BloodHound v8: Usability, Extensibility, and OpenGraph
Jul 29 2025
By: Justin Kohler • 18 min read
TL;DR BloodHound v8 introduces exciting new features enabling users to get more and do more with the BloodHound Attack Path Management platform. These include enhanced abilities to work with BloodHound Enterprise data, increased integration work, and expansions to BloodHound coverage. BloodHound v8 also introduces BloodHound OpenGraph’s game changing ability to ingest data outside of the traditional AD/Entra ID views into the graph.
This release represents the biggest functional update since BloodHound launched. It expands how users interact with data, how teams integrate BloodHound into their workflows, and how the platform models identity risk across hybrid environments beyond the traditional Microsoft ecosystem.
We’re organizing the new features into three themes:
- Usability: Faster, clearer access to relevant information with Table View, Inheritance tracking, and a new cypher query library.
- Extensibility: Extends attack path coverage in Azure and Active Directory, expands Identity Attack Path Management beyond Tier Zero with Privilege Zones, and introduces new integrations to extend attack path data into your broader security and IT ecosystem.
- BloodHound OpenGraph: Unleash BloodHound to ingest and map attack paths in new platforms
This is a massive release for BloodHound and there’s a lot to cover. Let’s dive in.
Usability: Faster, Clearer Access to Information
This release includes multiple changes that improve how users interact with BloodHound data. These features reduce investigation friction, improve clarity, and make it easier to share insights across teams.
Introducing Table View
Attackers and Defenders can still think in graphs… but sometimes a list is pretty helpful.
A key part of BloodHound’s value has always been its ability to visualize the attack path. A picture really can speak louder than words, particularly if you’re trying to understand how any on-prem user can be used to take control of an Azure tenant:
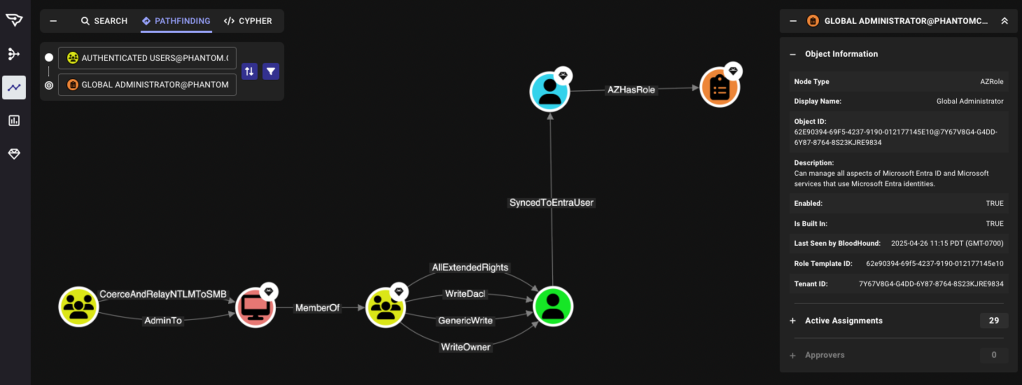
But what if the data you’re returning doesn’t have a relationship or a path? For example, let’s take a query that might be used by a defender or someone in the identity team to find users with passwords older than one year:
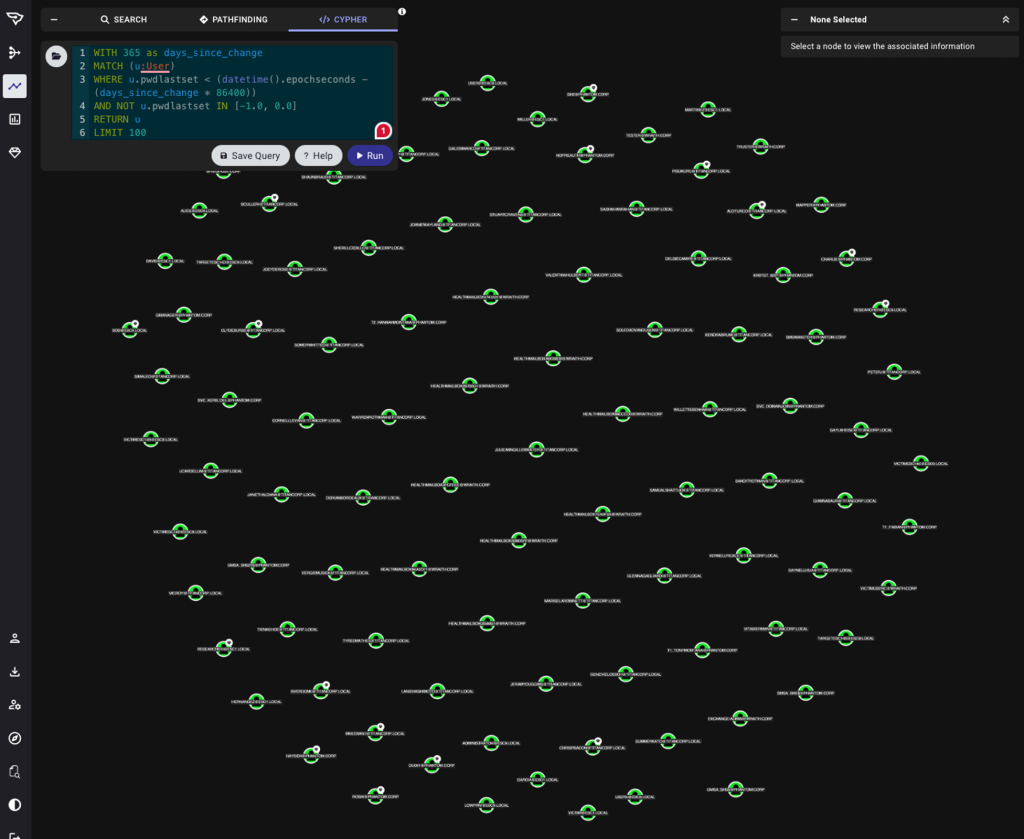
Yes, you get accurate results, but they aren’t clear or actionable. What if you wanted to sort by the oldest password or highlight those that are administrators?
