blog category
BloodHound

BloodHound
Fueling the Fight Against Identity Attacks
When we founded SpecterOps, one of our core principles was to build a company which brought...
By: David McGuire
Mar 5, 2025 • 4 min read
Read Post
BloodHound
Enhancements for BloodHound v7.0 Provide Fresh User Experience and Attack Path Risk Optimizations
TL;DR: Refreshed user interface with a new vertical navigation layout for improved user experience. General Availability...
By: Dev Bhatt
Feb 11, 2025 • 6 min read
Read Post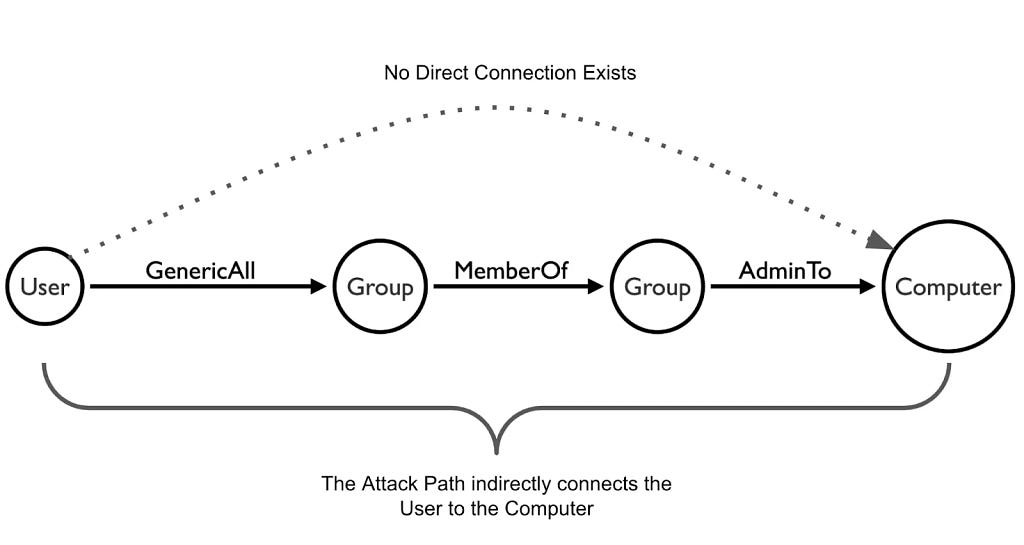
BloodHound
Insurance companies can reduce risk with Attack Path Management
TL;DR Insurance companies host large amounts of sensitive data (PII, PHI, etc.) and often have complex...
By: Kirsten Gibson
Jan 23, 2025 • 4 min read
Read Post
BloodHound
We created a new tool to help you install and manage BloodHound instances, BloodHound CLI! GitHub...
By: Christopher Maddalena
Jan 17, 2025 • 3 min read
Read Post
BloodHound
Intune Attack Paths — Part 1 Prior Work Several people have recently produced high-quality work around Intune tradecraft. I...
By: Andy Robbins
Jan 15, 2025 • 21 min read
Read Post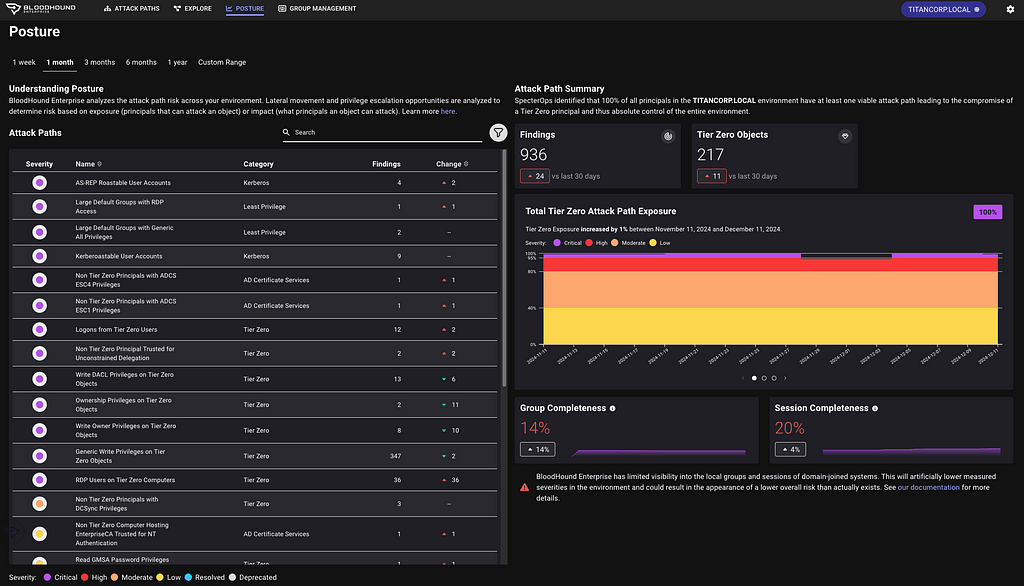
BloodHound
Unwrapping BloodHound v6.3 with Impact Analysis
Just in time for the holidays, sharper tools for faster defense Today, the SpecterOps team rolled out...
By: Justin Kohler
Dec 12, 2024 • 6 min read
Read Post
BloodHound
FedRAMP High Authorization for BloodHound Enterprise is a Critical Win for the Public Sector
Author: David McGuire, CEO, SpecterOps Today, we’re thrilled to announce that SpecterOps has earned FedRAMP High...
By: David McGuire
Dec 5, 2024 • 3 min read
Read Post
BloodHound
TL;DR: BOFHound can now parse Active Directory Certificate Services (AD CS) objects, manually queried from LDAP,...
By: Matt Creel
Oct 30, 2024 • 14 min read
Read Post
BloodHound
Closing the Gaps: How Attack Path Management Improves Vulnerability Management Programs
In conversation: Pete McKernan & Luke Luckett As organizations seek to wrap their arms around potential cybersecurity...