What’s in a name? TTPs in Info Sec
What are TTPs?
When reading through various information security reports, blogs, and tweets, I often see the acronym “TTP” used to describe a myriad of things (such as Testing, Tools, Processes, Programs, etc) related to information security. Though TTP is a commonly used acronym, it is often not the original meaning: Tactics, Techniques, and Procedures. In this post, I’m going to discuss my interpretation of TTPs (based on Department of Defense doctrine) and explain why I believe this is the way you should be using TTP!
TTP according to Joint Publication 1–02
Tactics, Techniques, and Procedures are specific terms which originated in the Department of Defense and have been used for many years to describe military operations. Joint Publication 1–02, Department of Defense Dictionary of Military and Associated Terms specifically defines Tactics, Techniques, and Procedures:
Tactics — The employment and ordered arrangement of forces in relation to each other.
Techniques — Non-prescriptive ways or methods used to perform missions, functions, or tasks.
Procedures — Standard, detailed steps that prescribe how to perform specific tasks.

Now that we have the “official” definitions, what do they actually mean? I like to think of these as a hierarchy of specificity, going from the most broad (Tactics) to the most specific (Procedures). In order to help clarify what these actually mean in practice, I will go through and explain what each term actually means in greater detail. Additionally, I’ll use the metaphor of “car ownership” to help describe each of these terms.
Tactics
Tactics are high-level considerations with limited specific information dictating how things should be done. Normally used for planning and/or tracking purposes, there are no specific directions or instructions, just general guidance useful for high-level considerations to ensure that everything necessary is completed as part of a bigger whole.
To use the analogy of car ownership, there are many “Tactics” involved in owning a car, such as providing fuel, cleaning, and preventative maintenance. Each of these could be viewed as a “tactic” involved in owning a car. For the purpose of this example, we will focus on “Preventative Maintenance” as the chosen tactic into which we will deep dive.
Techniques
Techniques form the grey area between the high-level perspective of tactics and very specific details of Procedures (which we discuss next). They consist of the actions that are expected to be accomplished, but without specific directions (i.e. non-prescriptive) for how to complete that action. This typically results in identifying tasks that need to be accomplished, but without micromanaging how to accomplish the task.
To continue the car analogy, if the chosen Tactic is “Preventative Maintenance,” there would be numerous different Techniques that could be employed to accomplish that tactic, such as changing the oil, rotating tires, replacing brakes, etc. These techniques outline the general tasks which need to be accomplished, however do not provide specific instructions for how to accomplish them. We will choose “changing the oil” as the technique we are interested in and will use to discuss procedures.
Procedures
Procedures are specific detailed instructions and/or directions for accomplishing a task. Procedures include all of the necessary steps involved for performing a specified task, but without any of the high-level consideration or background for why the task is being performed. The priority for procedures is ensuring complete detailed instructions so a task can be correctly completed by anyone qualified to follow the directions.
To complete our car analogy, the procedures for implementing the “changing the oil” technique would be specific to the car being maintained. This would include all the information about frequency of change, type of oil, type of filter, location of drain plug, tools required, etc. The procedures should be such that anyone (well, almost anyone) would be able to perform the task described using these directions.
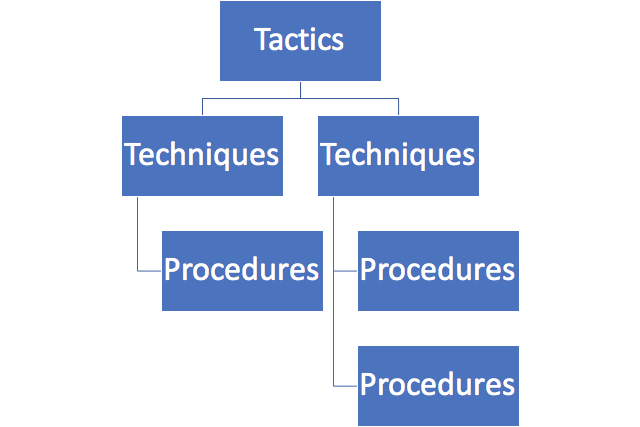
Presenting Tactics, Techniques, and Procedures as a hierarchy can help to visualize the relationships between them. To accomplish the desired Tactics it will be necessary to use one or more Techniques. To complete the desired Techniques there will need to be one or more Procedures to follow. What differentiates “advanced” threat actors from others is their ability to implement new Techniques or sophisticated Procedures that can’t easily be replicated by others, though their Tactics are largely the same as others.
How does this relate to “cyber”?
While TTP has been used to describe conventional warfare, it can also be very useful in describing cyber security. Fortunately, the MITRE ATT&CK Matrix is already laid out in a way that utilizes this structure and provides an excellent single source for security based TTPs.