This is where Table View comes in. Users can now select Table as a layout to return that same query, select relevant data to present, sort as desired, and download to csv:
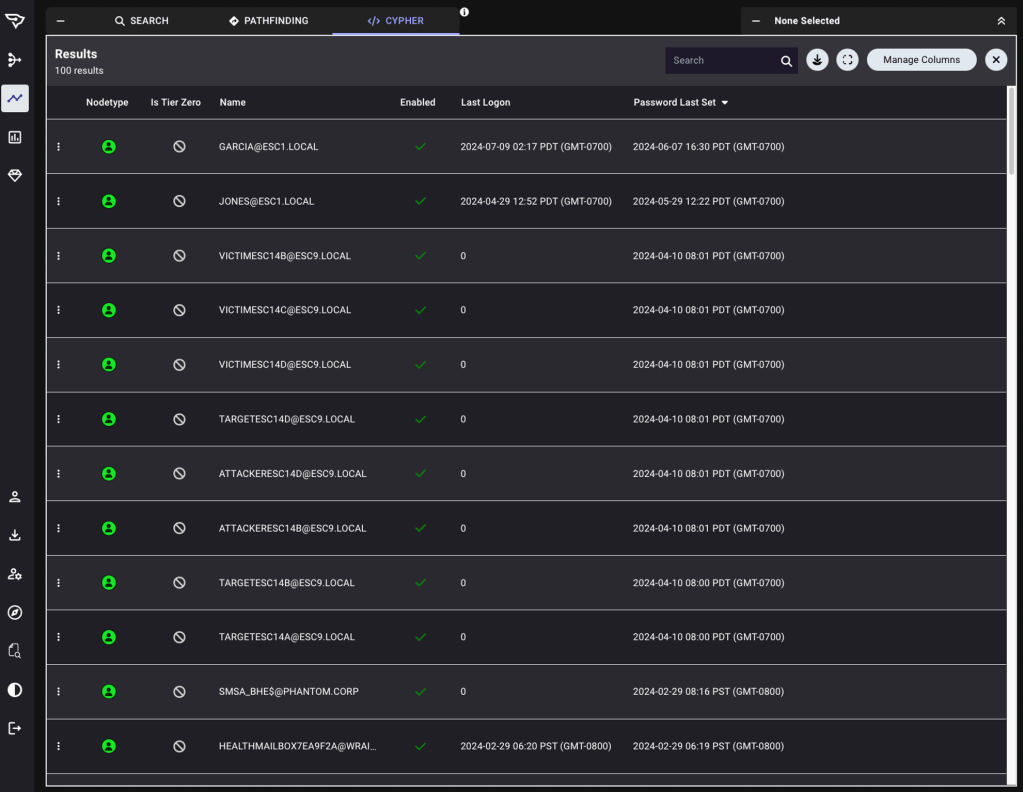
Now you can use Table View to more efficiently interrogate the BloodHound dataset for other use cases:
- Use a naming scheme to denote users that are allowed to have admin rights or privilege roles? Use Table View to find violations of these policies where regular users are eligible or have been assigned privileged roles.
- Trying to wrap your arms around Non-Human identities? Use Table View to find service accounts or non-human identities without owners populated in the object record, credentials that haven’t been rotated on time, etc.
Once you organize your data, quickly download it to .csv to send to a separate team or simply copy the URL and send to another user with access to BloodHound to directly view and interact with the results.
