blog category
Research & Tradecraft

Research & Tradecraft
Machine Learning Series Chapter 1
MICROGRAD FOR MORTALS TL;DR Let’s use Micrograd to explain core ML concepts like supervised learning, regression,...
By: Diego lomellini
Jul 2, 2025 • 42 min read
Read Post
Research & Tradecraft
Misconfiguration Manager: Still Overlooked, Still Overprivileged
TL;DR It has been one year since Misconfiguration Manager’s release and the security community has been...
By: Duane Michael, Garrett Foster
Jun 26, 2025 • 8 min read
Read Post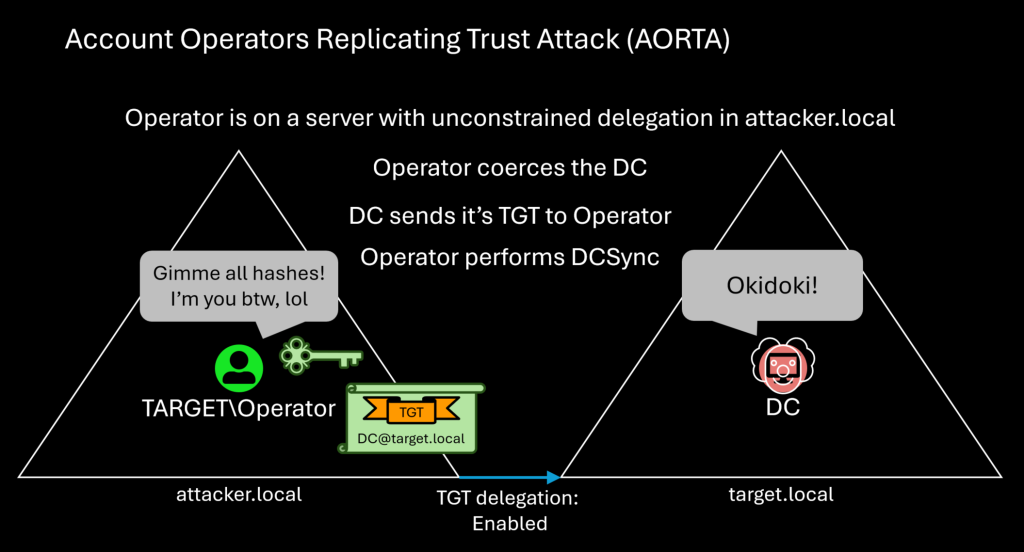
Research & Tradecraft
Untrustworthy Trust Builders: Account Operators Replicating Trust Attack (AORTA)
TL;DR The Incoming Forest Trust Builders group (not AdminSDHolder protected) can create inbound forest trusts with...
By: Jonas Bülow Knudsen
Jun 25, 2025 • 20 min read
Read Post
Research & Tradecraft
Lost in Translation: How L33tspeak Might Throw Sentiment Analysis Models for a Loop
TL;DR Sentiment analysis models are used to assess conventional use of language, but what happens when...
By: Max Andreacchi
Jun 24, 2025 • 9 min read
Read Post
Research & Tradecraft
While LLMs can expedite parts of the technical writing/editing process, these tools still require human oversight...
By: Sarah Miles
Jun 20, 2025 • 11 min read
Read Post
Research & Tradecraft
Ghostwriter v6: Introducing Collaborative Editing
TL;DR: Ghostwriter now supports real-time collaborative editing for observations, findings, and report fields using the YJS...
By: Christopher Maddalena, Alex Parrill
Jun 18, 2025 • 9 min read
Read Post
Research & Tradecraft
Administrator Protection Review
TL;DR Microsoft will be introducing Administrator Protection into Windows 11, so I wanted to have an...
By: Adam Chester
Jun 18, 2025 • 11 min read
Read Post
Research & Tradecraft
OneLogin, Many Issues: How I Pivoted from a Trial Tenant to Compromising Customer Signing Keys
TL;DR OneLogin was found to have security vulnerabilities in its AD Connector service that exposed authentication...
By: Julian Catrambone
Jun 10, 2025 • 11 min read
Read Post
Research & Tradecraft
Update: Dumping Entra Connect Sync Credentials
TL;DR Microsoft has recently changed how Entra Connect Sync authenticates to Entra ID. This blog post...