Transforming Red Team Ops with Mythic’s Hidden Gems: Browser Scripting
TL;DR Mythic’s browser scripting provides tons of flexibility that operators can tailor to their unique needs to best analyze the data provided to them, beyond raw text output. Developers can further enable the operator experience by ensuring the agents are designed around using structured data in message responses.
Command and control (C2) frameworks have become the backbone of modern red team operations, providing the infrastructure needed to manage compromised systems and execute post-exploitation activities. While many frameworks exist in the offensive security landscape, few offer the architectural flexibility and operator-centric features that make Mythic truly unique. Today, we’ll explore what sets Mythic apart from other C2 frameworks and dive deep into one of its most underappreciated features: browser scripting for dynamic response formatting.
Before we get too far into the post, I want to put a disclaimer that this will be a mix of technical details riding the line of documentation and more higher level philosophy.
Understanding Mythic’s Unique Architecture
Beyond Traditional C2 Frameworks
Most C2 frameworks follow a monolithic design where the server, agents, and communication protocols are tightly coupled. Mythic takes a fundamentally different approach with a modular architecture designed to facilitate a plug-n-play ecosystem where new agents, communication channels, and modifications can happen on the fly. This isn’t just about modularity for the sake of it — it’s about creating a server-side language that provides developers with unprecedented freedom.
Fundamentally, Mythic uses a web-based front end (React) and Docker containers for the back-end. A GoLang server handles the bulk of the web requests via GraphQL APIs and WebSockets. This server then handles connections to the PostgreSQL database and communicates to the other Docker containers via RabbitMQ. This architecture enables individual components to exist on separate physical computers or virtual machines, providing deployment flexibility that traditional frameworks struggle to match.
The Server-Side Language Philosophy
What makes Mythic revolutionary is its approach as a server-side framework designed to provide a server-side language for handling diverse agent types. The Mythic repository itself does not host any payload types or any C2 profiles. Instead, Mythic provides a command that can be used to install agents into a current Mythic instance. This separation means that Mythic serves as a universal translator and orchestrator, capable of speaking to agents written in any language as long as they communicate using Mythic’s expected message format.
Due to this nature, profiles and agents can be developed separately from the server and then integrated into the platform. This design for a C2 framework is where Mythic really excels compared to other platforms. Developers have the freedom to create their own custom agents with unique capabilities for a central server.
The beauty of this approach lies in its extensibility. If an agent uses a communication method that Mythic doesn’t natively support, developers can create a new C2 profile to handle that specific protocol while still leveraging Mythic’s comprehensive server-side capabilities. Whether you’re building agents in C, Rust, Python, .NET, or even exotic languages like Nim, Mythic can accommodate them all through its standardized messaging interface.
Container-Based Development Freedom
The communications between the agents and the server are JSON based. Therefore, when we want to implement an agent in a low-level language like C/C++ that has no builtin JSON library, we need to use what they call a “translator container” that will transform our messages from JSON to binary and vice versa. This translator container system exemplifies Mythic’s philosophy: remove barriers to agent development by providing server-side solutions to common problems.
Mythic uses Docker and Docker-compose for all of its components, which allows Mythic to provide a wide range of components and features without having requirements exist on the host. Each payload type runs in its own containerized environment, complete with its own build dependencies, compilation tools, and runtime requirements. This means developers can focus on agent functionality rather than worrying about dependency conflicts or server-side prerequisites.
The Hidden Gem: Browser Scripting for Dynamic Response Formatting
While Mythic’s architectural flexibility gets attention in technical circles, one of its most valuable operator-focused features remains underutilized: browser scripting. This capability addresses a fundamental problem that, in our opinion, has plagued the offensive security community for years — the reliance on unstructured, plaintext responses that burden operators with manual parsing and analysis.
The Problem with Plaintext Responses
Traditional C2 frameworks typically return command output as raw text, leaving operators to manually sift through potentially massive amounts of data to identify valuable information. Consider a directory listing with hundreds of files, a process listing with dozens of running applications, or network enumeration results spanning multiple subnets. In these scenarios, operators must:
- Manually parse through verbose output
- Identify relevant information among noise
- Copy and paste data to craft follow-up commands
- Maintain mental context about discovered assets
- Struggle with inconsistent formatting across different commands
This approach represents a significant operational inefficiency that scales poorly with complex engagements. Browser scripting is a way for an agent developer or operator to dynamically adjust the output that an agent reports back. You can turn data into tables, download buttons, screenshot viewers, and even buttons for additional tasking.
Transforming Data into Intelligence
Browser scripting fundamentally changes how operators interact with C2 output by enabling dynamic, structured presentations of data. Instead of returning raw text, agents can provide structured data (JSON, XML, or other formats) that browser scripts transform into intelligent, interactive displays.
