blog category
BloodHound
BloodHound
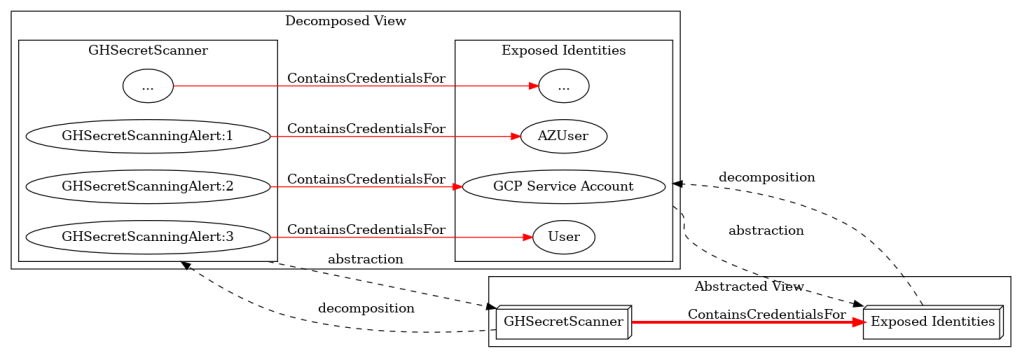
Taming the Attack Graph: A Many Subgraphs Approach to Attack Path Analysis
TL;DR This blog presents a framework using technology subgraphs, decomposition, and graph abstraction to model hybrid...
By: JD Crandell
Nov 13, 2025 • 8 min read
Read Post
BloodHound
ShareHound: An OpenGraph Collector for Network Shares
TL;DR: ShareHound is an OpenGraph collector for BloodHound CE and BloodHound Enterprise that maps network shares,...
By: Remi GASCOU
Oct 30, 2025 • 7 min read
Read Post
BloodHound
TL;DR: You can use PingOneHound in conjunction with BloodHound Community Edition to discover, analyze, execute, and...
By: Andy Robbins
Oct 20, 2025 • 14 min read
Read Post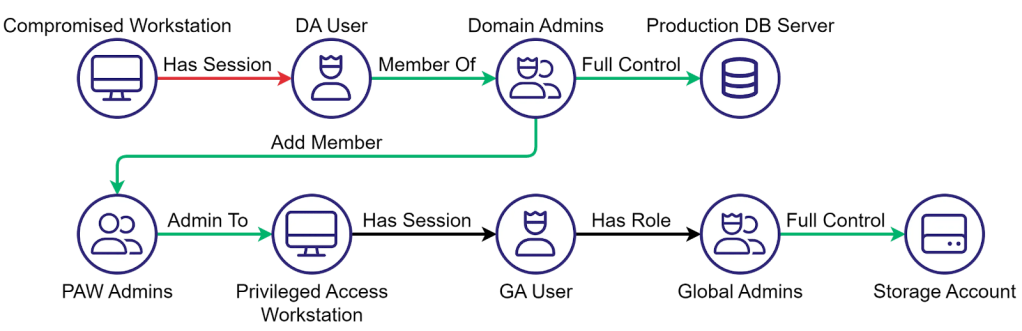
BloodHound
The Clean Source Principle and the Future of Identity Security
TL;DR Modern identity systems are deeply interconnected, and every weak dependency creates an attack path — no...
By: Jared Atkinson
Oct 8, 2025 • 13 min read
Read Post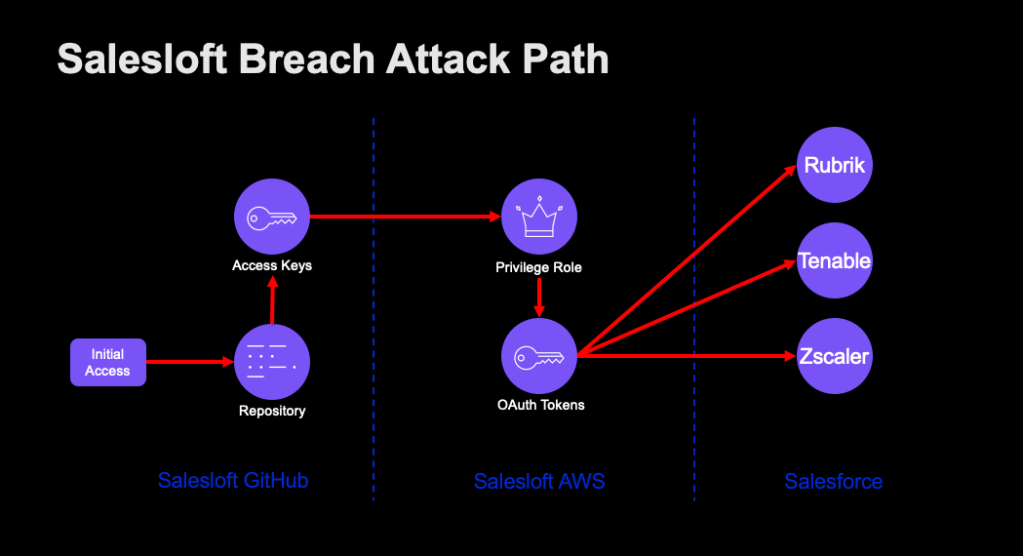
BloodHound
The Salesloft–Drift Breach: An Attack Path Case Study
TL;DR This post analyzes the Salesloft–Drift incident through an attack path lens, showing how violations of...
