BloodHound Community Edition v8 Launches with OpenGraph: Identity Attack Paths Beyond Active Directory & Entra ID
TL;DR SpecterOps announces the rollout of BloodHound Community Edition 8.0, which includes usability and expandability enhancements for community members. The rollout also includes BloodHound OpenGraph, which lets you trace beyond AD and Entra ID to visualize how identities, devices, and permissions connect across cloud platforms, SaaS tools, and endpoints via attack paths.
BloodHound has long been the go-to tool for red teamers mapping privilege escalation and for blue teamers trying to stop it. Whether you’re tearing through an AD forest or untangling Entra ID sprawl, it’s probably helped you find something ugly.
This post is all about what’s new in BloodHound Community Edition (CE) 8.0. Our commercial edition designed for defenders has picked up some powerful upgrades, too (because stopping the paths is just as important as finding them).
Introducing OpenGraph: A New Framework for Building Identity Attack Path Maps
OpenGraph is the biggest leap forward for BloodHound CE since SharpHound hunted down the scent of its first token. With OpenGraph, you can now pull in identity data from other sources (starting with GitHub, Snowflake, 1Password, and Microsoft SQL Server) and weave it directly into your graph. For the first time, you can ingest and visualize identity attack paths and relationships from any platform, repository, or application.
That means you’re no longer stuck in the AD/Entra ID universe. Now you can trace how identities, devices, and permissions connect across cloud platforms, software-as-a-service (SaaS) tools, and endpoints; and map attack paths that reach far beyond the domain controller (DC).

(Hybrid MS-SQL – SCCM Attack Path Image)
Want to see how a GitHub maintainer account links back to your corporate Entra ID, or how a misconfigured MS SQL database becomes a treasure trove of confidential data? With OpenGraph, you can define custom relationships, grow your graph, and chase down risk wherever it hides.
Here’s what that looks like in the wild:
- GitHub: An Entra ID account maps to a GitHub user with push access to production. That’s a clean path from Azure to CI/CD to prod; no bones about it.
Attack Paths from AD through Github using BloodHound OpenGraph
- Snowflake: A corporate identity has access to sensitive Snowflake datasets. OpenGraph lets you trace the privilege chain and simulate exfiltration or abuse with surgical precision.
- Jamf: A user’s tied to a Jamf-managed macOS device with elevated rights. Congratulations – you just sniffed out a new lateral path through a trusted endpoint.
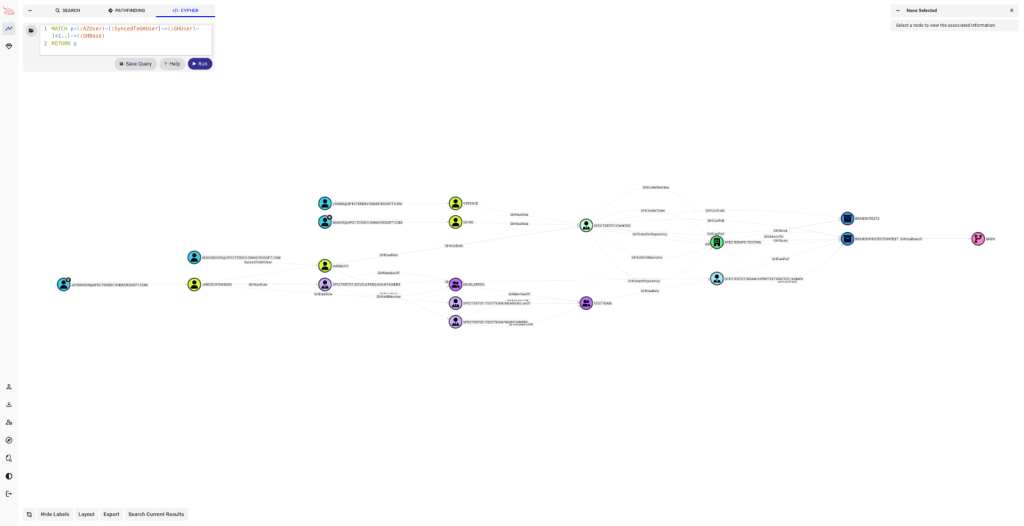
- Microsoft SQL Server: In an SCCM default setup, the SMS Provider has database access that escalates to full sa privileges via SQL role inheritance and TRUSTWORTHY settings. This allows OS command execution through xp_cmdshell. Since MSSQL runs as a domain account and tools like Mimikatz can extract its credentials from memory.
