blog category
Research & Tradecraft


Research & Tradecraft
Automating Azure Abuse Research — Part 2
By: Andy Robbins
Aug 31, 2022 • 8 min read
Read Post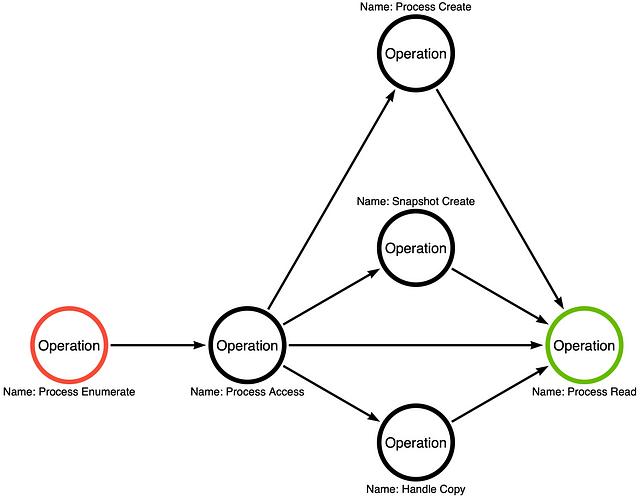
Research & Tradecraft
Part 5: Expanding the Operation Graph
By: Jared Atkinson
Aug 18, 2022 • 17 min read
Read Post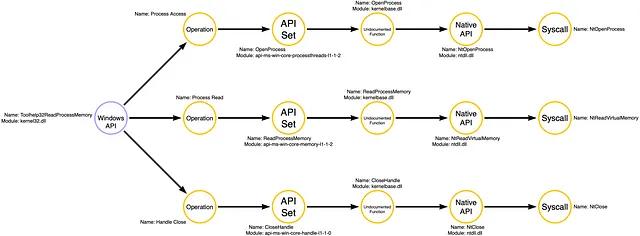
Research & Tradecraft
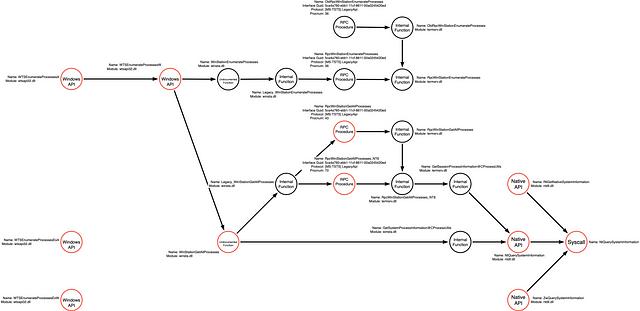
Part 3: Expanding the Function Call Graph
By: Jared Atkinson
Aug 9, 2022 • 15 min read
Read Post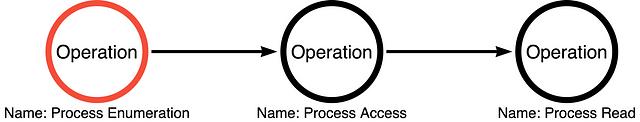
Research & Tradecraft
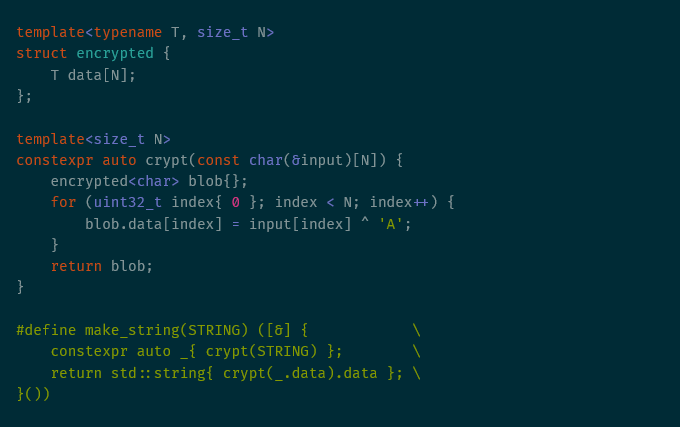
Encrypting Strings at Compile Time
Thank you to SpecterOps for supporting this research and to Duane and Matt for proofreading and...
By: Evan McBroom
Jul 20, 2022 • 5 min read
Read Post
Research & Tradecraft
Part 1: Discovering API Function Usage through Source Code Review