BloodHound Query Library
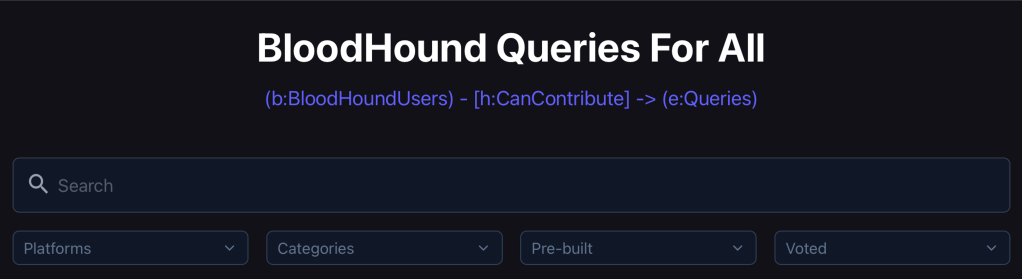
Want a way to explore the new table view with a brand new suite of queries? The new BloodHound Query Library provides over 170 curated queries across both BloodHound Enterprise and BloodHound Community Edition. Each query is stored in YAML, searchable in a dedicated UI, and mapped to real-world use cases.
Rather than replacing BloodHound’s built-in functionality, the library serves as an extension and an educational bridge – helping users understand query patterns, learn from real-world examples, and eventually develop the confidence to write their own custom queries.
The BloodHound Query Library isn’t just another collection of queries. Several features set it apart:
- Open Query Ecosystem: Unlike the traditional model where queries were added to BloodHound as product features (or infrequent community pull requests), the library creates a centralized open ecosystem for query sharing and community voting to surface the most valuable content
- Standardized Query Format: Each query is a YAML file and includes not just the query, but metadata like platform compatibility, description, and resource links. YAML ensures readability and makes contributions easy while maintaining consistency
- Web Interface: Unlike static cheat sheets or the raw YAML files, the library provides a user-friendly, searchable interface with direct run and copy functionality to improve usability and locate the queries you need in a matter of seconds
- Coverage across common assessment tools: To showcase BloodHound’s broader security assessment capabilities, we’ve mapped BloodHound queries to common security tools such as Microsoft Defender for Identity, Netwrix PingCastle, and Tenable Nessus. This enables different teams to leverage BloodHound’s comprehensive attack path data, whether they’re conducting red team assessments, blue team analysis, or compliance audits.
Read the deep-dive blog on the Query Library for more information. And, if you’ve developed useful queries that aren’t yet in the library, consider contributing them to the community via the Library. See the Contributing section in the GitHub repository for more.
Track Access Control Entry (ACE) Inheritance in Active Directory
Active Directory allows administrators to delegate privileges via inheritance. Rather than directly assign the HelpDesk the ability to reset user passwords, this privilege can be assigned at an OU that contains all users.
To date, we’ve always modeled these privileges and attack paths directly, as an attacker would. In this example, we can use the SVC_PAYADMIN account to add a member to Domain Admins.
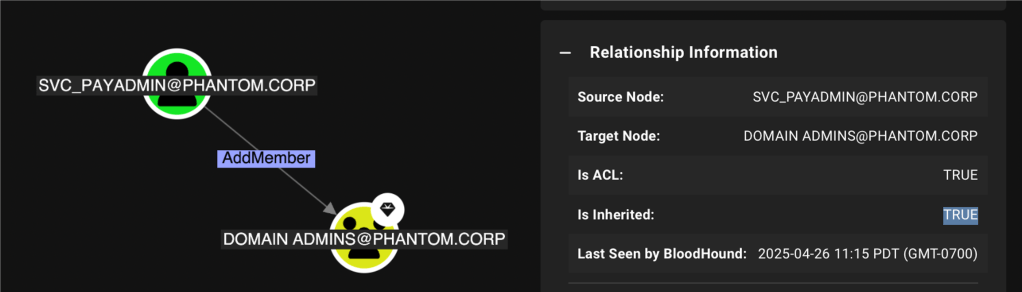
Example of how Inherited privileges looked before
In prior versions, we can see that the privilege is inherited, but not from where it’s inherited. This is very important for the defender to properly target remediation.
Now, BloodHound can highlight exactly where this privilege is inherited, enabling defenders to address the risk at the source without chasing the inheritance manually in Active Directory.
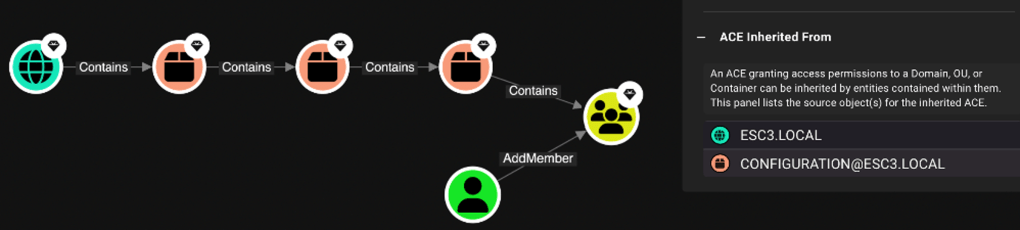
Detailed ACE inheritance tracking in BloodHound V8
Extensibility: Extend the coverage, impact, and workflows of Attack Path Management
Privilege Zone Analysis (BloodHound Enterprise Only).
