blog category
BloodHound
BloodHound
BloodHound Operator — Dog Whispering Reloaded
BloodHound Operator — Dog Whispering Reloaded It’s summer 2024 and we are back! Actually, we are SO back,...
By: JD Crandell
Aug 6, 2024 • 20 min read
Read PostBloodHound
Hybrid Attack Paths, New Views and your favorite dog learns an old trick
Introducing Hybrid Attack Paths Death from Above: An Attack Path from Azure to Active Directory With BloodHound...
By: Justin Kohler
Aug 2, 2024 • 6 min read
Read Post
BloodHound
Mapping Snowflake’s Access Landscape
Attack Path Management Because Every Snowflake (Graph) is Unique Introduction On June 2nd, 2024, Snowflake released a...
By: Jared Atkinson
Jun 13, 2024 • 28 min read
Read Post
BloodHound
ADCS Attack Paths in BloodHound — Part 2
ADCS Attack Paths in BloodHound — Part 2 In Part 1 of this series, we explained how we incorporated...
By: Jonas Bülow Knudsen
May 1, 2024 • 13 min read
Read Post
BloodHound
Final Steps to BloodHound Enterprise for Government— FedRAMP High Compliance
Final Steps to BloodHound Enterprise for Government— FedRAMP High Compliance Ever since SpecterOps first launched BloodHound Enterprise...
By: Justin Kohler
Mar 5, 2024 • 3 min read
Read Post
BloodHound
The altSecurityIdentities attribute of Active Directory (AD) computers and users allows you to specify explicit certificate...
By: Jonas Bülow Knudsen
Feb 28, 2024 • 38 min read
Read Post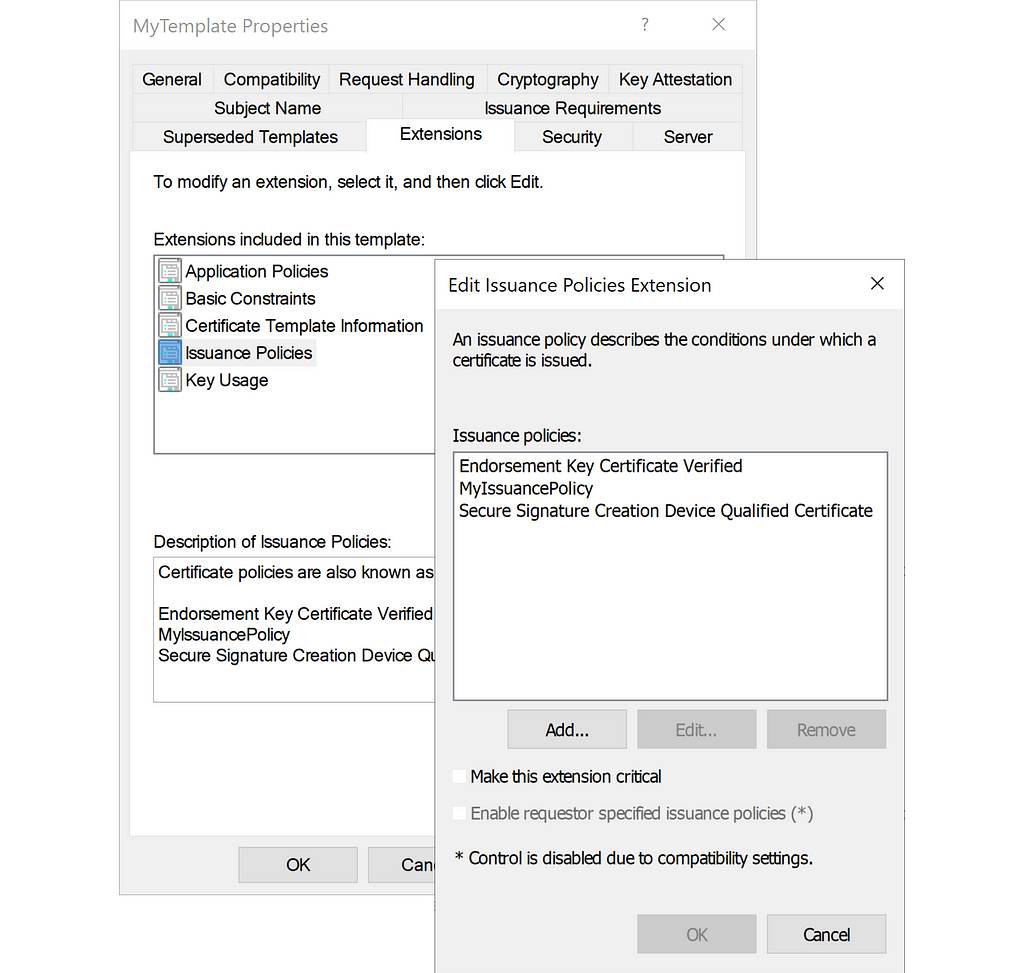
BloodHound
It is possible to configure an Active Directory Certificate Services (ADCS) certificate template with an issuance...
