Getting the Most Value Out of the OSCP: After the Exam
Jun 2 2025
By: Kieran Croucher • 20 min read
TL;DR In the final post of this series, I’ll discuss what to do after your latest exam attempt to get the most value out of your OSCP journey.
DISCLAIMER:
All opinions expressed in this article are solely my own. I have reviewed the content to ensure compliance with OffSec’s copyright policies and agreements. I have not been sponsored or incentivized in any way to recommend or oppose any resources mentioned in this article.
Introduction

Throughout this series, I’ve shared practical advice for PEN-200: Penetration Testing with Kali Linux students seeking to maximize the professional, educational, and financial value of pursuing the Offensive Security Certified Professional (OSCP) certification. So far, I’ve focused on four distinct phases of “the OSCP journey”: 1) pre-enrollment preparation, 2) the course material, 3) the lab networks, and 4) the exam. In this final post, I’ll discuss how students can leverage their most recent exam experience to learn from their mistakes and increase their chances of passing the exam on subsequent attempts. I’ll also share guidance for newly certified OSCP professionals on how to continue their cybersecurity journey with purpose and direction.
Get your OSCP+ certification with PEN-200 | OffSec
PEN-200 is OffSec's foundational pentesting course– learn and practice the latest techniques. Earn your penetration testing certification (OSCP & OSCP+).
www.offsec.com

After the Exam…

“To finish the moment, to find the journey’s end in every step of the road, to live the greatest number of good hours, is wisdom.” — Ralph Waldo Emerson
What you do after each OSCP exam attempt carries both short- and long-term implications for your professional success. Here are the three takeaways from this post:
- Pass or fail, every student should conduct a thorough retrospective of their last exam attempt to determine what went well, where to focus future study efforts, and what productivity sinks to eliminate
- For students still trying to pass the exam, connecting with others can inspire new strategies, uncover useful training resources, and impart valuable insight; certified professionals can also use this network for career support and guidance
- The final piece of advice in this series is simply to reflect on your OSCP journey so far and decide what you want to pursue next, whether that’s further self-guided study, a new certification, or a job transition
Conduct an Exam Attempt Retrospective
After your OSCP exam — whether you passed or not — the most valuable thing you can do is pause and unpack what actually happened. For students still pursuing the certification, the benefit is clear: increasing the odds of passing the next attempt. However, even newly certified professionals can gain valuable insight by identifying areas for improvement or exam-day “bottlenecks” that hindered productivity. In this section, I propose a structured retrospective methodology, defined here as a deliberate and reflective review of your performance with the goal of identifying what worked, what failed, and what to improve. You can think of it as a technical postmortem of your latest exam attempt.

It took me three attempts to pass the OSCP exam. In my first attempt, I performed well on the standalone machine set but struggled with lateral movement and privilege escalation in the Active Directory (AD) set. I assumed my only obstacle was a lack of familiarity with AD attack vectors, so I rewrote my notes for the appropriate PEN-200 modules and practiced more with AD network exercises. Had I conducted an exam retrospective, however, I would have uncovered several other weaknesses in my approach:
- An underdeveloped external reconnaissance methodology
- Poor tradecraft documentation
- Suboptimal time management
My second attempt resulted in an even poorer performance (I exfiltrated only a single flag) despite being better informed on AD internals. Needless to say, I was shocked and profoundly disappointed.