Version 8 brings enhancements to Privilege Zone Analysis in Early Access for BloodHound Enterprise customers. Most organizations assume they’ve implemented least privilege, but assumptions don’t stop attackers. Privilege Zones in BloodHound Enterprise lets you define and analyze real-world security boundaries to stop lateral movement and eliminate attack paths across hybrid environments.
Organizations also try to implement some sort of separation of duties or least privilege. But as BloodHound quickly points out (as any attack path is a violation of these efforts), it’s really hard to do this without visibility.
Organizations may think they’ve architected their environments this:
But the reality looks much different:
BloodHound Enterprise customers can now expand their use of BloodHound Enterprise beyond Tier Zero and properly map and enforce these boundaries by shutting down Attack Paths to Privilege Zones:
After defining custom zones, BloodHound Enterprise will automatically capture attack path choke points for remediation to implement separation of privilege:
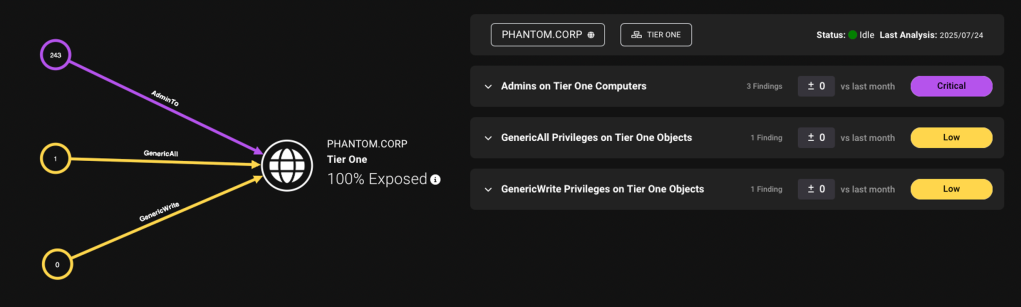
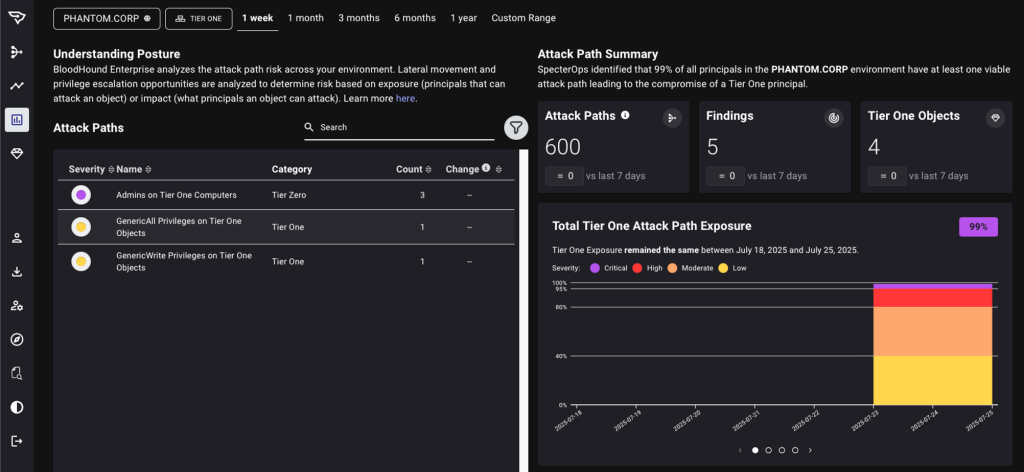
Defenders and Identity teams can now address these identity privilege violations at scale and implement the separation that makes sense for their organization, whether you adhere to the Tiered Administration / Enterprise Access Model or simply want to make sure your regular users don’t have access to business-critical data like PCI or HIPAA assets.
Read up on the full capabilities of Privilege Zones here or the announcement blog here.
Microsoft Privileged Identity Management (PIM)
Just-in-time access through Microsoft PIM, also known as Entra PIM, is a popular way to reduce always-on privilege, but in most environments, it’s either misconfigured or inconsistently applied. The result: temporary escalations that still create persistent risk.
BloodHound now detects attack paths that rely on PIM-eligible assignments, even if the role is not currently active. For BloodHound Enterprise customers, it also flags misconfigurations where Tier 0 roles or other custom privilege zone roles can be activated without multi-factor authentication.
