CVE-2019–12757: Local Privilege Escalation in Symantec Endpoint Protection

Symantec Endpoint Protection Version: 14.2 RU1 Build 3335 (14.2.3335.1000) and below
Operating System Tested On: Windows 10 1803 x64
This vulnerability was found in conjunction with Marcus Sailler, Rick Romo and Gary Muller of Capital Group’s Security Testing Team
Preconditions:
In order for this vulnerability to be reliably exploited, Symantec Endpoint Protection’s “Tamper Protection” feature needs to be disabled. Tamper protection being disabled in massive organizations is a common thing that is observed. It is my stance that this is a vulnerability regardless if Tamper Protection is enabled or not. With this feature disabled (we have seen various environments with this disabled or tuned down), exploitability of the vulnerability is high. With Tamper Protection enabled, the vulnerability still exists but exploitability is much, much lower. We haven’t taken the time to reverse the filter driver, but this could still potentially be exploited with tamper protection on.
Vulnerability Overview
When a scan is started, the ccSvcHst.exe process (as NT AUTHORITY\SYSTEM) checks for user-specific scan settings located at “HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler\<USERSID>\Custom Tasks\”.
When created, this key is granted “FullControl” rights to the currently logged-on user. It is possible to create a registry symbolic link on “HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler\<USERSID>\” and point it to an arbitrary location in the machine registry hive, resulting in an arbitrary registry key write primitive as “NT AUTHORITY\SYSTEM” with a permissive DACL. This can be used to fully elevate privileges on the host.
Vulnerability Explanation
When a scan is started, the ccSvcHst.exe process (as NT AUTHORITY\SYSTEM) checks for user-specific scan settings located at “HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler\<USERSID>\Custom Tasks\”.
If the logged-on user’s Security Identifier (SID) isn’t already in the “HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler” registry path, ccSvcHst.exe will create it (as NT AUTHORITY\SYSTEM):

While doing so, ccSvcHst.exe explicitly sets the Discretionary Access Control List (DACL) to contain an Access Control Entry (ACE) that permits the currently logged on user “FullControl” rights over the HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler\<USERSID>” key.
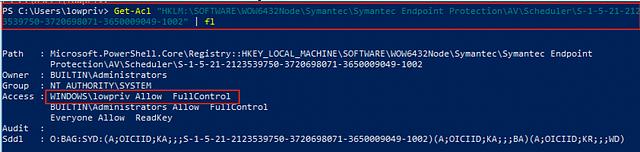
Since the logged-on user has “FullControl” over “HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler\<USERSID>\”, it is possible to delete it and replace the key with a registry symbolic link to an arbitrary location in the HKLM registry hive.
In this instance, we are replacing “HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler\<USERSID>\” with a symbolic link that points to “HKLM\ SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsqmcons.exe”
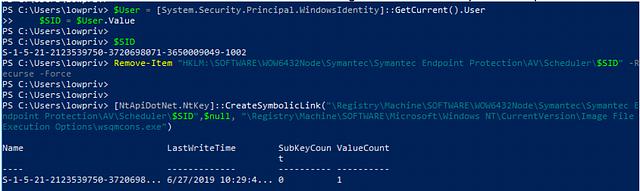
Doing so basically points “HKLM\SOFTWARE\WOW6432Node\Symantec\Symantec Endpoint Protection\AV\Scheduler\<USERSID>\” to “HKLM\ SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsqmcons.exe”. When ccSvcHst.exe tries to create this key when a scan starts, it will hit the symbolic link and create “HKLM\ SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsqmcons.exe” instead.
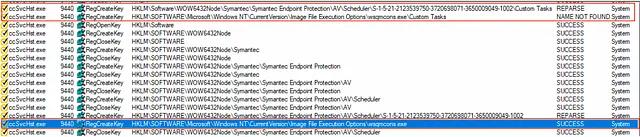
When ccSvcHost.exe creates “HKLM\ SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsqmcons.exe” via the symbolic link, it does so while granting the currently logged-on user “FullControl” over the key:
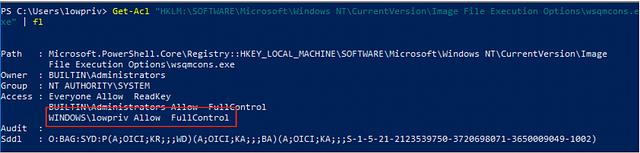
Since the currently logged-on user now has “FullControl” rights over the Image File Execution Options registry key for the “wsqmcons.exe” executable, we can simply create the “Debugger” registry key and point it to our payload. In this case, it will simply be “C:\Windows\System32\cmd.exe /c cmd.exe”.
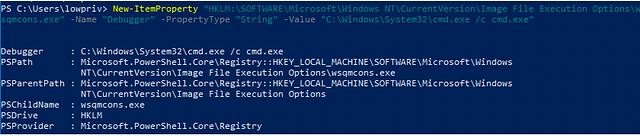
The reason for picking “wsqmcons.exe” as the executable to set the IFEO debugger value on is that there is a scheduled task called “Consolidator” that exists by default on Windows 10. This scheduled task runs as “NT AUTHORITY\SYSTEM” and starts “wsqmcons.exe”. With our “malicious” debugger set to “wsqmcons.exe”, our payload will run when the scheduled task “Consolidator” starts.
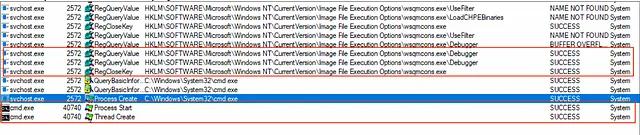
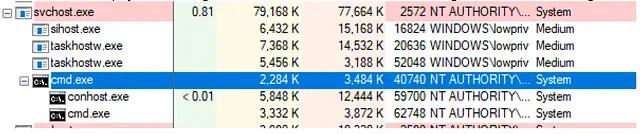
This results in our payload running as “NT AUTHORITY\SYSTEM”, resulting in Local Privilege Escalation:
Proof of Concept code can be found here: https://gist.github.com/enigma0x3/5dbb9a72b592992b27dd703edb4c20b1
This vulnerability has been fixed in Symantec Endpoint Protection (SEP) 14.2 RU2 and Symantec Endpoint Protection Small Business Edition (SEP SBE) 12.1 RU6 MP10d via CVE-2019–12757
DISCLOSURE TIMELINE
As committed as SpecterOps is to transparency, we acknowledge the speed at which attackers adopt new offensive techniques once they are made public. This is why prior to publicization of a new bug or offensive technique, we regularly inform the respective vendor of the issue, supply ample time to mitigate the issue, and notify select, trusted vendors in order to ensure that detections can be delivered to their customers as quickly as possible.
- June 27th, 2019: Vulnerability identified in conjunction with Capital Group’s Security Testing Team
- June 27th, 2019: Joint disclosure with Capital Group began. Symantec PSIRT case is opened
- July 10th, 2019: Symantec PSIRT confirmed the vulnerability
- July 25th, 2019: Symantec PSIRT communicated the intention to fix the vulnerability in the next SEP release
- August 28th, 2019: Symantec PSIRT informed us that the release will be pushed out to October/November
- September 16th, 2019: Update requested
- September 17th, 2019: Symantec PSIRT confirmed that the release date is still pushed back to October/November
- October 16th, 2019: Requested an update on the estimated release date
- October 16th, 2019: Symantec PSIRT confirmed a release date of November 8th, 2019
- November 7th, 2019: Symantec PSIRT informed us that the release date is delayed and the new date is November 14th, 2019
- November 14th, 2019: Fix published