Interactive Tables with Contextual Actions
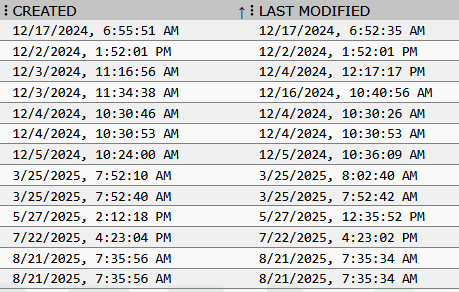
Interactive tables represent a powerful feature of Mythic’s browser scripting system, transforming dense command output into organized, actionable displays. Creating tables is a little more complicated than returning raw text, but not by much. Browser scripts return a dictionary with the key table which has an array of dictionaries, allowing multiple tables per response. Each table requires three core components: headers that define column structure and data types, rows containing the actual data with styling and interactive elements, and a title providing context for the table contents.
The header configuration controls not just appearance, but the fundamental behavior of each column. The type field is particularly critical, controlling data presentation and sorting behavior. String types provide alphabetical sorting, while size types automatically convert bytes to human-readable formats (1024 → 1KB). Date types handle various timestamp formats with proper chronological sorting, and number types ensure mathematical ordering rather than alphabetical. Button types disable sorting for interactive elements that don’t require ordering.
Visual Context and Row Styling
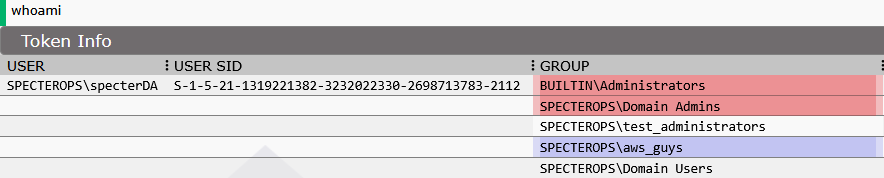
The real power emerges in row configuration, where each data point can include rich formatting and visual cues. Row-level styling applies CSS properties to entire rows for visual categorization — background colors to distinguish file types from directories, colored borders to highlight special properties like writable files, and conditional formatting based on security relevance.
Cell-level enhancement transforms static data into intelligent displays through the icon system. Mythic provides an extensive icon library designed for operational contexts: file and folder icons (folder, executable), action icons (download, upload), and status icons (security, warning). Each icon can be color-coded to create immediate visual assessment — red for high-value targets, orange for warnings, blue for information, green for safe operations. A full list of the icons available can be found in the ResponseDisplayTable code.
Advanced Button Integration
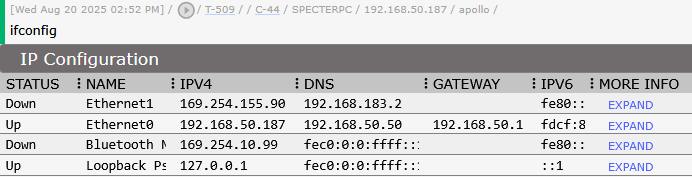
Within table cells, multiple button types enable different interaction patterns. Dictionary buttons display structured metadata in popup modals without cluttering the main view, perfect for detailed file properties or permission breakdowns. String buttons show unstructured data like file paths or command output in dedicated viewing windows. Task buttons enable immediate follow-up actions with pre-populated parameters, while menu buttons combine multiple actions into space-efficient dropdown menus.
The button system supports sophisticated contextual options that an operator or developer can use to extend the information provided from Mythic by default. File type recognition analyzes extensions and properties to determine appropriate actions — executables could get hash calculation options, documents could get metadata extraction capabilities, archives could get listing functions. Permission-based actions dynamically adjust based on security context, showing deletion options only for writable files with appropriate confirmations.
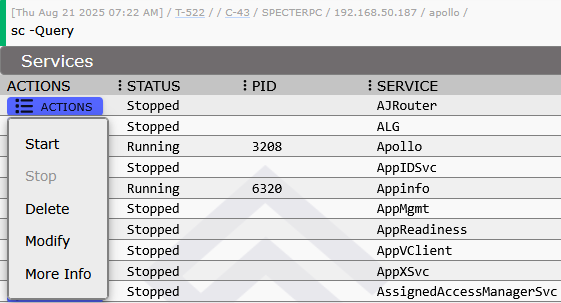
Task Buttons for Seamless Operations
Task buttons represent the operational bridge between data discovery and action execution, eliminating traditional workflow friction. The openDialog flag allows you to specify that the tasking popup modal should open and be partially filled out with the data you supplied in the parameters field. Similarly, the getConfirmation flag allows you to force an accept/cancel dialog to get the user’s confirmation before issuing a task.
Rather than discovering data, mentally noting details, switching contexts, and manually crafting commands, task buttons enable immediate action execution with pre-populated parameters and intelligent defaults.
Parameter Handling and Command Integration
Task buttons integrate seamlessly into any browser script element through a fundamental structure providing extensive control over user interaction. The ui_feature field serves as the critical link between browser scripts and Mythic’s command system. Each agent command must declare its UI feature in the command definition, enabling proper task routing when browser scripts reference these features. This is done by adding the supported_ui_features field into the command registration script, i.e. supported_ui_features = [“cat”]. Once added to the agent commands, the command can be referenced in the browser script with ui_feature:”cat” to execute those actions directly from the rendered data instead of executing the command manually.