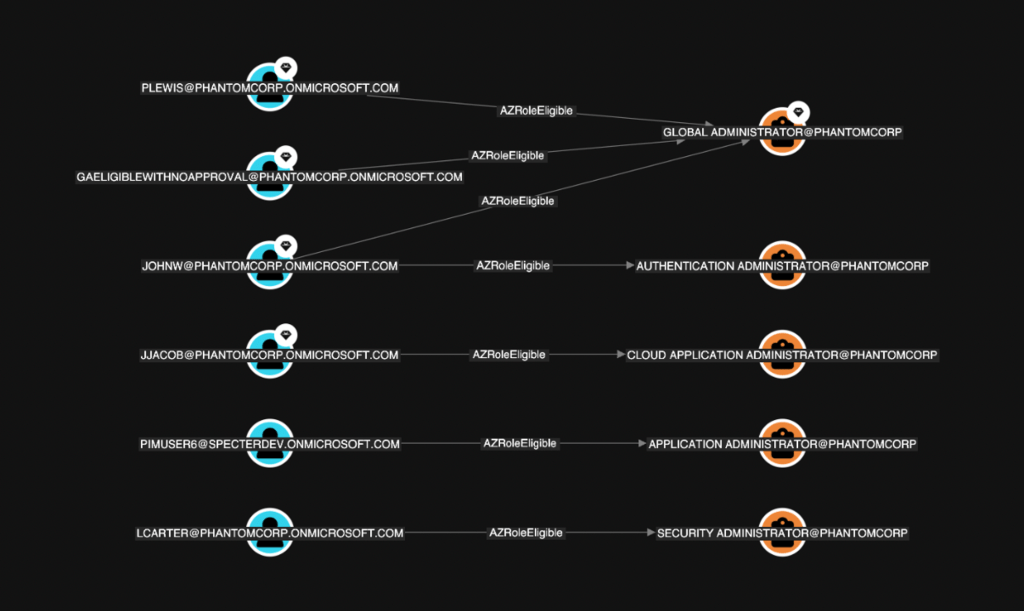
The feature introduces two new edge types:
- AZRoleEligible: The user or group is eligible to activate a privileged role.
- AZRoleApprover: The user or group is allowed to approve a role activation request
Modeling PIM Maturity in BloodHound
BloodHound now models the full range of PIM implementation patterns, from completely exposed to properly enforced.
PIM Maturity Stage 0: No PIM at All
Users or groups hold privileged roles that are always active. Every login creates a token with the role’s permissions, and those tokens are always available to any attacker with local access.
PIM Maturity Stage 1: Partially Implemented PIM
Users or groups must activate roles, but the activation process is weak or poorly enforced.
- Tokens created during login still allow the user to activate the role.
- If MFA isn’t required, or if users can approve their own requests, this creates a trivial privilege escalation path.
- Misconfigured PIM is often only marginally better than no PIM at all.
PIM Maturity Stage 2: Misconfigured PIM
BloodHound explicitly flags misconfigurations where PIM is in use but Tier 0 / Custom Zone roles do not require MFA.
This creates a critical gap—an attacker with a foothold can activate powerful roles without any additional barriers.
PIM Maturity Stage 3: Properly Configured PIM
This is what good looks like:
- Role activation requires MFA
- Tokens are only elevated after activation
- Even if an attacker has access to the system, they can’t activate the role without completing the same MFA challenge
Why This Matters
Most defenders assume that using PIM reduces identity attack surface. That’s only true if PIM is correctly enforced and paired with MFA and good hygiene. Otherwise, attackers can activate roles just as easily as the users they compromise.
With these updates, BloodHound closes a major visibility gap in cloud identity risk. You no longer have to guess whether a role is exploitable. You can see the path, understand the activation mechanism, and take action.
This also puts security and IAM teams on the same page. No more arguing over whether a user “really” has access. If BloodHound shows a viable path, it’s actionable.
Expanded visibility of Domain and Forest Trusts in Active Directory

BloodHound has also replaced the legacy TrustedBy edge with a new, more accurate trust model. The old edge was simple, but overly broad. It made trust relationships look like direct privilege escalation paths even when they weren’t exploitable. That led to false positives and confusion, especially in complex multi-domain environments.
The new model introduces four new trust edges, each designed to reflect whether a trust is present, how it’s configured, and whether it’s abusable.
Here’s what’s changed:
- TrustedBy is gone. It’s been split into edges that more precisely describe the type and abuse potential of each trust.
New Trust Edges
- SameForestTrust
Represents a trust between two domains in the same Active Directory forest. These trusts are always present and bidirectional.- Always traversable, because a compromise of one domain in a forest enables a compromise of others.
- Reflects the reality that AD domains are not security boundaries within a forest
- CrossForestTrust
Represents a trust between domains in different forests.- Not traversable by default. These trusts only become exploitable when misconfigured.
- This reduces noise and prevents false positives in environments with properly configured inter-forest trusts.
