Know your adversary
Attackers don’t go through your tools – they go around them, leveraging gaps in your program and exploiting identities to reach your critical assets. Our mission is to demystify tradecraft and stop adversaries in their tracks.

BLOODHOUND
Introducing BloodHound 8.0 and OpenGraph
Explore a breakthrough in attack path management >
RESEARCH
State of Attack Path Management Report
See our latest on the bleeding edge of attack paths >Identity attack path management
A new approach is needed
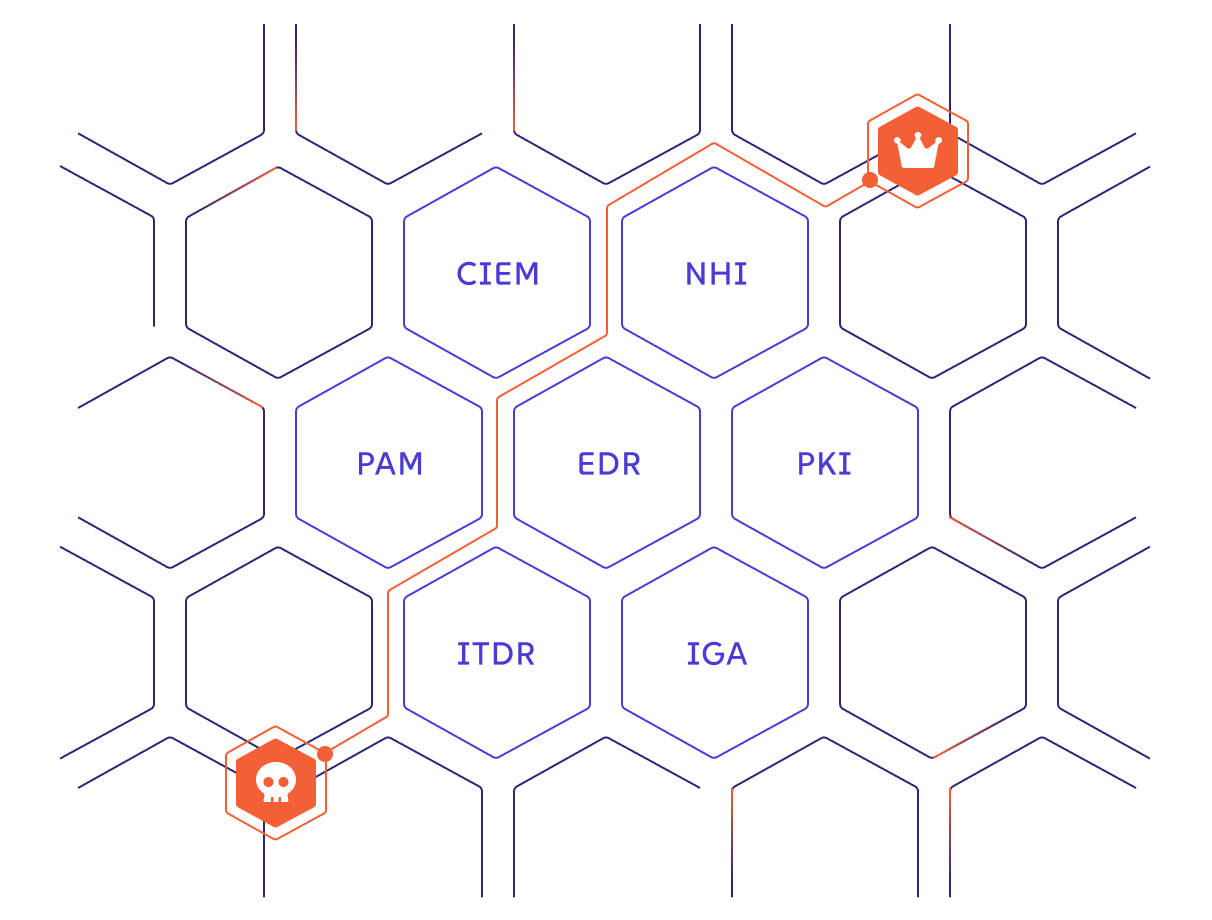
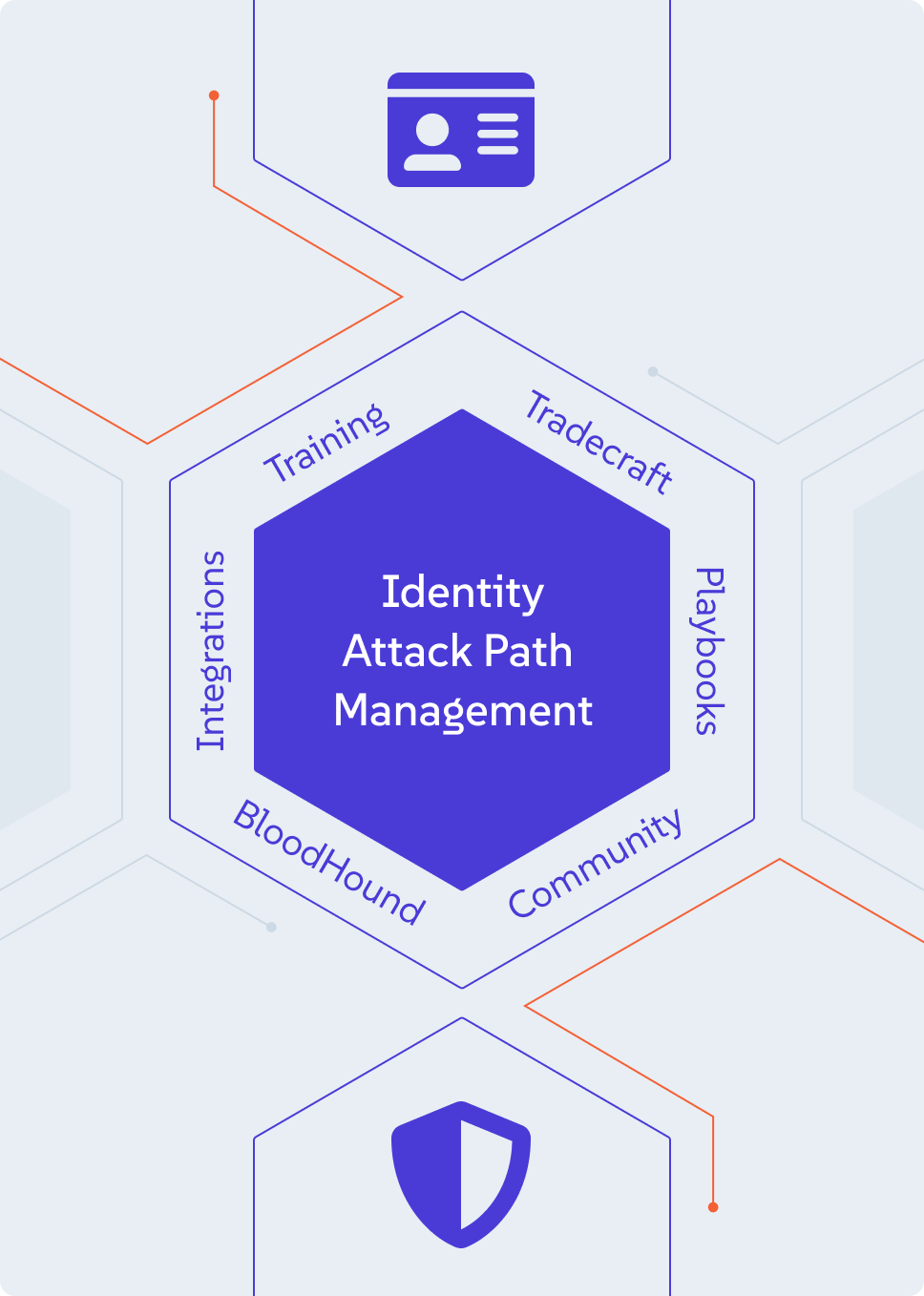
Identity Attack Path Management is a structured approach to identify and disrupt how attackers exploit identity to gain control of systems and data.
Security and Identity teams can now join forces through the power of industry-leading tradecraft, training, and technology.
WHY SPECTEROPS
Built by Attackers. Trusted by Defenders.
SpecterOps is built from the adversary’s point of view — not because we admire them, but because we’ve been them. Our platform is shaped by practitioners, not philosophy. Our training teaches tradecraft, not theory. And our services are grounded in front-line knowledge, not check-the-box compliance.


Training & Tradecraft
World-class instruction in adversary tactics and tradecraft.
Learn from experts
Community Driven
Our commitment to knowledge sharing, research, and open-source projects.
Explore our arsenal of tools
BloodHound
Identity Attack Path Management from open-source roots to an enterprise-grade security platform.
Reduce operational and business risk
Continuously map and eliminate attack paths
BloodHound Enterprise continuously maps identity relationships and permissions across your environment to reveal the hidden attack paths that lead to your crown jewels.
