blog category
Research & Tradecraft

Research & Tradecraft
DCOM Again: Installing Trouble
TL;DR I am releasing a DCOM lateral movement beacon object file (BOF) that uses the Windows...
By: Craig Wright
Sep 29, 2025 • 12 min read
Read Post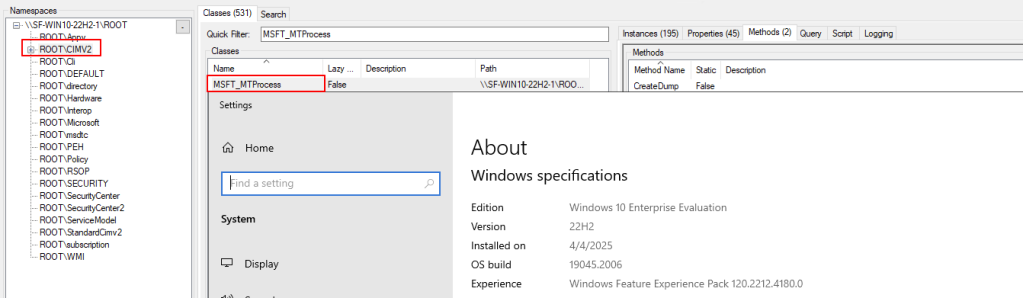
Research & Tradecraft
TL;DR: Win32_Process has long been the go-to WMI class for remote command execution. In this post we...
By: Steven Flores
Sep 18, 2025 • 7 min read
Read Post
Research & Tradecraft
This One Weird Trick: Multi-Prompt LLM Jailbreaks (Safeguards Hate It!)
TL;DR: Using multiple prompts within the context of a conversation with an LLM can lead to...
By: Max Andreacchi
Sep 5, 2025 • 13 min read
Read Post
Research & Tradecraft
Dough No! Revisiting Cookie Theft
TL;DR Chromium based browsers have shifted from using the user’s Data Protection API (DPAPI) master key...
By: Andrew Gomez
Aug 27, 2025 • 15 min read
Read Post
Research & Tradecraft
Operating Outside the Box: NTLM Relaying Low-Privilege HTTP Auth to LDAP
TL;DR When operating out of a ceded access or phishing payload with no credential material, you...
By: Logan Goins
Aug 22, 2025 • 13 min read
Read Post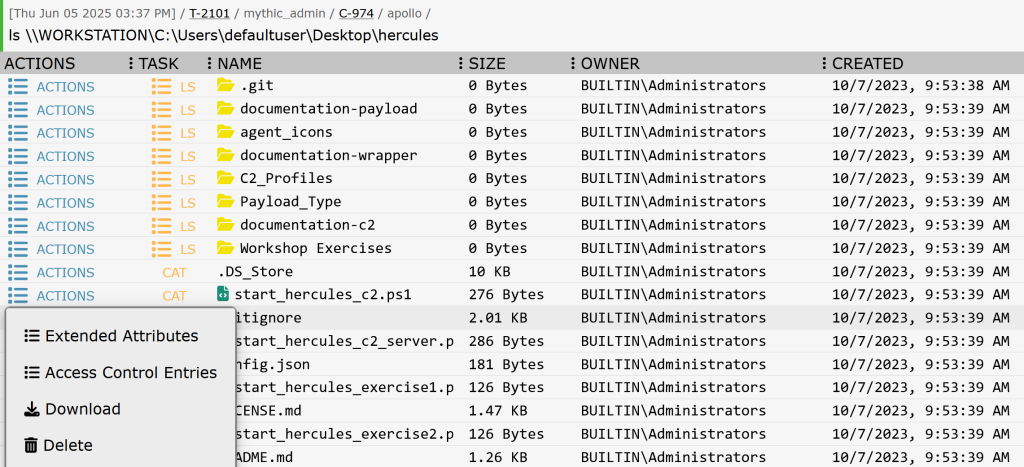
Research & Tradecraft
Transforming Red Team Ops with Mythic’s Hidden Gems: Browser Scripting
TL;DR Mythic’s browser scripting provides tons of flexibility that operators can tailor to their unique needs...
