blog category
Research & Tradecraft

Research & Tradecraft
One Phish Two Phish, Red Teams Spew Phish
PHISHING SCHOOL How to Give your Phishing Domains a Reputation Boost “Armed with the foreknowledge of...
By: Forrest Kasler
Jun 4, 2024 • 20 min read
Read Post
Research & Tradecraft
Part 13: Why a Single Test Case is Insufficient
By: Jared Atkinson
May 31, 2024 • 24 min read
Read Post
Research & Tradecraft
Increasing our understanding of EDR capabilities in the face of impossible odds. Introduction I recently had...
By: Luke Paine
May 30, 2024 • 12 min read
Read Post
Research & Tradecraft
Behavior vs. Execution Modality
On Detection: Tactical to Functional Part 12 Introduction At Shmoocon 2015, Will Schroeder (Harmj0y) gave a...
By: Jared Atkinson
May 21, 2024 • 20 min read
Read Post
Research & Tradecraft
Part 12: Behavior vs. Execution Modality
By: Jared Atkinson
May 21, 2024 • 20 min read
Read Post
Research & Tradecraft
This post is a follow-up to my previous post on manual LDAP querying. I would highly...
By: Hope Walker
May 2, 2024 • 20 min read
Read Post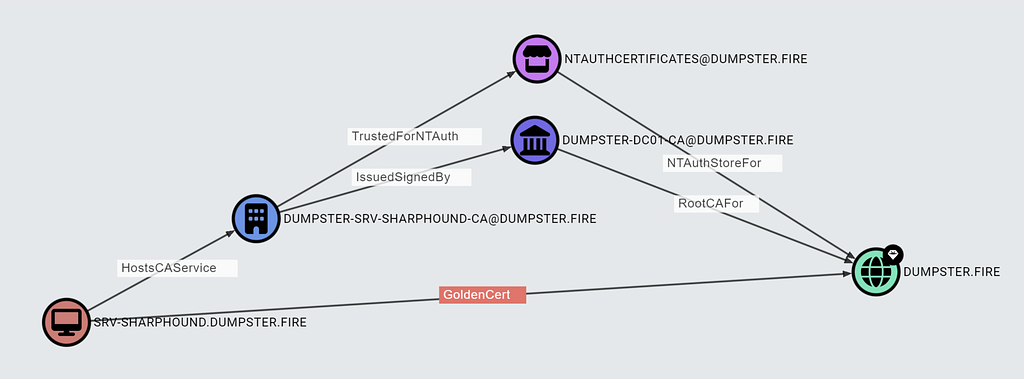
Research & Tradecraft
ADCS Attack Paths in BloodHound — Part 2
ADCS Attack Paths in BloodHound — Part 2 In Part 1 of this series, we explained how we incorporated...
By: Jonas Bülow Knudsen
May 1, 2024 • 13 min read
Read Post
Research & Tradecraft
In August of last year, @tifkin_, @0xdab0, and I released Nemesis, our offensive data enrichment platform....
By: Will Schroeder
Apr 25, 2024 • 10 min read
Read Post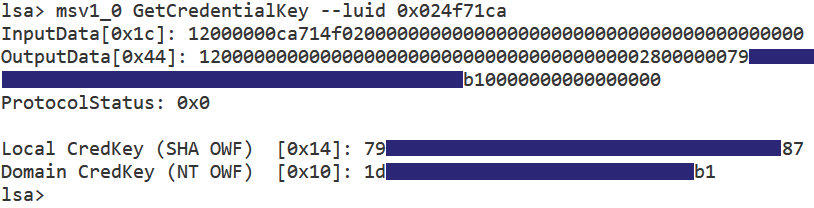
Research & Tradecraft
Thank you to SpecterOps for supporting this research, to Elad for helping draft this blog, and...