-
Continuously graph identity relationships and privilege escalation paths
-
Prioritize with choke points to remove millions of paths with a single fix
-
Remediate graph-based findings with step-by-step, impact-aware guidance
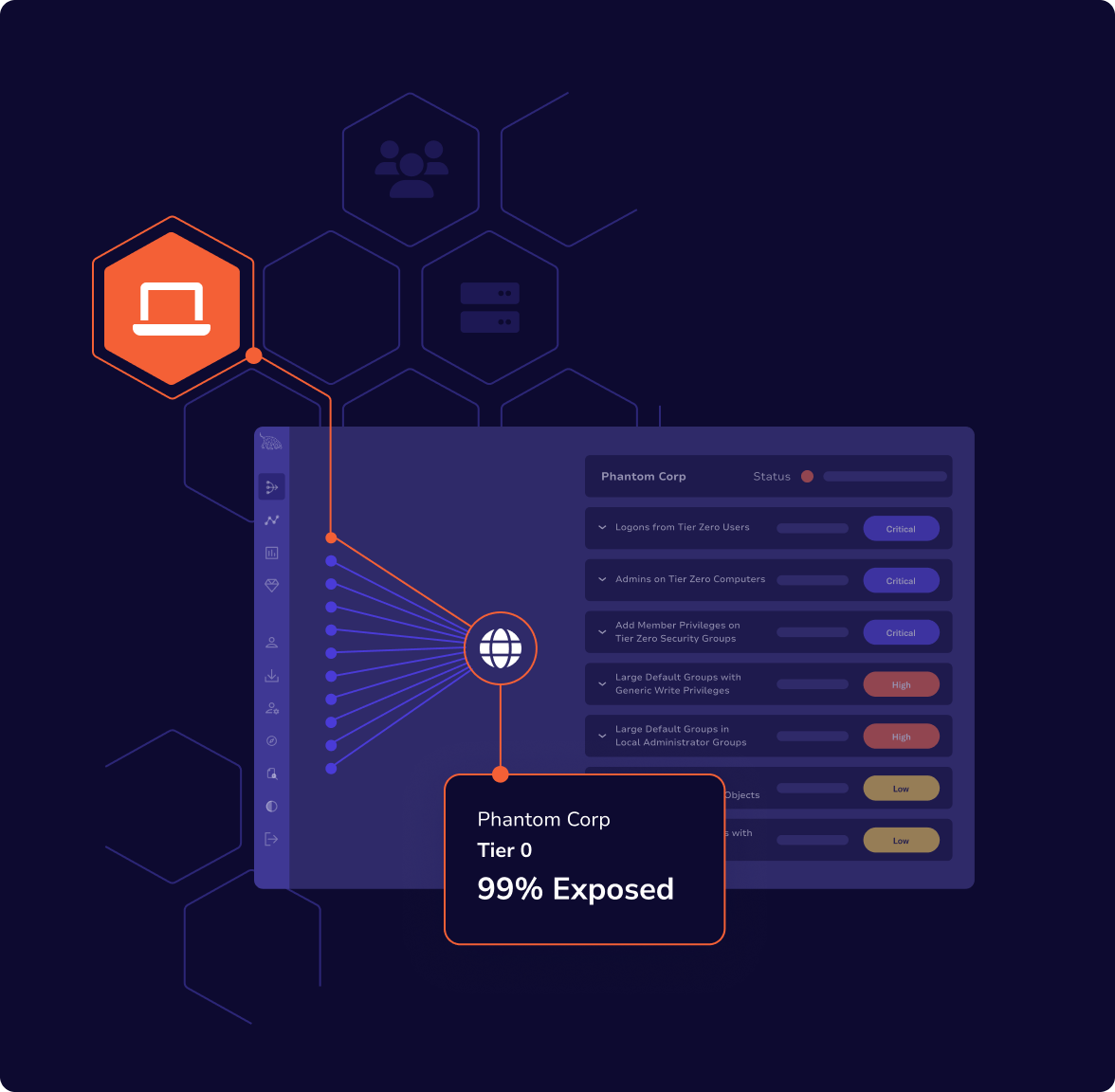