Dialog Management and Risk Assessment
The openDialog and getConfirmation parameters provide crucial control over user interaction flow, enabling appropriate safety measures for different operation types. Safe reconnaissance operations like directory listings require no dialogs, moderate risk operations like file downloads benefit from parameter review dialogs, while high-risk operations like process injection require both parameter review and explicit confirmation with custom acceptance text. Advanced button styling can use icons and color coding for immediate risk assessment.
Visual Data Enhancement
Effective color coding creates immediate visual hierarchy and risk assessment, enabling operators to prioritize actions and identify critical information at a glance. A security-focused color palette can use red shades for immediate attention items like critical vulnerabilities and admin credentials, orange for caution-required items like executables and writable directories, blue for standard information like user documents and system data, purple for special handling items like encrypted content, and green for safe operations like downloads and backups. A legend of color coding can also be displayed to the operator to ensure the information is apparent without the need to look up the context.
Visual enhancement becomes most powerful when it responds intelligently to operational context, automatically applying appropriate styling based on data analysis. File extension analysis applies security-critical styling to .key, .pem, and certificate files with red key icons, while executable extensions get orange warning icons and document extensions receive blue informational styling. Network service recognition automatically assigns appropriate icons — web services get language icons, remote access services get key icons, and administrative services receive security icons.
Progressive Information Disclosure
Hover text provides crucial contextual information without cluttering the primary interface, enabling progressive disclosure of detailed information. This creates a layered information architecture where essential data remains visible at all times, additional details reveal on hover, and comprehensive information becomes available through buttons or popups. Effective hover text patterns show full file paths when displaying truncated names, provide relative time information alongside timestamps, explain permission implications, and display protocol details for network services.
Visual data enhancement transforms Mythic’s interface from a text-based command system into an intelligent visual environment where operators can immediately assess data relevance, security implications, and operational opportunities, dramatically reducing cognitive load while increasing operational awareness and efficiency.
Advanced Browser Scripting Capabilities
Screenshot and Media Display
Screenshots represent one of the most operationally valuable data types in red team engagements, providing immediate visual context that can reveal critical information about target environments, user activities, and security postures. Browser scripts transform screenshot handling from a cumbersome file management task into an integrated intelligence gathering capability.
The screenshot display system supports both single and multiple image rendering through a sophisticated gallery interface. When agents capture screenshots of multiple monitors or take sequential captures over time, browser scripts can present these as organized galleries rather than separate file downloads. This approach maintains operational context — operators can see the progression of user activities or compare different desktop states without losing track of which command generated which screenshot.

Inline Media Integration: Screenshots integrate directly into task results, eliminating context switching between command outputs and file management interfaces. The media key in browser script responses enables automatic rendering with filename and agent_file_id specifications. Also, as the name of the media key implies, this method can be used to display more media than just screenshot images. If operators prefer not to have media auto-render, user settings provide toggle control, offering a button-based authorization approach before displaying potentially sensitive visual content.
Download Management
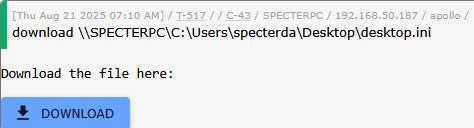
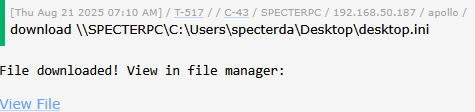
When downloading files from a target computer, it can be configured so the user is able to click a button in-line with the tasking to download the resulting file(s) instead of then having to go to another page to download it or running the download command and pasting in the filename.
File exfiltration represents a critical phase of most red team operations, but traditional C2 frameworks often create friction between file discovery and actual data extraction. Mythic’s download management capabilities eliminate this friction through intelligent integration of download functionality directly into reconnaissance results.
Streamlined Exfiltration Workflows: Download management extends beyond individual files to support sophisticated exfiltration workflows. Batch download capabilities enable operators to queue multiple files for simultaneous transfer, while automatic organization categorizes downloads by file type, source system, or operational phase. Integration points with external analysis tools allow immediate processing of exfiltrated data without manual file handling, such as with Nemesis.
Progress and Status Management: The system can track transfer progress through plaintext fields displaying completion status and total chunks, providing operators with realistic expectations for transfer completion times. This transparency enables better operational planning, particularly for large files or bandwidth-constrained environments. Browser scripts can display partial progress information during ongoing transfers, maintaining operational awareness even for long-running exfiltration tasks.
Search Integration
Sometimes you’ll want to link back to the “search” page (tasks, files, screenshots, tokens, credentials, etc) with specific pieces of information so that the user can see a list of information more cleanly.
Search integration represents the connective tissue that transforms individual discoveries into comprehensive operational intelligence. Rather than treating each command output as an isolated piece of information, browser scripts can create intelligent cross-references that build operational timelines and reveal patterns across different data sources.
The search link system operates through the search response key, creating direct links to Mythic’s global search interface with pre-populated query parameters. These links use the same URL parameters that manual searches generate, enabling browser scripts to construct sophisticated search queries that operators can then refine or expand. The display structure includes plaintext descriptions, hover text for context, and the actual search parameters targeting specific data types and search fields.