By: Alexander K. DeMine
Aug 21, 2025 • 30 min read
Read Post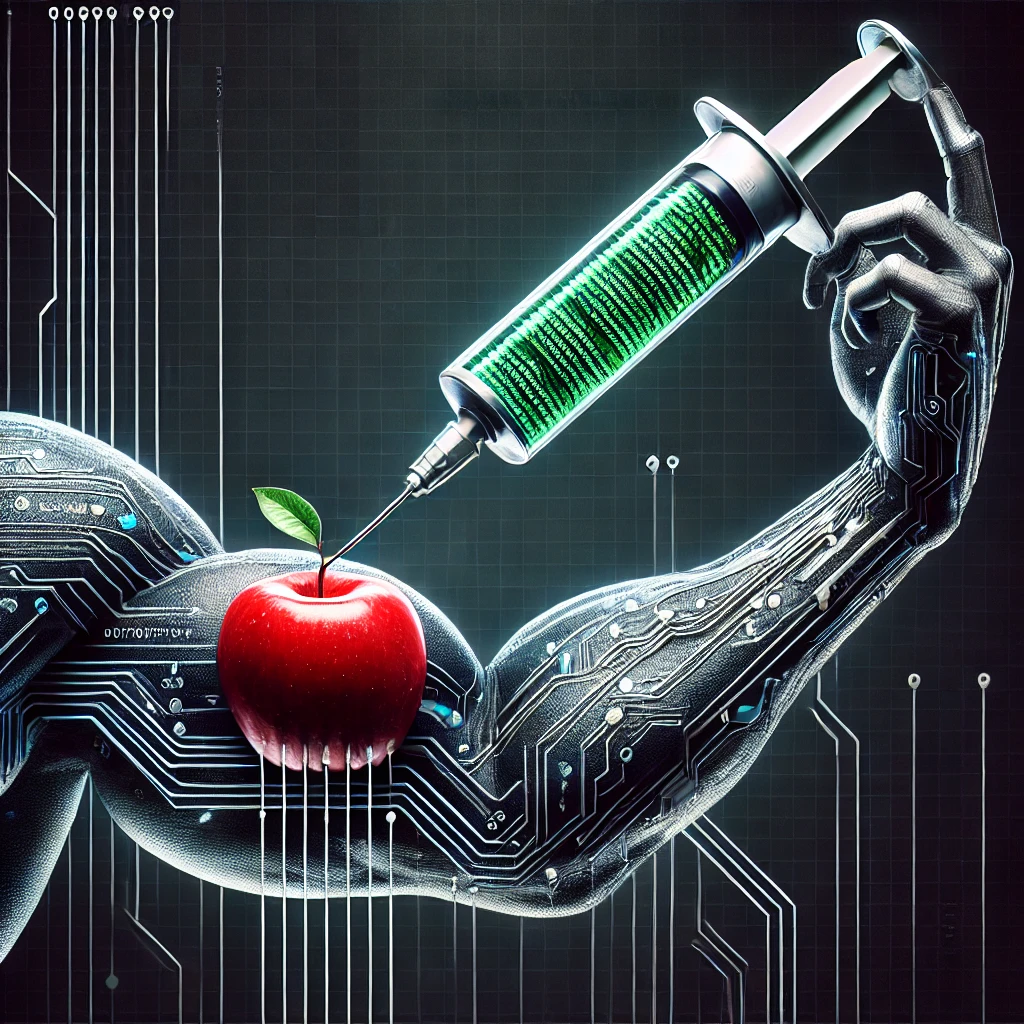
Research & Tradecraft
ARM-ed and Dangerous: Dylib Injection on macOS
Modern Dylib Injection Techniques for AArch64 macOS TL;DR This post details how I extended the Mythic...
By: West Shepherd
Aug 21, 2025 • 24 min read
Read Post
Research & Tradecraft
TL;DR WebClient is a common targeted service for NTLM relay attacks. In this post we will...
By: Steven Flores
Aug 19, 2025 • 31 min read
Read Post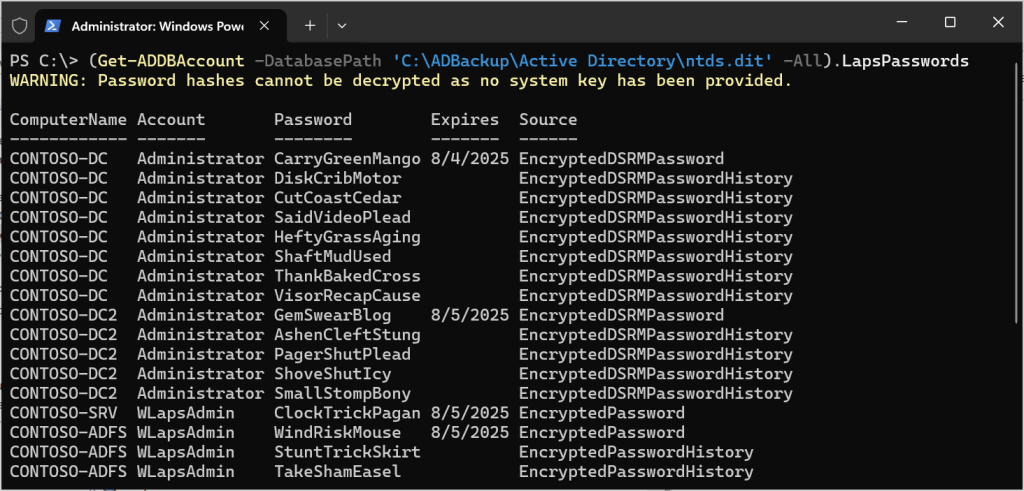
Research & Tradecraft
Juicing ntds.dit Files to the Last Drop
TL;DR Several new Active Directory offline attack capabilities have recently been added to the DSInternals PowerShell module....