BloodHound Scentry
Expertise to accelerate your Attack Path Management practice.
Built on years of adversary tradecraft and real-world experience protecting Fortune 100 organizations, Scentry helps your team identify, prioritize, and remove high-impact identity attack paths—reducing risk from misconfigurations, excessive privileges, and unintended attack paths. You’ll protect critical assets through Privilege Zones and follow a clear, repeatable program with defined deliverables and measurable progress.
BloodHound Scentry
Expertise to mature your Identity
Attack Path Management
Many breaches today begin with valid credentials—not novel malware—making identity attack paths one of the most common routes to critical systems and sensitive data.
BloodHound Scentry helps you rapidly build, scale, and mature your Identity Attack Path Management practice. Advance from tactical remediation to strategic risk reduction with expert guidance and optimized processes that integrate into your existing security operations.

Founder of Mandiant Security
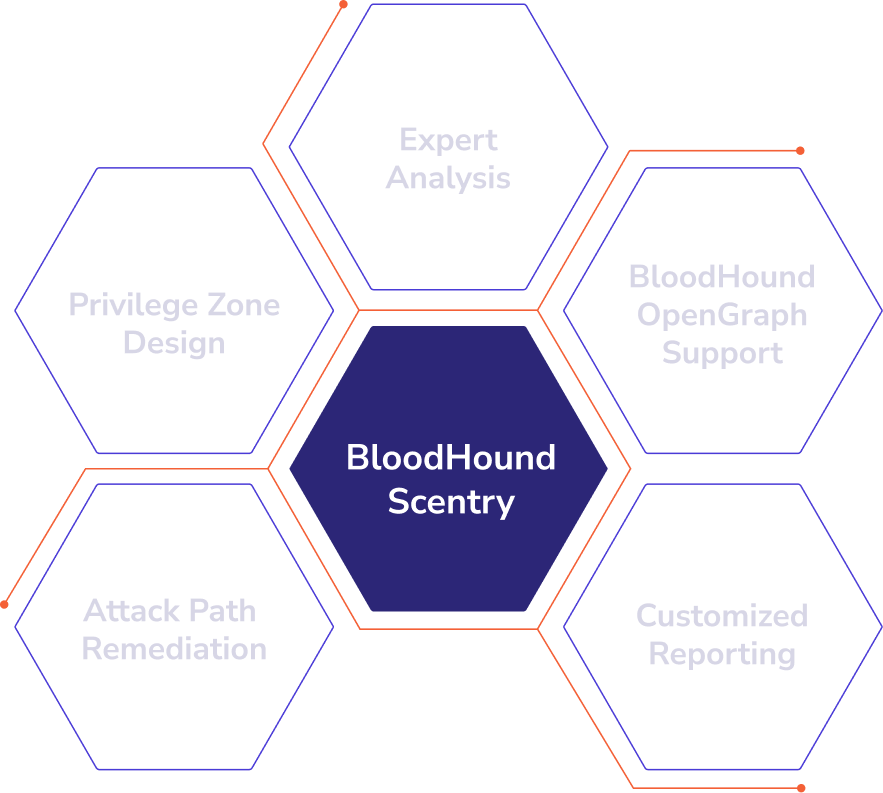
What you get with BloodHound Scentry
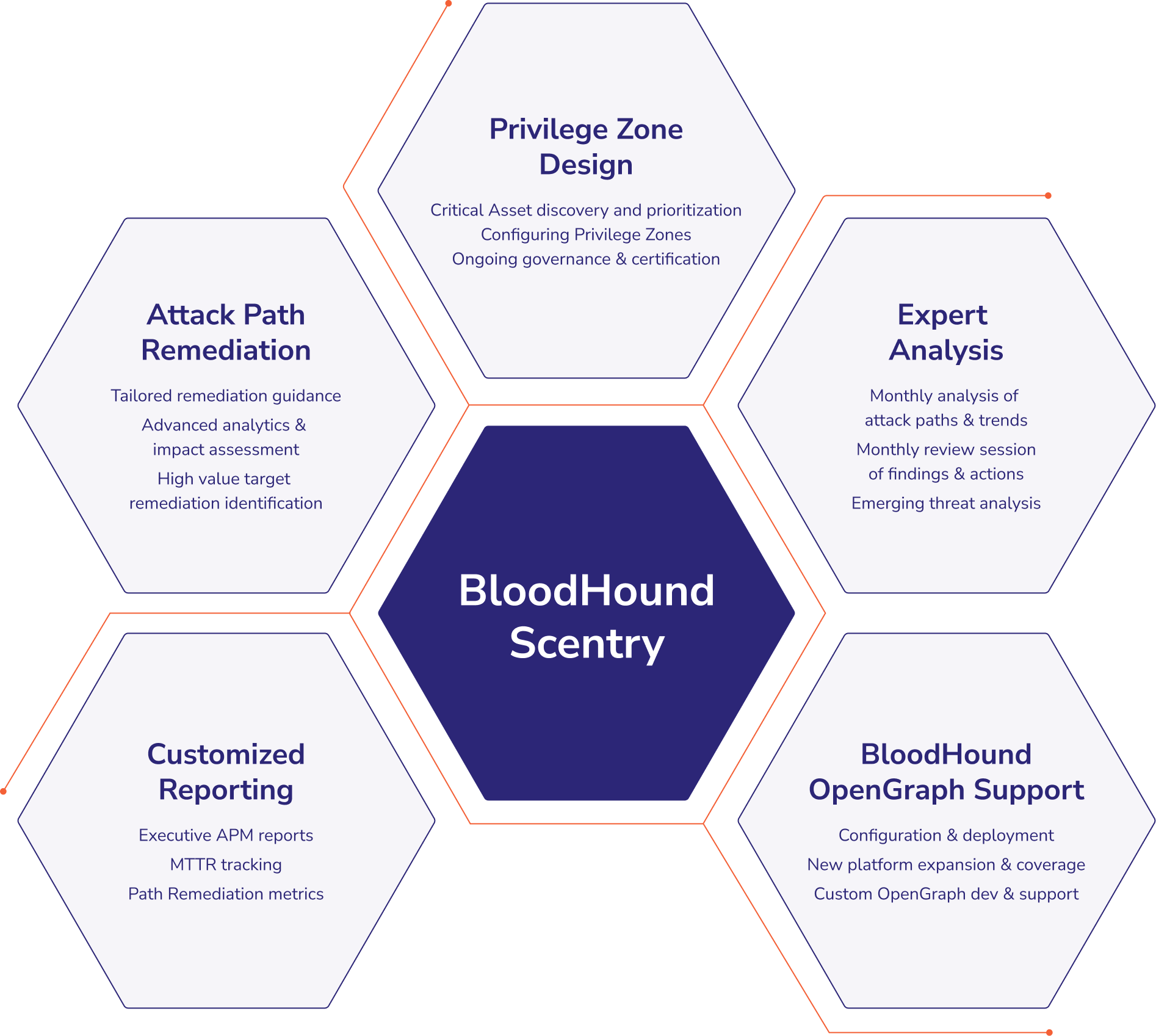
Attack Path Remediation
Every environment has unique requirements, constraints, and technical debt. Scentry experts assess your identity environment (including Active Directory and Entra ID), identify high-impact attack paths and priority actions, and deliver tailored remediation guidance aligned to your identity model—reducing risk from misconfigurations, excessive privileges, and unintended access paths.