By: Jared Atkinson
Sep 24, 2025 • 11 min read
Read Post
BloodHound
BloodHound Operator: The Six Degrees Of Master Yoda
A Technical Dive Into BloodHound OpenGraph With BloodHound Operator & Master Yoda… TL;DR: The latest version...
By: SadProcessor
Sep 4, 2025 • 17 min read
Read Post
BloodHound
Adding MSSQL to BloodHound with OpenGraph
TL;DR MSSQLHound is a standalone PowerShell collector that adds 7 new nodes and 37 new MSSQL...
By: Chris Thompson
Aug 4, 2025 • 27 min read
Read Post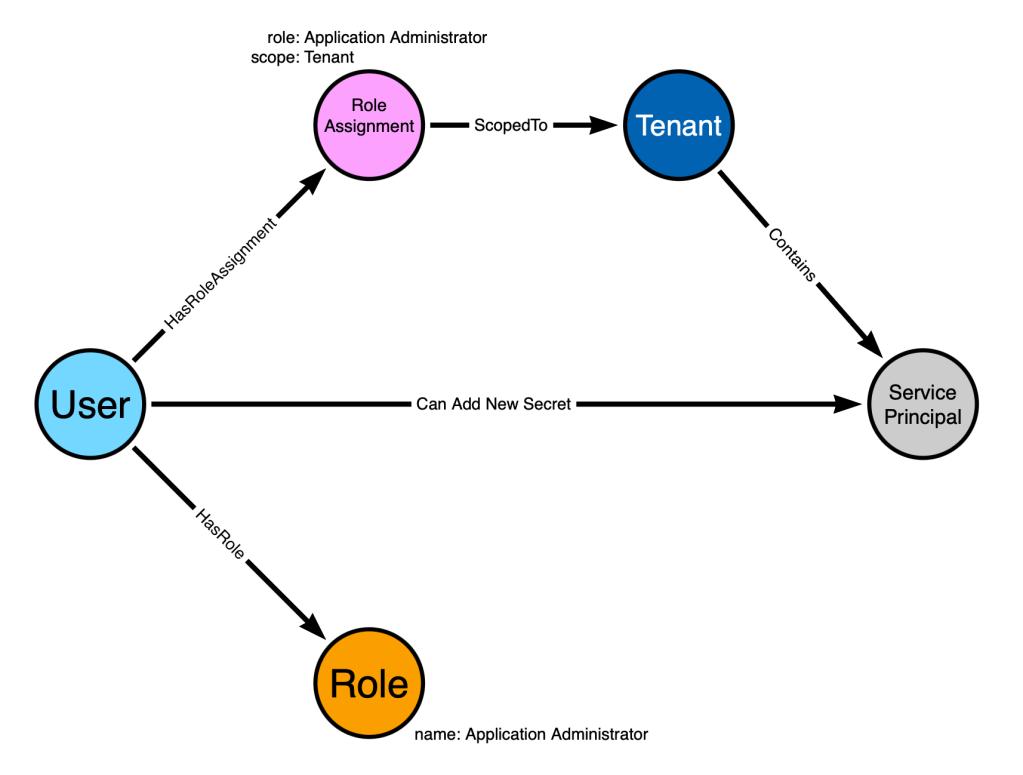
BloodHound
Attack Graph Model Design Requirements and Examples
TL;DR OpenGraph makes it easy to add new nodes and edges into BloodHound, but doesn’t design...
By: Andy Robbins
Aug 1, 2025 • 34 min read
Read PostBloodHound
BloodHound v8: Usability, Extensibility, and OpenGraph
TL;DR BloodHound v8 introduces exciting new features enabling users to get more and do more with...