After pulling myself out of that slump, I mulled over my latest attempt and used the lessons I’d learned to perform significantly better on my third and final try. With that success in mind, I revisited my retrospective process and refined it for this blog series. The workflow is illustrated in the swimlane flowchart diagram below:
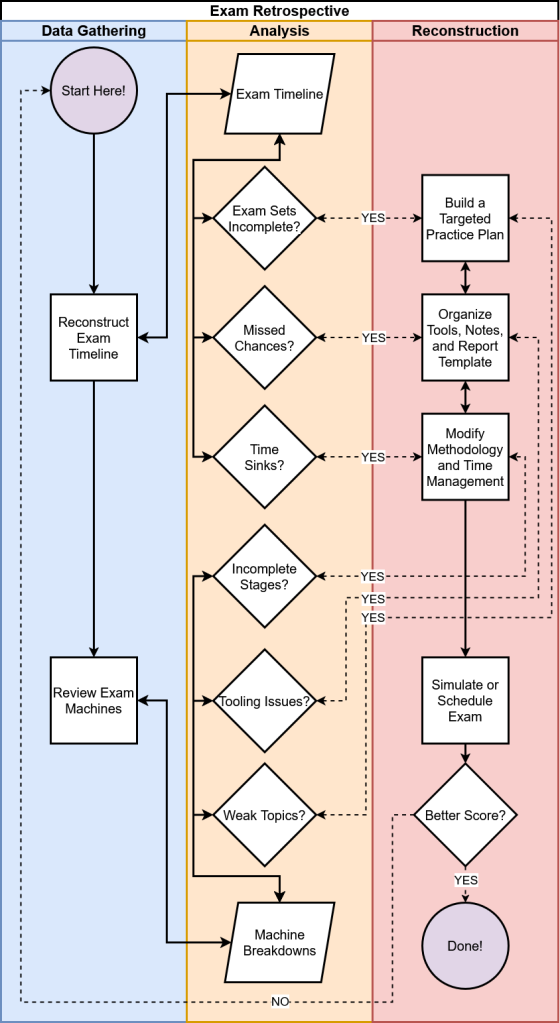
The first, and arguably most important, phase of the exam retrospective is data gathering. The quantity, quality, and accuracy of the data you collect at this stage largely determines the retrospective’s value. By the end of this phase, you should have two core outputs that will inform the next stages of analysis:
- Timeline: Reconstruct your exam attempt as accurately as possible by capturing timestamps of your actions; break down each event by challenge set, machine, attack stage (e.g., reconnaissance, privilege escalation, lateral movement), and report status
- Machine Breakdown: Review your notes to identify the observable technologies on each of the six exam machines; note the services discovered, attacks or procedures attempted, tools used, and where you stopped along each attack path
After completing the data gathering phase, take a two-pronged approach to the analysis phase:
- Identify operational hurdles that ate into your 24-hour testing window and hampered productivity using the exam timeline
- Use the machine breakdowns to identify which technologies, tools, or attack stages hindered your exam performance
The goal in both cases is to enumerate deficiencies you can address later in the reconstruction phase. During reconstruction, you will build on your findings by 1) creating a targeted study plan, 2) reorganizing your notes, reference guides, or report templates, and 3) refining your testing methodology and time management strategy.

Start by analyzing your exam timeline and using your observations to guide improvements in your preparation:
- Did one challenge set (i.e., the AD or independent challenges) take significantly longer than the other or remain incomplete?
This could signal a technical knowledge gap in areas like AD enumeration, Windows/Linux exploitation, or web application testing. If so, adjust your study plan to focus deliberately on these topics before your next attempt. Platforms like Hack The Box (HTB) allow you to filter machines by technology, operating systems (OS), or attack type; making it easier to target weak areas and reinforce essential skills. - Did missing or incomplete notes, fragmented reference guides, or disorganized report templates cause you to lose time?
If you struggled to retrieve commands or documentation under pressure, it’s time to streamline your tradecraft resources. Consolidate your notes, build out your reference guides, and prep your report templates in advance to minimize exam-day friction. - Did you fall into time sinks or go down rabbit holes that led nowhere?
Reflect on how your methodology might have contributed to wasted time. Consider introducing more automation, pruning redundant steps, or adopting a timeboxing approach like the Pomodoro Technique to improve your efficiency.

In the second step of the analysis phase, use the exam machine breakdowns you created earlier to answer the following questions and develop action items:
- Did you fail to exploit or enumerate any technologies or services?
Use these insights to shape a focused study plan. Again, utilize platforms like HTB and prioritize practical training resources to dictate your informed study approach. - Did you discover a vulnerability but fail to exploit it due to tool issues or syntax errors?
Explore alternative tools that better align with your workflow and update your reference guide with accurate syntax and usage examples. Link entries in your reference guide for given exploitation techniques to examples of HTB or OffSec lab machines where you successfully executed those techniques. Aim to maintain at least two tools for each post-exploitation task: one that runs from your Kali Linux box and another that you can execute on a compromised host (e.g., a PowerShell script or .NET assembly). Apply the same principle to external recon tasks. Keeping your toolkit diverse and your notes accurate can save critical time under pressure. - Did specific attack stages (e.g., external reconnaissance, privilege escalation, credential harvesting) not return actionable results or break down?
Revisit and revise your methodology. Resources like HackTricks and Swissky’s cheatsheets can help close knowledge gaps. Add checkboxes or mind maps to your processes for common services (e.g., FTP, SMB, and HTTP) to ensure thorough and repeatable enumeration. Apply the same structured approach to post-exploitation workflows for both Windows and Linux targets. Test your updated methodology against easy-to-medium HTB machines to validate your changes before the next attempt.

