blog category
Research & Tradecraft
Research & Tradecraft
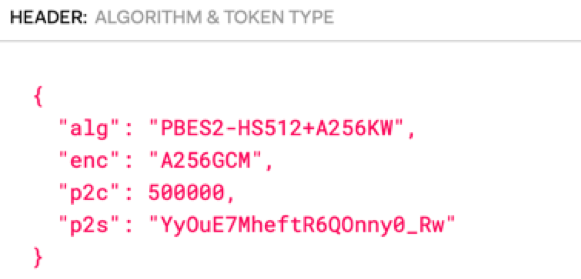
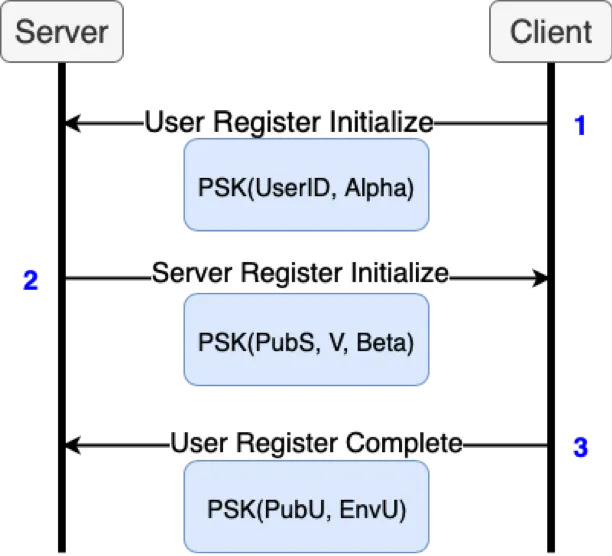
Merlin Goes OPAQUE for Key Exchange
By: Russel Van Tuyl
Aug 20, 2019 • 15 min read
Read Post
Research & Tradecraft
Covenant: The Usability Update
By: Ryan Cobb
Aug 2, 2019 • 10 min read
Read Post
Research & Tradecraft
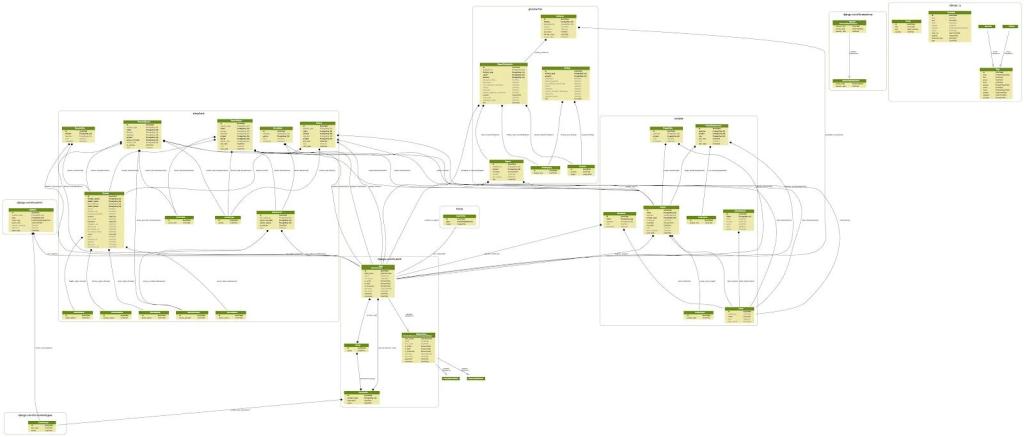
Introducing Ghostwriter: Part 2
By: Christopher Maddalena
Jul 30, 2019 • 10 min read
Read Post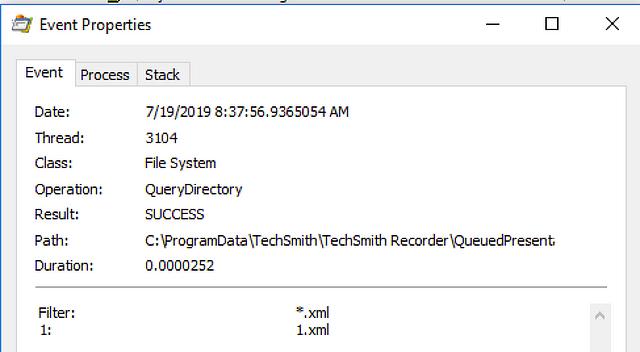
Research & Tradecraft
CVE-2019–13382: Local Privilege Escalation in SnagIt