Enterprise-wide visibility and identity risk posture
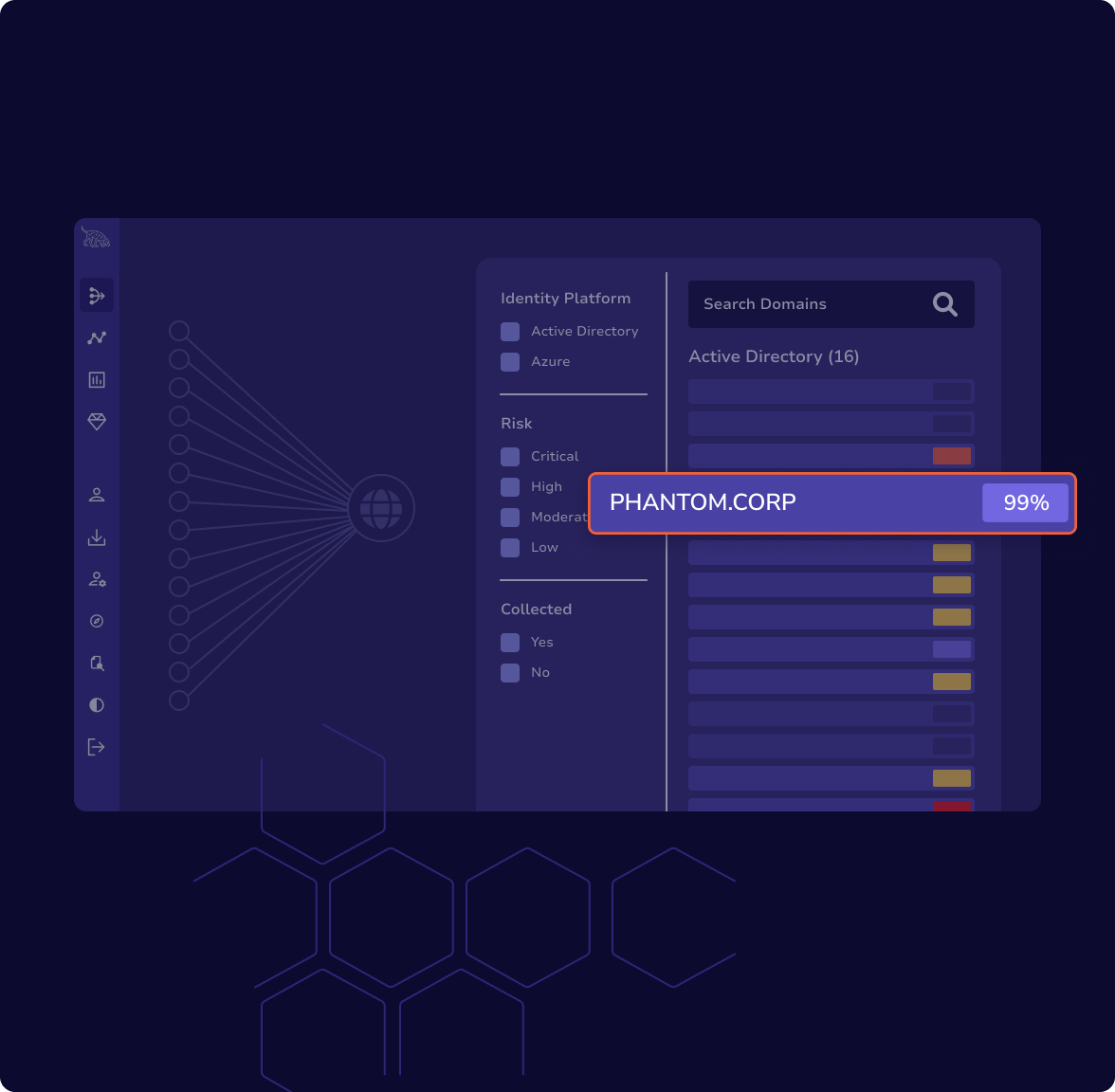
BloodHound Enterprise gives you a complete picture of how identities — human or non-human — can be exploited in your environment, helping you measure, prioritize, and reduce identity-based risk over time.
