Jan 27 2022 |
3 Foundational Pillars for Attack Path Management: Pillar 2 — Empirical Impact Assessment
3 Foundational Pillars for Attack Path Management: Pillar 2 — Empirical Impact Assessment
Attack Paths are the chains of abusable privileges and user behaviors that create direct and indirect connections between Active Directory Users and Computers. The unintended consequence of these misconfigurations enables low-privilege users to reach high-value targets and are used by Ransomware. Others have detailed this as well, including this recent post from 451 Research’s blog on identity and access security. To address these consequences, enterprises need an empirical impact assessment of each Attack Path to systematically prioritize their resources for remediation and reduce their exposure.
In part one of this three-part series on the Attack Path Management Pillars, we explained how organizations can remove the risk of thousands of misconfigurations by focusing on Attack Path choke points. Specifically, we discussed mapping misconfigurations to high-value targets, identifying strategic choke points, and providing real-world remediation guidance.
In part two of this series, we address the need to empirically assess any given identity-based Attack Path’s impact on an organization. Doing so allows enterprises to prioritize their mitigation efforts and measure their overall exposure to the most prevalent tactics available for attackers to take control of an organization’s network.
BloodHound Enterprise: Empirical Impact Assessment of Attack Path choke points
Historically, Active Directory (AD) security solutions will point to a particular configuration and offer a subjective risk assessment of that specific configuration / misconfiguration. Unfortunately, the subjective ‘risk’ associated with these misconfiguration fails to consider the access or exposure it opens to an attacker. Consider this hypothetical scenario:
Imagine a Help Desk user, Riley, who created a server in the environment. Later, this server is promoted to a Domain Controller, meaning that Riley has ownership rights over a Domain Controller and can now access a high-value asset in the environment. You may initially view this risk as relatively small (a single user can escalate to a critical asset).
