Getting the Most Value Out of the OSCP: Pre-Course Prep
Feb 12 2025
By: Kieran Croucher • 20 min read
TL;DR The first post in a five-part practical guide series on maximizing the professional, educational, and financial value of the OffSec certification pursuit for a successful career in offensive cybersecurity consulting.
DISCLAIMER:
All opinions expressed in this article are solely my own. I have reviewed the content to ensure compliance with OffSec’s copyright policies and agreements. I have not been sponsored or incentivized in any way to recommend or oppose any resources mentioned in this article.
Introduction
Love it or hate it, the Offensive Security Certified Professional (OSCP) remains a significant hurdle for many aspiring offensive security consulting professionals. While the course and exam offer undeniable educational value, I believe there are underappreciated practical steps students can take during their “OSCP journey” to strengthen their candidacy and develop the essential soft and technical skills needed for success in the field. In this post (hopefully the first of a small series), I’ll explore three pieces of practical advice for students to consider before enrolling in the course. In future posts, I hope to explore more advice tailored to distinct phases of the OSCP journey.
Get your OSCP+ certification with PEN-200 | OffSec
PEN-200 is OffSec's foundational pentesting course– learn and practice the latest techniques. Earn your penetration testing certification (OSCP & OSCP+).
www.offsec.com

A Little Bit About Me
I am an associate consultant in the offensive security consulting industry, having successfully transitioned from a career as a software engineer in information technology (IT). While my background in offensive security consulting is still growing, I feel that my recent experience as a student trying to earn the OSCP certification (or, as I like to call them, “OSCP-hopefuls”) and my successful pivot into this field have provided me with valuable insights to share on this topic.
Some Background Context
The OSCP is a popular cybersecurity certification that tests an individual’s ability to identify, exploit, and report on misconfigurations/vulnerabilities affecting web applications, common network services, and the Linux and Windows operating systems. Maintained by OffSec (formerly Offensive Security), the certification stands out due to its rigorous exam, which requires candidates to complete a 24-hour practical black-box penetration testing scenario. Students are given an additional 24 hours to write and submit a report for grading. To earn the OSCP, candidates must successfully exfiltrate a minimum number of “flags” and submit a satisfactory report.
Infosec & Cybersecurity Training | OffSec
Build cyber workforce resilience with our unmatched skills development and hands-on learning platform and library.
www.offsec.com

Employers widely recognize the OSCP as a valuable credential for entry-level roles in the offensive security consulting industry, which includes cybersecurity services like penetration tests, red team engagements, and purple team exercises. Its frequent appearance in job postings (which has earned it the joking moniker, “the LSAT for hackers”) and the challenging nature of the exam for junior ethical hackers make it a significant milestone. As a result, it’s common for students who pass the exam to altruistically share their experience in OSCP journey articles, offering insights to others who are on the same path, detailing what they studied, how they approached the exam, and their personal takeaways.
I was originally going to write my own article following this same prototype, but recent developments led me to reconsider. Although I passed the exam in March 2024, the OSCP exam underwent a significant format change in September 2024. Given these changes, I felt that a “review” of my OSCP journey would likely be outdated.
So Why Are You Writing This?

While I consider the OSCP a strong addition to my resume, I’ve found that much of the “value” I gained from the pursuit of the OSCP — value I’ve leveraged during job applications and in my current role — came from unexpected places. As it turns out, the OSCP journey is just as important, if not more so, than the credential itself. With that in mind, I felt compelled to share specific details of my OSCP experience, the lessons that served me well, and the actions I would take if I could go back and do it all over again.
If you look at the bulk of OSCP-related content online, it’s clear that the focus is overwhelmingly on developing the technical mastery needed to pass the exam. While this focus is understandably important, it overlooks the broader picture. The exam itself, along with the technical content required to pass it, offers valuable lessons, but they’re just one part of the overall journey that can contribute to a thriving career in offensive security.
This article aims to fill that gap by offering practical advice that students can follow to not only pass the OSCP but also to grow into well-rounded penetration testers. Some of this advice may be considered “extra mile” exercises, while others are proactive steps that can be employed more passively. Regardless, all of them are designed to help candidates maximize the professional, personal, and financial value of earning an OSCP certification.
A Few Disclaimers Before We Dive In