-
Monitor identity risk trends over time across business units or the enterprise at scale
-
Respond to new high-risk on-premise, cloud, or hybrid identity attack path
-
Report on remediation efficacy with confidence
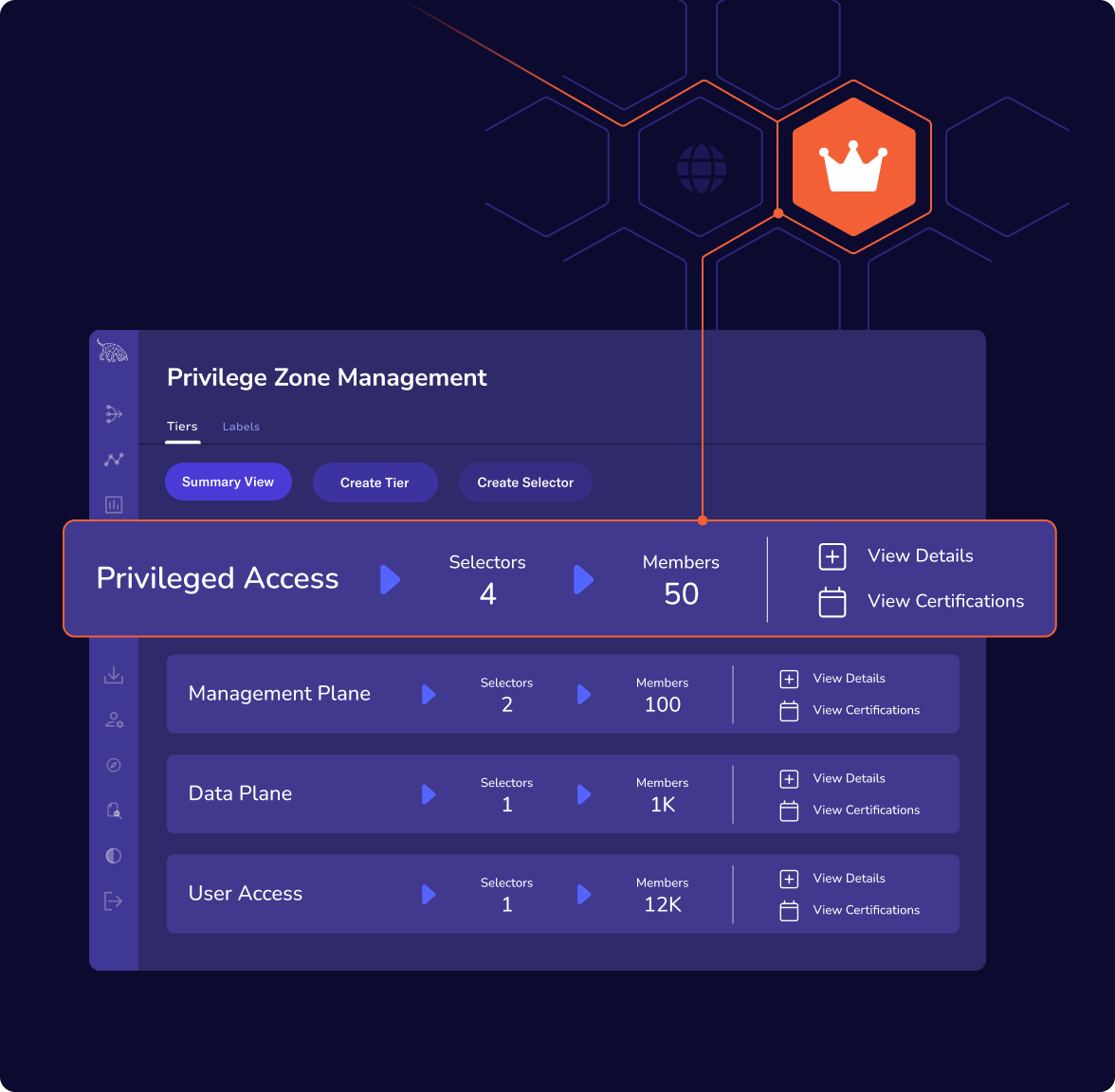
Enforce boundaries that attackers can’t cross
Prevent lateral movement and privilege escalation by defining and enforcing custom access zones—whether in on-premises, cloud, or hybrid environments.
-
Define Zones based on tiers, sensitivity, or business function
-
Prevent escalation or lateral movement between zones
-
Finally implement least privilege with a practical technical control
Customer success stories
Helping those leading the fight
Empowering the security community
We’re in this together.
We believe that security is strengthened when knowledge flows freely. We’re committed to advancing the industry through meaningful open source contributions, cutting-edge research, and authentic knowledge sharing.
As pioneers who’ve walked both sides of the security equation, we share tools and expertise that reveal what attackers actually see and do. From BloodHound and Mythic to our latest community projects, we’re equipping security teams worldwide with the tradecraft intelligence that truly matters.
Ready to get started?
See how BloodHound Enterprise eliminates millions of attack paths while focusing your defenses on the routes attackers actually use to reach your critical assets.
Book a Demo