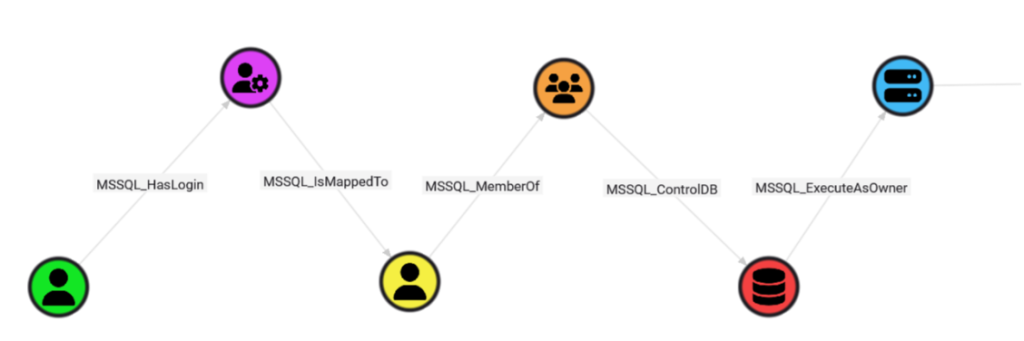
Attack Paths from AD through Microsoft SQL using BloodHound OpenGraph
BloodHound OpenGraph isn’t a one-and-done drop; rather, it’s the start of something bigger. Expect continuous expansion as the SpecterOps team, the BloodHound community, and strategic partners feed in new connectors, techniques, and research.
Here’s what’s available right out of the gate:
- Custom Identity Ingestion: Bring in the weird stuff! OpenGraph lets you model identities and relationships unique to your environment.
- Advanced Querying: Slice, dice, and path-find across hybrid identity graphs with powerful Cypher-based queries.
- Visual Attack Path Mapping: See how it all connects. From initial foothold to crown jewels, the graph draws the map.
The goal? Keep pushing deeper. More data. More visibility. More ways to make identity risk painfully obvious.
OpenGraph is baked into BloodHound CE 8.0. We won’t backport it to BloodHound Legacy, so if you’re still running the old version, it’s time to upgrade.
Now That You Have OpenGraph, Show Us What You Can Do with It
BloodHound has always been more than a tool; it’s been a platform shaped by the community that uses it to break things better. From the earliest privilege escalation chains to cutting-edge cross-domain attack paths, some of the best BloodHound content hasn’t come from us. It’s come from you.
Now that OpenGraph is live in BloodHound 8.0, we’re throwing down a challenge: Use it. Abuse it. Break new ground with it.
We’re inviting the community to submit writeups, talk proposals, and real-world research that shows what’s possible with OpenGraph. Whether you’re owning data lakes or MacBooks, getting to a production database via GitHub, or just building something weird that works, we want to see it!
Top submissions will get:
- All authors of blog posts on research involving OpenGraph will receive a BloodHound Challenge coin and swag in the mail.
- For research talks on OpenGraph accepted by a security conference with more than 200 attendees, we’ll have a special bonus. You can choose between any SpecterOps training class or a free trip to attend SO-CON 2026 (ticket, flight, and hotel included). A maximum of 10 people are eligible to receive this incentive bonus, at SpecterOps’ discretion (that’s the parents speaking).
- Submit your research using this form.
Let’s see what kind of trouble you can get into!
Also New in BloodHound CE 8.0: Usability & Performance
BloodHound CE 8.0 isn’t just about OpenGraph. This release brings a ton of long-requested improvements, many based directly on community feedback.