By: Matt Nelson
Jul 24, 2019 • 9 min read
Read Post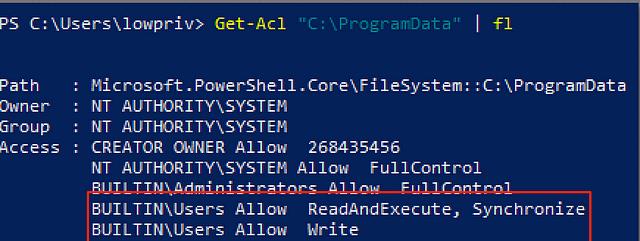
Research & Tradecraft
CVE-2019–13142: Razer Surround 1.1.63.0 EoP
By: Matt Nelson
Jul 5, 2019 • 5 min read
Read Post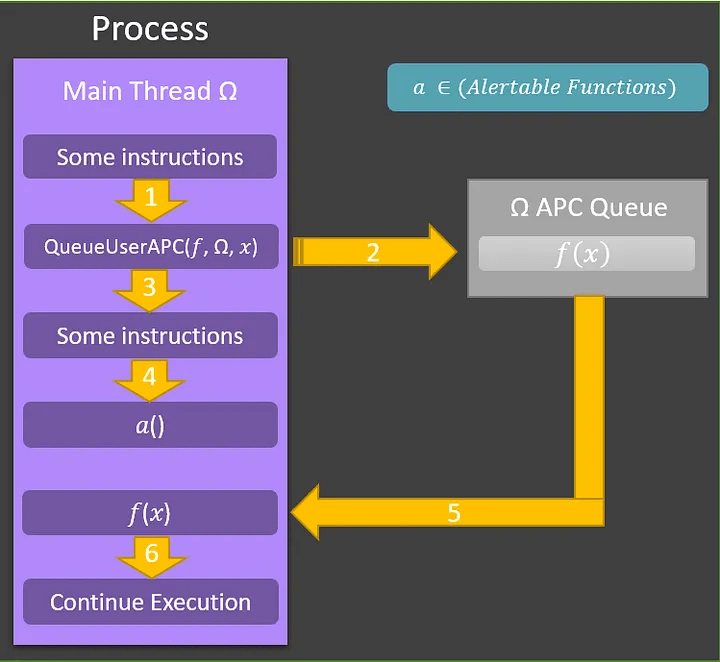
Research & Tradecraft
The Curious Case of QueueUserAPC
Summary Due to the nature of the .NET compiled language runtime, user asynchronous procedure calls (APCs)...
By: Dwight Hohnstein
Jul 1, 2019 • 9 min read
Read Post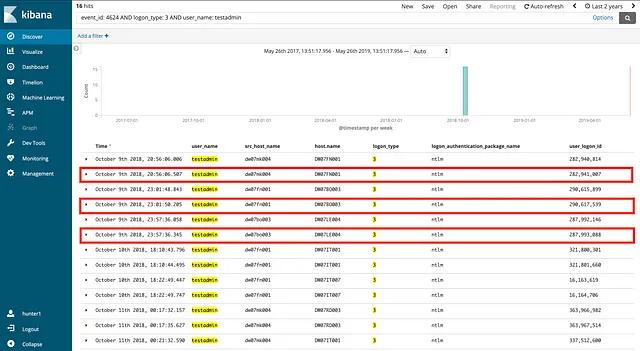
Research & Tradecraft
Diving into the Security Analyst’s Mind