By the end of both analyses, you should have a concrete plan to address the weaknesses exposed during the retrospective. If you’re still preparing for the OSCP — or simply want to gauge your progress — allocate time to retest your skills and methodology after completing your action items. If you followed my advice from the third post of this series and haven’t yet completed one of the three PEN-200 lab networks that simulate the exam environment, now’s the time. Treat the lab network as your control environment and your new score as the dependent variable: the measurable outcome of your adjusted approach. Once you’re satisfied with the results, reschedule your next OSCP exam attempt.

By following this approach, PEN-200 students will be better prepared for future OSCP exam attempts and better equipped to continue their self-guided education after earning the certification. This methodology can be applied as an iterative feedback loop across multiple attempts, helping to identify skill gaps and drive continuous improvement. As long as students maintain a positive attitude and a genuine interest in self-discovery, they can expect steady progress in both exam performance and testing confidence.
Network With Industry Professionals and Fellow Students
Throughout the OSCP study process, it’s easy to become hyperfocused and socially isolated. In doing so, students often miss out on one of the PEN-200’s greatest strengths: its expansive network of peers, mentors, and potential professional contacts. Whether you’ve already earned your OSCP or are still working through the exam process, connecting with others can transform the solitary grind of preparation into a collaborative, enriching journey and accelerate your professional aspirations.

As a current PEN-200 student, networking offers opportunities to learn, share, and stay motivated. After I failed my second attempt, I reached out to a friend enrolled in PEN-300: Advanced Evasion Techniques and Breaching Defenses and asked if I could shadow him while we both worked on HTB Pro Labs. During those sessions, we swapped enumeration checklists, shared our favorite tools, and discussed our approaches to exam retrospectives. Other students can benefit from networking by finding accountability partners, joining study groups, discovering new exploitation strategies, and staying emotionally grounded throughout this challenging process.
NOTE:
One of my favorite takeaways from shadowing mock penetration tests was learning how to speed up directory brute-force enumeration on Windows Internet Information Services (IIS) Web Servers. Because Windows hosts are case-insensitive — unlike UNIX-like systems — you can significantly reduce redundancy and improve performance by using tools like gobuster or dirsearch with a wordlist limited to lowercase or uppercase entries. This is just one example of how collaborating with other OffSec students or ethical hackers can inspire new testing strategies and accelerate your learning process.
For newly certified OSCP holders, networking takes on renewed importance. Earning the certification opens doors to job opportunities, interviews, and professional conversations that weren’t accessible before — but you can’t expect to walk through them without making connections first. Talking with people who are deeply embedded in the industry also provides insights that static courses can’t realistically capture like real-time knowledge about evolving roles, industry or specific company expectations, and career path requirements that wax and wane with industry trends. Networking also helps you plan the next phase of your self-guided education — whether that means expanding on PEN-200 concepts, charting your own course by exploring new cybersecurity domains, building a home lab, or other ideas I’ll cover later in the post. Conversations with those who’ve already moved beyond PEN-200 can help you set clear goals, avoid common pitfalls, and stay aligned with the rapidly evolving demands of the offensive security industry.
The most obvious networking platform for PEN-200 students is the official OffSec Discord server, but many other communities are worth exploring:
- Discord Servers: HackTheBox, TryHackMe, Kali Linux & Friends, and DEFCON host active pocket communities of current and former PEN-200 students
- OffSec Office Hours: The OffSec Discord hosts weekly livestreams on Fridays where an instructor walks through an OffSec Proving Grounds machine; these sessions are a great way to stay sharp and engage with other OSCP-hopefuls
- Reddit: The
r/oscpsubreddit focuses specifically on OSCP-related content, though the quality and tone of posts can vary (it is Reddit, after all) - Content Creators: Figures like IppSec, The Cyber Mentor, and Tib3rius regularly produce livestreams and educational material, maintaining active online communities where you can connect with like-minded learners
- LinkedIn: Many OffSec students use LinkedIn to showcase their OSCP certification, share their learning journeys, comment on others’ milestones, and build professional relationships
- In-Person Events: Local meetups such as OWASP Local Chapters, Security BSides events, or regional DEF CON Groups are great places to find a supportive community, sharpen your skills, define a new career path, and potentially meet future travel partners for a trip to the world-famous DEF CON conference in Las Vegas
Discord – Group Chat That’s All Fun & Games
discord.com
Whether you’re newly certified or still grinding to earn the OSCP, don’t neglect the networking opportunities this journey presents. As a current student, sharing tips and hurdles keeps you technically informed and motivated. As a newly minted OSCP, connecting with career mentors and peers reinforces your knowledge and expands your professional circle. By engaging in Discord servers, study group meetups, or LinkedIn discussions, you gain real-time insights, accountability, and a support network that lasts well beyond the exam. No matter where you are in the OSCP journey, investing time in these communities accelerates your learning and lays the groundwork for long-term success in offensive security.
Ask Yourself, “What’s Next?”

