management Platform
How SpecterOps helps
We support your identity attack path management journey across four connected elements:
BloodHound Enterprise
Visualize hidden access and privilege. Prioritize the most dangerous attack paths. Eliminate them—fast and safely.
-
Map out paths attackers could take across your environment
-
Identify and prioritize the most exploitable weaknesses
-
Remediate with confidence—no guesswork, no chaos
Training
Sharpen your edge with expert-led courses. Go deep on identity threats and how to stop them.
-
Learn directly from the creators of BloodHound
-
Get hands-on experience solving real-world scenarios
-
Build internal expertise that scales with your team
Services
Get hands-on help from the team that built the tools. We solve hard problems across your identity landscape.
-
Assess and mature your Identity Attack Path Management program
-
Accelerate remediation with guided support
-
Customize solutions for your unique environment

Community
Connect with peers, swap insights, and stay ahead. This is where the identity security community lives.
-
Join the conversation in our public Slack workspace
-
Access open-source tools, research, and best practices
-
Collaborate with others solving the similar challenges
Overview
Why SpecterOps for Identity Attack Path Management?
We built the category
From red team assessments to the leading platform for identity attack path management, we’ve pioneered the practice.
We think like attackers
Our expertise comes from real-world adversary tradecraft, not theoretical models.
We enable your success
Training, services, and technology that work together to make your identity attack path management practice operationally effective.

State of Attack Path Management report
Attackers don’t go through your tools, they go around them. This is a key conclusion from the inaugural report from SpecterOps, which explores identity risk through the eyes of the adversary. Learn the difference between access graphs and attack paths, how identities in transit reshape exposure, and what it takes to build a sustainable Attack Path Management strategy grounded in real-world tradecraft.
Ready to get started?
See how BloodHound Enterprise eliminates millions of attack paths while focusing your defenses on the routes attackers actually use to reach your critical assets.
Learn More