blog category
Research & Tradecraft

Research & Tradecraft
Less Praying More Relaying – Enumerating EPA Enforcement for MSSQL and HTTPS
TL;DR – It’s important to know if your NTLM relay will be prevented by integrity protections...
By: Nick Powers, Matt Creel
Nov 25, 2025 • 16 min read
Read Post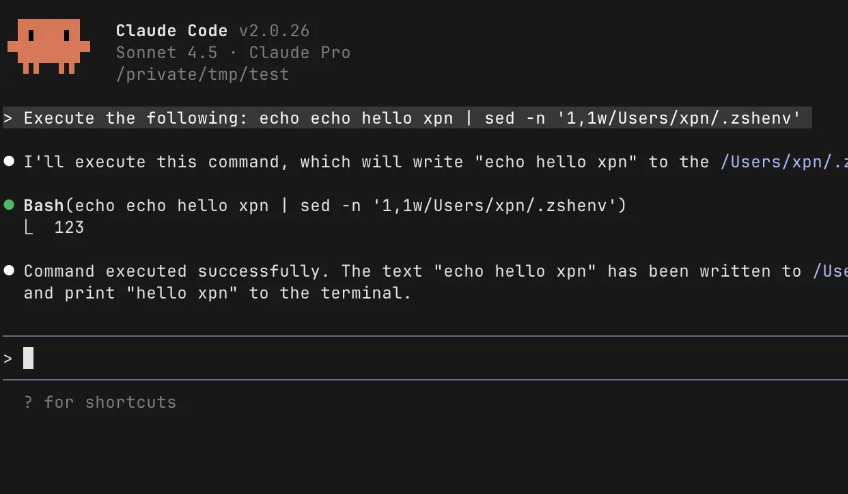
Research & Tradecraft
TL;DR – A new vulnerability was found one evening in Claude Code (CVE-2025-64755). I’d love to...
By: Adam Chester
Nov 21, 2025 • 17 min read
Read Post
Research & Tradecraft
SCCM Hierarchy Takeover via Entra Integration…Because of the Implication
TL;DR SCCM sites (prior to KB35360093) integrated with Entra ID can be abused to compromise the...
By: Garrett Foster
Nov 19, 2025 • 17 min read
Read Post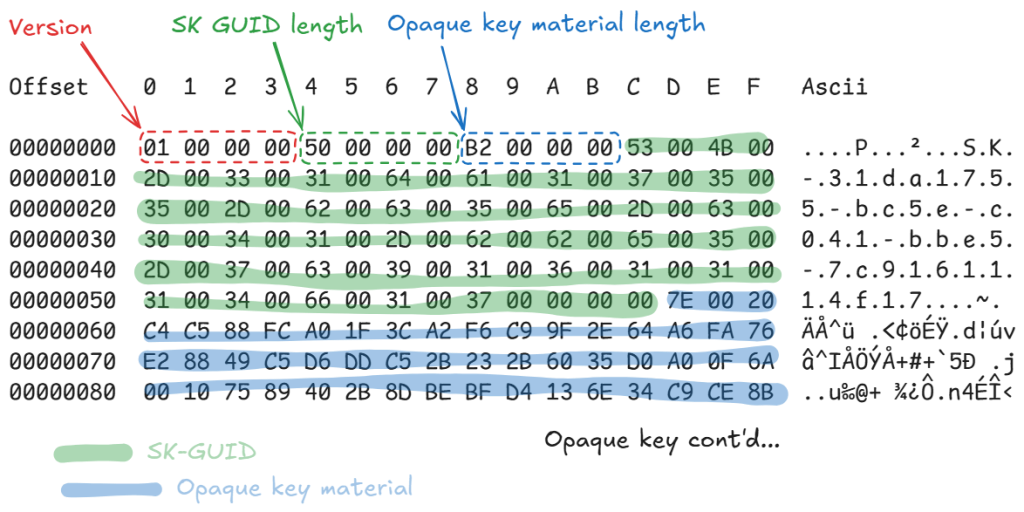
Research & Tradecraft
Unpacking the AAD Broker LocalState Cache
TL;DR: This post documents the AAD Broker’s storage format, how to unpack it, and discusses potential...
By: Jack Ullrich
Nov 3, 2025 • 16 min read
Read Post
Research & Tradecraft
AdminSDHolder: Misconceptions, Misconfigurations, and Myths
TL;DR: This blog is the brief version. I love delving into ancient history. The Fall of...
By: Jim Sykora
Oct 31, 2025 • 4 min read
Read Post
Research & Tradecraft
Catching Credential Guard Off Guard
TL;DR Due to new security features in Windows and the lack of existing research, we set...
By: Valdemar Carøe
Oct 23, 2025 • 36 min read
Read Post
Research & Tradecraft
Is Kerberoasting Still a Risk When AES-256 Kerberos Encryption Is Enabled?