I would like to take a moment to personally congratulate everyone reading this who has recently passed the OSCP exam. You’ve likely invested months — if not years — into earning this credential, amassing a solid foundation of experience and knowledge along the way. Ask yourself: What did you enjoy most? What would you prefer to avoid in the future? These reflections can guide your next challenge, the skills you want to sharpen, and your broader career direction. To close out this series, I’d like to explore those possibilities and highlight how they can enhance your professional profile.
First things first: take a break. Seriously. You’ve reached an impressive milestone and while it’s tempting to dive immediately into the next pursuit, give yourself time to rest and decompress. If possible, take a vacation (or at least a few days off) to recover from the intensity of exam prep.

Before deciding what’s next, update your resume to include your OSCP certification and prepare for the job hunt. If you’re entering the cybersecurity job market, I highly recommend the Infosec Job Hunting w/ BanjoCrashland YouTube playlist. It covers everything from finding job postings and writing resumes to networking and interview preparation. Many of the techniques discussed in this series involve open-source intelligence (OSINT) gathering techniques, which can double as skill development for future offensive roles. The creator, Jason Blanchard of Black Hills Information Security, also hosts a weekly Twitch stream, Job Hunt Like a Hacker, which expands on these lessons with real-time advice and feedback. While I haven’t attended the stream personally, at least 278 people (as of this writing) credit Blanchard and his content for helping them successfully pivot into cybersecurity — an endorsement of both his insight and the supportive community he’s fostered.
Many OSCP holders choose to write a public reflection on Medium, LinkedIn, or a personal blog platform. If you do the same, structure it like a retrospective: document what went well, what didn’t, how you studied, and what you would change in hindsight. Avoid spoilers, walkthroughs, or anything that could violate OffSec Terms and Conditions. A well-written reflection not only inspires other PEN-200 students but can also serve as a networking tool, a technical writing sample, and a resume booster. Take your time writing it and ensure it’s something you’re proud to attach your name to.
This whole series has focused on one cybersecurity certification (the OSCP) and briefly mentioned a few others. In spite of that, I recommend caution before making another certification your next professional goal. As I said in the first post of this series, it’s important to view all certifications through a critical lens. The certification industry is, ultimately, a business and students should remain conscious of marketing narratives that inflate their importance or imply that earning one guarantees employment in your field of choice. Rather than chasing credentials to bypass every human resources (HR) filter — a Sisyphean task, in my opinion — focus instead on crafting a narrative of steady, deliberate growth in your ethical hacking journey. That narrative can include certifications, but it could also highlight personal projects, practical experience, and self-guided exploration. In short, learn to wield certifications like a scalpel rather than a claymore while also peppering your journey with cost-effective resume boosters.
For example, many offensive security professionals pursue the Certified Red Team Operator (CRTO) or Offensive Security Experienced Penetration Tester (OSEP) after earning the OSCP. Equally valid (and often more cost-effective) alternatives include climbing the ranks on HTB, developing your own command and control (C2) framework, or participating in bug bounty programs like HackerOne or Bugcrowd. A few strategic acronyms on your resume can open doors, but too many can spell doom for your wallet.