Not ideal but seemingly low risk on its own:

However, how many other users have a path to control Riley’s account? Well, everyone else in the Help Desk (and the SysAdmin team) can change Riley’s password:
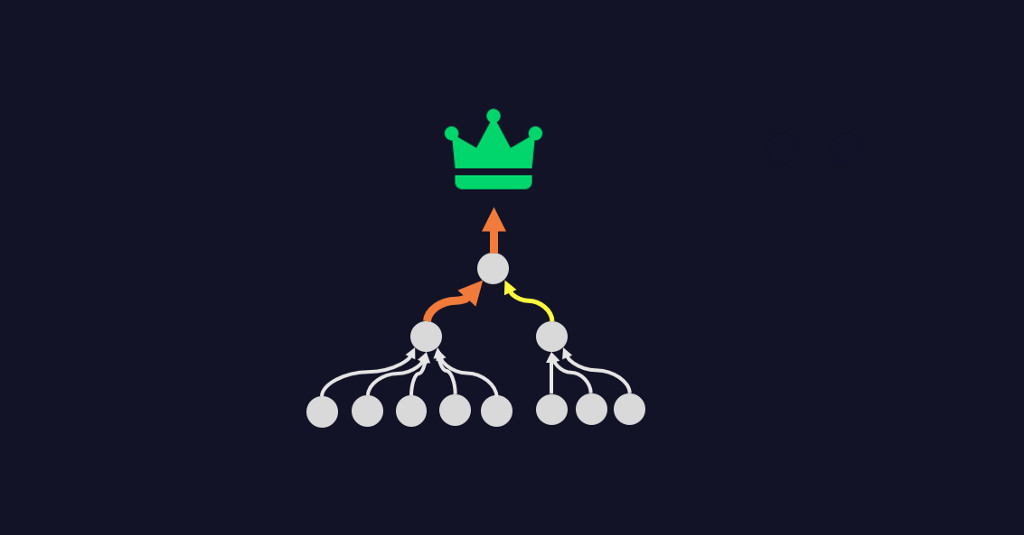
Additionally, yesterday Riley used a script to deploy some new software to every workstation in the enterprise. That script used Riley’s credentials to conduct an interactive logon for every software install:
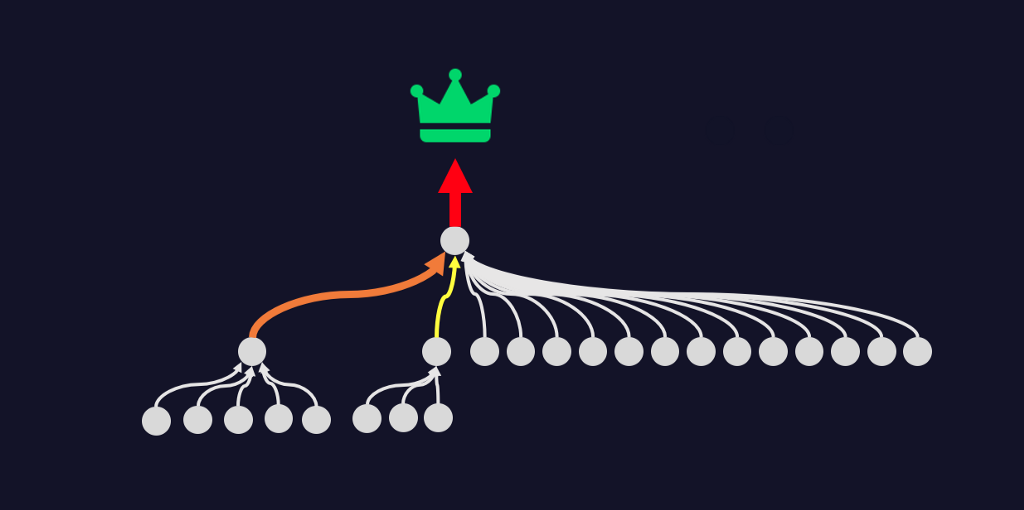
Suddenly, what originally looked like a path from a single user to a high-value asset, is actually a path from most of the organization to full control of the domain. Focusing on the severity of the single misconfiguration dramatically understates the risk created by this issue.
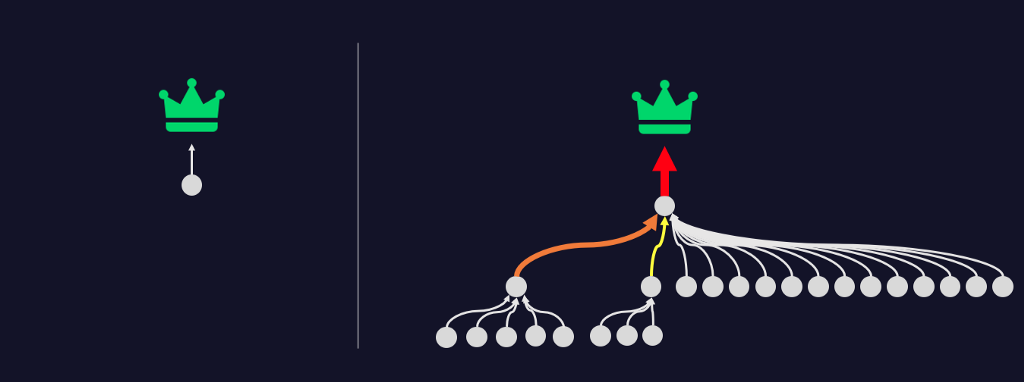
Alternatively, Attack Path Management (APM) solutions like BloodHound Enterprise prioritize based on the exposure that any given misconfiguration creates. The ability for these solutions to comprehensively enumerate every relationship that exists in AD means that APM solutions can empirically assess the risk to any given high-value target.
Empirical Impact Assessment Benefits
Benefit 1: Data-driven Prioritization
Being presented with a list of hundreds or thousands of misconfigurations from Active Directory security tools can be daunting. Sorting that list based on which items are ‘serious’ based on the potential risk without the context of your network is a recipe for wasted time and effort. Instead, APM solutions like BloodHound Enterprise provide organizations the empirical exposure (percentage of overall users & computers in an organization that are part of a pathway) for any given Attack Path.
BloodHound Enterprise Attack Paths have the following Exposure rankings:
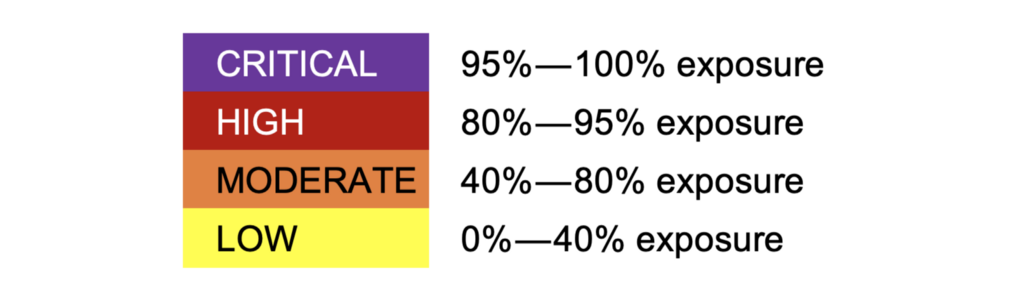
This calculation determines the severity of any given Attack Path by the specific configuration of an environment, rather than hard-coded values based on one particular tactic or subjective (read: flawed) views of risk.
