blog category
Research & Tradecraft

Research & Tradecraft
PHISHING SCHOOL Making Your Malware Look Legit to Bypasses EDR I wanted to write this blog about...
By: Forrest Kasler
Jul 30, 2024 • 8 min read
Read Post
Research & Tradecraft
PHISHING SCHOOL How to Bypass EDR With Custom Payloads If endpoint detection and response (EDR) protections keep...
By: Forrest Kasler
Jul 23, 2024 • 17 min read
Read Post
Research & Tradecraft
The Security Principle Every Attacker Needs to Follow
Earlier this year, I was tasked with developing a follow-on course for our renowned Adversary Tactics:...
By: Elad Shamir
Jul 17, 2024 • 12 min read
Read Post
Research & Tradecraft
PHISHING SCHOOL Bypassing Web Proxies so Your Phish Don’t Suffocate You just fought long and hard...
By: Forrest Kasler
Jul 16, 2024 • 13 min read
Read Post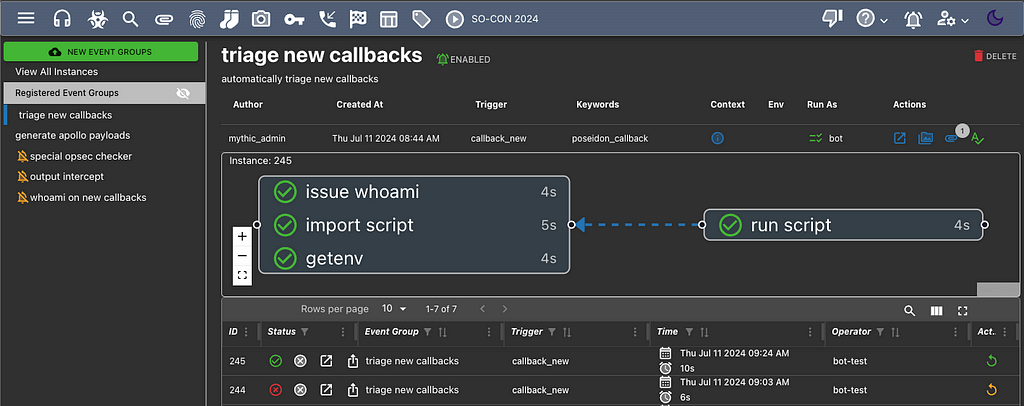
Research & Tradecraft
Mythic 3.3 Beta: Rise of the Events
A brief overview of Mythic 3.3’s new features Eventing Flows Mythic 3.3 Updates Mythic 3.3 has too many...
By: Cody Thomas
Jul 15, 2024 • 8 min read
Read Post
Research & Tradecraft
PHISHING SCHOOL How to Make Your Phishing Sites Blend In As you read this, bots are coming...
By: Forrest Kasler
Jul 9, 2024 • 12 min read
Read Post
Research & Tradecraft
Like Shooting Phish in a Barrel
PHISHING SCHOOL Bypassing Link Crawlers You’ve just convinced a target user to click your link. In doing...
By: Forrest Kasler
Jul 2, 2024 • 14 min read
Read Post
Research & Tradecraft
An AWS Administrator Identity Crisis: Part 1
BLUF: Every attack path needs a destination. This is a formalized way of describing destinations in...
By: Daniel Heinsen
Jun 28, 2024 • 11 min read
Read Post
Research & Tradecraft
I Will Make you Phishers of Men
PHISHING SCHOOL Convincing Targets to Click Your Links When it comes to phishing advice, the number one...