- Article Structure: Due to the length of my original draft, I decided to split this post into a five-part series representing each “phase” of the OSCP journey: 1) pre-course preparation, 2) during the course, 3) during the labs, 4) during the exam, and 5) after the exam (pass or fail)
- Target Audience: While the primary audience for this article is for students hoping to break into the offensive security consulting industry, I do not mean to discount or exclude individuals who have already secured a consultant role or are pursuing the OSCP for other reasons such as personal enrichment or workplace/regulatory compliance (luckily, I believe much of my advice still generally applies to these individuals)
- Not an Endorsement: This article is not an endorsement of the OSCP itself (at various points in this series, I will submit what I believe to be valid but fair criticism of the credential), but rather a vehicle to share insights from my personal experience with the certification
- No Guarantees: I cannot promise that students who follow this advice will pass the OSCP exam or successfully pivot into the offensive security consulting industry
- Other Paths are Valid: The OSCP is not a gatekeeper to the offensive security consulting industry (I know many junior to senior-level experts without the credential) and I would advise students to consider every path to a successful and fulfilling career before committing to the certification program
Before the Course…

“By failing to prepare, you are preparing to fail.” — Benjamin Franklin
Let’s start with advice that applies to students who are either considering enrolling in the PEN-200: Penetration Testing with Kali Linux course or are actively planning to. If you could walk away from this article with just three takeaways, here they are:
- Estimate whether the return on investment (ROI) will be positive or negative before committing to enrollment, and explore ways to reduce upfront costs
- If you’re preparing for the PEN-200 with external training, complete the training before enrolling and use that time to build your resume with practical and challenging achievements
- Start creating a reference guide (AKA a “command cheat sheet”) early to improve your testing efficiency and become more familiar with common offensive security tools
Consider the ROI

The OSCP is undeniably an expensive certification program. Given the steep financial and time commitments, one must consider whether the tangible and intangible benefits of the program represent a net-positive, neutral, or net-negative ROI relative to the candidate’s career goals and personal circumstances.
At the time of this article, the base cost of the OSCP certification starts at $1,749, which includes 90 days of access to the online course, lab materials, and a single exam attempt. However, a more realistic estimate — factoring in multiple exam attempts and lab extensions — can easily exceed $2,000. Individual exam retakes cost $250 each, while 30-day lab extensions cost $360 apiece. Additionally, many students choose to invest in external training resources, each with its own associated costs (more on that later). For those seeking an extended study period and additional benefits, the LearnOne subscription offers a year of course and lab access, two exam attempts, and other perks for $2,749/year.
Individual Pricing | OffSec
Content and course pricing at OffSec varies by difficulty level. We have options to fit different budgets and needs for individual learners and organizations.
www.offsec.com

Additionally, studying for the OSCP is a significant time investment, and failed exam attempts include mandatory cooldown periods that can further extend the overall timeline and costs. While everyone progresses through the PEN-200 course and labs at their own pace, the most effective approach is often a marathon pace, not a sprint. If you’re under a strict time constraint or primarily seeking quick, incremental resume boosters, the OSCP may not align with your current goals.
The OSCP is also not the only practical ethical hacking certification program available, many of which are more cost-effective. Some of these courses cover material that is not included in the PEN-200 course but is arguably critical knowledge in the offensive security consulting industry, such as command and control (C2) frameworks and their infrastructure, antivirus (AV) evasion techniques, and more sophisticated web application and Active Directory (AD) attack vectors. While my personal experience is limited to Zero Point Security’s Certified Red Team Operator (CRTO) certification, I’ve heard positive reviews of the Hack the Box Certified Penetration Testing Specialist (HTB CPTS) and Practical Network Penetration Tester (PNPT) credentials. These programs are comparable in difficulty and scope to the OSCP and, perhaps most notably, are currently below $500, making them a more affordable alternative to the OSCP.
Security Certification Roadmap – Paul Jerimy Media
IT Security Certification Roadmap charting security implementation, architecture, management, analysis, offensive, and defensive operation certifications.
pauljerimy.com
It should also be noted that certification programs are just one of many pathways to a career in offensive security consulting. While they are often a key metric technical recruiters use to assess candidates, other accomplishments — such as independent ethical hacking projects, competitive tournaments, or content creation — can carry equal or even greater weight on an application. These alternative routes showcase not only technical expertise but also initiative, creativity, and passion for cybersecurity, most of which come at a much lower upfront cost.