It is not unusual for organizations to have high severity Attack Path exposures (see my previous post on Active Directory Attack Paths — “Is it always this bad?” for more details about why). By accurately identifying Attack path choke points, APM minimizes work required to eliminate the risk of all the downstream misconfigurations.
Benefit 2: Measureable Remediation
One of the biggest challenges in remediation efforts is knowing whether the mitigation actions were effective. Traditionally, one of the challenges of solving Attack Path risk was determining whether any particular change removed the actual risk. Due to the continuous and comprehensive mapping performed in BloodHound Enterprise, you will quickly see if your mitigation efforts eliminated or reduced the Attack Path Exposure. No more reliance on hope as a strategy.
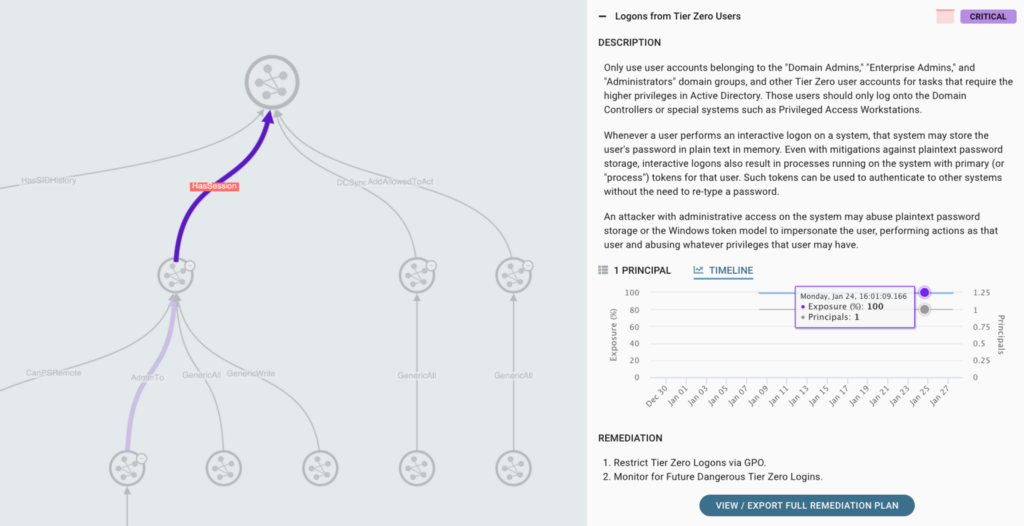
Benefit 3: Identify and Reverse AD Configurations with Unintended Consequences
Directory services such as Active Directory or Azure AD are not static; organizations must make configuration changes frequently to enable applications, users, and groups. As such, changes with the best intentions can create unintended consequences. Continuous visibility into Attack Paths allows our customers to quickly identify and reverse AD configuration changes if they create risky exposure. We’ve seen seemingly benign configurations in AD spawn massive risk from Attack Paths. With a constant, up-to-date picture of this map, teams can cut off newly formed Attack Paths early rather than identifying them 3, 6, or even 12 months later after business processes require those new relationships.
Benefit 4: Unambiguous Security Posture Metrics
It is essential to assess your security posture in a quantifiable way. We can’t improve what we can’t measure. Further, we need to be able to communicate both the risk that specific projects / endeavors may have on the organization’s security posture and illustrate the performance of a given team or technology. Subjective metrics lack empirical data, only complicate matters, and therefore don’t help. APM solutions like BloodHound Enterprise present clear, unambiguous exposure metrics that can be measured and presented over time.
BloodHound Enterprise specifically measures Tier Zero Exposure over time. In other words, “how much of my environment has the ability to attack our high-value targets using any available Attack Path”. This empirical measurement is used across security / AD / and other IT teams to establish a common understanding of the risk and how to measure the effectiveness of overall Attack Path Management efforts.
