blog category
Research & Tradecraft
Research & Tradecraft
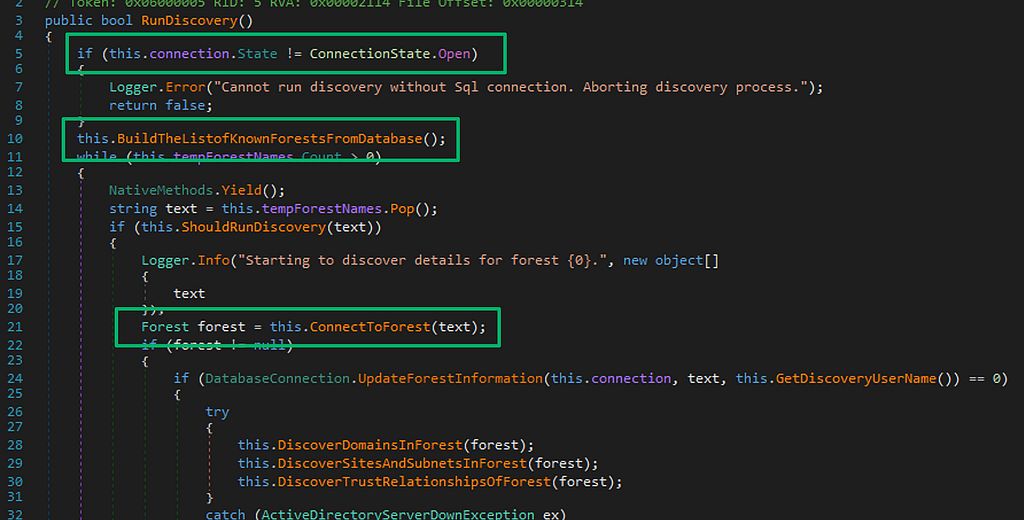
Decrypting the Forest From the Trees
TL;DR: SCCM forest discovery accounts can be decrypted including accounts used for managing untrusted forests. If...
By: Garrett Foster
Mar 6, 2025 • 10 min read
Read Post
Research & Tradecraft
Don’t Touch That Object! Finding SACL Tripwires During Red Team Ops
During red team operations, stealth is a critical component. We spend a great deal of time...
By: Alexander K. DeMine
Feb 20, 2025 • 17 min read
Read Post
Research & Tradecraft
Entering a Covenant: .NET Command and Control
By: Ryan Cobb
Feb 17, 2025 • 11 min read
Read Post
Research & Tradecraft
Forging a Better Operator Quality of Life
A new Mythic add-on for Windows Agents Mythic provides flexibility to agent developers for how they want...
By: Cody Thomas
Feb 5, 2025 • 7 min read
Read Post
Research & Tradecraft
Further Adventures With CMPivot — Client Coercion
Further Adventures With CMPivot — Client Coercion Perfectly Generated AI Depiction based on Title TL:DR CMPivot queries can be used...
By: Diego lomellini
Feb 3, 2025 • 8 min read
Read Post
Research & Tradecraft
SlackPirate Set Sails Again! Or: How to Send the Entire “Bee Movie” Script to Your Friends in Slack
TLDR: SlackPirate has been defunct for a few years due to a breaking change in how...
By: Daniel Mayer
Jan 31, 2025 • 7 min read
Read Post
Research & Tradecraft
Entra Connect Attacker Tradecraft: Part 2
Now that we know how to add credentials to an on-premises user, lets pose a question:...
By: Daniel Heinsen
Jan 22, 2025 • 11 min read
Read Post
Research & Tradecraft
Intune Attack Paths — Part 1 Prior Work Several people have recently produced high-quality work around Intune tradecraft. I...
By: Andy Robbins
Jan 15, 2025 • 21 min read
Read Post
Research & Tradecraft
On Detection: Tactical to Functional Why it is Difficult to Say What a Tool Does Introduction Over...