blog category
Research & Tradecraft
Research & Tradecraft
Lateral Movement with the .NET Profiler
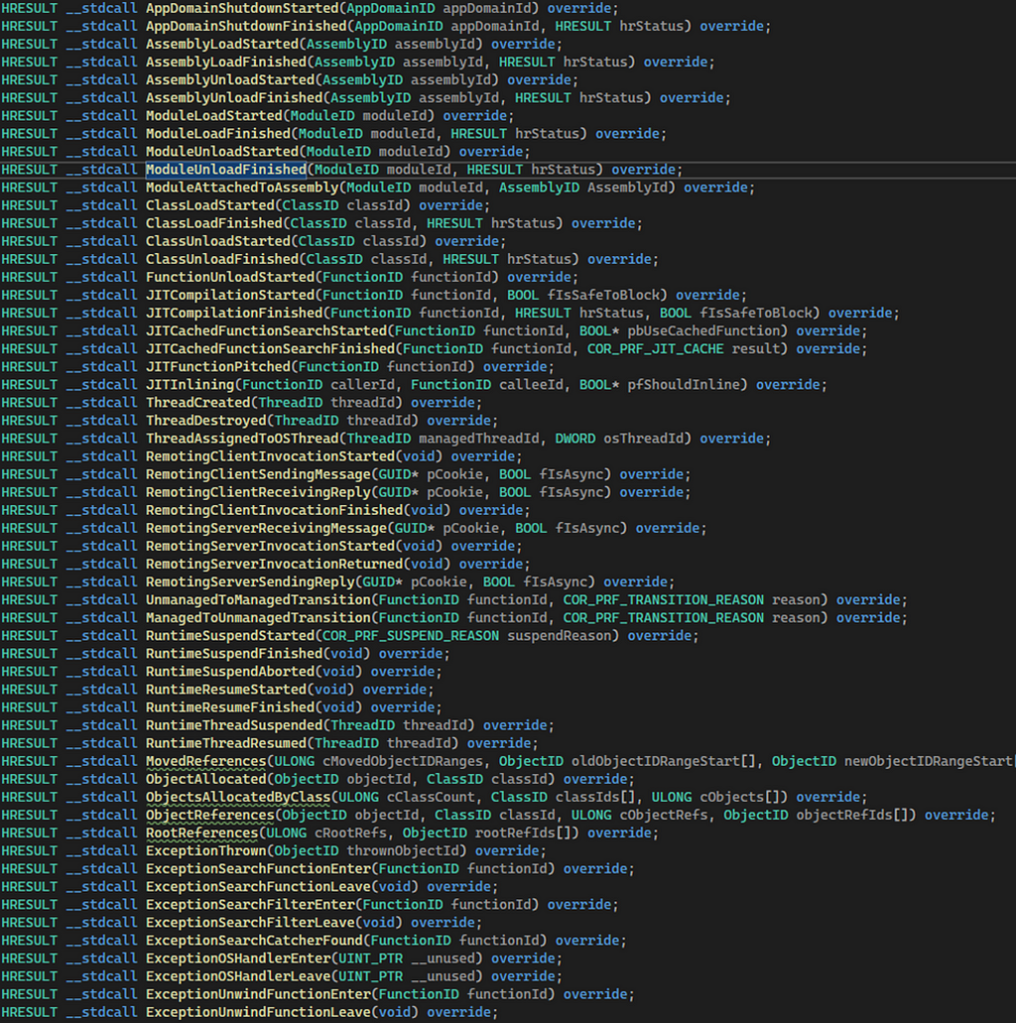
Lateral Movement with the .NET Profiler The accompanying code for this blogpost can be found HERE. Intro I spend...
By: Daniel Mayer
Jun 11, 2024 • 8 min read
Read Post
Research & Tradecraft
Ghostwriter v4.2: Project Documents & Reporting Enhancements After April’s massive Ghostwriter v4.1 release, we received some...
By: Christopher Maddalena
Jun 10, 2024 • 7 min read
Read Post
Research & Tradecraft
Automating SCCM with Ludus: A Configuration Manager for Your Configuration Manager
TL;DR: Using Ludus as the backend, and with the help of Erik at Bad Sector Labs,...
By: Zach Stein
Jun 6, 2024 • 13 min read
Read Post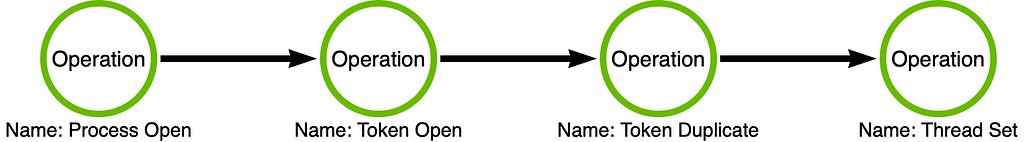
Research & Tradecraft
On Detection: Tactical to Functional When the Operation is not Enough Introduction A while back, I was...
By: Jared Atkinson
Jun 5, 2024 • 17 min read
Read Post
Research & Tradecraft
One Phish Two Phish, Red Teams Spew Phish
PHISHING SCHOOL How to Give your Phishing Domains a Reputation Boost “Armed with the foreknowledge of...
By: Forrest Kasler
Jun 4, 2024 • 20 min read
Read Post
Research & Tradecraft
Part 13: Why a Single Test Case is Insufficient
By: Jared Atkinson
May 31, 2024 • 24 min read
Read Post
Research & Tradecraft
Increasing our understanding of EDR capabilities in the face of impossible odds. Introduction I recently had...
By: Luke Paine
May 30, 2024 • 12 min read
Read Post
Research & Tradecraft
Behavior vs. Execution Modality
On Detection: Tactical to Functional Part 12 Introduction At Shmoocon 2015, Will Schroeder (Harmj0y) gave a...
By: Jared Atkinson
May 21, 2024 • 20 min read
Read Post
Research & Tradecraft
Part 12: Behavior vs. Execution Modality