Intelligent Cross-Referencing: Search integration becomes most powerful when it connects related information across different operational domains. Discovered credentials link directly to the global credential store, enabling operators to see all instances where specific accounts appear across the engagement. File discoveries connect to the comprehensive file tracking system, showing everywhere specific filenames or paths have been encountered.
Implementation Examples
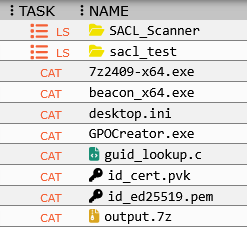
File Listing Enhancement
First, let’s start with a traditional example of a directory listing. For this, we’ll look to the industry standard Cobalt Strike. Using the builtin ls command, we obtain the size, type, last modified date, and name of the files and sub directories within a simple listing structure as though we were to execute the same listing via the CLI. However there is little context or information outside of this listing, nor directly actionable items of interest for us. If we want additional information, we copy and paste items into other commands, like icacls, or if we want to send the data to another system for triage, the listing format is not a very robust structure for further data analysis.
With browser scripting, this becomes an interactive table where extensions determine appropriate file type icons, each row includes download buttons pre-configured with the full file path, executable files get additional context menus for analysis options, and document files link to potential credential extraction tasks.
This transformation represents the fundamental value proposition of Mythic’s browser scripting — converting static, hard-to-parse text into actionable intelligence interfaces. The raw file listing provides basic information but requires manual interpretation and command construction for follow-up actions. The enhanced version eliminates cognitive overhead by presenting the same data with immediate visual categorization and embedded operational capabilities.
Breaking Down a Real-World Implementation: Apollo’s File Browser
Let’s examine how Apollo’s ls_new.js browser script transforms basic directory listings into sophisticated operational interfaces. This real-world implementation demonstrates every major browser scripting concept working together to create a comprehensive file management solution. The script we are using as our example here is this commit in case you want to follow along.
Architectural Foundation and Error Handling
The script begins with essential error handling and response validation:
function(task, responses) {
if (task.status.includes("error")) {
const combined = responses.reduce((prev, cur) => {
return prev + cur;
}, "");
return { 'plaintext': combined };
} else if (responses.length > 0) {This pattern establishes the fundamental browser script architecture — always handle error conditions first, ensure responses exist before processing, and provide fallback plaintext display when structured processing fails. The error handling prevents browser script failures from breaking the operator interface, maintaining operational continuity even when commands encounter unexpected conditions.
Intelligent File Type Classification System
Apollo implements a sophisticated file categorization system using frozen objects and extension mappings:
const FileType = Object.freeze({
ARCHIVE: 'archive',
DISKIMAGE: 'diskimage',
WORD: 'word',
EXCEL: 'excel',
POWERPOINT: 'powerpoint',
PDF: 'pdf',
DATABASE: 'db',
KEYMATERIAL: 'keymaterial',
SOURCECODE: 'sourcecode',
IMAGE: 'image'
});
const fileExtensionMappings = new Map([
[".zip", FileType.ARCHIVE],
[".doc", FileType.WORD],
[".pem", FileType.KEYMATERIAL],
// … extensive mappings
]);This approach demonstrates advanced visual data enhancement principles. Rather than hardcoding icon assignments throughout the script, Apollo creates a centralized classification system that maps file extensions to semantic categories. The frozen object pattern prevents accidental modification of core file types, while the Map structure provides efficient extension lookups for large directory listings.
Dynamic Visual Styling and Icon Assignment
The visual enhancement system automatically applies appropriate styling based on file classification:
const fileStyleMap = new Map([
[FileType.KEYMATERIAL, {
startIcon: 'key',
startIconHoverText: "Key Credential Material",
}],
[FileType.ARCHIVE, {
startIcon: "archive",
startIconHoverText: "Archive File",
startIconColor: "goldenrod",
}],
[FileType.SOURCECODE, {
startIcon: 'code',
startIconHoverText: "Source Code",
startIconColor: "rgb(25,142,117)",
}],
]);This demonstrates strategic color coding in practice. Key material receives security-focused styling to draw immediate attention, while archives get distinctive coloring to indicate they require investigation. Source code files get developer-friendly styling that communicates their technical nature. The hover text provides progressive information disclosure — operators get immediate visual categorization with detailed context available on demand.
Contextual Action Generation
Apollo’s action system demonstrates sophisticated task button implementation with contextual intelligence:
let entrySubTaskAction = function (data, entry) {
if (entry["is_file"]) {
let cat_parameters = "";
if (entry["full_name"].includes(":")) {
cat_parameters = entry["full_name"];
} else {
cat_parameters = "\\\\" + data["host"] + "\\" + entry["full_name"];
}
return {
name: "cat",
type: "task",
ui_feature: "cat",
parameters: cat_parameters,
}
} else {
return {
name: "ls",
type: "task",
ui_feature: "file_browser:list",
startIcon: "list",
parameters: {
host: data["host"],
full_path: entry["full_name"],
}
}
}
};This function exemplifies contextual action generation — files get content viewing capabilities while directories get navigation options. The parameter handling demonstrates both string and dictionary approaches, with the cat command using string parameters for UNC path construction, while directory listing uses structured dictionary parameters. The ui_feature field properly maps to Apollo’s command system, enabling seamless task routing.