- Table View and Inheritance Tracking: Visual graphs are great, but sometimes you just want raw data. Table View gives you a sortable list of nodes and their properties—perfect for digging into ACEs and inherited permissions. Inheritance tracking now shows where rights originate, so you can trace privilege flows from root to edge. See visuals for both enhancements here.
- Query Library: Want a way to explore the new table view with a brand new suite of queries? The new BloodHound Query Library provides over 170 curated queries all stored in YAML, searchable in a dedicated UI, and mapped to real-world use cases.
- Azure PIM Roles: We added coverage to support PIM roles within Entra ID. Find attack paths through identities that can enable Global Administrator or other privileged roles.
- Back button: Yes, a real back button. Small feature, big impact. A frequent community request. It also means that you can now bookmark views and securely share them among teams.
- New trust edges: In case you missed it, BloodHound replaced the legacy TrustedBy edge with a new, more accurate trust model, which includes four new trust edges, each designed to reflect whether a trust is present, how it’s configured, and whether it’s abusable. Additional details on this model and other enhancements to BloodHound Community Edition and BloodHound Enterprise can be found here.
Still on BloodHound Legacy? Here’s What You’re Missing
We know that a few of you haven’t made the jump from BloodHound Legacy yet. We acknowledge that we didn’t have feature parity from the start when we merged the code base for BloodHound CE and BloodHound Enterprise a few years ago with the goal to modernize the architecture. We have now caught up on feature parity (yay!) and added quite a few cherries on top.
Here are some of the features we added since BloodHound Legacy that you may appreciate:
- Performance & Scalability: BloodHound Legacy couldn’t keep up with big environments. BloodHound CE fixes that with a fully overhauled backend and containerized deployment. Ingest faster, query smoother, and scale cleanly. You’ll save tons of time (though less time to fetch a coffee).
- REST API Access: Script it. Automate it. Integrate it. BHCE includes a RESTful API and SDK for popular programming languages so you can tie BloodHound into your workflows and tooling.
- Native Kali Linux support: As of version 7, the good folks over at OffSec have packaged BloodHound CE up for Kali Linux, so you’re just one sudo apt update && sudo apt install -y bloodhound away from your bright, shiny future.
- Modern UX: A built-in Cypher viewer, Dark Mode, and a cleaner overall interface. It’s all the small quality-of-life improvements you’ve been asking for.
- Multi-User Support: CE includes enterprise-grade user management (RBAC, 2FA, SAML, and OIDC support) without giving up the open-source license.
- Cypher Compatibility: Still writing custom queries? Good. BHCE maintains Cypher support with improved stability for query libraries. Check out our technical article on Cypher support here.
Migrating from BloodHound Legacy
BloodHound Legacy is officially deprecated. If you’re still on it, now’s the time to upgrade. BloodHound CE 8.0 is faster, more capable, and actively maintained.
New to CE? Start here:
Need help migrating data? Keep reading. We’ve got you covered:
- Convert Cypher libraries: BHCE uses a new format for Cypher libraries. Luckily, community member WafflesExploits & SEERcurity Spotlight wrote some tools to convert your favorite Cypher libraries into the new BHCE format. That inspired our own team member, Scoubi, to expand upon it in his repo. You can check out the tool here.
- Discover your environment: While BHCE still collects your environments’ data using SharpHound (Active Directory) and AzureHound (Entra ID), the output format has changed. Please discover your environment again with the latest version to use the data in BHCE.
Help Blue Teams Stay on Top of Attack Paths
We’ve heard the same story from pentesters again and again: you break in, map the paths, write the report…and a year later, the same issues are still there. BloodHound CE 8.0 helps you expose identity attack paths with more clarity than ever, but exposing the problem isn’t always enough.
If your customers are interested in discovering attack paths in real-time and getting a step-by-step methodology to address the findings, consider pointing them to BloodHound Enterprise in your final report. It gives defenders the same graph-based visibility you have, so they can actually close off the attack paths you have used to own them and stay on top of them going forward.


