blog category
Blog

Research & Tradecraft
Is Kerberoasting Still a Risk When AES-256 Kerberos Encryption Is Enabled?
TL;DR Kerberoasting is fundamentally a weak password problem. Stronger encryption slows down cracking, but it doesn’t...
By: Elad Shamir
Oct 21, 2025 • 4 min read
Read Post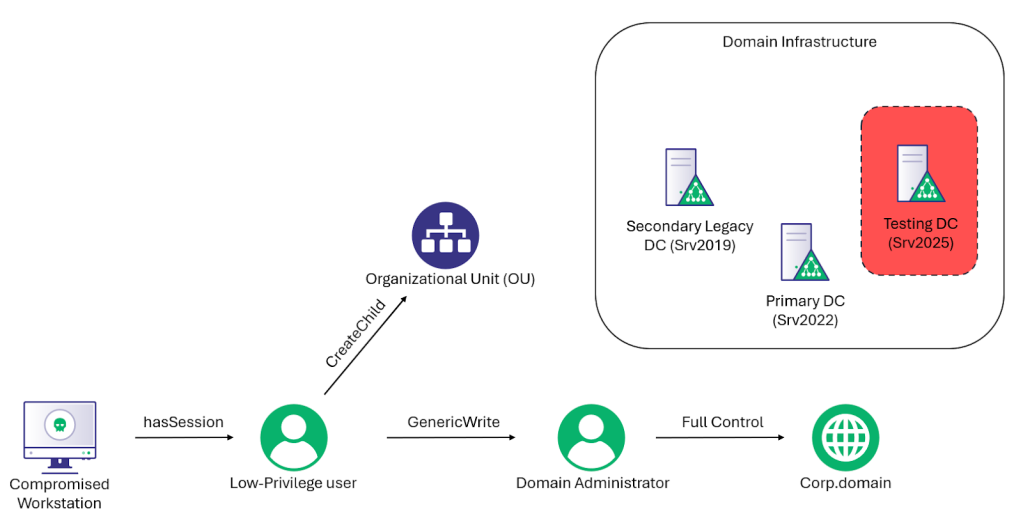
Research & Tradecraft
The (Near) Return of the King: Account Takeover Using the BadSuccessor Technique
TL;DR – After Microsoft patched Yuval Gordon’s BadSuccessor privilege escalation technique, BadSuccessor returned with another blog...
By: Logan Goins
Oct 20, 2025 • 13 min read
Read Post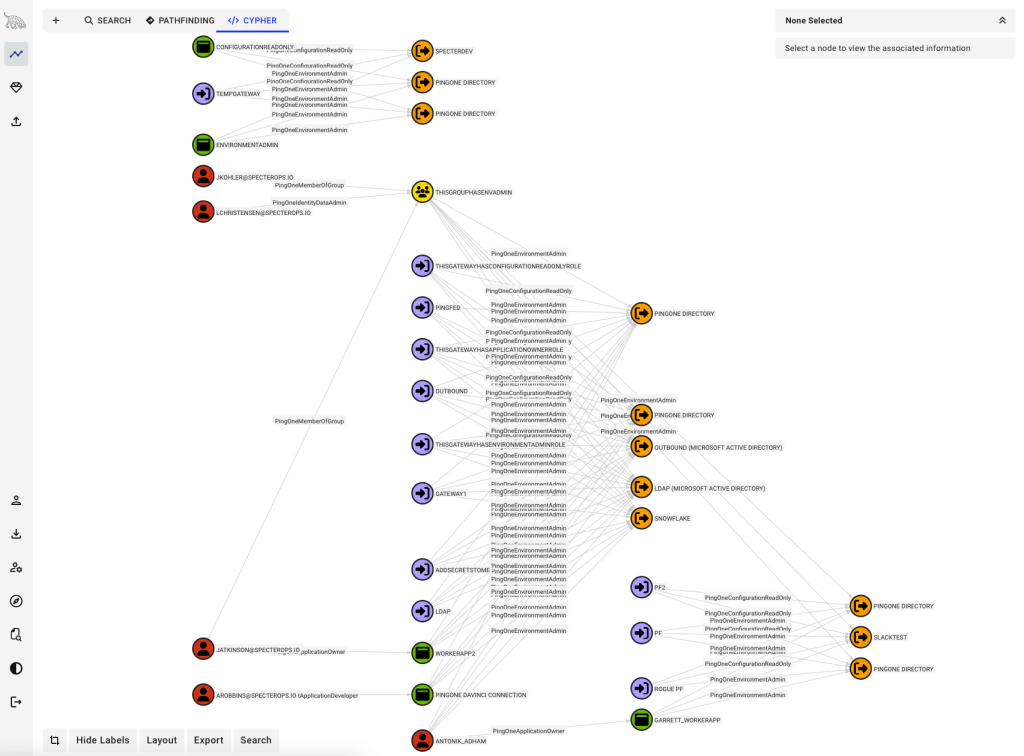
BloodHound
TL;DR: You can use PingOneHound in conjunction with BloodHound Community Edition to discover, analyze, execute, and...