Advanced Menu System Implementation
The actions menu showcases sophisticated button integration with multiple interaction patterns.
actions: {
button: {
startIcon: "list",
name: "Actions",
type: "menu",
value: [
{
name: "Extended Attributes",
title: "Viewing Extended Attributes for " + entry["name"],
type: "dictionary",
leftColumnTitle: "Extended Attributes",
rightColumnTitle: "Values",
startIcon: "list",
value: {
"Extended Attributes": entry["extended_attributes"],
},
},
{
name: "Access Control Entries",
type: "table",
title: "Viewing Access Control Lists for " + entry["name"],
// … nested table structure
},
{
name: "Download",
type: "task",
disabled: !entry["is_file"],
startIcon: "download",
ui_feature: "file_browser:download",
parameters: {
host: data["host"],
full_path: entry["full_name"],
}
},
{
name: "Delete",
type: "task",
startIcon: "delete",
ui_feature: "file_browser:remove",
getConfirmation: true,
parameters: {
host: data["host"],
full_path: entry["full_name"],
}
},
]
}
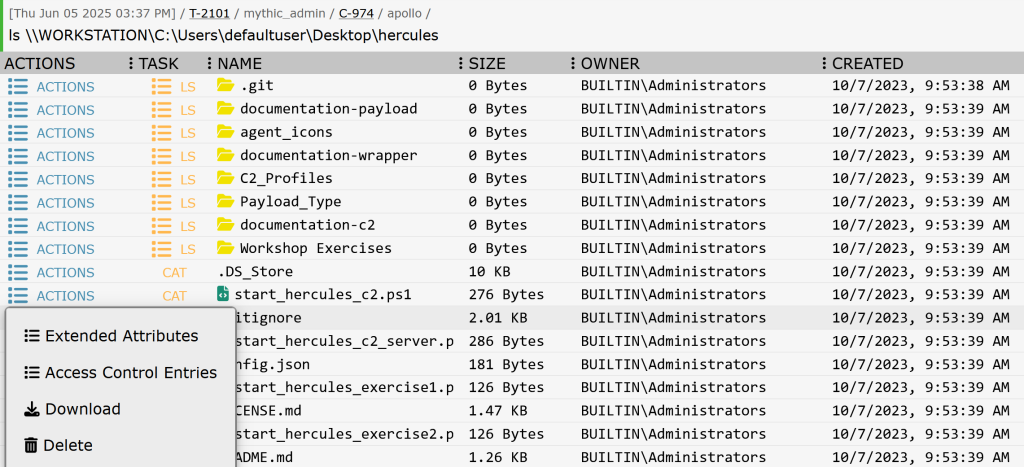
}This menu demonstrates every major button type working together. Dictionary buttons display extended attributes without cluttering the main interface. Table buttons create nested tables for ACL information, showing how browser scripts can present complex hierarchical data. Task buttons provide immediate operational capabilities with appropriate safety measures — downloads execute immediately for efficiency, while deletions require confirmation to prevent accidents. The disabled property shows contextual availability — download options only appear for files, not directories.
Table Architecture and Data Integration
Apollo’s table structure demonstrates comprehensive header configuration and row management:
let formattedResponse = {
headers: [
{
plaintext: "actions",
type: "button",
width: 120,
disableSort: true,
},
{
plaintext: "name",
type: "string",
fillWidth: true,
},
{
plaintext: "size",
type: "size",
width: 100,
},
// … additional headers
],
title: "",
rows: [],
};The header configuration showcases data type intelligence — the size column uses the “size” type for automatic human-readable conversion, while the name column uses “string” type with fillWidth for optimal space utilization. Button columns disable sorting since action menus don’t have meaningful sort orders. This attention to data type details ensures the interface behaves intuitively for operators.
Operational Integration and Data Flow
The script’s data processing loop demonstrates how browser scripts integrate with agent responses:
for (let i = 0; i < responses.length; i++) {
let data = {};
try {
data = JSON.parse(responses[i]);
} catch (error) {
console.log(error);
const combined = responses.reduce((prev, cur) => {
return prev + cur;
}, "");
return { 'plaintext': combined };
}
// Process structured data…
}This pattern handles the reality of agent communication — responses might be malformed JSON, network issues might cause partial responses, or agents might return unexpected data structures. The fallback to plaintext ensures operators never lose access to raw command output, while the structured processing provides enhanced capabilities when data permits. Bringing it all together in an organized and informational table for the operator to analyze and act upon without excessive manual parsing.

Implementation Possibilities
Process Enumeration Potential
Listing processes can transform from a wall of text into an intelligent overview with multiple visualization approaches. Traditional table formats might categorize processes by type (system, user, security tools) with color-coded visual representation of memory usage and CPU consumption. Suspicious processes can be automatically highlighted through pattern recognition, while each process entry includes context menus for injection, monitoring, or termination.
The process enumeration enhancement can follow similar patterns to file listing but adapt the contextual intelligence for process-specific operations. Visual categorization might use color coding to distinguish system processes (red security icons) from user processes (blue person icons), while memory usage gets automatic conversion to human-readable formats through the size column type.
