Perfect is the Enemy

At some point early in my career, I heard a phrase that has stuck with me over the years; “Perfect is the enemy of good.” I’ll be honest, at first, I didn’t really understand what it meant (which is probably why I remembered it). How could this be the case? Throughout education and any type of testing, you are always pushed to do things as perfectly you can, so how could trying to achieve perfection possibly be a bad thing? It wasn’t until some time had passed that I realized the intent and wisdom of “perfect” being the enemy and what “good” meant, especially in information security.
Pareto Principle
Many people have heard of the 80/20 rule, or more accurately the Pareto Principle, which originated with the observation by Italian economist Vilfredo Pareto that 80% of the land in Italy was owned by 20% of the population back in 1896. It turns out that this concept, where the distribution of return for resources in uneven, did not just apply to land ownership in Italy and has proven to be applicable in many different areas. It is now a generally accepted observation that 80% completion of a task require 20% of the work, the remaining 20% takes 80%. This is displayed in the graphic below.
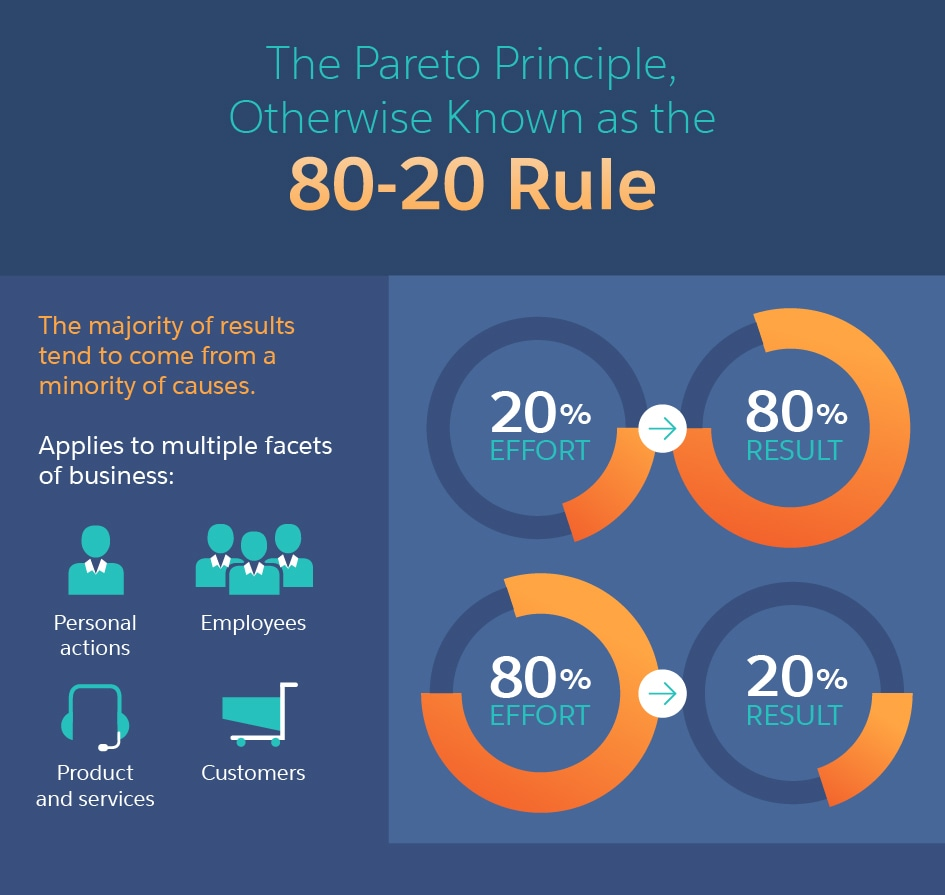
A real world example of this occurred in 2002 at Microsoft. Steve Ballmer sent at an email to enterprise customers which stated:
“One really exciting thing we learned is how, among all these software bugs involved in the report, a relatively small proportion causes most of the errors. About 20 percent of the bugs causes 80 percent of all errors, and — this is stunning to me — 1 percent of bugs caused half of all errors.”
In an ideal world, everyone would have unlimited time, money, and knowledge to apply to solving any problems that life or work may throw their way. Unfortunately, we do not exist in that world. The reality is that those are all finite resources that must be managed in order to solve problems and make progress.
As I learned more about the Pareto Principle and saw the large amount of effort that it took to achieve 100% completion of a task, I started to ask myself: “How valuable was that last 20%? Was it worth so much of my time to actually try to get to 100% or could that time be better leveraged getting to 80% somewhere else?”
I realized that I have been making this calculation back when I was in college studying for final exams. In classes where I was doing well, I was less worried about studying for the final and instead focused my efforts on classes where I was performing more poorly.
