blog category
Research & Tradecraft
Research & Tradecraft
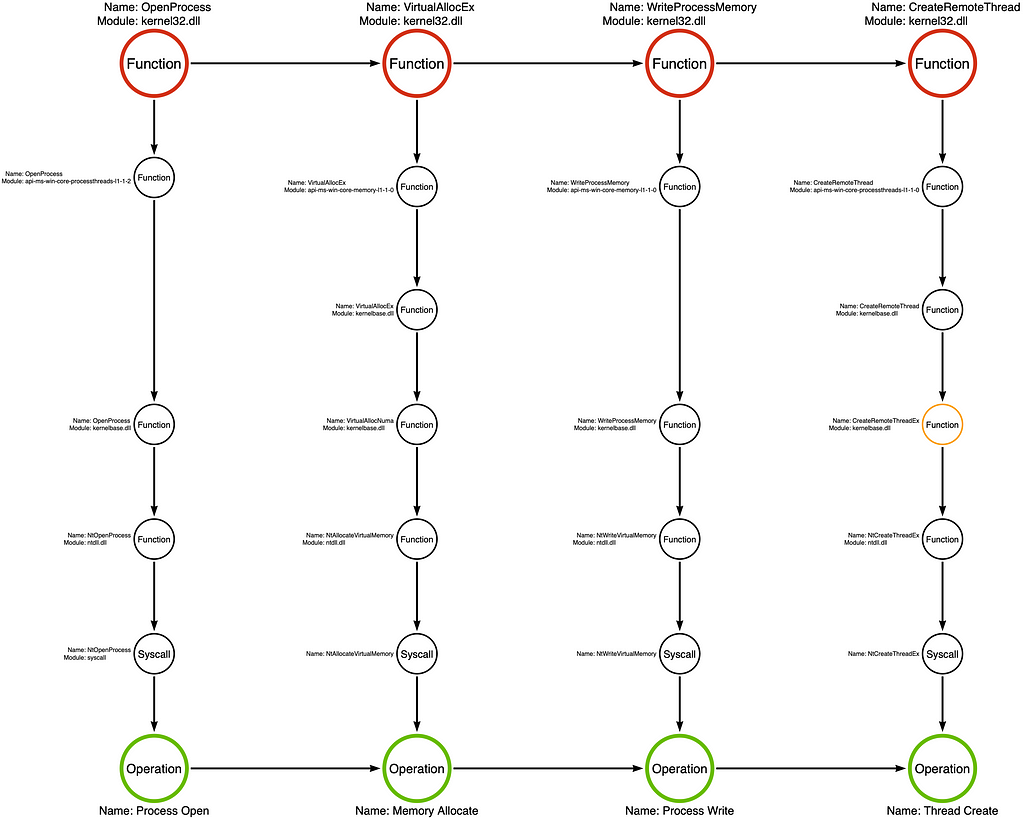
Part 15: Function Type Categories
On Detection: Tactical to Functional Seven Ways to View API Functions Introduction Welcome back to Part...
By: Jared Atkinson
Jan 7, 2025 • 24 min read
Read Post
Research & Tradecraft
ADFS — Living in the Legacy of DRS
ADFS — Living in the Legacy of DRS It’s no secret that Microsoft have been trying to move customers...
By: Adam Chester
Jan 7, 2025 • 32 min read
Read Post
Research & Tradecraft
TL;DR This blog walks you through setting up an ADFS lab using Ludus and/or a flexible...
By: Beyviel David
Dec 19, 2024 • 7 min read
Read Post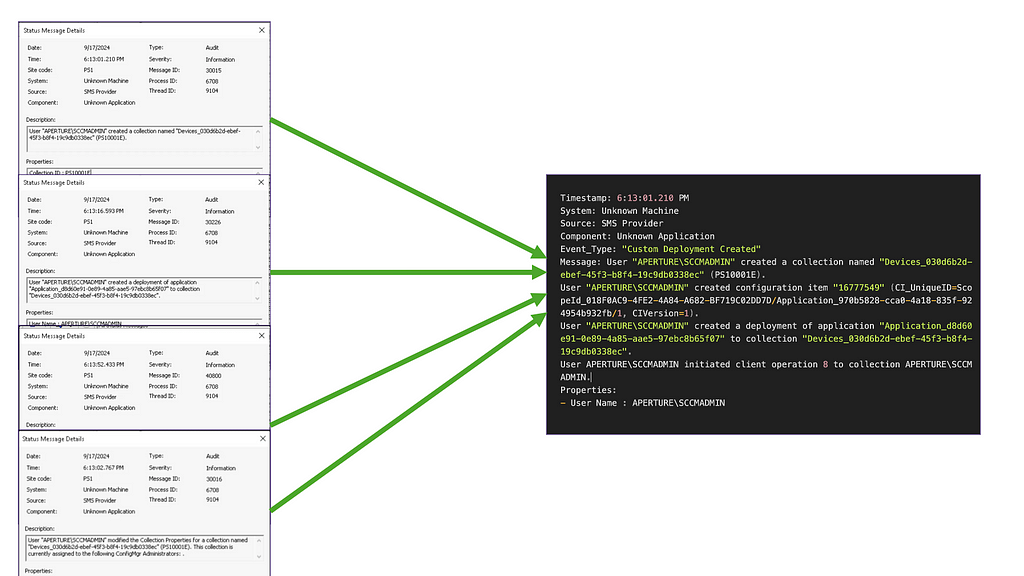
Research & Tradecraft
Misconfiguration Manager: Detection Updates
TL;DR: The Misconfiguration Manager DETECT section has been updated with relevant guidance to help defensive operators...
