blog category
Research & Tradecraft

Research & Tradecraft
Going for Broke(ring) – Offensive Walkthrough for Nested App Authentication
TL;DR: Microsoft uses nested app authentication (NAA) for many applications. Access and refresh tokens for select...
By: Hope Walker
Aug 13, 2025 • 19 min read
Read Post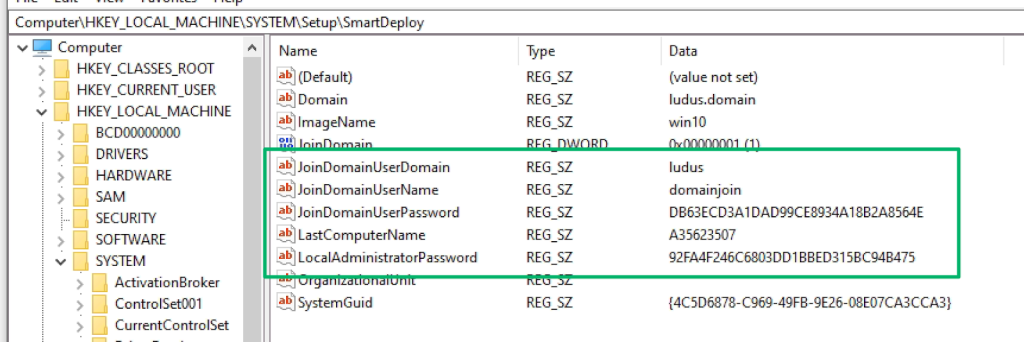
Research & Tradecraft
HKLM\SYSTEM\Setup\sMarTdEpLoY – The (Static) Keys to Abusing PDQ SmartDeploy
TL;DR: Prior to version 3.0.2046, PDQ SmartDeploy used static, hardcoded, and universal encryption keys for secure...
By: Garrett Foster
Aug 12, 2025 • 10 min read
Read Post
Research & Tradecraft
TL;DR Due to modern advances in the AD CS attack landscape, an update to Certify was...
By: Valdemar Carøe
Aug 11, 2025 • 16 min read
Read Post
Research & Tradecraft
TL;DR We took a chainsaw to Nemesis 1.0, kept the parts that operators loved (i.e., automated...
By: Will Schroeder
Aug 5, 2025 • 7 min read
Read Post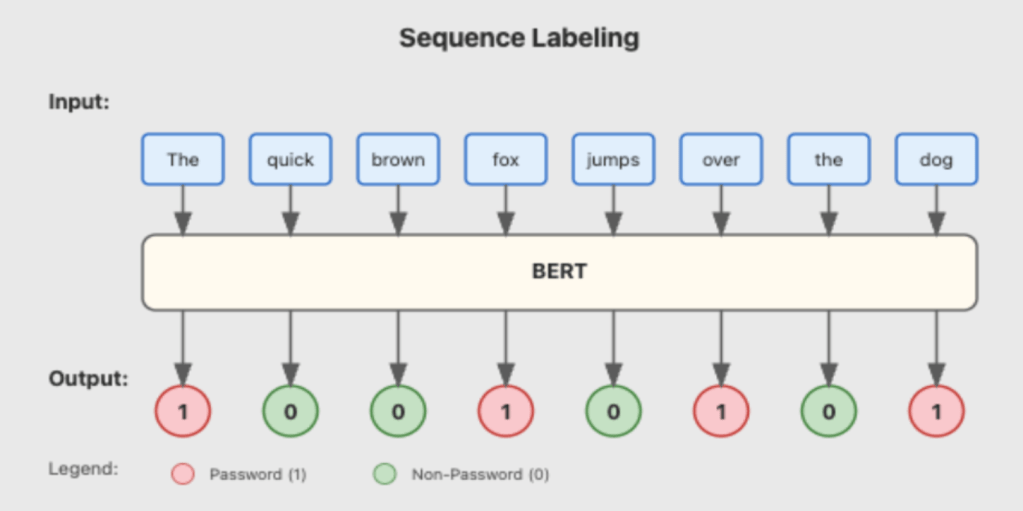
Research & Tradecraft
What’s Your Secret?: Secret Scanning by DeepPass2
TL;DR DeepPass2 is a secret scanning tool that combines regex rules, a fine-tuned BERT model, and...
By: Neeraj Gupta
Jul 31, 2025 • 14 min read
Read Post
Research & Tradecraft
Entra Connect Attacker Tradecraft: Part 3
TL;DR Attackers can exploit Entra Connect sync accounts to hijack device userCertificate properties, enabling device impersonation...
By: Daniel Heinsen
Jul 30, 2025 • 16 min read
Read Post
Research & Tradecraft
Make Sure to Use SOAP(y) – An Operators Guide to Stealthy AD Collection Using ADWS
Learn how to perform stealthy recon of Active Directory environments over ADWS for Red Team Assessments
By: Logan Goins
Jul 25, 2025 • 17 min read
Read Post
Research & Tradecraft
TL;DR: Ghostwriter now supports real-time collaborative editing for observations, findings, and report fields using the YJS...
By: Christopher Maddalena
Jul 23, 2025 • 4 min read
Read Post
Research & Tradecraft
I’d Like to Speak to Your Manager: Stealing Secrets with Management Point Relays
TL;DR Network Access Account, Task Sequence, and Collection Settings policies can be recovered from SCCM by...