Still, there are notable benefits to pursuing the OSCP. The PEN-200 course encompasses an impressive breadth of penetration testing knowledge and the exam itself is notoriously challenging. Considering this, the OSCP has earned a well-deserved reputation as a litmus test for prospective consultants and technical recruiters therefore eagerly seek OSCP-certified candidates. Additionally, the certification has been around for a relatively long time and has strong name-brand recognition in the industry. Finally, it includes an impressive set of lab networks for students to practically apply the technical skills learned during the course to an environment composed of intentionally vulnerable machines. This aspect in particular provides a well-defined path to an audience — mostly composed of entry-level ethical hackers — from beginner to professional-level penetration testing mastery.
There are also pragmatic reasons to pursue the OSCP. Although I don’t have specific metrics to support my claim, my anecdotal experience in the job market suggests that many organizations incorporate the OSCP in their hiring process. Some firms require candidates to hold the certification, model their technical interviews after the exam, or mandate new hires to earn the credential within a specified time frame. Earning the OSCP early in your job search could therefore open up more doors for you professionally. Moreover, if your next role represents a significant increase in base income, the associated costs of the OSCP may be offset relatively quickly.
One straightforward way to increase the ROI of an OSCP investment is to reduce the upfront cost associated with the bundle. For currently enrolled university students, OffSec offers a 10% discount on a LearnOne subscription through its Achieve financing program. OffSec has also historically held an annual sale on LearnOne subscriptions during November through January. Beyond OffSec, many nonprofits offer partial or complete discounts for common certification programs — including the OSCP — to successful applicants of scholarship programs. Many companies also provide professional development benefits, which can cover the cost of an OSCP voucher. This is especially common among cybersecurity consulting firms and serves as a compelling argument in favor of waiting until after securing a new position before enrolling in the PEN-200.
Pricing | OffSec
Course pricing at Offensive Security varies by difficulty level. We have options to fit different budgets and needs.
www.offsec.com

In summary, the OSCP is a significant financial investment and prospective students should not take it lightly. For many, it represents a major milestone in their ethical hacking journey, a source of personal growth, and a pathway to a new career. For others, its benefits may only be marginal or, depending on the circumstances, not in their best interests. Ultimately, the decision rests with the individual, who should weigh all the factors and considerations to determine if the OSCP is the right choice for them.
Build Your Resume While You Study

While the course provides robust hands-on training, many OSCP-hopefuls — including myself — supplement their PEN-200 training with additional resources to enhance their learning experience. By strategically choosing training options, you can not only deepen your technical knowledge but also strengthen your resume or CV, making your study efforts even more rewarding.
The official OffSec motto is “Try Harder”, which essentially means that successful problem solvers are persistent, creative, and open to new ideas. At the risk of sounding arrogant, I’d suggest adding another adjective to the mix: “retrospective”. Penetration testers and others who face recurring challenges throughout their careers are more likely to succeed if they can learn from past experiences and apply those lessons to current problems. External training, then, is a natural extension of the Try Harder mindset. It’s also prudent, since we can deliberately select exercises we can showcase on a resume, reference in cover letters, or leverage using the STAR method during behavioral interviews.