By: Jonas Bülow Knudsen
Feb 14, 2024 • 15 min read
Read Post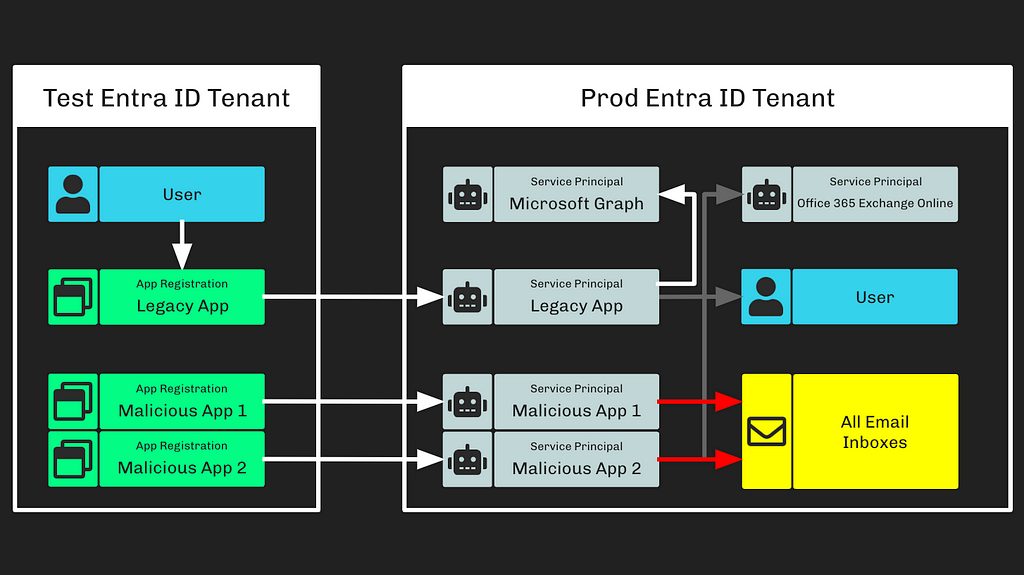
BloodHound
Microsoft Breach — How Can I See This In BloodHound?
Microsoft Breach — How Can I See This In BloodHound? Summary On January 25, 2024, Microsoft announced Russia’s...
By: Stephen Hinck
Feb 2, 2024 • 7 min read
Read Post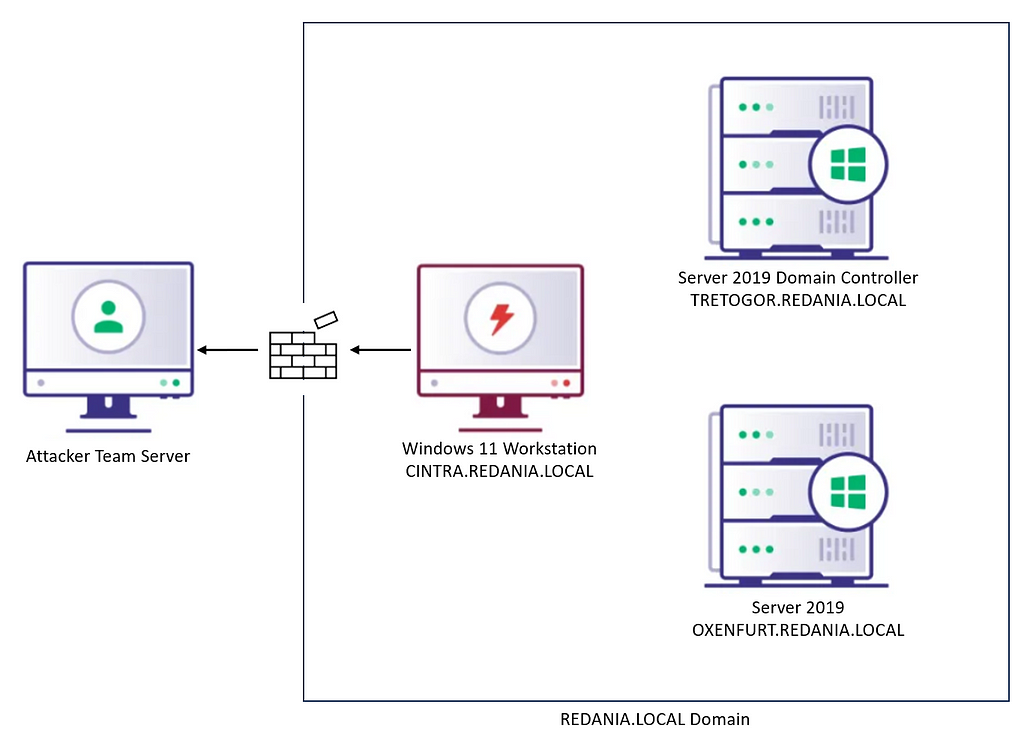
BloodHound
Background If you’ve found yourself on a red team assessment without SharpHound (maybe due to OPSEC...