- AbuseTGTDelegation
Indicates that ticket-granting ticket (TGT) delegation is enabled on a cross-forest trust.- Traversable
- Enables coercion attacks where an attacker forces a DC in one domain to authenticate to them and captures the TGT.
- Models techniques like cross-forest DCSync via unconstrained delegation.
- SpoofSIDHistory
Indicates that SID history spoofing is possible due to weak SID filtering on a cross-forest trust.- Traversable
- Allows an attacker to spoof membership in privileged groups in the target domain.
- Highlights dangerous conditions that often go undetected without careful audit of trust configurations.
Check out Jonas’s blog for a deep dive on this new enhancement in trusts.
New Integrations to Improve Observability and Enhance Workflows (BloodHound Enterprise primarily)
Managing attack paths at scale involves making sure the practice fits with the systems and tools teams in use today to manage risk. In addition to our Splunk SIEM and Splunk SOAR integrations, we’re launching new additions to help teams operationalize their attack path data more efficiently:
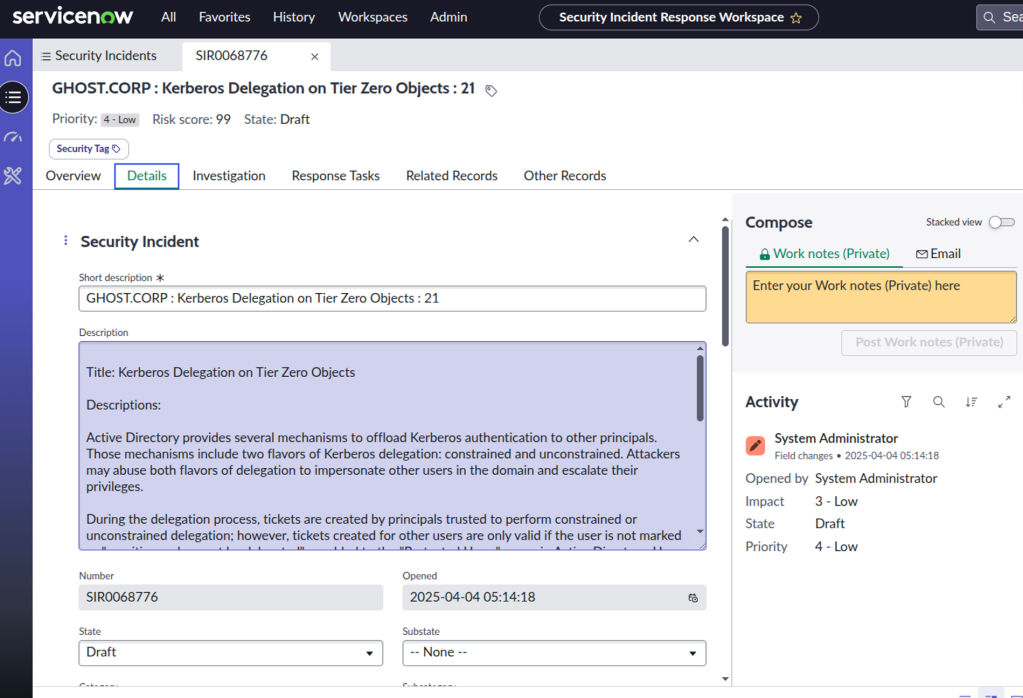
ServiceNow Incident Response
Available now in the ServiceNow Marketplace, BloodHound Enterprise’s ServiceNow Incident Response (SIR) module allows defenders and identity teams to automatically pull attack path choke points into their IT Service Management (ITSM) console for more streamlined remediations.
- Guided setup to get started
- Transform, map, and get the data to the teams who need it for remediation
- Customizable filtering to focus on priority environments or platforms
Cisco Duo Single Sign-On for BloodHound Enterprise
Duo Single Sign-On is a cloud-hosted SSO product that layers Duo’s strong authentication and flexible policy engine on top of BloodHound Enterprise logins. Duo Single Sign-On acts as an identity provider (IdP), authenticating your users using existing on-premises Active Directory (AD) or another SSO IdP. Duo SSO prompts users for two-factor authentication and performs endpoint assessment and verification before permitting access to BloodHound Enterprise.
Available now for Cisco Duo customers here.
