3 Foundational Pillars for Attack Path Management: Pillar 1 — Continuous & Comprehensive Mapping
Dec 9 2021
By: Justin Kohler • 5 min read
3 Foundational Pillars for Attack Path Management: Pillar 1 — Continuous & Comprehensive Mapping
When we coined the term “Attack Path Management” (APM) in our post ‘The Attack Path Manifesto’ in May of 2021, we set out to bring awareness to the most prevalent tactic used by adversaries to accomplish their mission. But we also shared a new approach which can prevent & remove this tactic.
The tactic, abusing identity-based Attack Paths in directory services such as Active Directory, allows knowledgeable attackers toappear as legitimate users in your organization. These attackers take advantage of chains of abusable privileges and user behaviors which create direct and indirect connections between computers and users (let’s call these ‘misconfigurations’) to reach critical assets.
NOTE: When we refer to Active Directory, please note the same applies for Azure.
The new approach, Attack Path Management (APM), departs from the legacy concept of reporting insurmountable lists of AD misconfigurations. Instead, Attack Path Management prevents adversaries from abusing AD through what we describe as the three APM Pillars:
- Continuous and Comprehensive Attack Path Mapping
- Empirical Impact Assessment of Attack Path Choke Points
- Practical, Precise, and Safe Remediation Guidance
Through mapping, assessing strategic choke points, and providing real-world remediation guidance, organizations can remove the risks of thousands of misconfigurations by mitigating a single misconfiguration (choke point).
In this three-part series, we will dissect each of the three APM Pillars and share how they enable enterprises to prevent adversaries from accomplishing their mission.
BloodHound Enterprise: Continuous, Comprehensive Attack Path Mapping
Historically, technologies scan for and list AD misconfigurations and stop there. Continuous, comprehensive Attack Path mapping goes the next step to enumerate the links and relationships between every user, computer, and object in AD that create ‘pathways’ for attackers to abuse. Not only does this provide visibility to those Attack Paths, but it enables AD administrators (for the first time) to have full understanding of the real permissions against any given object, computer, user, etc.
More specifically, continuous and comprehensive mapping pinpoints your organization’s ‘exposure’ as viewed by adversaries abusing AD. In other words, once an adversary has access to any user or computer, what paths are available to them and how far can they go? Having real-time knowledge of your current objects, computers, users, etc. that are exposed to adversaries is the first step in Attack Path prevention.
The next logical question is how those mappings are created. This starts with a service that is installed on one Windows server (physical or virtual) that has connectivity to query your domain controller. It supports both privileged and unprivileged collection of your domain objects for analysis. As domain objects are collected, BloodHound Enterprise automatically identifies critical assets (e.g., Tier Zero / Control Plane objects such as Admin accounts and groups, domain controllers, applied Group Policy Objects (GPOs), etc.). BloodHound Enterprise then uses this set of critical assets to chart the pathways made possible by every relationship and every misconfiguration in AD. The result is an exposure map of every user or computer that can provide an adversary access to your critical assets.
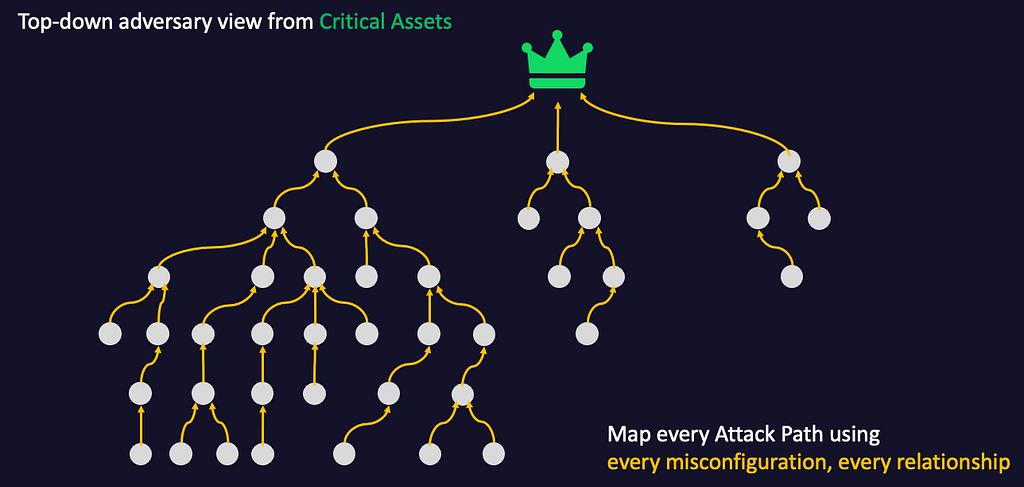
This map is helpful, but AD is constantly evolving. New users, groups, computers, applications, and data are added continuously, which necessitates continuous visibility over these objects and the resulting Attack Paths. This continuous visibility provides the ability to verify the effectiveness of remediation activities by demonstrating the decreasing severity or the complete removal of Attack Paths. Furthermore, continuous visibility into Attack Paths allows our customers to quickly identify and reverse AD configurations that have unintended consequences. We’ve seen seemingly benign configurations in AD spawn massive opportunities for Attack Paths. With a constant, up-to-date picture of this map, teams can cut off newly formed Attack Paths early rather than identifying them 3, 6, or even 12 months later after business processes have been built on top of that new relationship.
