May 23 2023 |
FOSS BloodHound 4.3.1 release
We are excited to share the release of BloodHound version 4.3.1. We have accepted a lot of pull requests made by BloodHound users for bug fixes and cool improvements in this release. We are super grateful for the continued support and contributions from our dedicated community. Together, we are making BloodHound a better tool.
Let’s jump into what’s new.
New features
The most prominent new features are:
- New edge: DumpSMSAPassword
- Linux abuse info in the help menu
New edge: DumpSMSAPassword
Simon Décosse recently published a great research blog post on Standalone Managed Service Accounts (sMSA). Simon explains how an adversary with local admin access to an AD-joined computer can dump the cleartext password from LSA secrets of any sMSAs installed on this computer. This allows the adversary to authenticate to AD as the sMSA account and abuse the privileges of the service account.
Simon further explains how to collect the necessary data for this attack narrative by reading the msDS-HostServiceAccount LDAP attribute of computers, which contains the Distinguished Names of the sMSAs installed on that computer.
Simon created a pull request for BloodHound and SharpHound (and SharpHoundCommon) which enables BloodHound to create a new edge covering this attack narrative. SharpHound will now collect the msDS-HostServiceAccount attributes of AD computer objects and create DumpSMSAPassword edges to the installed sMSAs.
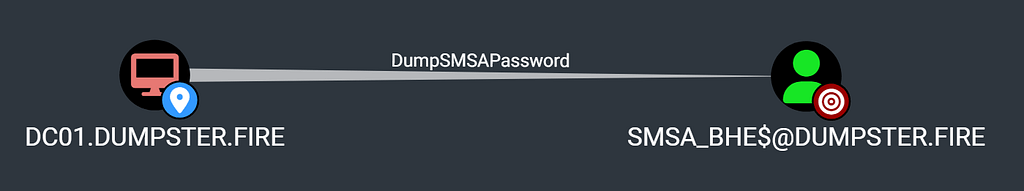
Awesome work, Simon, and thanks a lot for your contribution!
Linux abuse info in the help menu
We included a huge pull request from Charlie Bromberg (Shutdown) in 4.3.1 that introduce a ‘Linux Abuse’ tab in the help text for on-prem AD edges:
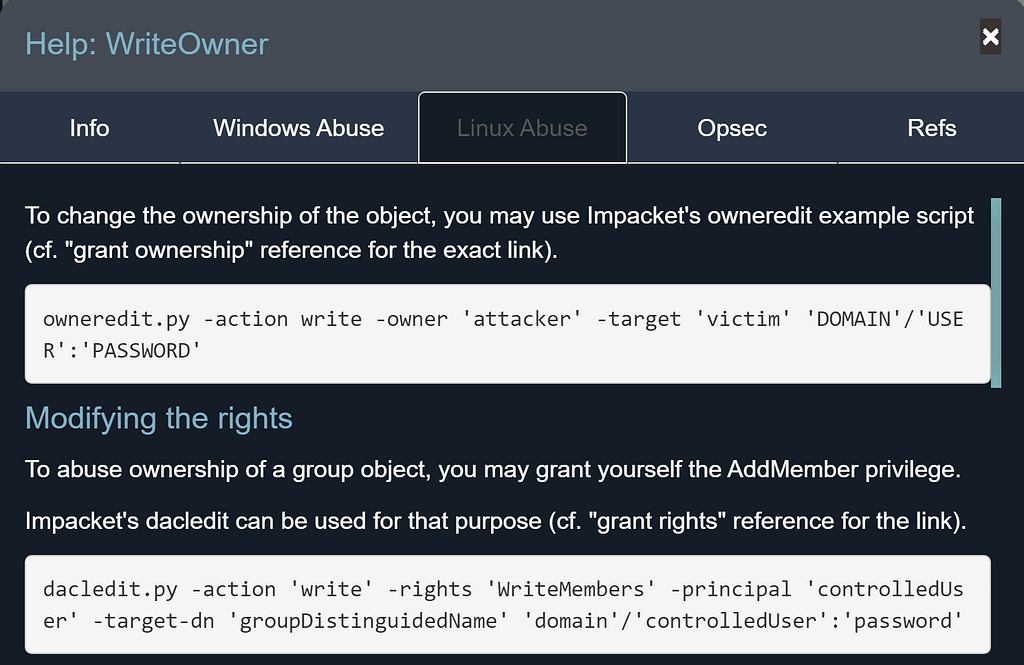
The Windows abuse tab and the Linux abuse tab will describe the same attack narrative but contain different details of how the attack can be executed on Windows and Linux respectively. Only Windows instructions were available before this pull request.
Having this information at hand when using BloodHound will be super helpful. Thanks a lot, Charlie, we value all the time and effort you have put into this!
Bug fixes
Several smaller bugs have been fixed. The most prominent ones are listed here:
- Trust edges are now being generated again
- BloodHound will no longer crash with a white screen when clicking on the help text for certain edges
- BloodHound will no longer create AdminTo edges to gMSAs and sMSAs
- All edges are now switched to ‘on’ in the pathfinding edge filter by default
Improved installation instructions
We have accepted quite a lot of pull requests for updates to the installation docs. This should make it easier to get BloodHound up and running. Thanks to all of you that have helped point out missing information or cmdlets not working. Special thanks to Daniel Scheidt (ADCluemmelSec) for creating a Windows Installation Walkthrough and Troubleshooting video which is now included in the docs.
Final words
Thanks to everyone that contributed to this release. We value every commit — from minor changes to large improvements.
You can download BloodHound v4.3.1 and see the entire list of changes and contributors here: https://github.com/BloodHoundAD/BloodHound/releases/tag/v4.3.1
The new DumpSMSAPassword edge and some of the bug fixes require that you use the latest SharpHound collector (v1.1.1) that can be downloaded here: https://github.com/BloodHoundAD/BloodHound/tree/master/Collectors
FOSS BloodHound 4.3.1 release was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.