Cody Thomas
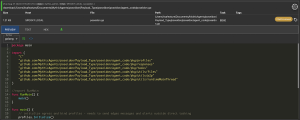
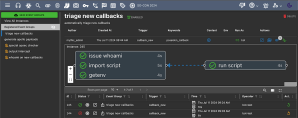
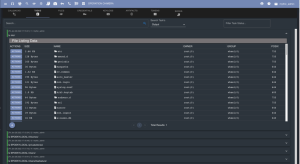
Cody Thomas is a Senior Software Engineer at SpecterOps specializing in offensive software development where he is the original author and maintainer of the Mythic Command and Control framework. He was the course architect for Adversary Tactics: Mac Tradecraft and performed offensive macOS research.
See the latest by Cody Thomas