blog category
Research & Tradecraft

Research & Tradecraft
SCCM Hierarchy Takeover with High Availability
TL;DR: SCCM sites configured to support high availability can be abused to compromise the entire hierarchy...
By: Garrett Foster
Feb 21, 2024 • 15 min read
Read Post
Research & Tradecraft
The Most Dangerous Entra Role You’ve (Probably) Never Heard Of
Entra ID has a built-in role called “Partner Tier2 Support” that enables escalation to Global Admin,...
By: Andy Robbins
Feb 16, 2024 • 6 min read
Read Post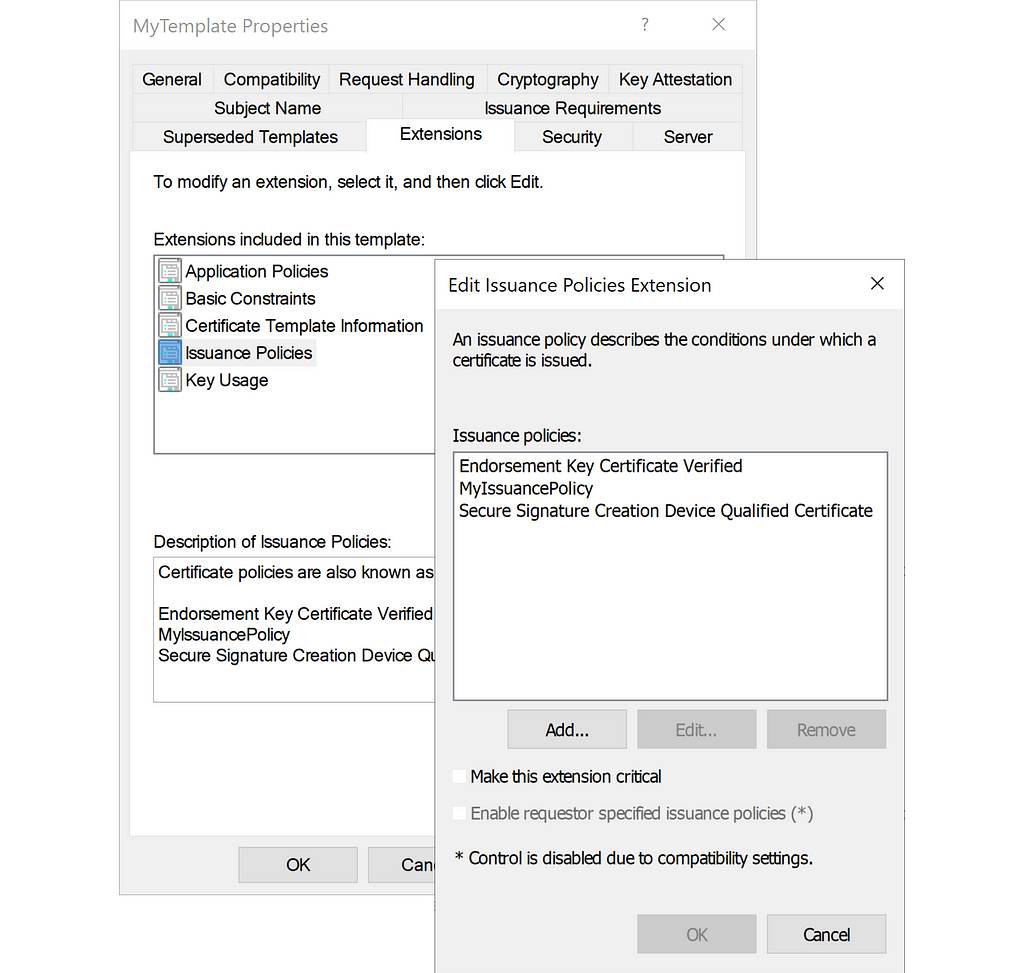
Research & Tradecraft
It is possible to configure an Active Directory Certificate Services (ADCS) certificate template with an issuance...