Privilege Zone Design
BloodHound Enterprise lets you create Privilege Zones around your most critical assets. Scentry experts identify and prioritize high-value identity assets, configure effective Privilege Zones and access boundaries, and track ongoing governance, certification, and control effectiveness over time.
Expert Analysis
Scentry experts provide monthly analysis of identity attack paths, trends, and key risk drivers across your environment. We share clear findings, prioritized recommendations, and practical next steps, and investigate emerging threats and adversary techniques when your organization or industry faces elevated identity risk.

BloodHound OpenGraph Support
BloodHound OpenGraph expands attack path coverage across any platform, repository, or application—including hybrid identity systems and custom applications. Scentry experts help you design, build, and validate OpenGraph extensions to meet your coverage requirements and continuously map new identity relationships, privileges, and attack paths as your environment changes.
Customized Reporting
Scentry tracks the progress of your Identity Attack Path Management (APM) practice with tailored reporting, including identity hygiene reports and quarterly executive packages. These reports connect attack path remediation and privilege zone adoption to measurable improvements in identity security posture, operational risk reduction, and business outcomes.

Why BloodHound Scentry for Identity Attack
Path Management (APM)?
Establish workflows to review, prioritize, and track attack paths using BloodHound Enterprise and OpenGraph data
Coordinate remediation across Security, Identity/IAM, and IT with clear ownership and accountability
Identify critical assets, implement Privilege Zones, and reduce privilege escalation and lateral movement risk
Set risk-aligned SLAs and measure progress with consistent metrics and reporting rhythms
Communicate remediation outcomes to stakeholders and leadership in business-relevant terms
The difference between knowing what to fix and consistently reducing attack path risk is where BloodHound Scentry bridges the gap—
combining SpecterOps expertise with BloodHound Enterprise to accelerate maturity and expand protection for critical assets.
For additional details, use cases and outcomes, check out the BloodHound Scentry data sheet.
Watch the On-Demand Scentry Webinar
In this session, learn how BloodHound Scentry supports teams through expert guidance and extended capacity, including white glove implementation, Privilege Zone configuration support, ongoing graph analysis and monitoring for emerging threats, tailored remediation planning, and structured reporting rhythms.