Network Discovery Visualization Potential
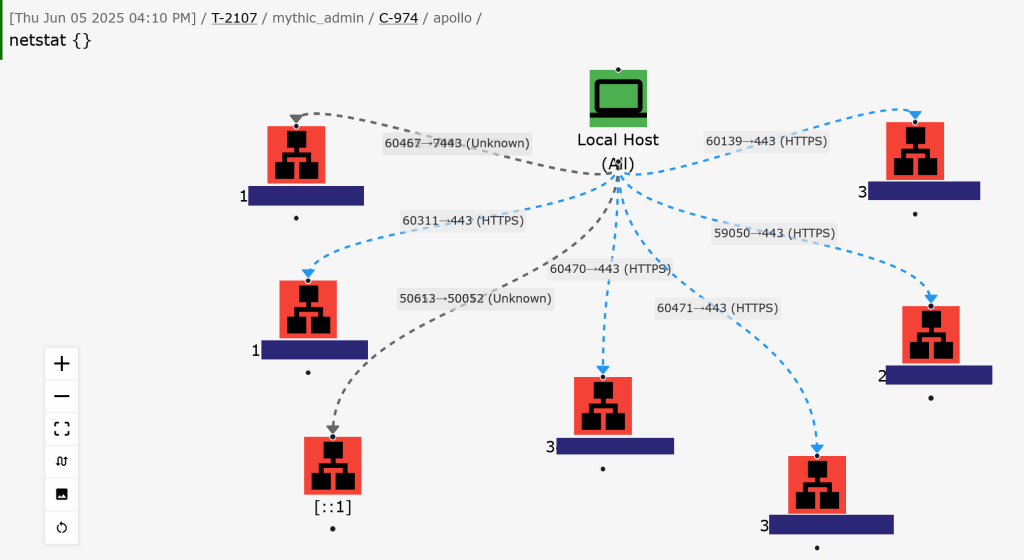
Network enumeration results present perhaps the most compelling case for advanced browser scripting visualization. While traditional table presentations could show discovered hosts in sortable formats with color-coded service types and quick action buttons for further enumeration, the graph functionality opens significantly more sophisticated possibilities.
Using Mythic’s graph engine, network discovery could render as interactive network maps where discovered hosts become nodes with computer icons, colored by operating system or security posture. Edges could represent network relationships — direct connections, shared subnets, or discovered trust relationships. Service enumeration results could overlay additional icons showing web services (language icons), database services (database icons), or administrative services (security icons).
Graph Implementation for Network Discovery: The graph system supports nodes with unique IDs, custom images (computer, lan, language icons), styling for visual categorization, and overlay images for status indicators. Each discovered host becomes a node with:
- Base Image: Computer icon colored by OS type or criticality
- Overlay Icons: Service type indicators (web, database, admin)
- Node Data: Host information, open ports, discovered services
- Context Buttons: Quick access to enumeration tools specific to discovered services
Edges between nodes could represent network relationships with animated connections for active communications, colored lines indicating connection types (direct, routed, VPN), and edge labels showing protocols or port information. The interactive nature allows operators to click nodes for detailed information or right-click for context menus with host-specific actions.
This visualization approach transforms linear network enumeration output into spatial intelligence maps where operators can immediately understand network topology, identify critical infrastructure nodes, and plan lateral movement paths through visual relationship analysis rather than mental correlation of text-based data. For example, one operator may want their netstat output as a simple table in the first figure below while another may want a graph like the second figure.
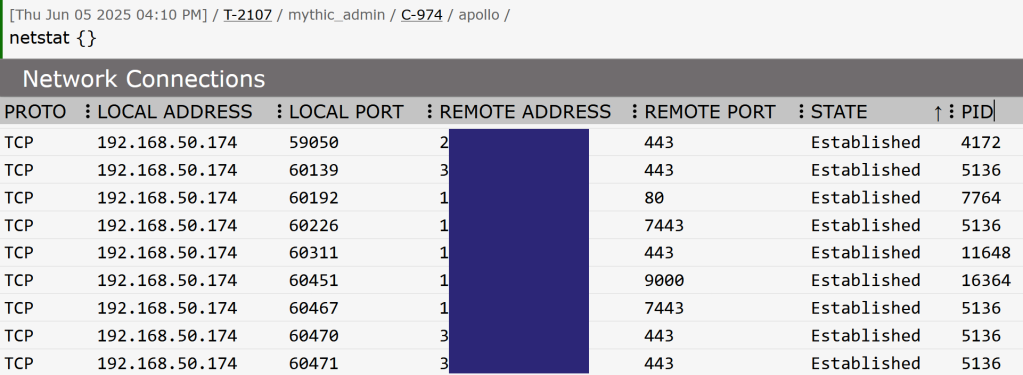
Advanced Integration Scenarios
These implementation examples demonstrate potential approaches for browser scripting transformation of red team operations. The choice between table, graph, or hybrid presentations depends on the specific operational context and data relationships. File systems naturally suit hierarchical table presentations, while network topologies benefit from spatial graph visualization. Process relationships could effectively use either approach — tables for detailed process information, graphs for relationship visualization.