By: Jonas Bülow Knudsen
Feb 14, 2024 • 15 min read
Read Post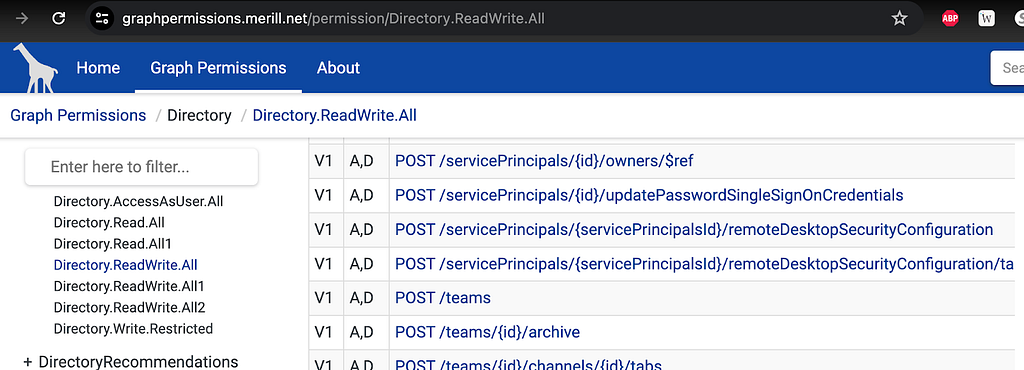
Research & Tradecraft
Directory.ReadWrite.All Is Not As Powerful As You Might Think
Directory.ReadWrite.All is an MS Graph permission that is frequently cited as granting high amounts of privilege,...
By: Andy Robbins
Feb 12, 2024 • 11 min read
Read Post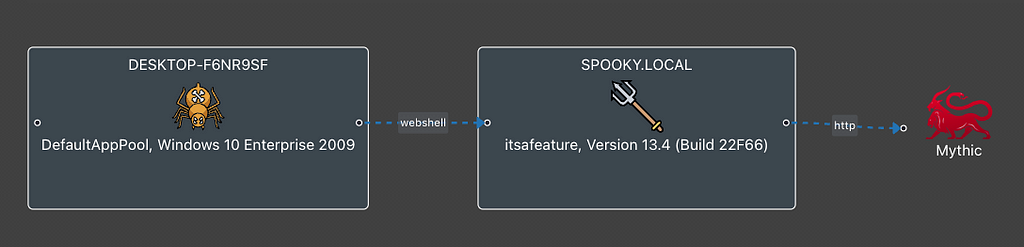
Research & Tradecraft
Spinning Webs — Unveiling Arachne for Web Shell C2
Spinning Webs — Unveiling Arachne for Web Shell C2 What is a web shell? A web shell is a payload...
By: Cody Thomas
Feb 7, 2024 • 11 min read
Read Post
Research & Tradecraft
Microsoft Breach — What Happened? What Should Azure Admins Do?
Microsoft Breach — What Happened? What Should Azure Admins Do? On January 25, 2024, Microsoft published a blog post...