Finally, I understood the meaning of “perfect being the enemy of good.” While it is always desirable to achieve the 100% solution, sometimes that is not actually the best thing to do. In fact, sometime pursuing perfection can cause a negative outcome. If I were to get a perfect final exam score, but fail my other finals, that could put my overall college degree at risk.
Applying this to information security
Applying the Pareto Principle to information security, with only “20% of effort” we should be able to achieve an “80% solution.” However, this level of completeness is often not acceptable to an organization. A solution that can be evaded in some fashion is not complete until all evasion methods are identified and the perfect solution is created. Unfortunately, it is often the case that during the development of the “perfect” 100% solution, there is nothing in place until the full solution is identified. There is a balance between the risk of only having an 80% solution and the extra time it takes to have a perfect detection.
My personal opinion is that just because methods exist that can circumvent a security control does not mean that it does not provide any value to an organization or increase the overall security posture. Striving to quickly achieve the 80% solution and implement it in the environment can quickly yield positive benefits. If a detection or tool must be perfect before implementation, it will take much longer to implement, if ever. Additionally, the 80% solution can always be improved on and known deficiencies can be documented for future work. Rather than focus on the things that can be gained with a partial solution, the focus is often on the areas where there are problems. In pursuit of perfection, the end result is often nothing. I have further discussed how this applies in several different areas of information security as well below.
Detections
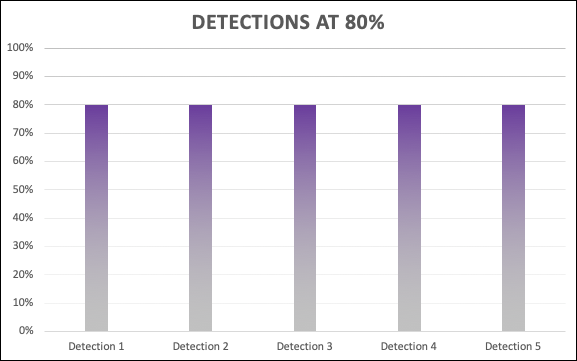
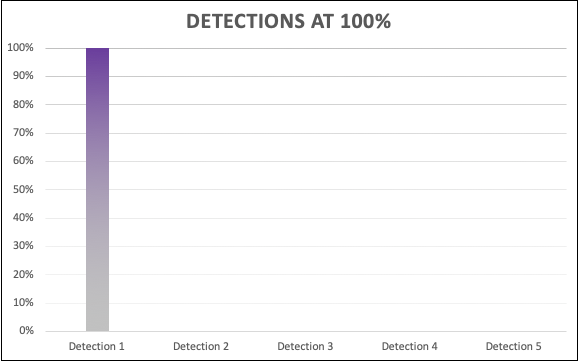
Breaches or compromises do not happen in a vacuum. Most, if not all, involve an attacker performing a wide variety of techniques across multiple systems in an environment to achieve their end objective. This is an important concept to understand because it means an organization doesn’t have to detect EVERYTHING in order to detect an attack, it just has to detect ONE of the techniques used. This is commonly referred to as the “Attacker’s Dilemma,” where a single indicator or alert can tip off incident response and halt an attack. Why does this matter? Well if we can create good 80% detections across a large number of techniques, we have a much greater chance of catching some element of attacker activity. This enables building a “minefield” of detections in an environment where an attacker cannot be sure what activity is safe and what is not. This provides a depth of coverage as there is not a single point of detection failure. The alternative would be to attempt to slowly create perfect detections. The statistics of evading a large number of 80% detections is small and the more 80% detections in place, the smaller the odds.
Which would you prefer using the same level of effort?
Investigations
While performing an investigation following a compromise, is it alway necessary to determine the full origin and intent of every attack that takes place? Perfect investigations take a large amount of time and often will yield little actionable value. Identifying what are the key aspects of an investigation (was sensitive data compromised, were sensitive systems compromised, was there lateral movement) is more important than reverse engineering every sample that ever land in your environment. Without realizing it, many people already accept the “good” solution every time they use any virtualized malware sandbox. Malware could deploy various anti-forensic techniques, however there is still often valuable information that can be gleaned. It is important to weight the time and resources invested into investigations to make sure that effort is warranted.
Tools
The perfect security tool doesn’t exist. This is not to bash on any vendors or be doom and gloom, it is just the reality, otherwise there would be no breaches! With this in mind, rather than spending all of your time trying to find the “perfect” solution, instead identify what critical features you must have, then find the tool that most closely aligns with those features. Learn what the limitations are of the tools you possess in your environment and focus future efforts on supplementing those areas.
Conclusion
Learning to embrace “good enough” can be a tough challenge. It is hard to stop striving for the perfect solution and learn to embrace the good solution at hand. To summarize this post, I will end with one more quote from General George Patton: “A good plan, violently executed now, is better than a perfect plan next week.” Focus on identifying and implementing good plans that are readily available. Stop chasing perfection.