The flexibility of Mythic’s browser scripting system enables operators to choose visualization approaches that best serve their analytical needs, transforming passive data consumption into active intelligence interaction regardless of the specific presentation format selected.
Operational Impact
The true value of browser scripting becomes apparent during complex, multi-system engagements where operators manage dozens of compromised hosts and thousands of data points. Instead of maintaining mental context about discovered assets or manually cross-referencing information across multiple text-based outputs, operators work with a living, interactive intelligence picture that grows more valuable as the engagement progresses.
Browser scripts eliminate the friction between discovery and action. When an operator discovers an interesting file, they don’t need to remember its path, switch contexts, and manually craft a download command — they click the download button that was intelligently generated as part of the initial discovery. When process enumeration reveals a security tool, the operator can immediately access injection options without memorizing process IDs or researching appropriate techniques.
This transformation from passive data consumption to active intelligence interaction represents a fundamental shift in how operators approach C2 management. Rather than being data processors, operators become intelligence analysts working with purpose-built tools that understand their operational needs.
Developer and Operator Perspectives
For Developers: Structured Output as a Design Philosophy
Browser scripting fundamentally changes how developers can approach agent design, encouraging a shift from human-readable text outputs to structured data that enables rich interactive experiences. This philosophical change impacts every aspect of agent development, from command output formatting to data collection strategies.
Structured Response Design Evolution: Traditional agent development focused on creating human-readable output that operators could understand when viewing raw text. Browser scripting inverts this priority — agents can return JSON objects with predictable schemas that browser scripts can parse and enhance. The human-readable presentation becomes the browser script’s responsibility, not the agent’s. This separation of concerns enables the same agent data to support multiple presentation formats without agent modifications.
Consider the difference between traditional process enumeration that returns formatted text strings versus structured JSON containing process objects with defined fields for PID, name, user, memory usage, and parent relationships. The structured approach enables browser scripts to create sortable tables, visual process trees, memory usage charts, or parent-child relationship graphs from the same underlying data.
Contextual Metadata and Forward-Thinking Design: Effective browser scripting requires developers to include metadata that may not be immediately visible but enables rich functionality. File enumeration agents should return not just filenames and sizes, but also full paths, permission details, file types, creation dates, and hash information. Network enumeration should include protocol details, banner information, and service version data. Process enumeration benefits from command line arguments, loaded modules, and network connections.
This additional context enables browser scripts to make intelligent decisions about visual presentation, available actions, and operational workflows. The extra data overhead typically proves minimal compared to the operational value gained through enhanced interface capabilities.
Action Enablement Through Data Structure: Developers should consider the complete operational workflow when designing agent responses. File discovery should include the full path information for immediate download actions. Process enumeration should provide the data necessary for injection, monitoring, or termination tasks.
The key insight involves understanding that agent responses feed directly into operator decision-making processes. By structuring data to support common operational workflows, developers enable browser scripts to present immediate action options rather than requiring operators to mentally parse output and manually construct follow-up commands.
Schema Consistency and Validation: Structured output requires consistent schemas across different operating systems, environments, and command variations. A file listing command could return the same JSON structure whether executed on Windows, Linux, or macOS, even though the underlying file system concepts differ. This consistency enables browser scripts to work reliably across diverse target environments. Doing so cuts down duplicate work in creating these scripts for operational use and also supports the expansion of data analysis in other tooling such as Nemesis.
Developers can implement response validation to ensure schema compliance and provide meaningful error messages when validation fails. This approach prevents browser script failures that could degrade the operator experience and maintains operational continuity even when unexpected conditions occur.
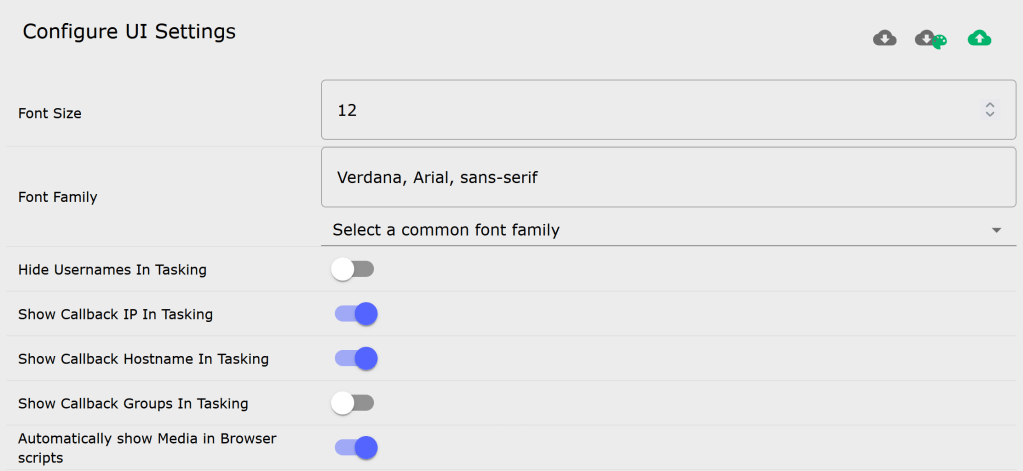
For Operators: Customization and Adaptation
As an operator, they exist in the web interface under the Mythic sidebar menu “Extra Shortcuts” -> “ <\> Browser Scripts”. You can enable and disable these for yourself at any time, and you can even modify or create new ones from the web interface as well.