BloodHound OpenGraph: Expanding the Frontiers of Identity Attack Paths
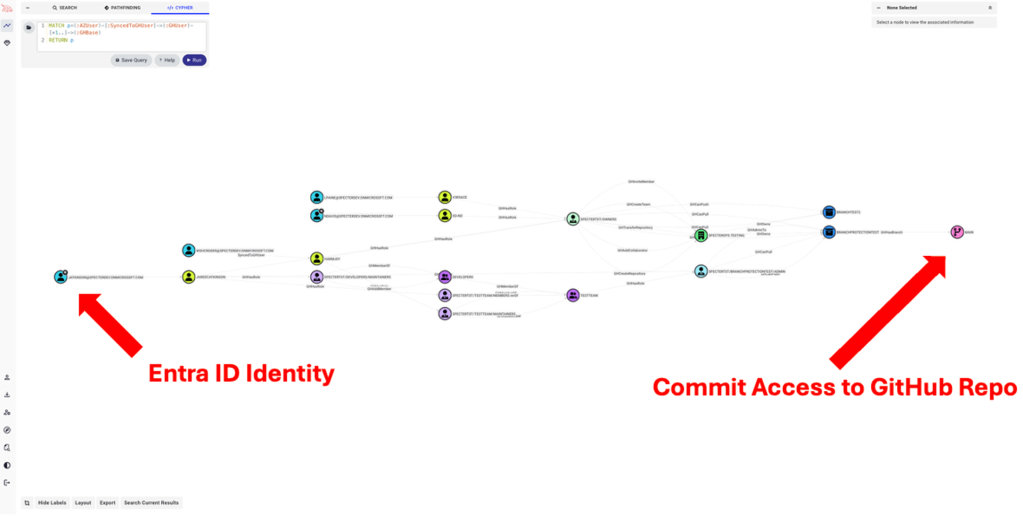
An Attack Path from Entra ID to Github using BloodHound OpenGraph
Saving the best for last, we’re so excited to announce BloodHound OpenGraph, opening up the ability to model attack paths in new platforms. Given the significance of this shift for BloodHound, I’ll be detailing why we did this in four key parts:
- The problem we wanted to solve
- BloodHound OpenGraph: A Foundation for the Future
- Key Benefits of BloodHound OpenGraph
- What’s next for BloodHound OpenGraph and how to get started
The Problem
When BloodHound first launched in 2016, it focused on the dominant identity system in most enterprises: Microsoft Active Directory. Over time, we expanded support to pull information from Windows endpoints, pushed to the cloud with Azure AD/Entra ID, and added coverage over Azure Graph API and Resource Manager. Focusing on Microsoft environments made sense for years, as AD and Azure Entra ID remained the backbone of identity in large enterprises, and for many, they still are. But the identity landscape has changed.
Modern environments are a hybrid of on-prem, cloud IaaS / PaaS, SaaS applications, federated IDPs, etc. GitHub repositories contain production secrets. Engineers escalate privilege through misconfigured AWS IAM roles. Third-party contractors gain access through Okta. The result is an increasingly fragmented identity surface, with hybrid attack paths that jump across platforms, many of which can not be modeled by BloodHound today.
We knew from the start that BloodHound Enterprise was not just an Active Directory security product, which is why we developed the concept of Attack Path Management in 2021. The reality is the logic we apply to create attack paths in Active Directory is no different than any other provider. Identities, privileges, and user behaviors collide to create attack paths within any platform.
Attackers, defenders, and identity teams know this too. For years, we’ve heard a consistent request from the BloodHound community and BloodHound Enterprise customers:

You fill in the blank: AWS, GCP, Okta, Kubernetes, SalesForce, custom internally developed applications. We get it – attack path management is an enterprise-wide need.
Before BloodHound OpenGraph, this process was complicated or excruciatingly slow. BloodHound previously had a rigid data ingestion process that was cumbersome to use, not just for our internal researchers but external parties as well. Datadog’s KubeHound project is a perfect example of this; the previous approach was too rigid and forced teams to completely separate tools for attack path research. This forced researchers to worry about things they shouldn’t have to (data management, visualization, etc.), but also missed critical hybrid attack paths between platforms (IAM roles to Kubernetes, for example).
BloodHound OpenGraph: A Foundation for the Future
BloodHound OpenGraph is our answer to a long-standing challenge: how to bring previously out-of-scope identity data into the graph- not as one-off integrations but as a general capability.
OpenGraph introduces a new, open ingestion framework that makes it possible to model arbitrary systems, identities, relationships, and abuse techniques. Whether you’re analyzing attack paths to code commit access, password vault permissions, misconfigured AWS IAM roles, or anything else — if you can describe it in terms of nodes and edges, you can map with OpenGraph.
Already, our team has used OpenGraph to model:
- GitHub Enterprise team structures and repo access
- 1Password vault permissions
- Microsoft SQL Server role chaining and escalation paths
Attack Paths from AD through Microsoft SQL using BloodHound OpenGraph
This is accomplished with a completely new data ingestion endpoint, which can accept generic attack graph data. Users can detail out custom nodes and edges, pick custom icons and colors, and immediately start digging in with Cypher searches in the Explore view.