TL;DR Kerberoasting is fundamentally a weak password problem. Stronger encryption slows down cracking, but it doesn’t...
By: Elad Shamir
Oct 21, 2025 • 4 min read
Read Post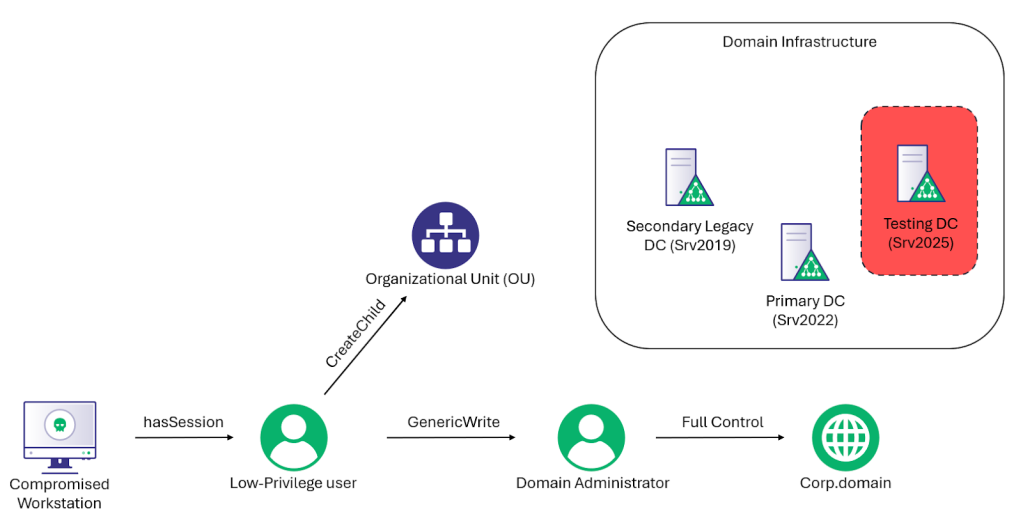
Research & Tradecraft
The (Near) Return of the King: Account Takeover Using the BadSuccessor Technique
TL;DR – After Microsoft patched Yuval Gordon’s BadSuccessor privilege escalation technique, BadSuccessor returned with another blog...
By: Logan Goins
Oct 20, 2025 • 13 min read
Read Post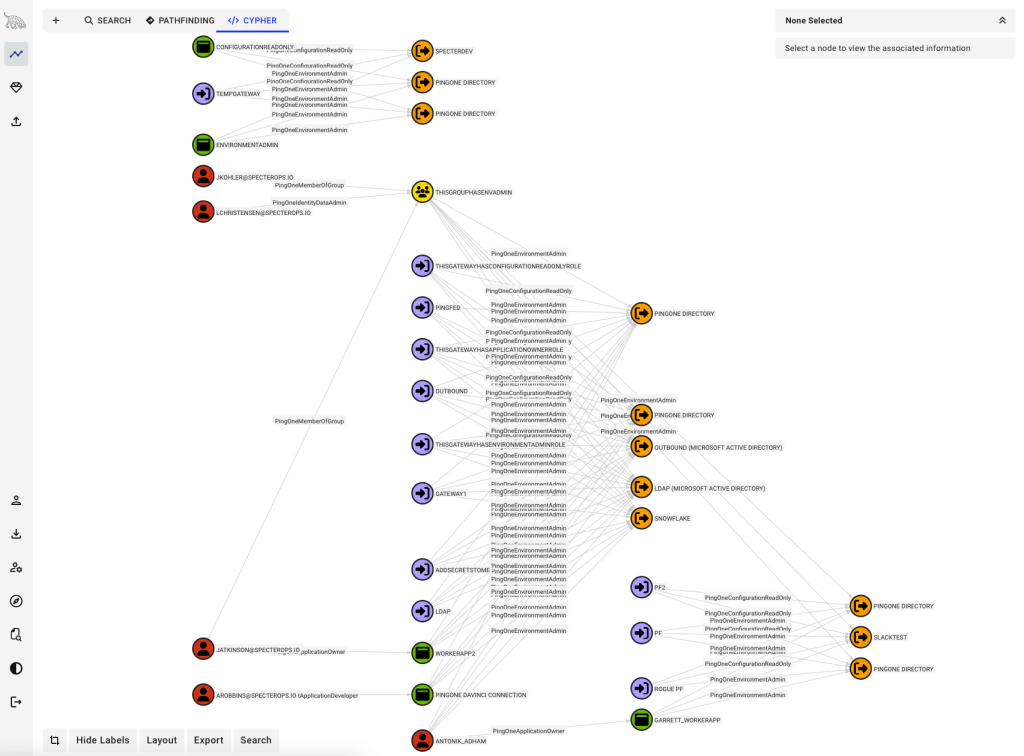
Research & Tradecraft
TL;DR: You can use PingOneHound in conjunction with BloodHound Community Edition to discover, analyze, execute, and...