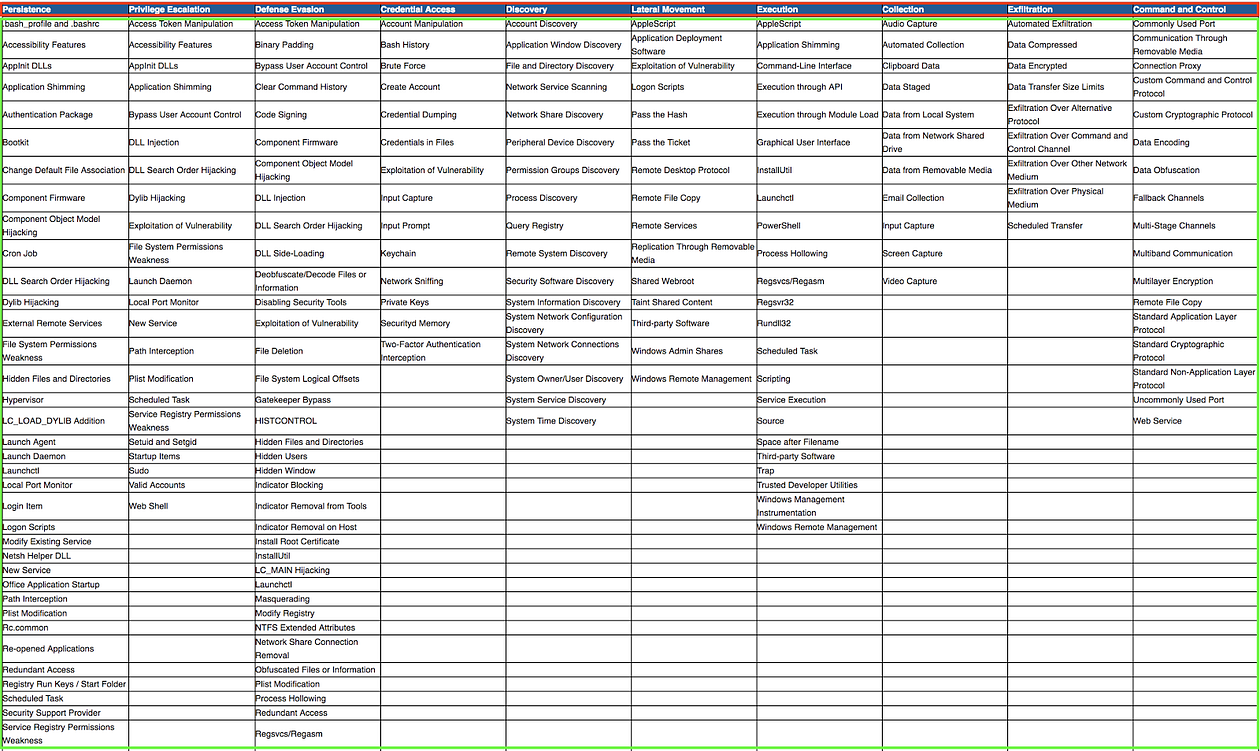
The column headers represent the various high level Tactics (highlighted in red) that an attacker utilizes as part of the cyber attack cycle. The individual entries in the Matrix under the Tactics represent the Techniques (highlighted in green). As we previously discussed, for each Tactic, numerous Techniques are listed. When you go click on any Technique, it will take you to a page with additional details of the Technique, including examples of real use by malicious actors. These examples represent the Procedures used and provide detailed analysis of the exact actions taken and resources used. Procedures can also be viewed as the specific hashes or exact tools and command lines used for specific malicious activity. MITRE ATT&CK provides an easily accessible TTP breakdown regarding computer security.
For example, when an attacker needs to access computers or resources on the network that aren’t on their initial foothold, they have to implement the Tactic of Lateral Movement. One popular Technique is to use the built-in Windows administrative shares, C$ and ADMIN$, as a writeable directory on the remote computer. A Procedure to implement this technique could be to use the SysInternals PsExec tool, which creates a binary to execute a command, copies it to a Windows Admin Share, and starts a service from that share. Blocking the SysInternals PsExec tool won’t completely remove the risk of the Windows Admin Shares Technique; an attacker can simply use a different Procedure, such as net use or the PowerShell cmdlet Invoke-PsExec. Understanding the specificity of attack and defensive countermeasures is crucial when evaluating the effectiveness of security controls.
Why does this matter?
Other than trying to clarify the use of “TTP”, why does any of this old military jargon matter in a modern computer-run world? The fact is, this approach to understanding malicious activity will make you a better attacker or defender. Being able to break down complicated attacks into TTPs will help make detection or replication of the attacks much easier to understand.
An understanding of the different Tactics involved in information security will help plan out any areas of deficiency in your personal experience of corporate environment and can focus effort where you may currently be lacking knowledge/coverage. For example, the “Assume Breach” mentality is a recognition that effective cybersecurity must recognize the other Tactics used by attackers, instead of focusing entirely on preventing initial compromise. This high-level perspective will help prevent an oversight in some part of the security program.
Understanding the difference between Techniques and Procedures is also incredibly important. Many network security tools and threat intelligence feeds focus on the specific Procedures used by an actor (such as tool hashes, file names, and C2 domains/IPs) rather than the overarching Technique in use. Occasionally, the security community will label something a new Technique, when it should more accurately be called a new Procedure for an existing Technique. Knowing the underlying technique and being able to adapt specific procedures will make you a better operator, regardless of what role you fill.
As the old adage goes “Give a man a fish, and you feed him for a day. Teach a man to fish, and you feed him for a lifetime.” When considering network defense, giving a fish is like focusing on brittle indicators from attacker Procedures (like hashes and specific IPs). It may meet your needs temporarily, but its effectiveness will be short-lived. Teaching to fish is focusing on the Technique in use, understand the technology and behaviors related to an attack, and creating resilient countermeasures that will work even when the attacker adapts or creates new Procedures.
Hopefully this post was helpful in clarifying the difference between Tactics, Techniques, and Procedures as well as highlighting the benefit of understanding each term.