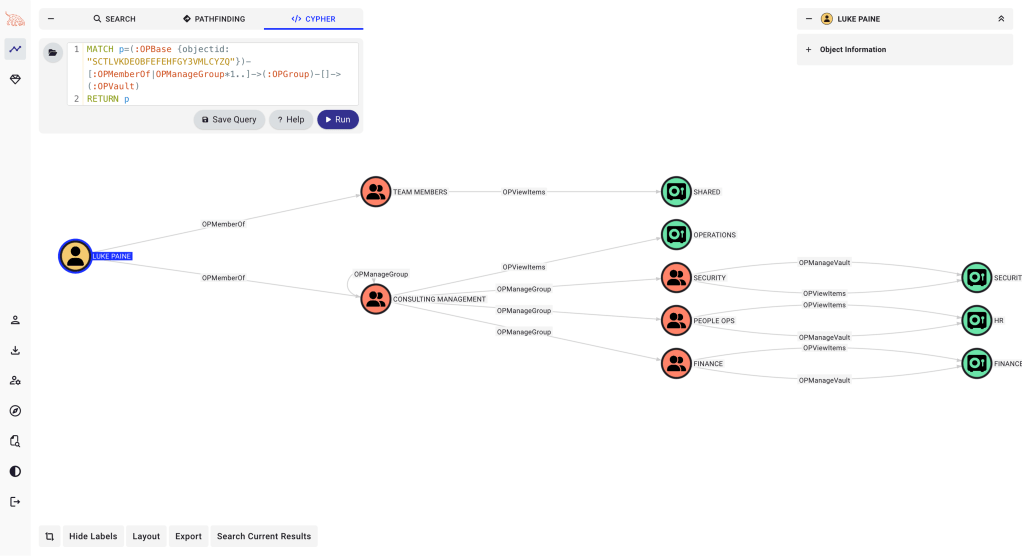
Exploring a 1Password instance to map user access to vaults
You can connect custom data to BloodHound’s existing data to find how an Active Directory user can SSH into Linux hosts or how a Non-Human Identity in Entra ID can take over a Kubernetes cluster.
We also thought comprehensively about how users would want to manage this custom-sourced data. At launch, we’re including controls to selectively delete all or specific types of data ingested through BloodHound OpenGraph. You can use our example extensions, analyze the results, and remove them from your BloodHound instance without affecting data sourced from SharpHound (Active Directory) or AzureHound (Azure / Entra ID).
Key Benefits of BloodHound OpenGraph
BloodHound OpenGraph doesn’t just make ingestion more flexible, it fundamentally changes how quickly and deeply we can explore identity attack paths.
Faster Research, Broader Coverage
BloodHound OpenGraph opens the possibilities to analyze attack paths in any platform, and it dramatically speeds up attack path research. What used to take our internal research team weeks to months to implement now takes hours.
The same speed boost applies to any researcher.
A New Power Tool for the Community
OpenGraph gives users of BloodHound Community Edition and BloodHound Enterprise a new level of control: define custom entities, model their relationships, and graph arbitrary identity systems. Want to explore IAM misconfigurations in GCP? Cross-platform SSO inheritance? Service account sprawl in a Secrets vault? You can build it — and share it.
We’ve already released several working examples in our documentation to show what’s possible. Note, users of BloodHound Legacy need to upgrade to BloodHound Community Edition to use BloodHound OpenGraph and benefit from the numerous improvements we’ve put in place over the past two years.
Enterprise Impact — Today and Tomorrow
For BloodHound Enterprise customers, OpenGraph sets the stage for deeper visibility and faster platform support. While the initial release is limited to Explore, the same ingestion foundation will power new first-class extensions with full support for attack path analysis, risk scoring, remediation documentation, and enforcement through Privilege Zones.
In short: OpenGraph accelerates everything.
What’s Next for OpenGraph — and How to Get Started
OpenGraph is launching today as a community-first capability. That means everything you need to start experimenting; schemas, documentation, and working examples is available now.
In the coming months, we’ll build on this foundation in three key ways:
- Support for Generic Entity Panels: At launch, BloodHound OpenGraph will support basic descriptions and data points for custom objects. We will extend this to build support for outbound / inbound control and other accordions to dive deeper into any identity or resource.
- Enterprise-Grade Collection: Data collection across BloodHound OpenGraph projects will depend on the specific project and may use a combination of scripts or tools to pull data. We’ll develop enterprise-supported collection methods to consume data directly from external providers with built-in support for authentication, error handling, and data normalization.
- Choke Point Analysis and Enforcement: BloodHound Enterprise will extend support for OpenGraph entities in attack path analysis, risk prioritization, remediation and Privilege Zones — giving defenders the same visibility and control across custom identity systems.
We’re also launching a community incentive program to reward original BloodHound OpenGraph contributions. If you’re building something with BloodHound OpenGraph, we want to see it, help you through the process, and share with the wider community. You can share your OpenGraph research here.
Get Started
- 📚 Explore the Docs: BloodHound OpenGraph Documentation
- 🧪 Try an Example Project: BloodHound OpenGraph Repository
- 🎁 Submit Your Contribution
This is the next evolution of BloodHound. We’re opening the graph — and we can’t wait to see what you build.