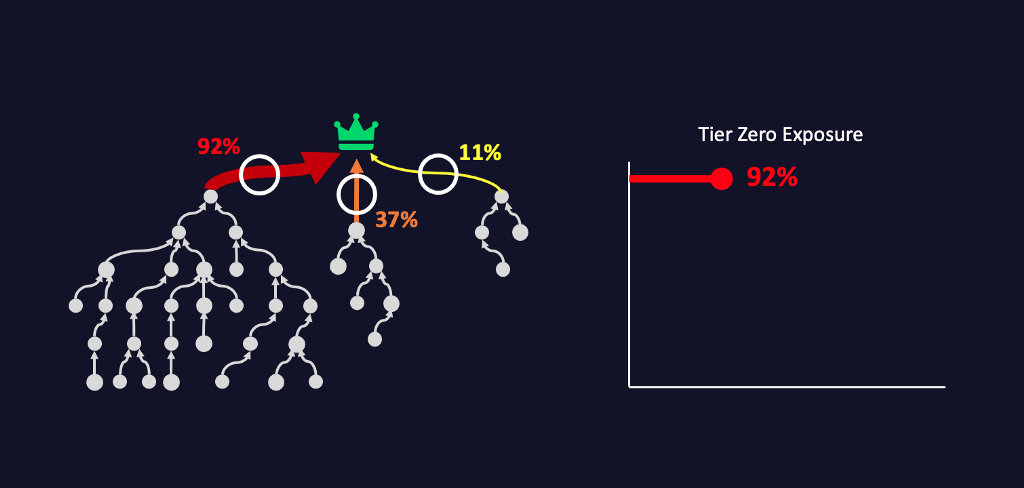
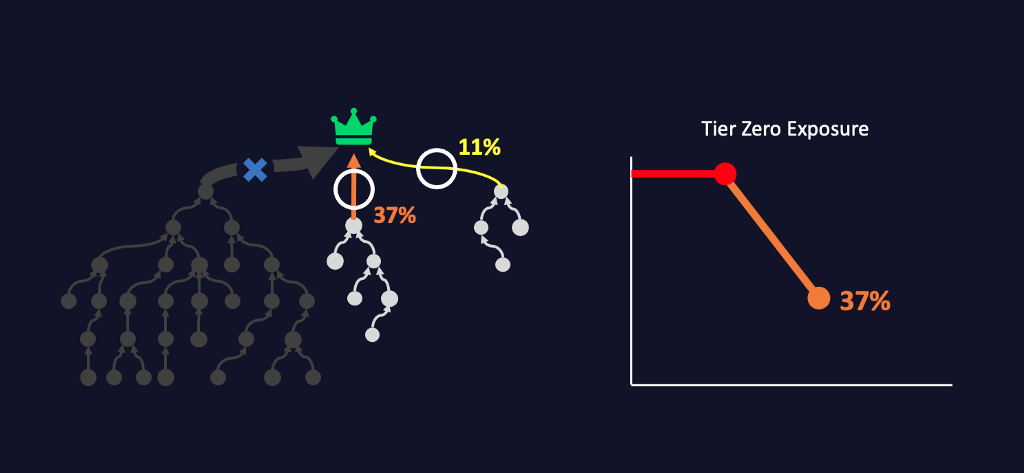
Summary
As a recap, BloodHound Enterprise delivers Attack Path Management by going beyond AD scans that simply list misconfigurations and instead maps the links and relationships that produce pathways adversaries can use to take control of your corporate network and systems. These maps automatically pinpoint the most critical misconfigurations to your high-value targets and provide an empirical impact assessment to inform you of the exposure (the number of users / computers that have direct / indirect access to those targets) of each of these choke points. Admin teams can then systematically address each choke point (from highest to lowest exposure), eliminating the risk of the thousands of downstream misconfigurations and taking away the adversary’s favorite tactic to control your organization.
Part three of this series will show how APM solutions like BloodHound Enterprise provide practitioners with practical, precise, and safe remediation guidance. Doing so ensures mitigation efforts effectively and efficiently deliver reduced exposure.
If you’re interested in learning more about BloodHound Enterprise, sign up for a demo here.
3 Foundational Pillars for Attack Path Management: Pillar 2 — Empirical Impact Assessment was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.