Generally, I recommend completing external resources before enrolling in PEN-200 for two reasons. First, supplemental training establishes a solid foundation in both theoretical knowledge and practical experience with tactics, techniques, and procedures (TTPs) before starting the course. Although PEN-200 assumes no prior experience in ethical hacking, having a baseline understanding of key concepts can make the course more manageable and improve your efficiency. Second, when you purchase a course and exam voucher, your access to the online course material and lab networks is automatically activated, and the expiration date is set. If you complete the course and labs before your access expires but still require additional training, any time spent on external resources during this period could have been used to take full advantage of OffSec’s official resources (such as reviewing the course material or writing reports on the lab networks, which I will discuss later in the series). Finishing most or all of your external training before starting PEN-200 ensures you aren’t wasting the expensive time you paid for by focusing on extrinsic resources.
Take full advantage of the low-pressure environment of external training by experimenting with different commands, refining your assessment methodology (more on that later in the series), and discovering which technology stack you enjoy hacking the most. Platforms like Hack the Box (HTB) and OffSec’s Proving Grounds are perfect for this. You may even pick up knowledge that isn’t covered in the PEN-200, giving you a potential edge when applying for jobs and helping you stand out as a candidate. Additionally, many external training platforms have active communities where learners can collaborate, share insights, and support each other. Building connections within these communities can provide valuable peer feedback, challenge your assumptions, and give you a sense of camaraderie as you navigate the complexities of penetration testing.
In conclusion, practical supplemental training offers the dual benefit of preparing you for the challenging PEN-200 course while strengthening your profile as a candidate for offensive security consulting roles. Below, I have included a table of my personal recommendations for practical training resources, including their costs and the types of challenges they offer. I have focused primarily on resources that I have personally used and are affordable, keeping in mind our previous discussion on ROI.
| Name | Cost | Description | Links |
|---|---|---|---|
| NetSecFocus Trophy Room | Free – $20/month | Curated by TJNull, a list of OSCP-aligned practical labs that can be pursued on HTB, Proving Grounds, and etc. | · NetSecFocus Trophy Room |
| IppSec Walkthroughs | Free – $20/month | High-quality video walkthroughs for retired HTB labs; treat the walkthroughs like a job shadowing exercise | · IppSec – YouTube · Ippsec Rocks |
| Dante and RastaLabs Pro Lab | $50/month | OSCP-aligned practical lab networks by HTB | · Hack the Box Pro Labs |
| PortSwigger Academy | Free | Guided walkthroughs for common web app vulnerabilities; focus on the server-side vulnerabilities relevant to PEN-200 syllabus and improve your literacy with the Burp Suite tool | · SQL Injection · Path Traversal · OS Command Injection · File Upload Vulnerabilities · API Testing |
| TryHackMe Learning Paths | Free – $14/month | OSCP-aligned guided practical course and labs | · Pre Security Training · Jr Penetration Tester Training · Offensive Pentesting Training · Web Application Pentesting Training |
| TCM Practical Ethical Hacking | Free | The discontinued versions of flagship TCM courses, now available for free on YouTube | · Ethical Hacking in 15 Hours – Part 1 · Ethical Hacking in 15 Hours – Part 2 · Ethical Hacking in 12 Hours · Linux Privilege Escalation · Windows Privilege Escalation |
| Personal Lab | Cost varies | Customizable lab tailored to individual learning goals | · Game of Active Directory (GOAD) · Ludus · Marvel-Lab 2.0 |
Begin Writing a Reference Guide