Browser scripts represent a fundamentally democratized approach to interface customization, enabling operators to adapt their working environment to match specific engagement needs, personal preferences, and evolving operational requirements without requiring developer intervention or server modifications.
Real-Time Customization Capabilities: The browser script interface provides immediate customization capabilities that respond to operational dynamics. During active engagements, operators can modify existing scripts to highlight specific patterns, add custom actions for discovered attack vectors, or create new visualization approaches for unique data types encountered during the operation.
This flexibility proves particularly valuable during complex, long-term engagements where operational priorities shift over time. Initial reconnaissance phases might benefit from broad data collection and general-purpose visualizations, while later exploitation phases could require focused interfaces that highlight specific vulnerability types or attack paths.
Engagement-Specific Script Development: Operators can develop scripts tailored to specific client environments, attack scenarios, or compliance requirements. Financial services engagements might require scripts that automatically identify and highlight PCI-relevant data, while healthcare assessments could focus on HIPAA-related information discovery. Manufacturing environments might benefit from industrial control system identification and visualization.
The web-based editing interface enables rapid iteration and testing of custom scripts without requiring development environment setup or deployment procedures. Operators can experiment with different visualization approaches, test action workflows, and refine interface elements in real-time during engagements.
Collaborative Script Development: Browser scripts can be shared among team members and adapted for different operational roles. Senior operators might develop sophisticated scripts that junior team members can use and learn from. Specialized roles like network penetration testers or application security analysts can create domain-specific scripts that enhance their particular operational focus.
The ability to enable and disable scripts per operator means that different team members can maintain personalized interface configurations while working on the same engagement. This approach prevents interface conflicts while enabling knowledge sharing and collaborative improvement of operational tools.
Operational Security and Script Management: Browser script customization includes important operational security considerations. Scripts that automatically highlight specific data types might inadvertently reveal operational priorities to other team members or create audit trails that could compromise operational security. Operators must balance interface enhancement with appropriate information compartmentalization.
The per-operator script management system enables fine-grained control over what information each team member sees and how it’s presented. This capability supports both operational security requirements and role-based access patterns that many organizations require for compliance and operational effectiveness.
Learning and Skill Development: Browser script customization serves as an excellent learning tool for operators seeking to improve their technical skills. The immediate feedback loop of script modification and interface changes enables rapid experimentation and learning. Operators can start with simple modifications to existing scripts and gradually develop more sophisticated customizations as their understanding grows.
This hands-on approach to interface development helps operators better understand the underlying data structures, command relationships, and operational workflows that drive effective red team operations. The skills developed through browser script customization often transfer to other areas of technical operations and tool development.
Integration with External Tools: Custom browser scripts can bridge the gap between Mythic’s interface and external tools that operators need for specialized analysis. Scripts can format data for easy import into network analysis tools, threat intelligence platforms, reporting systems, or to integrate efficiently with another one of Mythic’s hidden gems, Consuming Containers (more to follow on these). Copy functionality can be customized to format data according to external tool requirements, streamlining operational workflows that span multiple platforms.
This integration capability transforms Mythic from an isolated C2 platform into a central hub that connects with broader operational toolchains, improving overall engagement efficiency and reducing the overhead associated with tool switching and data translation the operator must do.
The Broader Mythic Ecosystem
Browser scripting represents just one facet of Mythic’s operator-centric design philosophy. Data modeling, tracking, and analysis are core aspects of Mythic’s ability to provide quality of life improvements to operators. From the very beginning of creating a payload, Mythic tracks the specific command and control profile parameters used, the commands loaded into the payload and their versions, who created it, when, and why.
This comprehensive data tracking enables browser scripts to access rich operational context, creating intelligent displays that understand not just what data was discovered, but how it relates to the broader engagement timeline and objectives.
Conclusion: Elevating Red Team Operations
Mythic’s browser scripting capability represents more than a quality-of-life improvement — it’s a fundamental reimagining of how operators should interact with C2 data. By transforming passive plaintext consumption into active intelligence interaction, browser scripts enable operators to focus on analysis and decision-making rather than data processing and manual task orchestration.
The combination of Mythic’s flexible server-side architecture and its browser scripting capabilities creates a platform where the barriers between data discovery and actionable intelligence are minimized. For red teams seeking to improve operational efficiency and reduce cognitive load during complex engagements, browser scripting represents a significant competitive advantage that many operators have yet to fully appreciate.
As the offensive security community continues to mature, tools like Mythic’s browser scripting point toward a future where operators work with intelligent, adaptive interfaces rather than static text terminals. The question isn’t whether your current C2 framework can display text — it’s whether it can transform that text into intelligence that accelerates your operations and enhances your analytical capabilities.
The hidden gems within Mythic aren’t just features — they’re force multipliers that redefine what’s possible in red team operations. Browser scripting is just the beginning of what becomes achievable when C2 frameworks prioritize operator experience alongside technical capability.