PEN-200 offers valuable lessons, but it’s still an entry-level certification and only scratches the surface of many cybersecurity topics. If you want to build on its concepts at a higher level, consider the following:
- Web Applications
While PEN-200 introduces core techniques like SQL injection (SQLi) and cross-site scripting (XSS), the web app security field itself spans hundreds of server-side and client-side vectors, subtle edge cases, and novel exploitation methods that researchers are constantly discovering. PortSwigger Academy is my favorite free platform for advancing these skills, as it offers comprehensive written material and interactive labs. - AD Attack Vectors
AD represents a massive attack surface and the PEN-200 therefore covers only the fundamentals while omitting topics like Kerberos delegation, Active Directory Certificate Services (ADCS), and Microsoft Configuration Manager (MCM/SCCM). Use BloodHound Community Edition as both an addition to your toolkit and a knowledge base for improving AD tradecraft. - Reporting
As mentioned in the third post of this series, technical reporting may be the most transferable skill from the PEN-200 into real-world engagements. Refer back to the included resources in that article and set time aside to improve this area. - Red Teaming
While red teaming overlaps significantly with penetration testing, it emphasizes different skills such as persistence, command and control, and exfiltration. Explore techniques relative to these domains and learn how to adapt each PEN-200 post-exploitation technique to blend with legitimate network traffic, enhancing stealth.
NOTE:
The differences between penetration testing and red teaming are often subtle and vary between organizations. Understanding these nuances is crucial when entering the job market, as mismatched expectations can hinder a successful career pivot. My favorite explanation comes from JUMPSEC, which notes that penetration testing aims to uncover as many flaws as possible, while red teaming focuses on achieving specific objectives to demonstrate real-world impact. Red teaming also places greater emphasis on operational security (OPSEC) evasion and threat actor emulation.
There are even more offensive security topics not covered in PEN-200 that may interest you:
- Cloud Security
Just as pervasive as web applications, cloud platforms — such as Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure — present huge attack surfaces. HackTricks Training is a relatively new but solid starting point for offensive cloud security training. - Wireless Security
While access to PEN-210: Foundational Wireless Network Attacks and an OffSec Wireless Professional (OSWP) exam voucher are available to OffSec Learn One subscribers, you might try the free WiFiChallenge Lab first before enrolling in another certification program. - Malware & Payload Development
Maldev Academy and SEKTOR7 Institute come highly recommended throughout the industry. The skills these courses help you develop are essential to advanced post-exploitation, red teaming, and custom implant engineering. - Other Domains
Other common domains are mobile devices and applications, industrial control systems (ICS), Internet of Things (IoT) devices, large language model (LLM) web applications, social engineering, and physical access control systems (PACS).

I wrote this series for PEN-200 students whose goal is to pivot into the offensive security consulting industry; however, that is only one demographic of the PEN-200 student body. Many students pursuing the OSCP are considering (or already employed in) fields tangential to penetration testing and red teaming. If you’re more aligned with adjacent fields like reverse engineering, development, security, and operations (DevSecOps), security operations center (SOC), or detection engineering, there are valuable resources for those too:
- Reverse Engineering & Malware Analysis
Try Malware Unicorn’s Reverse Engineering 101 or HackerSploit’s Malware Analysis Bootcamp for free, the latter of which concludes with case studies of artifacts from the 2018 Flare-On Challenge capture the flag (CTF) event and the cyberweapon Stuxnet (used during the sabotage campaign of Iranian nuclear enrichment facilities known as Operation Olympic Games). - DevSecOps
I highly recommend the corporate training program Secure Code Warrior or the more affordable Hacksplaining platform for individuals looking to improve their secure development skills. - SOC
SOC analysts are often on the front lines of incident detection and response. Utilize online training platforms like CyberDefenders or TryHackMe, both of which offer learning paths for SOC levels 1–3. Radiant Security has a helpful explanation of the differences between these tiers. - Detection Engineering
Now that you understand how many fundamental attacks work, flip the perspective by learning how to detect malicious behavior, craft alerts, and better understand attacker tradecraft. Budget-conscious learners can start with Practical Threat Detection Engineering from packt and its accompanying code repository, while Applied Network Defense offers a well-regarded catalog for those seeking deeper coverage. - Other Domains
Other common domains are digital forensics and incident response (DFIR), governance, risk, and compliance (GRC), and threat intelligence gathering (AKA threat hunting).
NOTE:
As with all commercial training options, consider whether the return on investment (ROI) justifies enrollment.
Lastly, consider how you might participate in or give back to the information security community. If you live in or near a city, look for volunteer opportunities as a technical coach for underrepresented communities (e.g., older citizens, non-native English speakers, or individuals with physical or cognitive disabilities) or as a volunteer network engineer for nonprofit organizations. Consider volunteering at a local public school to talk about careers in cybersecurity and what drew you to ethical hacking. Many diversity-focused nonprofit organizations and affinity groups in cybersecurity offer valuable resources like career mentorship, CTF events, digital privacy training, and financial sponsorship for professional development. Notable examples include Women in Cybersecurity (WiCyS), Blacks in Cybersecurity (BIC), Latinas in Cyber (LAIC), Secure Diversity, and Minorities in Cybersecurity (MiC). Getting involved with these groups can expand your network, strengthen your resume, and allow you to give back to the community in meaningful ways.
Earning the OSCP is an extraordinary accomplishment, but it’s just one checkpoint in a much longer and more worthwhile journey. Whether you continue with more certifications, lab projects, or community involvement, remember to stay curious, humble, and ethical. Make your next steps intentional, and remember: as with the OSCP, the process itself should be as rewarding as the prize.
Conclusion

It’s been a privilege to write this series and I’m grateful to my colleagues and friends for their valuable feedback and ongoing support. As always, I welcome your questions, constructive critiques, or additional advice for current and future PEN-200 students in the comments.
Getting the Most Value Out of the OSCP: After the Exam was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.