By: Andy Robbins
Oct 20, 2025 • 14 min read
Read Post
Blog
TL;DR Large Language Models (LLMs) are an evolution of a long history of turning non-mathy things...
By: Blaise Brignac
Oct 16, 2025 • 26 min read
Read Post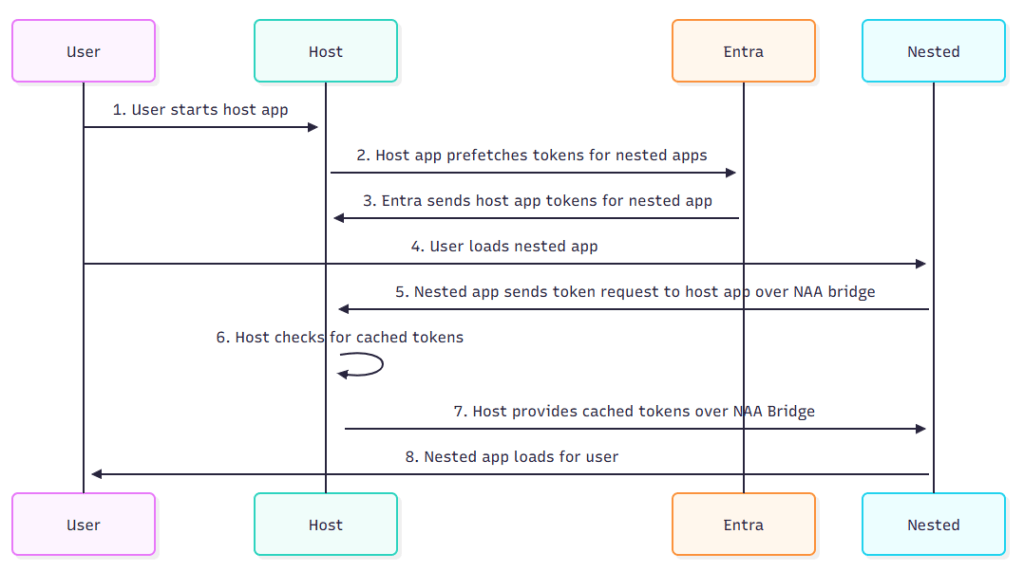
Research & Tradecraft
TL;DR This writeup is a summary of knowledge and resources for nested application authentication (NAA) and...
By: Hope Walker
Oct 15, 2025 • 12 min read
Read Post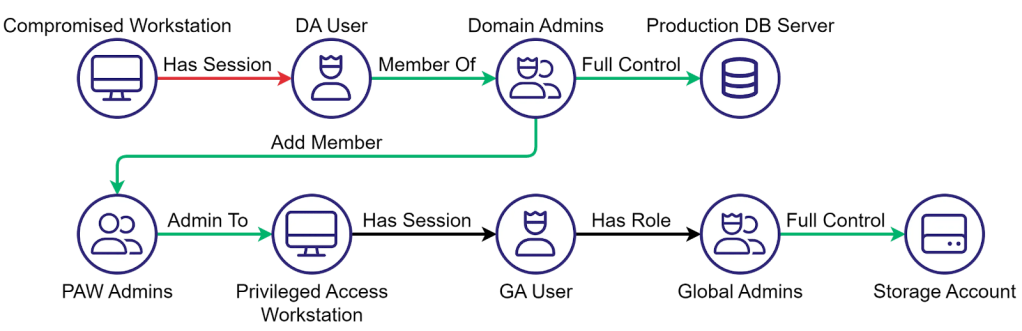
BloodHound
The Clean Source Principle and the Future of Identity Security
TL;DR Modern identity systems are deeply interconnected, and every weak dependency creates an attack path — no...
By: Jared Atkinson
Oct 8, 2025 • 13 min read
Read Post
Research & Tradecraft
AI Gated Loader: Teaching Code to Decide Before It Acts
TL;DR AI gated loaders collect telemetry, apply a policy with an LLM, and execute only when...
By: John Wotton
Oct 3, 2025 • 12 min read
Read Post
Research & Tradecraft
WriteAccountRestrictions (WAR) – What is it good for?
TL;DR A lot of things. The User-Account-Restrictions property grants read/write permissions to the user-account-control LDAP attribute,...
By: Garrett Foster
Oct 1, 2025 • 20 min read
Read Post
Research & Tradecraft
DCOM Again: Installing Trouble
TL;DR I am releasing a DCOM lateral movement beacon object file (BOF) that uses the Windows...