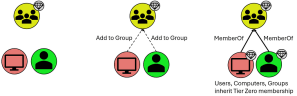
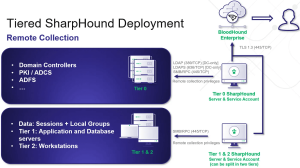
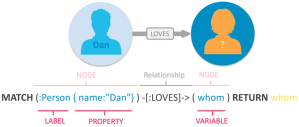
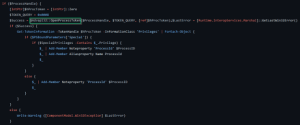
Nathan Davis
Nathan Davis is a Senior Technical Account Manager at SpecterOps. He specializes in helping clients integrate BloodHound Enterprise within their organizations. He can also be found answering questions for the BloodHound community on Slack.
See the latest by Nathan Davis