A reference guide is essentially a structure where consultants store key information they need to recall during engagements, such as command syntax or the requirements to launch a specific attack — essentially a “cheat sheet”. Not only is this type of resource valuable for the OSCP labs and exam, but it can also be an asset during a live engagement or published as a personal project that can be included on a job application.
I personally find command reference guides incredibly useful in both simulated training environments and live engagements. A well-organized, personalized reference guide not only improves your efficiency but also reinforces your assessment methodology, core-concept understanding, and technical writing abilities. Think of your guide as a living document that evolves alongside your growth as an ethical hacker, serving as a modular and reliable resource. Starting your reference guide early — even before beginning the PEN-200 course — can significantly enhance your testing efficiency and tool expertise.
A reference guide can arguably be started at any point in the OSCP journey, but I chose to include it in the “Pre-Course” section for multiple reasons. First, the guide should ideally transcend the OSCP and be useful for any ethical hacking project, so it makes sense to include it in one of the sections separate from the PEN-200 material. Second, if the student intends to pursue external training resources, they are bound to encounter useful tools before starting the course, making it prudent to document their usage. Finally, maintaining a reference guide is a continuous process, so I would like to get students in the habit of writing reference guides early as opposed to much later in the OSCP journey.
My favorite tool for creating reference guides is Obsidian, a free and cross-platform node-based note-taking utility. It offers a rich set of features, including an interactive graph, Markdown language support, a tagging system, and much more. Other node-based programs worth considering are Microsoft OneNote, Standard Notes, and CherryTree.
Obsidian – Sharpen your thinking
The free and flexible app for your private thoughts.
obsidian.md

Let’s take impacket-GetUserSPNs as an example. This tool is part of Fortra’s Impacket suite and is based on the original GetUserSPNs.py module. It automates the “Kerberoasting” attack, which allows attackers to retrieve the password hash of a service account in an AD environment.
impacket/examples/GetUserSPNs.py at master · fortra/impacket
Impacket is a collection of Python classes for working with network protocols. – fortra/impacket
github.com
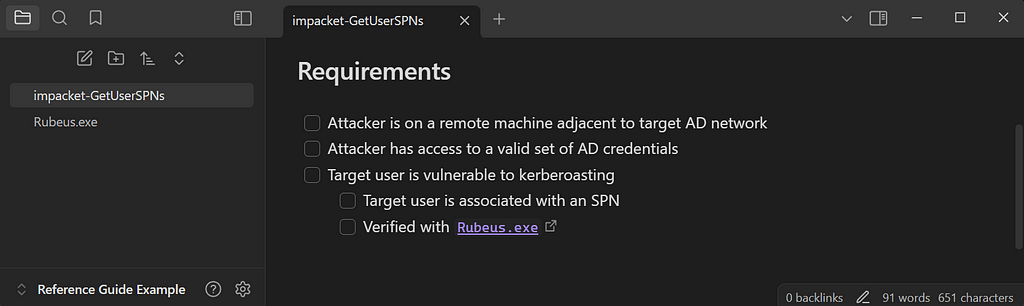
If we were writing a page for this tool in Obsidian, we could start with an overview section. This would include a link to the source code for the tool, as well as the MITRE ATT&CK framework page for Kerberoasting.
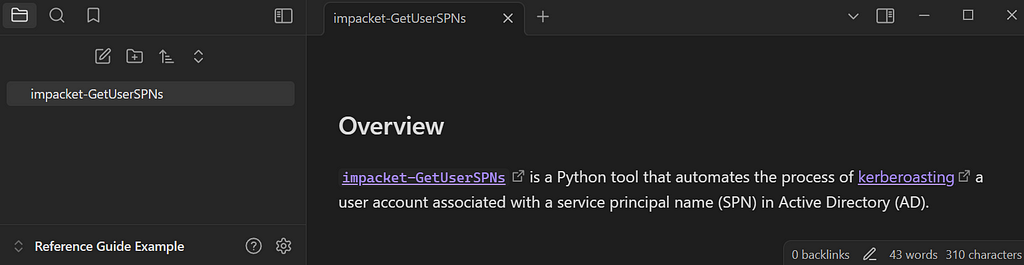
Next, we need to define the requirements necessary for this attack to be feasible. In this case, we should note that the attacker needs access to a valid credential set in AD and that the target user(s) must be a service account associated with a Service Principal Name (SPN). Additionally, it’s important to mention that this tool can be executed remotely from the attacker’s Linux machine on the same network, as some tools require execution on a victim’s Windows machine or through a C2 framework like Cobalt Strike. If verifying the feasibility of an attack requires additional tools, we can create links to other Obsidian pages and embed them here.
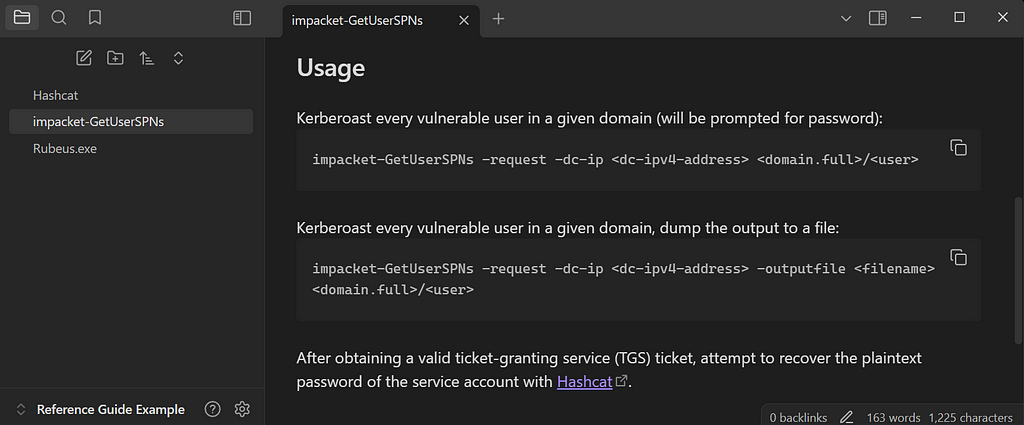
Next, we should include some command examples. Tools like impacket-GetUserSPNs often have many different command-line arguments and optional flags, so it’s best to prioritize the ones most relevant to you and omit the others.
Although it is considered [mostly] out of scope of the PEN-200 course, I still recommend including a section discussing how to enhance the “stealth” of a given command and thwart operational security (OPSEC) efforts. This is a critical topic in offensive security consulting and could help you stand out among other job candidates (a candidate who can demonstrate both technical aptitude with a given tool and how to use it stealthily is more desirable than one who only knows the former). While Kerberoasting is generally considered an “OPSEC-loud” technique, we will do our best to evade detection and explain our efforts in the OPSEC section. If you’re unsure whether a TTP can be made stealthier, consider researching it on resources like HackTricks or revisit this section later.