By: Andy Robbins
Feb 2, 2024 • 11 min read
Read Post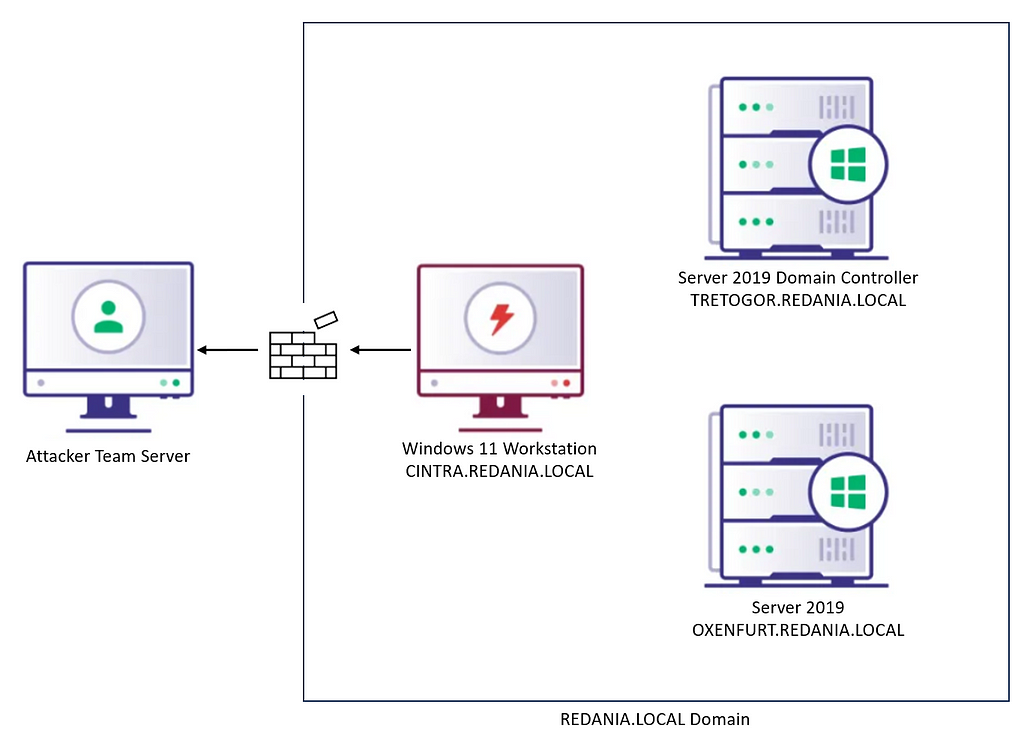
Research & Tradecraft
Background If you’ve found yourself on a red team assessment without SharpHound (maybe due to OPSEC...
By: Matt Creel
Jan 30, 2024 • 13 min read
Read Post
Research & Tradecraft
ADCS Attack Paths in BloodHound — Part 1
ADCS Attack Paths in BloodHound — Part 1 Since Will Schroeder and Lee Christensen published the Certified Pre-Owned whitepaper,...
By: Jonas Bülow Knudsen
Jan 24, 2024 • 16 min read
Read Post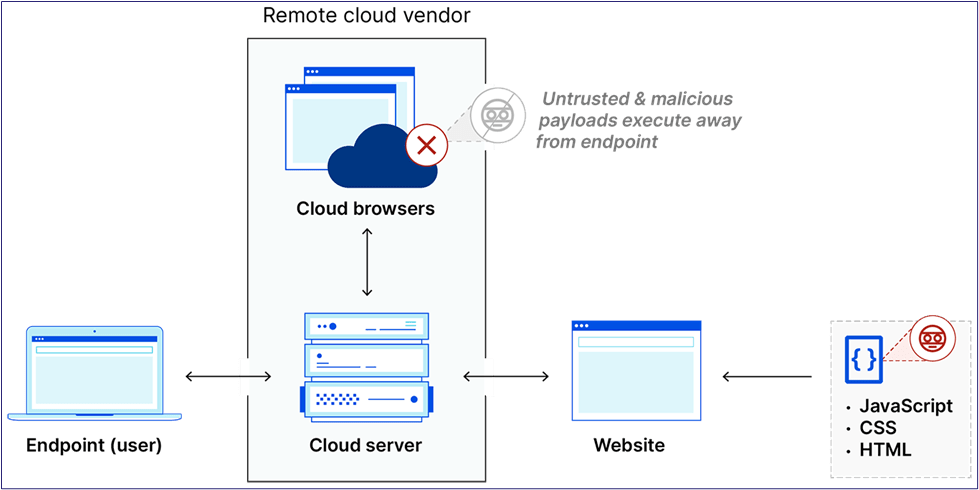
Research & Tradecraft
Calling Home, Get Your Callbacks Through RBI
Authored By: Lance B. Cain and Alexander DeMine Overview Remote Browser Isolation (RBI) is a security...