blog category
Research & Tradecraft
Research & Tradecraft
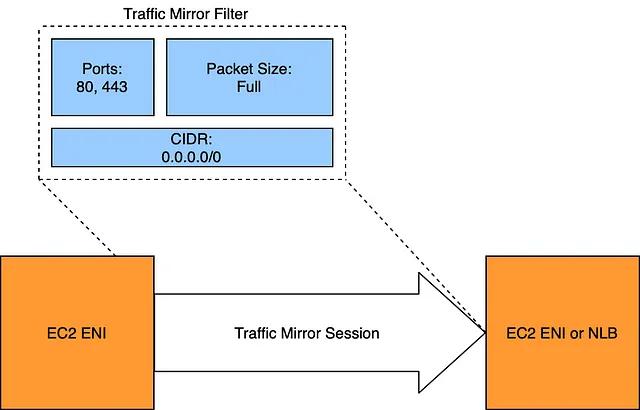
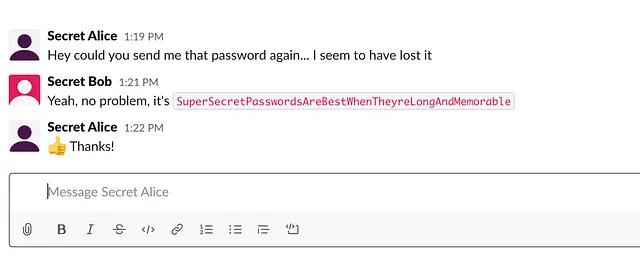
Abusing Slack for Offensive Operations
By: Cody Thomas
Mar 4, 2020 • 9 min read
Read Post
Research & Tradecraft
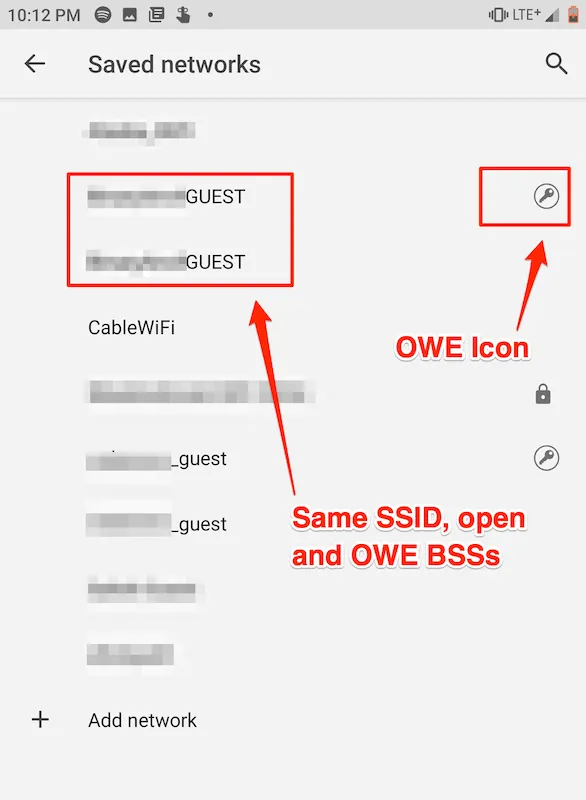
In early 2019, myself and fellow Denver-based researcher Steve Darracott (@theDarracott) set out to answer the question...
By: Gabriel Ryan
Feb 12, 2020 • 12 min read
Read Post

Research & Tradecraft
Ghostwriter: 2020 Feature Update
We introduced Ghostwriter in July 2019 when we felt it was a good v1.0, but active development never...
By: Christopher Maddalena
Jan 29, 2020 • 8 min read
Read Post
Research & Tradecraft
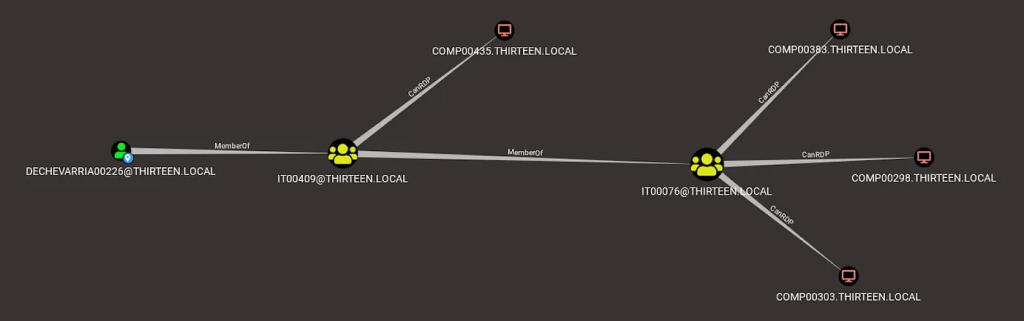
Revisiting Remote Desktop Lateral Movement
It’s no secret that attackers are looking for new techniques to execute lateral movement. However, there...
By: Steven Flores
Jan 22, 2020 • 8 min read
Read Post
Research & Tradecraft
Satellite: A Payload and Proxy Service for Red Team Operations