Finally, we will want to include the output from the command’s help menu (impacket-GetUserSPNs --help ).

If we wanted to go a step further, we could include an in-depth analysis of what happens “under the hood” when executing a typical Kerberoasting command. This would involve screenshots of the impacket-GetUserSPNs source code and network packets that Wireshark captured in a personal lab (more on this later in the series). Additionally, we could use Obsidian’s tagging system to link this page to a “kerberoasting” tag, unifying all other tools related to the Kerberoasting technique.
On a final note, a reference guide can serve multiple purposes depending on how you design it. A personalized guide — tailored to your study habits, tools, and workflow — can significantly improve your efficiency during exams or live engagements by helping you quickly locate critical information. If you’re like me and struggle with staying organized during an assessment, structuring your guide around an adversary emulation framework (e.g., the MITRE ATT&CK framework, Lockheed Martin’s Cyber Kill Chain, and Mandiant’s Targeted Attack Lifecycle) can support a systematic approach to problem solving. In any case, it is best to start writing your own guide early and continue building it as you progress on your ethical hacking journey.
Conclusion

I hope you enjoyed the first post in this series. If you have any comments, criticisms, or advice you think should have been included, please feel free to leave a comment. In the next post, I’ll explore additional advice for students as they begin reading the official PEN-200 course materials.
Getting the Most Value Out of the OSCP: Pre-Course Prep was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.