By: joshua prager
Dec 16, 2024 • 7 min read
Read Post
Research & Tradecraft
Attacking Entra Metaverse: Part 1
This is part one in a two (maybe three…) part series regarding attacker tradecraft around the...
By: Daniel Heinsen
Dec 13, 2024 • 8 min read
Read Post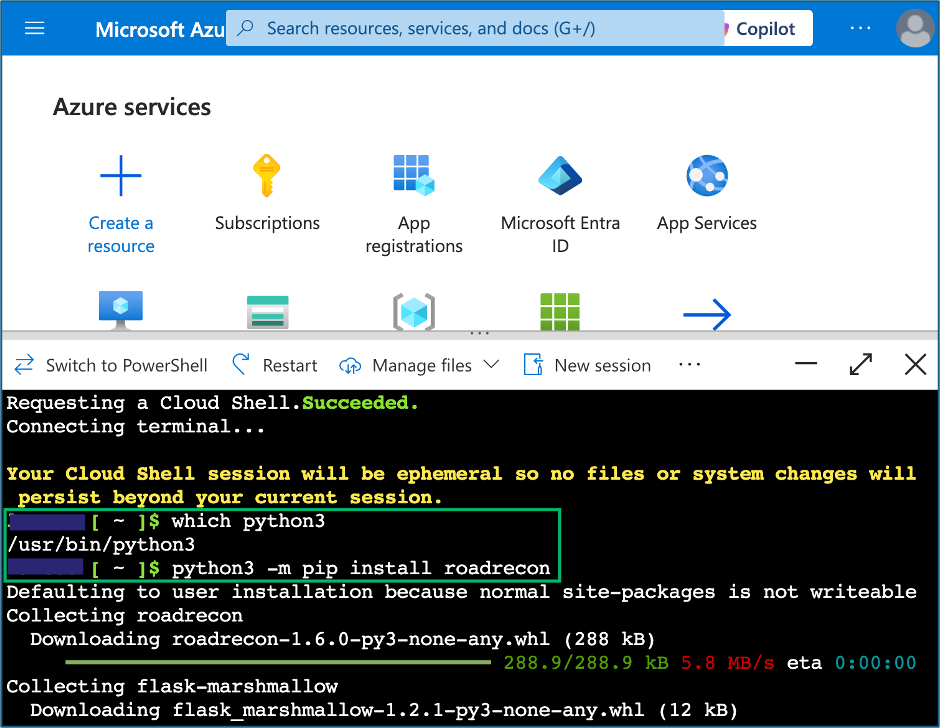
Research & Tradecraft
SPA is for Single-Page Abuse! – Using Single-Page Application Tokens to Enumerate Azure
Author: Lance B. Cain Overview Microsoft Azure is a leading cloud provider offering technology solutions to companies,...
By: Lance B. Cain
Dec 10, 2024 • 9 min read
Read Post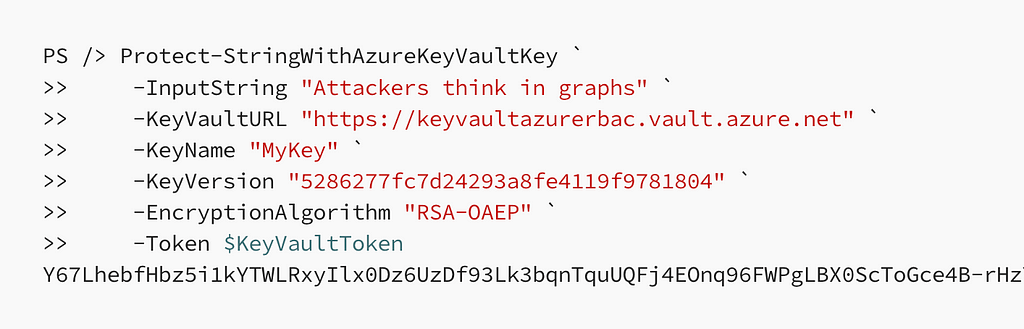
Research & Tradecraft
Azure Key Vault Tradecraft with BARK
Brief This post details the existing and new functions in BARK that support adversarial tradecraft research...
By: Andy Robbins
Nov 20, 2024 • 8 min read
Read Post
Research & Tradecraft
Maestro: Abusing Intune for Lateral Movement Over C2
If I have a command and control (C2) agent on an Intune admin’s workstation, I should...
By: Chris Thompson
Oct 31, 2024 • 13 min read
Read Post
Research & Tradecraft
Maestro: Abusing Intune for Lateral Movement Over C2