blog category
BloodHound

BloodHound
LudusHound: Raising BloodHound Attack Paths to Life
TL;DR LudusHound is a tool for red and blue teams that transforms BloodHound data into a...
By: Beyviel David
Jul 14, 2025 • 7 min read
Read Post
BloodHound
Privilege Zones: BloodHound Enterprise spreading like a computer virus (of security)
TL;DR The BloodHound Enterprise team recently pushed out Privilege Zones, one of the most requested features...
By: Irshad Ajmal Ahmed
Jul 8, 2025 • 5 min read
Read Post
BloodHound
Good Fences Make Good Neighbors: New AD Trusts Attack Paths in BloodHound
TL;DR The ability of an attacker controlling one domain to compromise another through an Active Directory...
By: Jonas Bülow Knudsen
Jun 25, 2025 • 24 min read
Read Post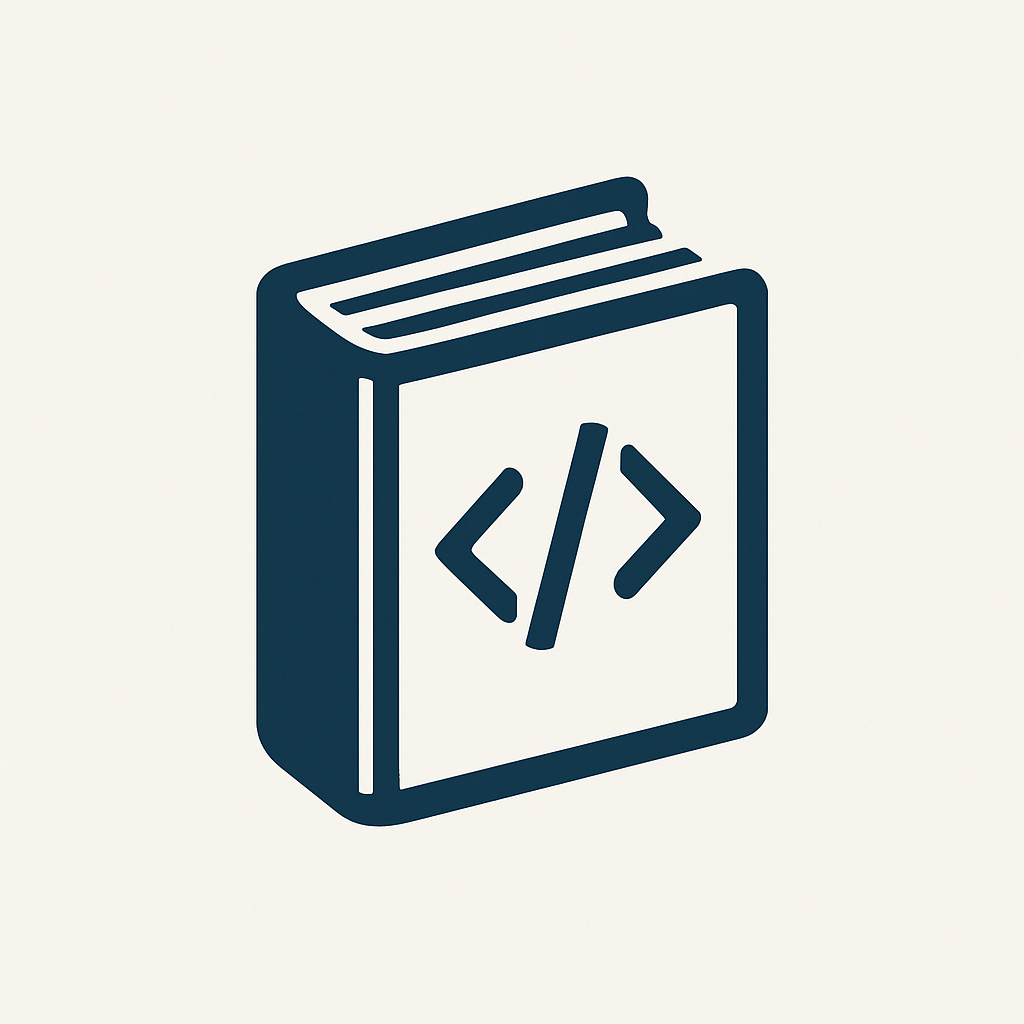
BloodHound
Introducing the BloodHound Query Library
TL;DR The BloodHound Query Library is a community-driven collection of Cypher queries designed to help BloodHound...
By: Martin Sohn Christensen, Joey Dreijer
Jun 17, 2025 • 6 min read
Read Post
BloodHound
Making Least Privilege Real: Previewing Privilege Zones in BloodHound Enterprise
TL;DR Most organizations assume they’ve implemented least privilege, but assumptions don’t stop attackers. Privilege Zones in...
By: Justin Kohler
Jun 16, 2025 • 8 min read
Read Post
BloodHound
Chatting with Your Attack Paths: An MCP for BloodHound
TL;DR In an effort to learn about Model Context Protocol servers, I created a MCP server...
By: Matthew Nickerson
Jun 4, 2025 • 22 min read
Read Post
BloodHound
(Why) IAM demands an #AttackGraph First Approach
TL;DR: Don’t start with access lists, start with attacker movement. Your new baseline: “Be the best...
By: Kay Daskalakis
May 27, 2025 • 23 min read
Read Post
BloodHound
The Renaissance of NTLM Relay Attacks: Everything You Need to Know
NTLM relay attacks have been around for a long time. While many security practitioners think NTLM...
By: Elad Shamir
Apr 8, 2025 • 40 min read
Read Post
BloodHound
Fueling the Fight Against Identity Attacks
When we founded SpecterOps, one of our core principles was to build a company which brought...