While we will cover this more in-depth in Part 2 of the blog series, you gain two critical pieces of knowledge by using this approach. The first is for each high value target you immediately identify the nearest misconfiguration(s) that, if you eliminate, the risk of the lower-level misconfigurations are moot. We call those misconfigurations closest to the critical target the “choke points”.
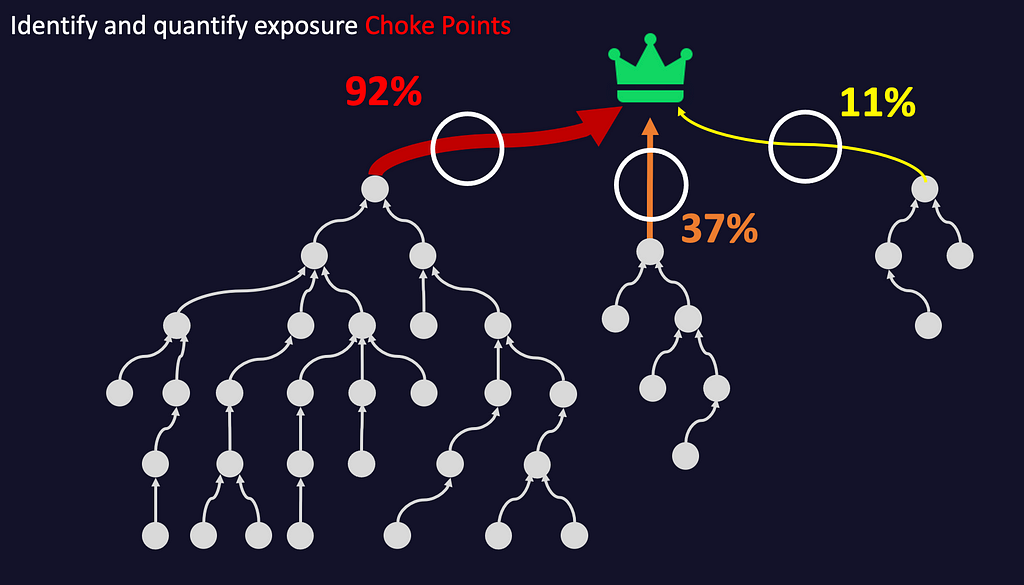
The second piece of gained knowledge is the empirical number of users & computers with a path to critical assets through each choke point. More users & computers = more exposure. This acts to prioritize which choke points you remediate first.
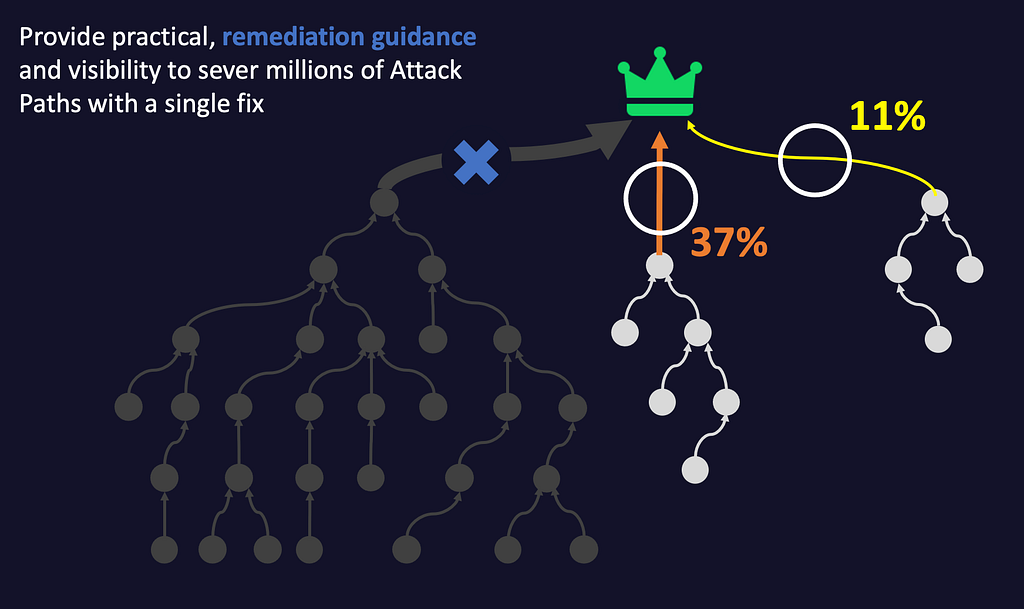
As a recap, BloodHound Enterprise delivers Attack Path Management by going beyond scanning and listing misconfigurations. Instead, BloodHound Enteprise maps the links and relationships that produce pathways adversaries can use to take control of your corporate network and systems. These maps automatically pinpoint the most important, nearest misconfigurations to your critical assets and empirically inform you of the exposure of each of these choke points. You can then systematically address each choke point (from highest to lowest exposure), eliminating the risk of the thousands of downstream misconfigurations and taking away the adversary’s favorite tactic to control your organization.
3 Foundational Pillars for Attack Path Management: Pillar 1 — Continuous & Comprehensive Mapping was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.


